Author: 360HeliosTeam
Source Link: http://blogs.360.cn/blog/wanacrypt0r_data_recovery_feasibility_analysi/
Recovery Tool Download Link: https://360totalsecurity.com/s/ransomrecovery/
Chapter 1 Introduction
Recently, 360 Internet Security Center detected a new variant of ransomware that targets both enterprises and individuals in multiple countries and regions. 360 released timely emergency warning on May 12th upon the detection to remind the users of the upcoming risks. The ransomware spreads itself with fast speed all around the world. According to incomplete statistics, in just a few hours of its burst, tens of thousands of devices in 99 countries have been infected and the Worm is still trying to expand its impact.
Generally, ransomeware is a kind of malicious program with clear extortion intention. It encrypts the victim’s files by using asymmetric cryptographic algorithm, making them inaccessible, and demands a ransom payment to decrypt them. Unless the ransom is paid, the files cannot be restored. This new variant is code-named as WanaCrypt0r by several security companies. What makes it so deadly is that it made use of the hacking tool “EternalBLue” which was stolen from the NSA . This also explains why WanaCrypt0r is able to spread itself quickly all over the globe and caused great loss in a very short time. Since the break-out of the Worm on May 12th, Core Security Department under 360 Internet Security Center has conducted close monitoring and in-depth analysis on it. We are now able to release a set of detection, defense and data recovery solutions against WanaCrypt0r.
360 Helios Team is the APT (Advanced Persistent Attack) research and analysis team of Core Security Department, mainly dedicated in APT attack investigation and threat incident response. Security Researchers have been analyzing the virus mechanism thoroughly to find the most efficient and precise method to recover the encrypted files. Using this technique, 360 is able to be the first security vendor that releases the data recovery tool – “360 Ransomware Infected File Recovery” to help its customers regain the infected files rapidly and completely. We hope that this article will be of a help for you to understand the tricks of this Worm, as well as a broader discussion towards recovering the encrypted files.
Chapter 2 Core Encryption Process Analysis
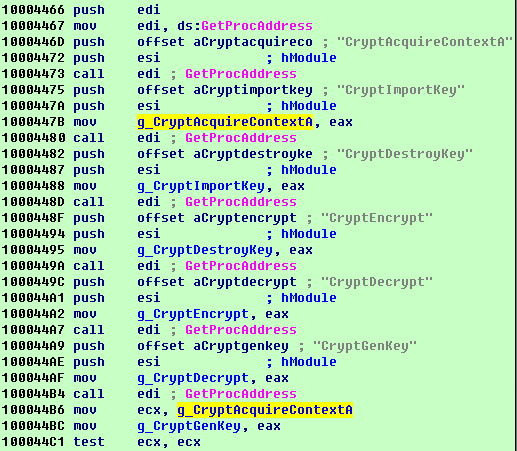
The worm will release an encryption module into memory and load the DLL in the memory directly. The DLL’s then exports function “TaskStart” which is to be used to activate the whole encryption process. The DLL dynamically get access to the file system and API functions that related to encryption in order to avoid static detection.
1. Initial stage
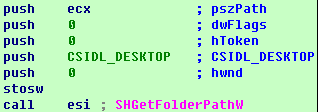
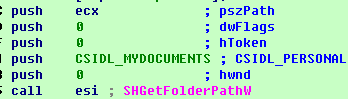
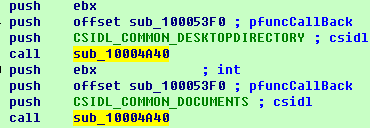
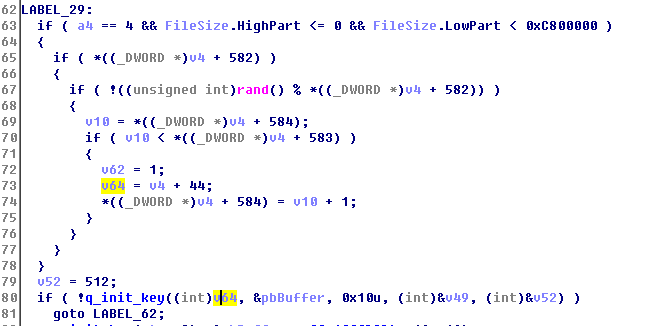
It firstly uses “SHGetFolderPathW” to get the paths of the desktop and file folders. Then it will call function “10004A40” to get the path of other users’ desktops and file folders and call function “EncrytFolder” to encrypt the folders separately.
It traverses all the disks twice from Z Drive all the way up to C Drive. The first scan is to run over all the local drives (excluding CD Driver). In the second scan, it checks all the mobile drives and calls function “EncrytFolder” to encrypt the file folders.
