With the spread of ransomware, it has brought serious threats to enterprises and individuals. 360 Brain of Safety has carried out comprehensive monitoring and defense against ransomware. From the data of this month, the feedback volume of anti-Lex virus has decreased slightly. Sodinokibi, Planetary and MegaCortext ransomware were added this month.
The 360 decryption tools added a new hacking virus for PokemonGo, Stop/KeyPass and SadComputer this month.
Infection data analysis
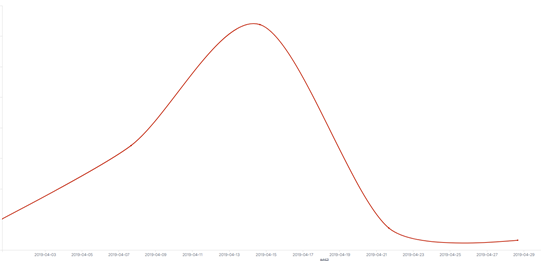
According to the statistics of the feedback data of the extortion virus in April 2019, this month’s feedback has a small decline compared with March. At the same time, there are two new ransomware worthy of attention this month: the Planetary ransomware distributed through the Windows domain, and the Sodinokibi ransomware (“Lock Blue” ransomware), which is highly coincident with the GandCrab transmission channel.
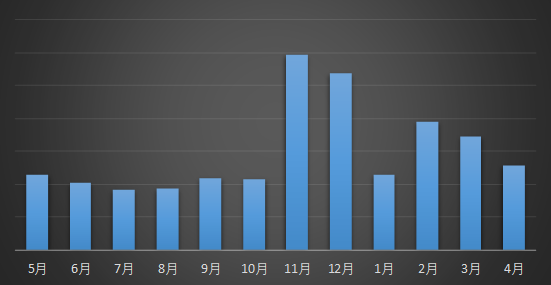
Figure 1. Ransomware feedback statistics for the past 12 months
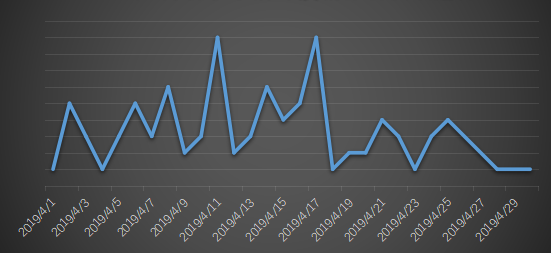
From the distribution of feedback volume, there are two peak feedbacks this month: April 11 and April 17 respectively. From the family of user feedback, there is no big outbreak in a single family. The two peaks of feedback are caused by the increase in the number of ransomware families.
Figure 2. Ransomeware feedback trend in April 2019
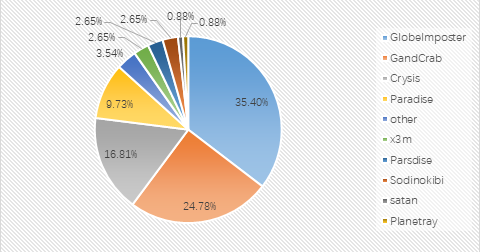
This month’s ransomware family accounted for the proportion: GandCrab ransomware slipped to second place, accounting for 24.78% this month; while GlobeImposter returned to the top with 35.4%; Crysis ransomware accounted for 16.81% Continue to stay in third place. The main reason for the decline in the GandCrab family is that GandCrab’s transmission channel is also diverted by two other ransomware, Paradise and Sodinokib.
Figure 3. Ransomware feedback distribution map for April 2019
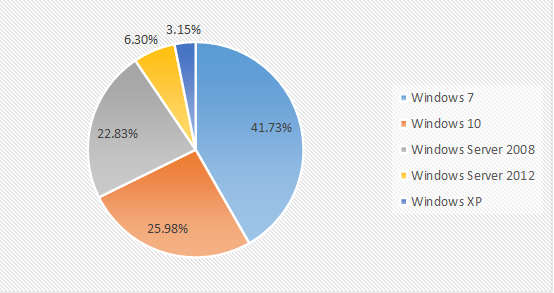
From the proportion of infected systems, the top three in this month are still Windows 7, Windows 2008 and Windows 10. Among them, Windows 7 system ranked first in all system versions with 41.73%, but it has a downward trend compared with 49.71% in the previous month.
Figure 4. Proportion of infected systems in April 2019
Comparing the infected system in March and April of 2019, it was found that the proportion of personal systems and server systems in the infected system in the two months was relatively stable, and the change was not very large.
Figure 5. Comparison of types of infected systems in March 2019 and April 2019
Epidemic Analysis of Ransomware
Sodinokibi Ransomware
At the end of April, 360 Brain of Safety monitored the ransomware transmission using a variety of methods, mainly using the WebLogic Remote Code Execution Vulnerability CVE-2019-2725 just revealed at the end of this month and attacking Windows servers with other vulnerabilities. In addition, The ransomware also uses spam to spread. There are two methods for spam propagation: the first method is to disguise the exe program to spread the image attachment; the second method is to use the macro of the Word document to spread. The following is a situational picture of 360 Brain of Safety detecting the spread of the ransomware through the vulnerability.
