Ransomware has posed a serious threat to the data security of enterprises and individuals. Fortunately, 360 Internet Security Center has detected and defensed ransomware immediately. According to the feedback from our users, we found that the number of our users attacked by ransomware shows a downward trend in July. On the other hand, the protection record demonstrates that server attacks were still active. Last month, the number of interceptions for weak passwords on a single day reached 4 million times.
Additionally, the updated version of our Ransomware Decryption Tool has provided some supports for ransomware Satan. We have successfully helped lots of users recover their documents.
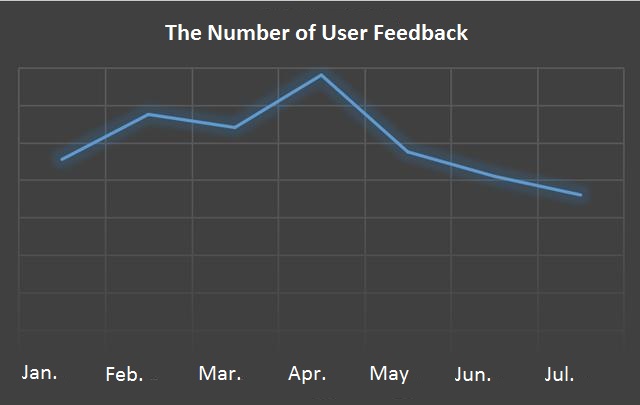
The data of the infected users
By analyzing our users’ feedback from January to July this year, the number of infected users has been declining since April. It can be concluded that 360 Total Security has produced significant effects on server anti-interceptions.
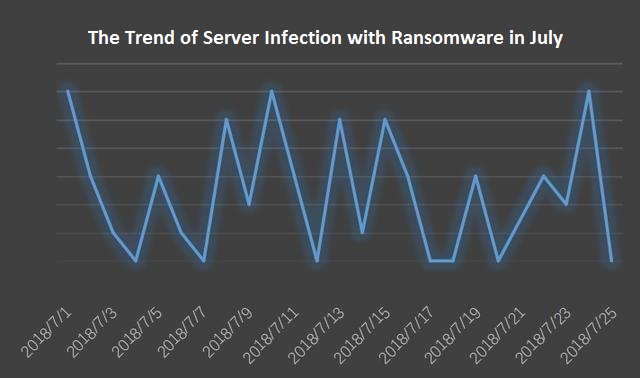
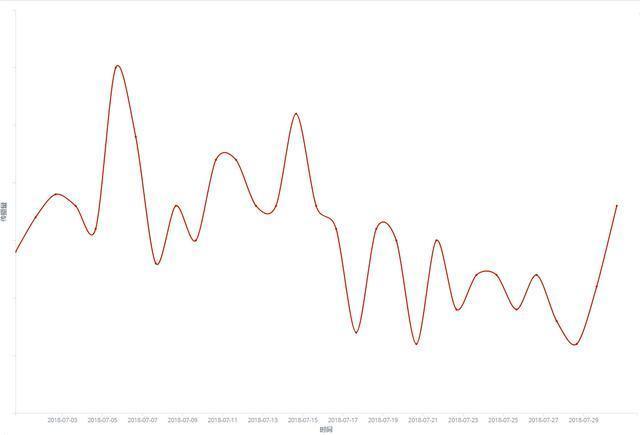
Based on the monitoring data in July, the weak password attack is still active. Also, the vulnerability attack has begun to increase, especially the third-party vulnerability attack such as WebLogic’s deserialization vulnerability. According to the inflection trend this month, the amount of ransomware transmission is not stable, showing cyclical fluctuations. This has a certain connection with its transmission method that the attackers like to launch attacks in a concentrated period of time.
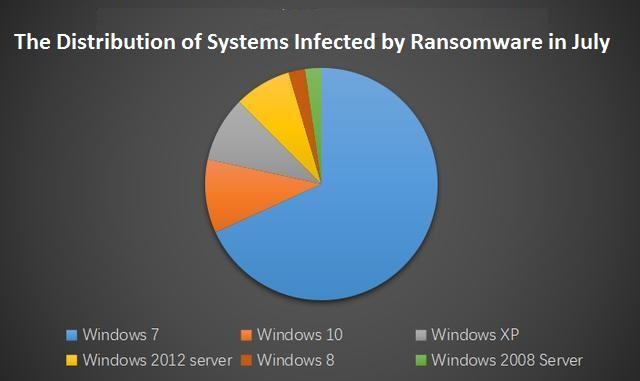
For the analysis of infected systems, the proportion of infections in Windows 7 is still the largest.
