Overview
On the evening of December 9, 2021, the exploitation details of a remote code execution vulnerability in the open source project Apache Log4j 2 were made public. The incident quickly fermented and swept through most of the Internet. As Log4j is a common basic component of java logging and is widely used, the disaster area is also expanding rapidly. This weekend when major manufacturers are busy patching, 360 Security Center has also detected a large number of attacks against individual users, and Minecraft Java Edition is one of them.
Attacks against gamers
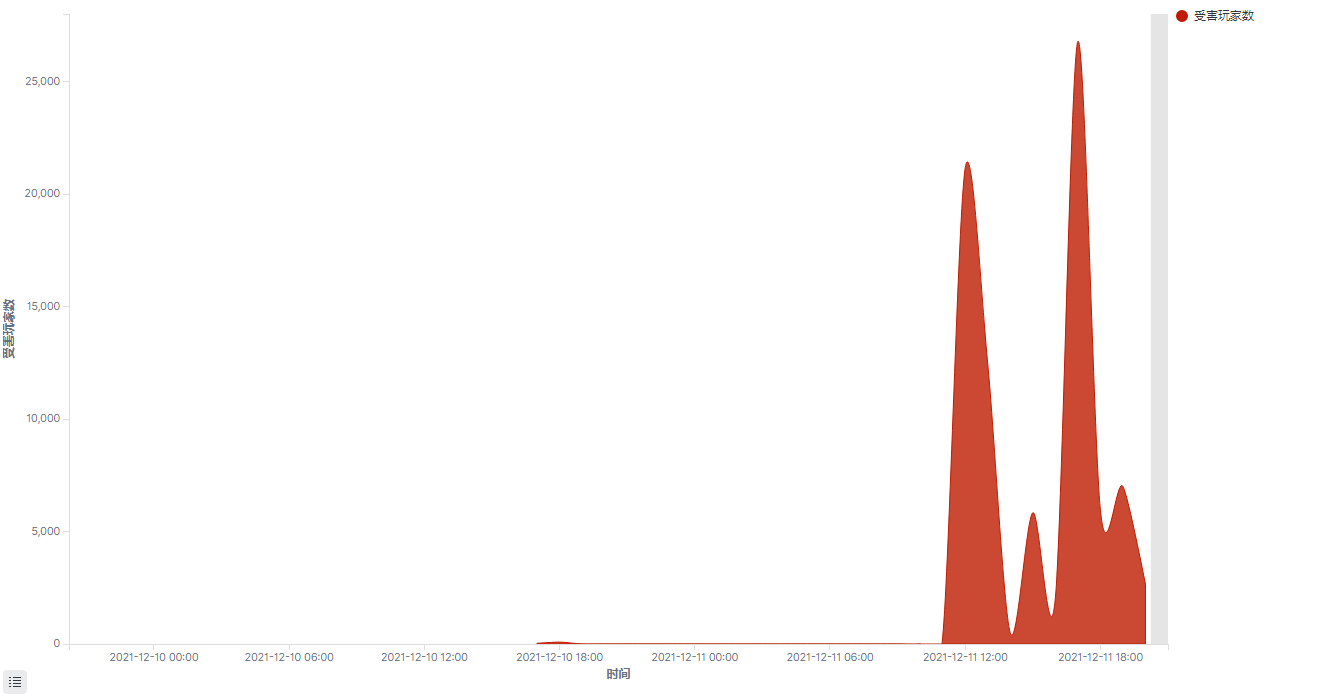
360 Security Center has detected that hackers are suspected of using the newly exposed log4j2 vulnerability to attack Minecraft players. The attack first occurred on December 10th. The scale of the early attack was small. The number of attacked players detected on the first day was around 100. Starting at 12 o’clock on December 11, hackers launched a large-scale attack. From 12 o’clock to the present, nearly 5,000 Mincraft players were attacked every hour on average. At the peak of the attack, more than 10,000 players were attacked.