Figure 6. The situation of the Sodinokibi ransomware spread through the vulnerability
GandCrab Ransomware
This month, GandCrab was diverted from the two ransomware families of Paradsie and Sodinokibi, resulting in a significant drop in the amount of transmission. At the same time, 360 Brain of Safety detected that GandCrab’s spread was divided into three phases this month: the first phase of use of vulnerabilities, U disk worms, remote desktop weak password attacks and spam to spread; the second solution phase has almost no transmission; The third stage is to pretend to be DHL (Global Logistics) to send an email, indicating that the package delivery is infinitely extended, and the attachment is a delay description. The attachment contains two exes and two shortcut keys (both executables are ransomware), and the shortcut points to the hidden ransomware.
MegaCortext Ransomware
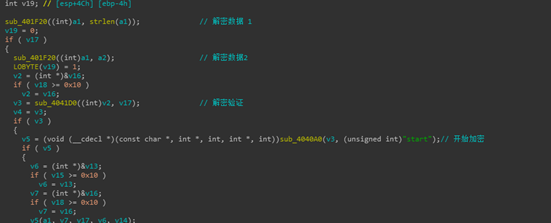
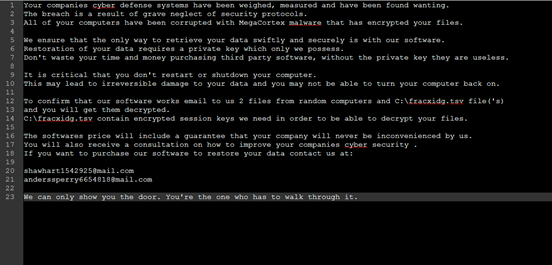
MegaCortext ransomware is a new ransomware that appeared at the end of this month. The ransomware spreader will send a batch to the entire domain after invading the domain control server. The batch file closes 44 processes and 199 systems. The service will disable 194 services, and will also issue a ransomware loader. The loader has a batch that passes a basbe64 string as a parameter to raise. Use a base64 string and a hard-coded string to XOR to generate a key, and use the key to decrypt the code of the encrypted file through the AES algorithm.
Figure 7. Decrypting the encrypted code
Figure 8. MegaCortext ransomware alert message
Satan Ramsomware
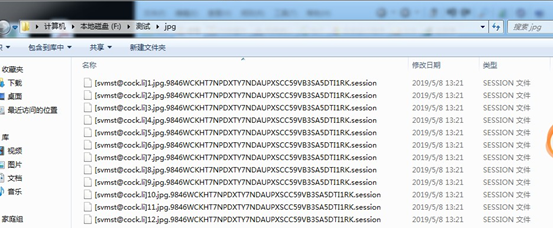
360 Brain of Safety has detected that the Satan ransom virus did not launch a major attack this month, and the overall spread in April was small. But this month Satan updated the encryption program again, changing the suffix to session and not using the previous mailbox. In addition, this update also confuses the code and adds anti-debugging features.
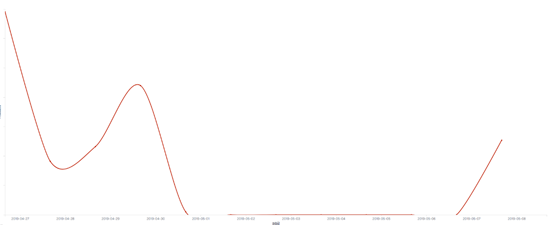
Figure 9. Satan ransomware transmission trend
Figure 10. Files encrypted by Satan
Hacker information disclosure
The following is the ransomware contact email used by hackers since April 2019.