The analysis of ransomware
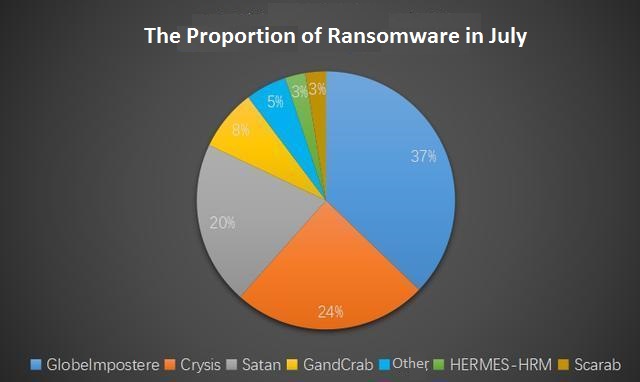
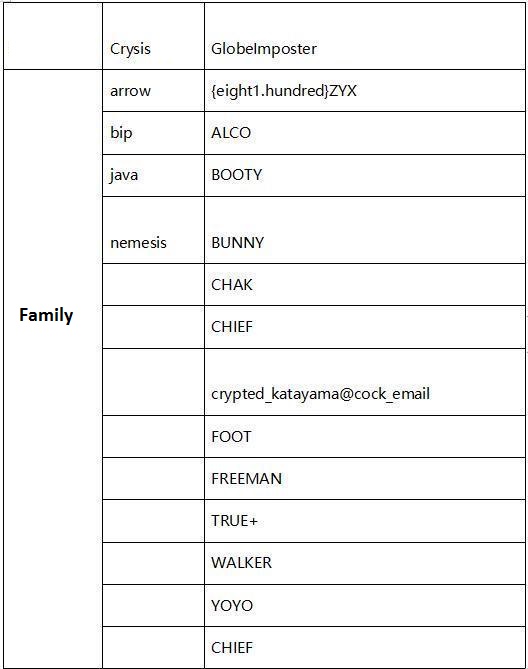
By collecting the statistics of anti-ransomware for July, Globelmposter and Crysis ransomware families are still the mainstream. Moreover, the proportion of Globelmposter has been higher than Crysis. For the BTCWare family, which had more feedback before, it did not have any new feedback this month. However, a new feedback about the Scarab ransomware exits this month.
The methods and the programs of the GlobeImposter family and the Crysis family have not changed a lot. We can see the suffixes that are still in use in the following table:
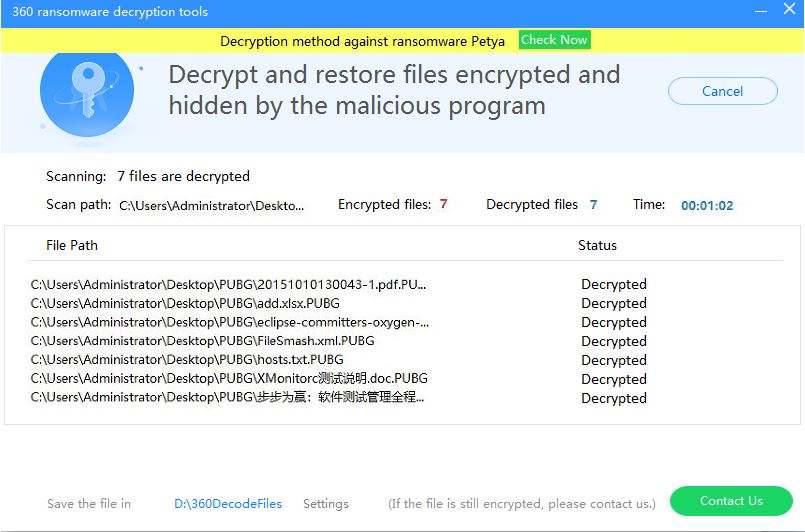
Among the ransomware still spreading in July is the ransomware Satan, which began its outbreak in June and was cracked in late July. The decryption tool has been added to the file decryption tool of 360 Total Security.
