The spread of the ransomware has brought serious security threats to businesses and individuals. The 360 security center provides comprehensive monitoring and defense against ransomware. From the statistics of this month, the feedback volume of anti-ransomware services has increased slightly, among which the feedback volume of GlobeImposter ranks first, and the new GetCrypt ransomware is worthy of attention.
The 360 decryption tools added new decryption function for ransomware X3m (suffix with firex3m), Planetary, JSWorm, and GetCrypt this month.
Infection Data Analysis
Compare with last month (April 2019), the amount of feedback on anti-ransomware services increased slightly this month. The increase was mainly due to new GetCrypt ransomware this month, and the Sodinokibi ransomware spread via email.
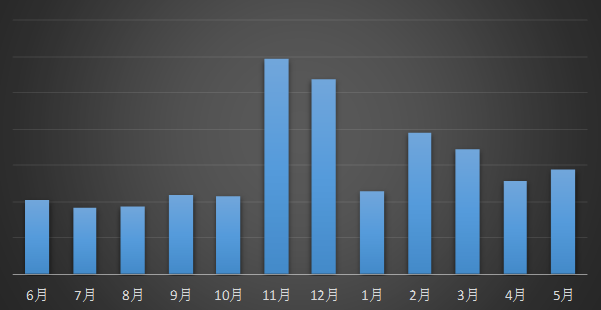 The feedback trand of ransomware in recent 12 months
The feedback trand of ransomware in recent 12 months
It shows from the feedback trends that there are more feedbacks on workdays and less on holidays. It mainly because the users can notice the malfunction of their machine earlier on workdays.
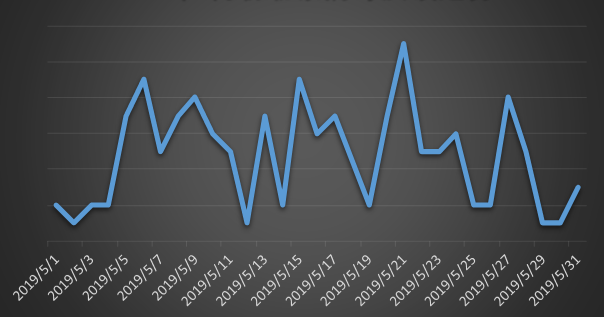 The feedback trends of ransomware in May
The feedback trends of ransomware in May
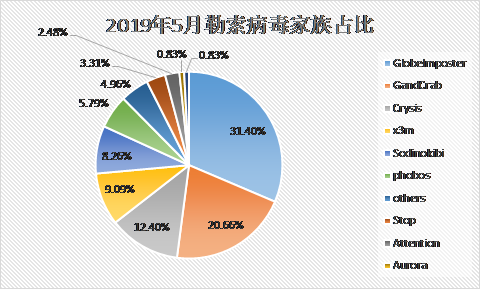
Analysis of the proportion of the ransomware families this month found that the GlobeImposter family accounted 31.4% of the total, followed by the GandCrab family, which accounted for 20.66%, and the Crysis family, which accounted for 12.4%
The proportion of ransomware families in May
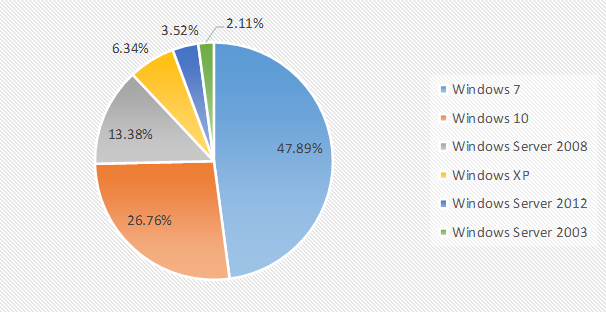
According to the proportion of infected systems, the top three in this month are still Windows 7, Windows 10, and Windows Server 2008. Among them, Windows 7 ranked first in all systems with 47.89%, compared with a slightly increase of 41.73% in the previous month.
The proportion of infected systems in May
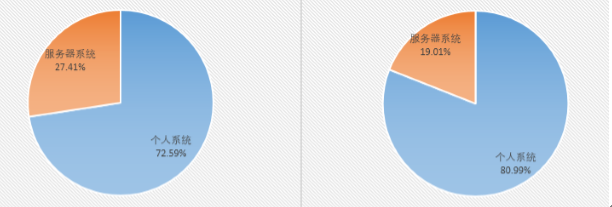
Compare with the infection system in April and May 2019, the proportion of personal system infection increased this month. This is closely related to the Sodinokibi ransomware appeared in early April, and it is expected that the proportion of personal system infection will increase in the coming month.
