According to 360 Brain of Security monitoring, in the past September, although the spread of some virus families decreased slightly, the overall proportion remained high. At the same time, the spread of Phobos and GlobeImposter families keep incraesing. Nemty ransomware variants reproduction cause big loss to user’s wealth. It is not difficult to see that with the brutal spread and variants of the ransomware, personal and enterprise security are facing a new round of threats.
GlobeImposter family
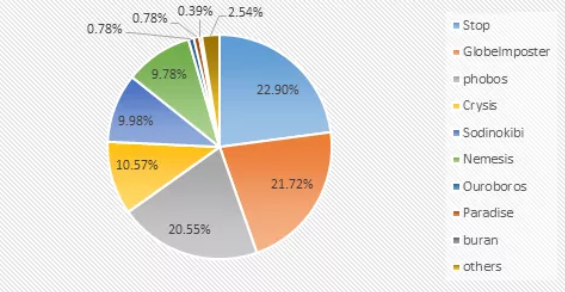
From the analysis of the proportion of the extortion virus family this month, the Stop family of the perennial tyrants is “slightly tired”, which is 12.24 percentage points lower than that of the previous month, but the overall traffic still leads the list with 22.90%. Closely followed are GlobeImposter family and phobos family, the amount of transmission has been steadily improved, and gradually narrowed to the top of the list, the two major ransomvirus family accounted for 21.72% and 20.55%.
Among them, the obvious increase of the GlobeImposter ransomware has become a “top killer” that is extremely harmful to enterprises. Since the ransomware communicator usually gets the password of a machine after blasting, then use the machine as a springboard to continue in the inner network. Therefore, once a computer in the intranet is compromised, multiple computers will be infected in the intranet. In addition, the ransomvirus has strong derivation ability and continues to evolve. After the “Twelve Lords + 865” series appeared last month, this month, on the basis of it, the “Twelve Lords + 865 +-20” series was derived, causing many companies to fall into blackmail.
Nemty virus “gene mutation” staged ransom storm
In the analysis of the proportion of infected personal systems and server systems in September, individual users were the main targets. This is closely related to the current distribution channel of ransomware. Sodinokidi and Nemty all use spam as the carrier to spread, while Stop spreads by disguising as activation tools and cracking software. These channels lead to personal system to be the majority of the infeacted system.
Among them, the Nemity ransomvirus that broke out in August 2019, 360 Brain of Security again monitored the latest variant of the ransom virus, Nemty 1.5 In September. From the monitoring data, the virus variant began to be distributed in large quantities via email on September 23, adding a download link to the content of the email, inducing the user to click to download and run the ransomware (“Download now” button in the figure below) This path is far more confusing than previous email attachments. At the same time, the payment page used by the Nemty 1.5 version banned the previous dark network (the user must use the Tor browser) to make the encrypted file “ransom” acquisition more convenient.
360 Brain of Security Build a safe wall in all directions
It is worth mentioning that in the 7th European Interpol-Interpol Cybercrime Conference, the report of the 2019 Internet Organized Crime Threat Assessment jointly released by Europol and Interpol pointed out that ransomware is still the biggest threat to network security, the worldwide need to strengthen cooperation against cybercrime.
In the face of the above security threats, the majority of users do not need to worry, the 360 Decryption Tool has added decryption support for the two ransomware families of Nemty and StopV2 in September. The newly emerged ransomware Nemty family at the end of August has already entered Top10. At the same time, from the decryption statistics of the decryption tool this month, the largest amount of decryption this month is the GandCrab ransomware and the highest number of users who use the decryption tool to decrypt files is the Stop family.
Throughout the analysis of the September ransomware epidemic situation, it is not difficult to see that the ransomware attack against the server is still the main direction of the current ransomware. Therefore, in order to cope with the threat of ransomware, enterprises urgently need to strengthen their own information security management capabilities such as weak passwords, vulnerabilities, file sharing and remote desktop management. 360 Brain of Security offers administrators the following targeted recommendations:
- As soon as possible, go to www.360totalsecurity.com to download and install 360 Total Security, and comprehensively intercept all kinds of ransomware attacks.
- Enterprise server administrators should not use the same account number and password for multiple machines, ensure login password complexity, and do regular replacement.
- The shared folder of important data should be set to access control and regular backup; regularly detect security vulnerabilities in the system and software, and timely patch.
- Individual users should download and install software from regular channels, use various activation tools with caution; for unfamiliar software, if it has been intercepted by anti-virus software, do not add trust to continue running.
- When encountering emails sent by strangers, be careful to check and try to avoid downloading attachments. If you need to download, please check the attachment firstly with security software.
Learn more about 360 Total Security