The image below is the screenshot of the user feedback provided, using our
file decryption tool for decryption:
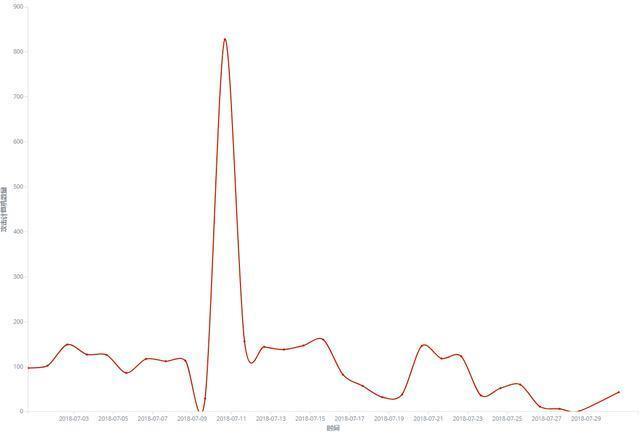
The spread of ransomware reached its highest point in mid-July, with a single-day interception of more than 800 times, and then began to decline.
Besides, Scarab is a new ransomware family which we should take attention to. Scarab was mainly spread in Russia before, but our users in Asia were infected seriously in July, causing servers to crash.
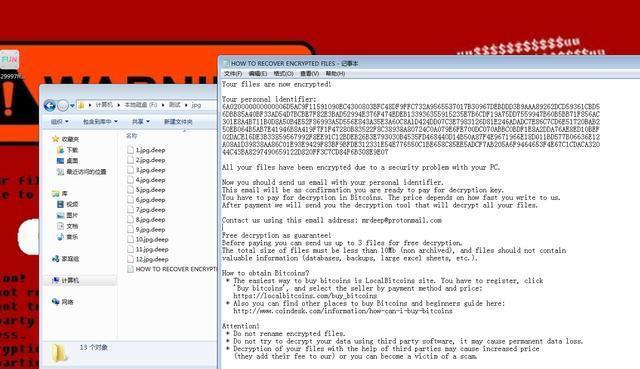
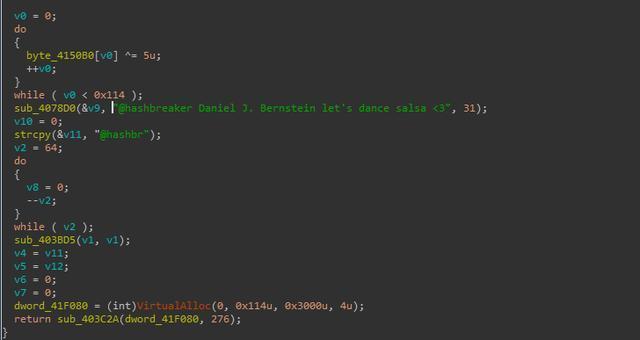
The early spread of Scarab ransomware was mainly spread by the Necurs botnet. At the late stage, it implanted virus into users’ systems mainly by cracking users’ weak passwords. The ransomware also used mass numbers of different file suffixes, which is similar to Globelmposter. The image below is one of the variants of Scarab.
GandCrab ransomware updated a new version, V4.0 in the early July, and a small version of update was also carried out in a month. Until now, GandCrab’s latest version captured by 360 Security Center is V4.2. In the process of updating the new version, our researchers guessed that GrandCrab had joined the SMB horizontal attack to spread because of its mass spreading numbers. However, it was confirmed that the ransomware has not yet joined this kind of spreading method. In the process of updating the version V3.0 to V4.0, the main update point is the encryption algorithm for the file. The ransomware changed from the initial use of RSA-2048 encryption algorithm to the more efficient encryption of Salsa2.0 algorithm.
Although the amount of GrandCrab infection is not large, according to our interception data, the ransomware family is still spreading.