Comparison of the proportion of infected systems in April and May
The Epidemic Analysis of Ransomware
GandCrab
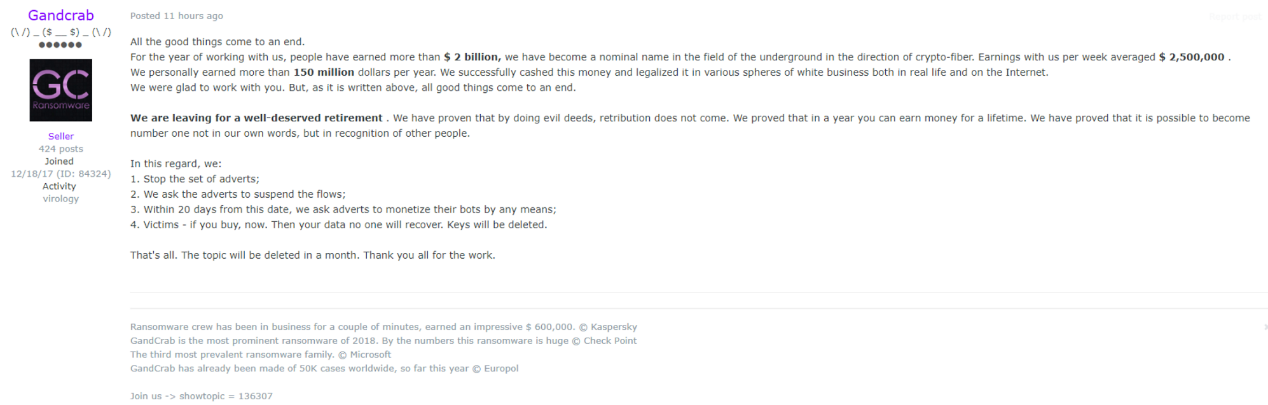
The volume of GandCrab has gradually declined since April. In mid-April, Sodinokibi started to occupy the main channel of GandCrab and achieved full channel occupation in May. Recently, the author of GandCrab announced in forum that the cumulative income has reached 2 billion US dollars, with an average weekly income of 2.5 million US dollars. The author also announced that it will stop the maintenance of the GandCrab ransomware and remove the key. The GandCrab ransomware has brought a “malicious paradigm” and it is expected that there will be more criminals join the ranks of making and distributing ransomare.
Forum announcement by the author of GandCrab
GetCrypt
On 21st May, 360 security center monitored GetCrypt ransomware began distributing through the RigEK vulnerability, and reached a peak on 22nd May. 360 total security intercepted more than 1,000 attacks of the virus every day, and monitored that recently the mainstream means of communication is illegal overseas websites. 360 decryption master to increase the decryption support for it. The 360 decryption tools has supported the decryption of GetCrypt.
X3m
X3m first appeared in 2016, but it has not received widespread attention due to its small amount of transmission. However, this time’s diffusion has led to an infection of many domestic enterprises and individual systems, and the influence has gradually increased. This variant mainly uses the brute force to get the remote desktop password and then manually poison it. The variant modifies the file suffix with firex3m.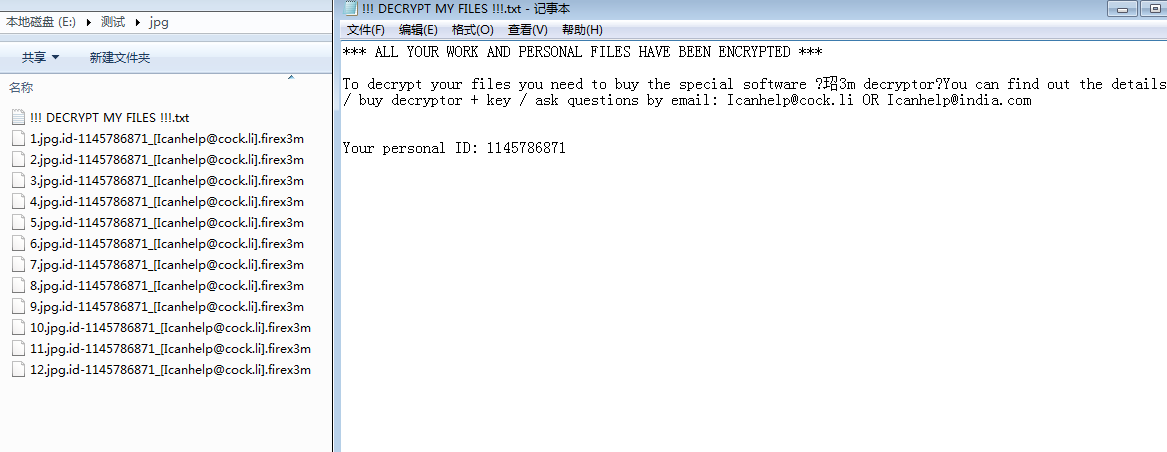
Files encrypted by X3m and Blackmail information
The 3DES and RC4 algorithms used in this variant to encrypt the file and write the key to the local temp000000.txt file. Therefore, as long as the temp000000.txt file still exists, the 360 decryption tools can be used for decryption.