Trends in the number of victimized players
There are also demonstrations of exploiting this vulnerability on the Internet. Just sending a message with a vulnerability triggering instruction in the online chat of the game can launch an attack on the user who receives this message. The attack is very easy to launch.
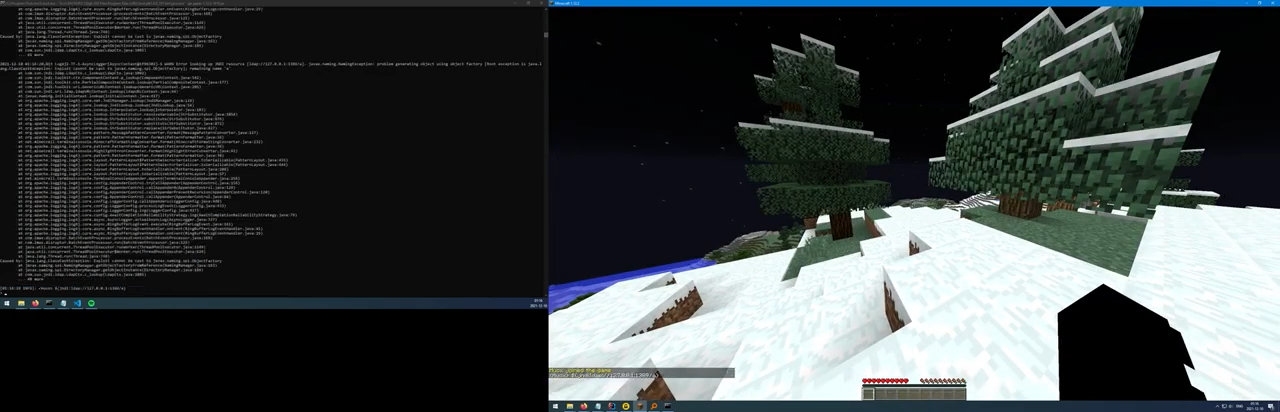
After the vulnerability is successfully exploited, the hacker triggers the remote code execution through the vulnerability, and then uses the local mshta to download and execute the remote hta file.
Process chain of attacked machine
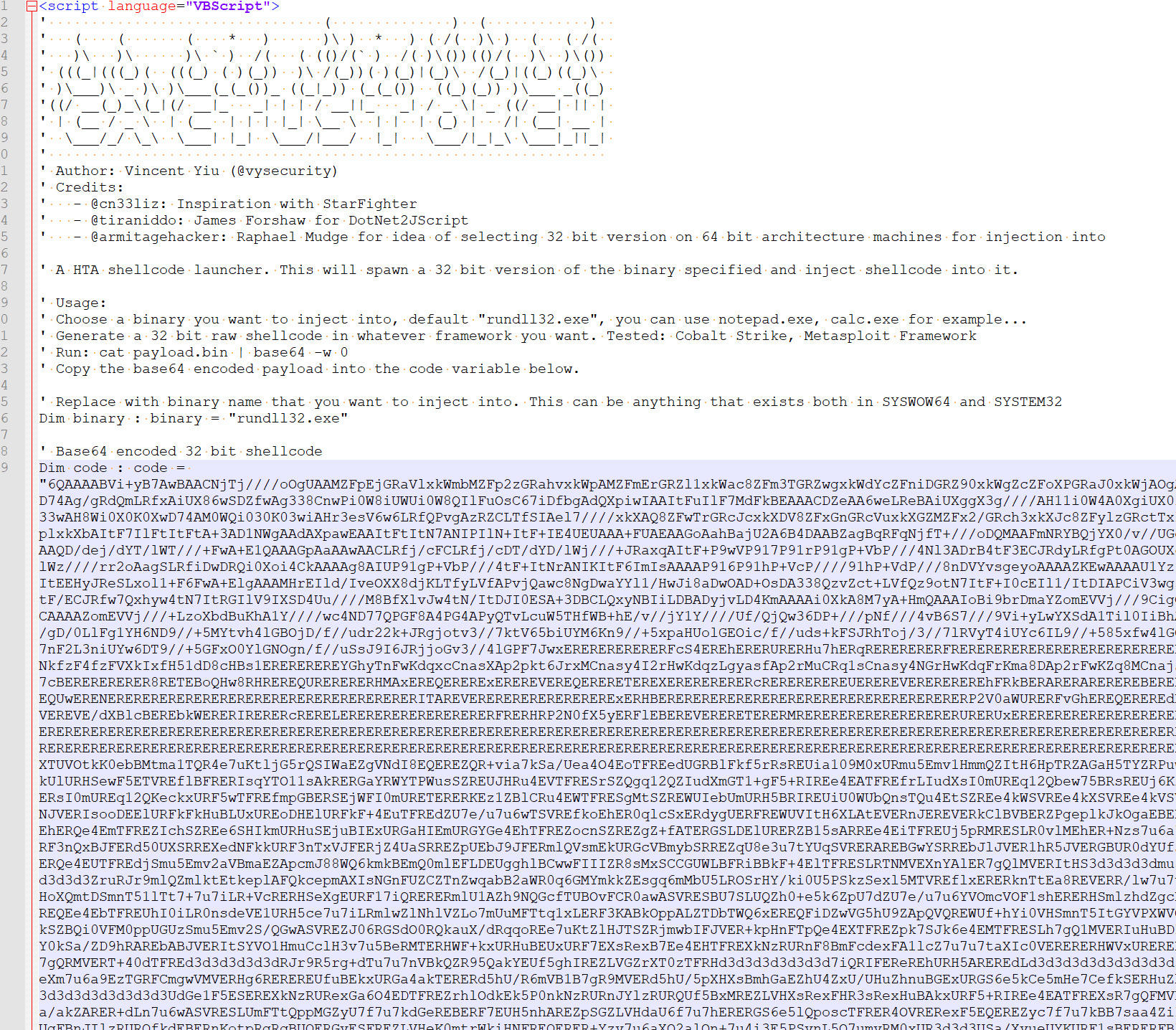
The hta file is actually a remote control Trojan generated by the cactusTorch framework. With this Trojan, the attacker can completely control the current user’s computer.
Part of the IOC of this attack
hxxp://114.132.231.19/A.hta
hxxp://114.132.231.19/O.hta
hxxp://114.132.231.19/2.hta
hxxp://114.132.231.19/OK1.hta
hxxp://114.132.231.19/OK1.hta
hxxp://114.132.231.19/hfs.exe
cc.wdnmdnmsl.xyz
Solution
For Minecraft vulnerabilities, manufacturers also urgently released repaired versions and repair suggestions. The main contents are as follows:
- If you use the official version, upgrade to the latest version as soon as possible, and you can upgrade by restarting the game.
- For unofficial versions, pay attention to third-party upgrade information.
- Use the Java version server, upgrade the version to 1.18.1
Official detailed recommended address: https://www.minecraft.net/zh-hans/article/important-message–security-vulnerability-java-edition
Regarding this attack, ordinary users should also harden their personal computers as soon as possible. 360 Security Center also gives the following security recommendations here:
Temporary emergency plan
Modify Log4j configuration:
log4j2.formatMsgNoLookups=True
Set the JVM startup parameters:
-Dlog4j2.formatMsgNoLookups=true
Set environment variables:
FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS value is true
360 Security Center Protection
Users who have installed the 360 Total Security, benefit from the powerful cloud intelligent recognition capabilities of 360 Security Center, and can recognize and intercept such attacks normally without upgrading.
At the same time, 360 has also updated the high-risk vulnerability immunity tool. You can download the green version on the official website of 360.cn and run it directly, mitigating similar attacks through vulnerability immunity.
At the same time, 360 has also updated the high-risk vulnerability immunity tool. You can download the green version on the official website of 360 Total Security and run it directly, mitigating similar attacks through vulnerability immunity.
http://www.360totalsecurity.com/en/sysvulterminator/
Learn more about 360 Total Security