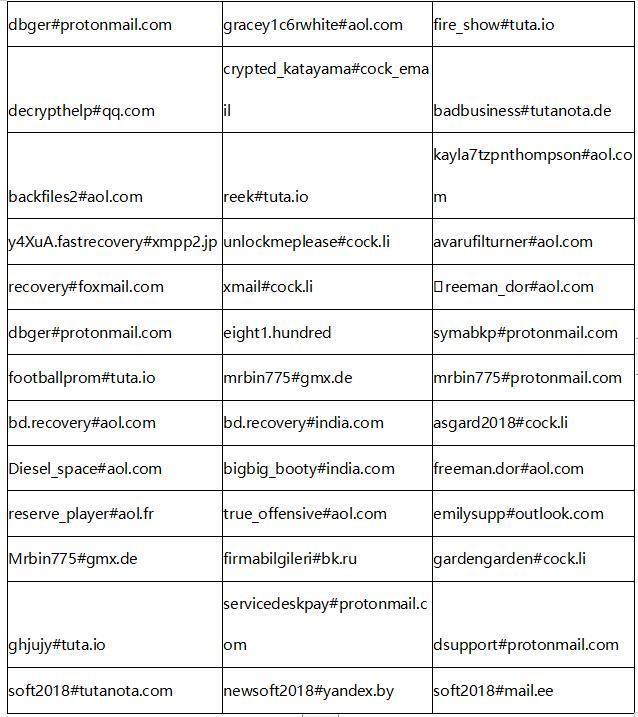
The following table contains the ransomware contact emails that hackers are still using since July (partly from our users’ feedback).
The data of attack protection
From the attack protection data in July, the proportion of Windows 7 in the attacked system is the highest, mainly because the number of Windows 7 user is large.
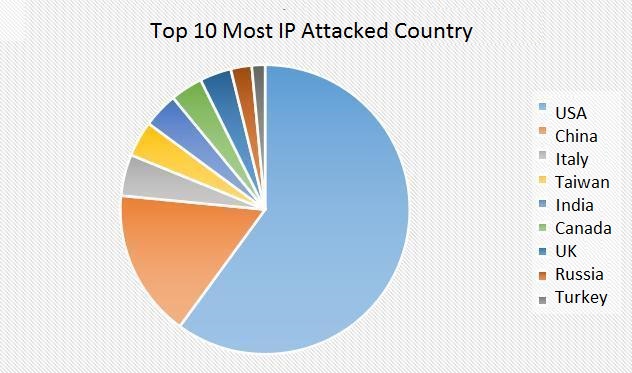
Analysis of the attack data found that the US IP occupies most of all IP. The following is a pie chart of the TOP10 of the IP-targeting country.
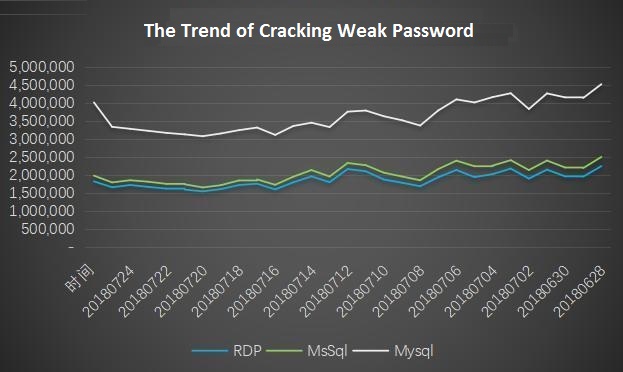
Currently, password anti-cracking has already supported the interception of weak password attacks against RDP, MySQL and MSSQL. The following is the interception data for July.
From the interception trend, the number of interceptions has shown a slight upward trend in this month. Through the analysis of IP data and the attacked users, it is found that hackers increase the attack frequency and tries to obtain the user login password more efficiently is the reason is the main cause of the upward trend.
Conclusion
The ransomware attack against the server has become a major direction of the current ransomware. Enterprises should strengthen their capabilities of information security management, especially weak passwords, vulnerabilities, file sharing and remote desktop management. Here are some suggestions to administrators:
1. Do not use the same account and password for multiple machines.
2. The login password must be complex. A password structure should be a mixture of uppercase and lowercase letters, numbers, and special symbols, and the number of passwords should be long enough, and the login password should be changed periodically.
3. Shared folder should be set access rights management. If users cannot set access rights because of other needs, it is recommended to perform regular security backups of this folder.
4. Regularly detect security vulnerabilities in systems and software, and patch them in time.