Phobos
Phobos ransomware’s blackmail information, and its extensions are both similar to Crysis, and there are many similarities in the way it is diffused, so it is easy to be mistaken for the CrySis ransomware. The feedback of the ransom virus has increased significantly this month, and several variants with larger transmissions will modify the file suffixes as actin, phobos, and accon.
The difference between the ransomware and Crysis can be judged by the renamed file name:
- Files encrypted by Phobos
The blackmail prompt information interface uses the same prompt information as the Crysis ransomware, so it is difficult to distinguish the two ransomware families from the prompt information. Crysis’s tips have been used by many other ransomware families, such as the early Xiaoba, and the recent Paradise. This has been adopted by many families, which is closely related to Crysis’s “long history” (Crysis ransomware is the only family that has spread since 2016 and has never stopped).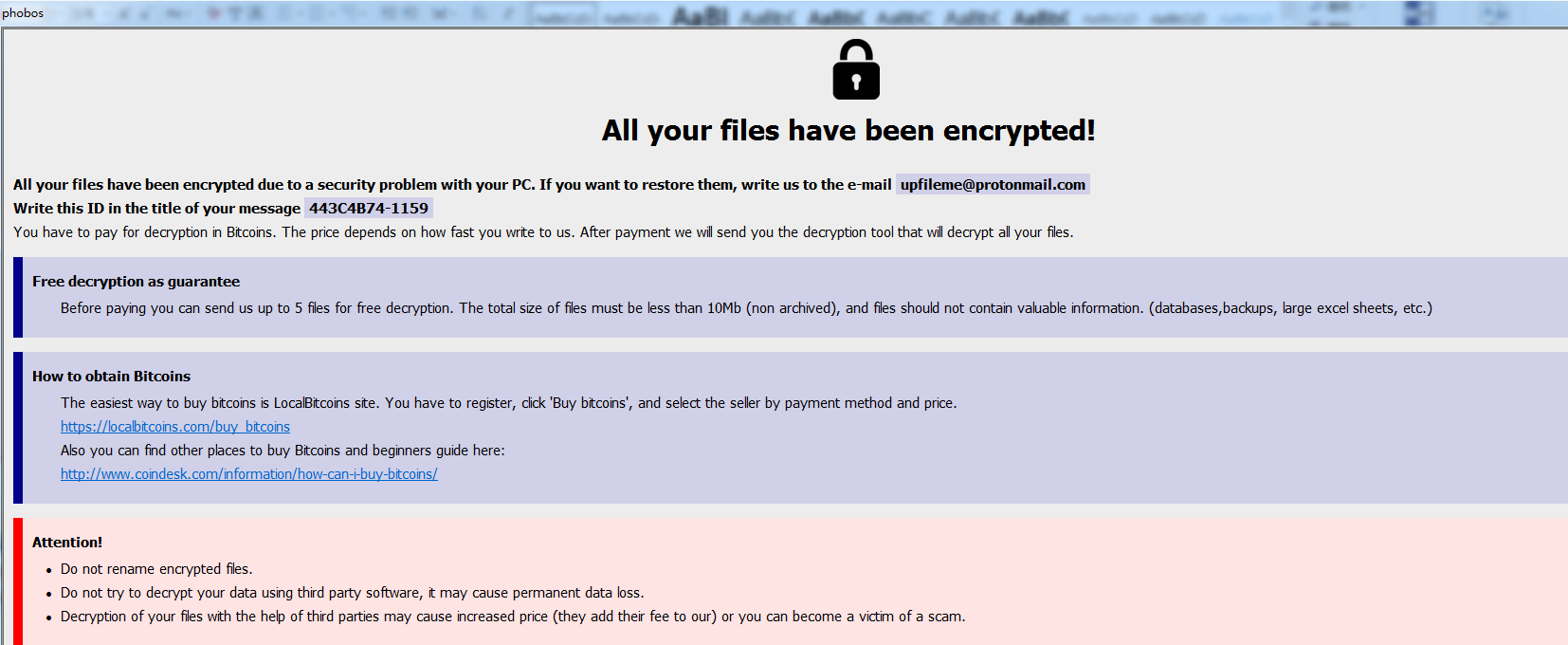