| beam@firemail.cc | support@p-security.li | supportbest@protonmail4.com |
| tracsebluopa1975@aol.com | pedantback@protonmail.com | datadecrypt@qq.com |
| falitodalgliesh@aol.com | coffix@india.com | encrypted@cock.li |
| crypt_sherhagdomski@godzym_bid | Coffix@Tuta.Io | helpme@countermail.com |
| gabbiemciveen@aol.com | jaffe@india.com | veracrypt@foxmail.com |
| barddoling@ganefs.com | kolet@tuta.io | ngeloco1337@protonmail.com |
| alphonsepercy@aol.com | andriybakyn@india.com | btc@decoding.biz |
| park.jehu@aol.com | cartmelsutton@venom.io | killsever@portonmail.com |
| mr.crypt@aol.com | supportbest@protonmail.com | icanhelp@cock.li |
| bk666@protonmail.com | evilcock@cock.li | serverkill@protonmail.com |
| mr.hacker@tutanota.com | goliaf@tuta.io | software7@tutanota.com |
| reek@tuta.io | alekstraza@bigmir.net | break@cock.li |
| return.data@qq.com | altairs35@protonmail.com | savefiles@cock.li |
| clasp@firemail.cc | backupfiles@keemail.me | decryptyourdata@qq.com |
| DonovanTudor@aol.com | booth_beau@aol.com | killbillkill@protonmail3.com |
| Killserver@protonmail.com | calwiposla1974@aol.com | China.helper@aol.com |
| alldataback@protonmail.com | data@decoding.biz | barddolling@ganefs.com |
| phobosrecovery@cock.li | decryptdocs@airmail.cc | mrgrayhorse@protonmail2.com |
| MailPayment@decoding.biz | decryptdocs@protonmail.com | scaletto@protonmail.com |
| parrnell.c@aol.com | decryptmyfiles@qq.com | backdata@qq.com |
| rodent@cock.li | decryptoperator@qq.com | decrypter2018@hotmail.com |
| killserver@protonmail.com | getbackdata@qq.com | nmare@protonmail.com |
| mailpayment@decoding.biz | helip@protonmail.com | tidwell.thibaud@aol.com |
| aq811@cock.li | lockhelp@qq.com | Benjamin_Jack2811@aol.com |
| donovantudor@aol.com | master777@tutanota.com | Benjamin_Jack2811@aol3.com |
| crypted_bizarrio@pay4me_in | recoveryhelp@airmail.cc | mrgrayhorse@protonmail3.com |
| autrey.b@aol.com | todecrypt@protonmail.com | support1prt@cock.li |
| hulkhoganztx@protonmail2.com | usacode@aol.com | franniestopp@magte.ch |
| hulkhoganztx@protonmail.com | immortalsupport@cock.li | unlock@cock.li |
| gorentos@bitmessage.ch | Benjamin_Jack2811@aol1.com | wixomd@ymolt2.com |
| merosa@firemail.cc | Benjamin_Jack2811@aol2.com | BIGBOSS777@airmail.cc |
| merosa@india.com | dresdent@protonmail1.com | decryptprof@qq.com |
| vengisto@firemail.cc | HulkHoganZTX@protonmail2.com | ramsey_frederick@aol.com |
| vengisto@india.com | Killback@protonmail2.com | REDHEAD |
Server protection data analysis
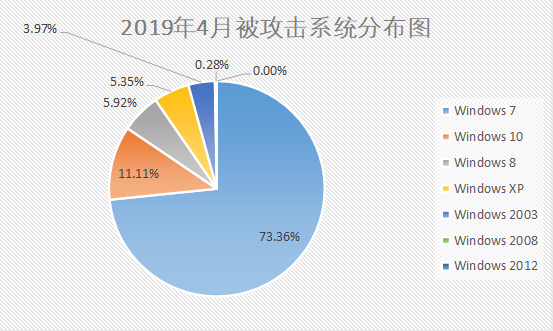
Through the comparative analysis of the data of March and April 2019, it is found that there is no change in the operating system’s proportion of rankings, only a small fluctuation.
Figure 11. Distribution of attacked systems in April 2019
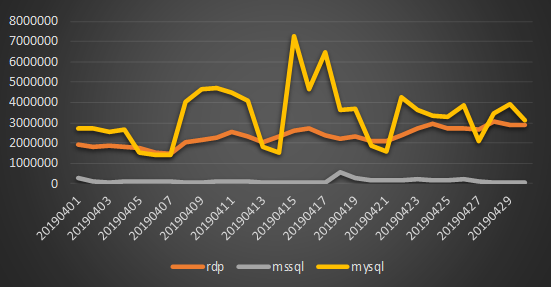
Through the statistical analysis of the weak password attack data monitored by 360 Brain of Safety, it is found that the overall trend of MySQL weak password attack has a great ups and downs. MySQL weak password attack has become the most popular object of hackers, and RDP (remote desktop) is weak. The password attack trend is relatively stable.
Summary
The ransomware attack against the server is still a major direction of the current ransomware. Enterprises need to strengthen their information security management capabilities—especially weak passwords, vulnerabilities, file sharing, and remote desktop management to deal with the threat of ransomware. Here we give the administrator some advice:
- Multiple machines, don’t use the same account and password.
- The login password must be of sufficient length and complexity, and the login password should be changed periodically.
- The shared folder of important information should be set to access control and be backed up regularly.
- Regularly detect security vulnerabilities in systems and software and patch them in time.
- Check the server periodically to see if there is an exception. View range includes.
a) Is there a new account?
b) Is the guest enabled?
c) Is there any abnormality in the Windows system log?
d) Whether the anti-virus software has abnormal interception
For the ransomware that launched this pair of personal computers that re-emerged this month, it is recommended that users:
1.Install 360 Total Security and make sure it is working properly.
2.Download the installation software from official channel.
3.For unfamiliar software, if it has been blocked by anti-virus software, don’t add trust to continue running.
Learn more about 360 Total Security