Phobos blackmail information
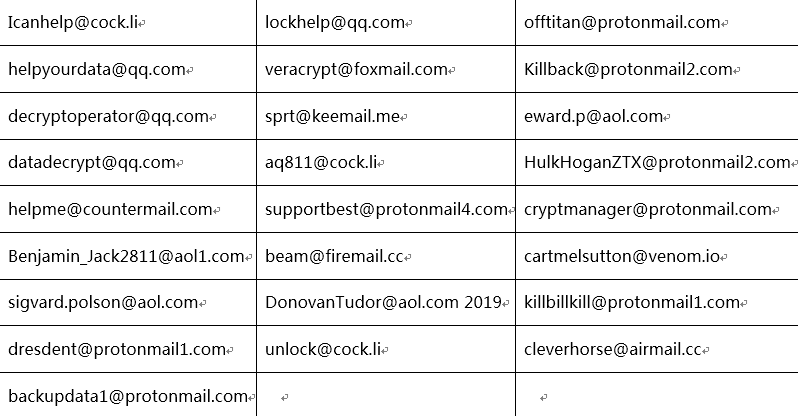
Hackers’ Information Disclosure
The following is the ransomware contact email used by hackers since May 2019:
Server Defence Data Analysis
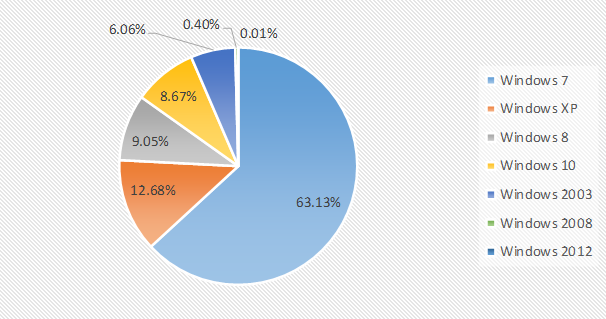
Through the comparative analysis of the data of April and May of 2019, it is found that among all the operating systems there is a significant increase in the XP system, from the previous month’s 5.92% as fourth to the current month’s 9.05% as second.
The Proportion of attacked system
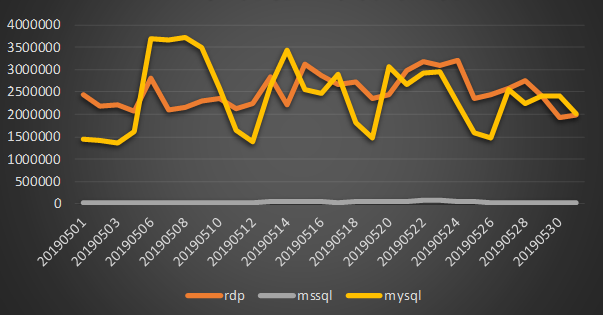
Through the analysis of weak password attack data in April and May, the number of weak password attacks has dropped significantly this month. The drop in attack volume mainly comes from weak password blasting against Mysql database, and the high peak dropped from more than 7 million to 400 million times, returning to the relatively “normal” attack peak.
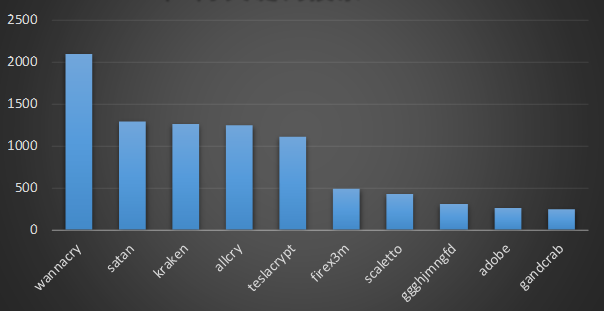
Ransomware Keywords
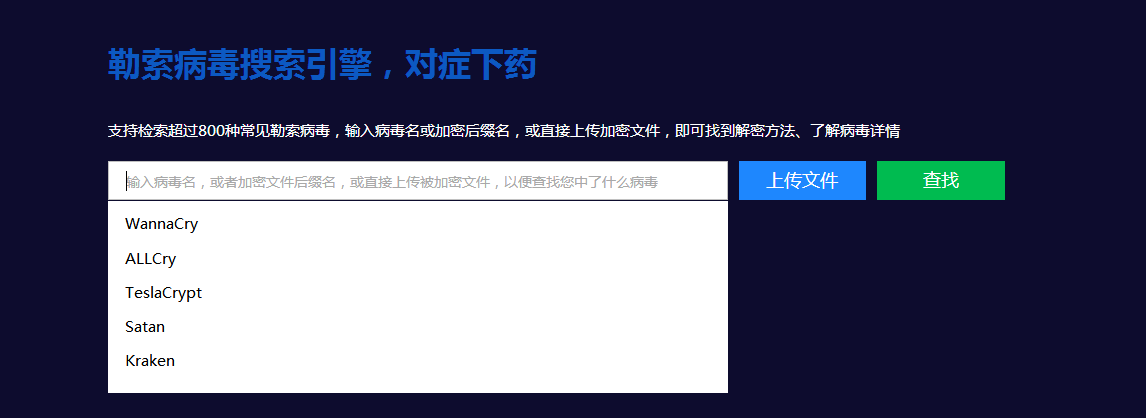
Because WannaCry, AllCry, TeslaCrypt, Satan, and kraken have experienced large-scale outbreaks, long-term transmission, or more domestic victims in the past, they have ranked in the early search and stayed in the recommendation column for a long time.
According to the users search for ransomware keywords statistics in this month. The keywords with large search volume are as follows:
- Firex3m: belongs to the X3m ransomware family, mainly through violent cracking of remote table passwords for manual poisoning. At present, it has been broken by the 360 decryption tools, and can be decrypted using the 360 decryption tools.
- Scaletto: belongs to the GlobeImpsoter family and is the most popular family this month.
- GGGHJMNGFD: belongs to the Attention family. The ransomware family is also manually sterilized by hacking remote desktop passwords. The ransomware family began to spread in March 2019. There are three known variants, respectively. The file suffix is OOOKJYHCTVDF. GGGHJMNGFD, YYYYBJQOQDU.
- Adobe: Belongs to the Crysis family, the adobe suffix is one of the most commonly used suffixes in the ransomware family.
- GandCrab: The ransomware author announced a profit of $2 billion and announced the suspension of GandCrab. Because of the high benefits it has received, it has caused a huge sensation in China.
Search key words top 10 in May 2019
Summary
The ransomware attack against the server is still a major direction of the current ransomware. Enterprises need to strengthen their information security management capabilities—especially weak passwords, vulnerabilities, file sharing, and remote desktop management to deal with the threat of ransomware. Here we give the administrator some advice:
- Multiple machines, don’t use the same account and password
- The login password must be of sufficient length and complexity, and the login password should be changed periodically.
- The shared folder of important information should be set to access control and be backed up regularly.
- Regularly detect security vulnerabilities in systems and software and patch them in time.
- Check the server periodically to see if there is an exception. View range includes:
- a) Is there a new account?
- b) Is the guest enabled?
- c) Is there any abnormality in the Windows system log?
- d) Whether the anti-virus software has abnormal interception
For the ransomware that launched this pair of personal computers that re-emerged this month, it is recommended that users:
- Install the security software and make sure it is working properly.
- Download the installation software from a regular channel.
- For unfamiliar software, if it has been blocked by anti-virus software, don’t add trust to continue running.
![· Crysis rename the file as : the original name.id-xxxxxxxx.[email address].suffix](https://static.ts.360.com/blog/wp-content/uploads/2019/06/8..png)
![Phobos rename the file as: the original name.id[xxxxxxxx-xxxx].[email address].suffix](https://static.ts.360.com/blog/wp-content/uploads/2019/06/9..png)