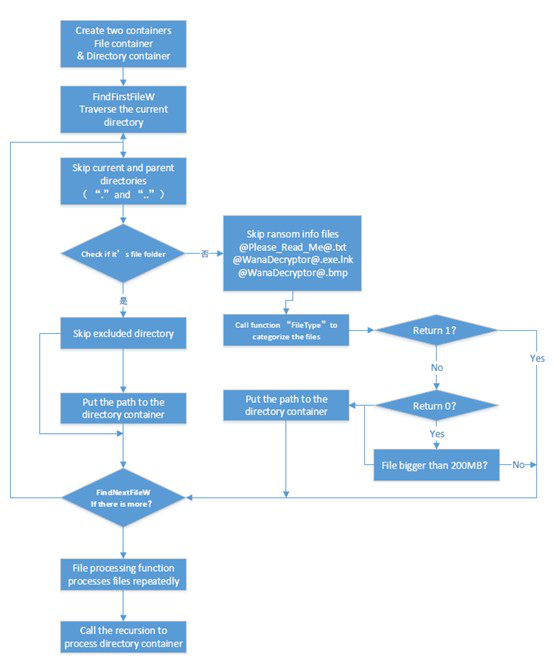
 2. File Traverse
2. File Traverse
Function “EncryptFolder” is a recursive function which can collect file information follows the below procedure:
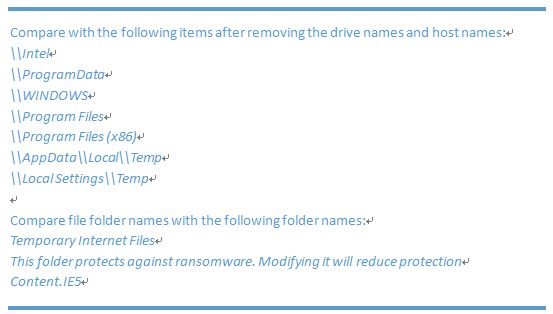
Remove paths or file folders during the traverse process:
There is an interesting folder with the name of “This folder protects against ransomware. Modifying it will reduce protection”. When you Google it, you will find that it matches the defense folder of ransomware protection software named Ransomfree.
While traversing the files, the ransomware will collect the file information such as files size, and then categorizes the files into different types according to their extension following certain rules:
Extension type list 1:
Extension type list 2:
3. Encryption Priority
In order to encrypt the important files as quickly as possible, WanaCrypt0r designed a complex priority queue:
Priority queue:
i. Encrypt Type 2 files that also match Extension list 1. If the file is smaller than 0X400, the encryption priority will be lowered.
ii. Encrypt Type 3 files that also match Extension list 2. If the file is smaller than 0X400, the encryption priority will be lowered.
iii. Encrypt the rest files (smaller than 0X400) and other files.
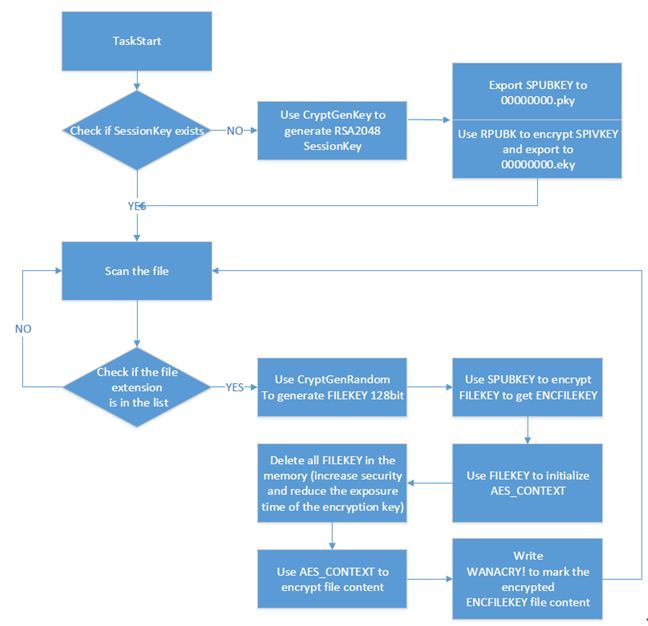
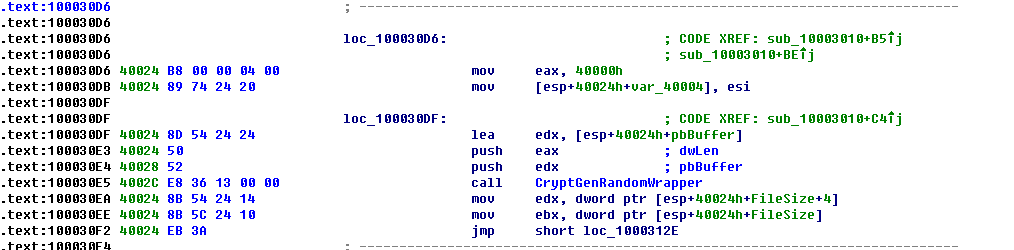
4. Encryption logic
The whole encryption process is completed by using both RSA and AES. While RSA encryption process uses a Microsoft CryptAPI, the AES code is statically compiled to the DLL. The encryption process is shown in the picture below:
File format after encryption:
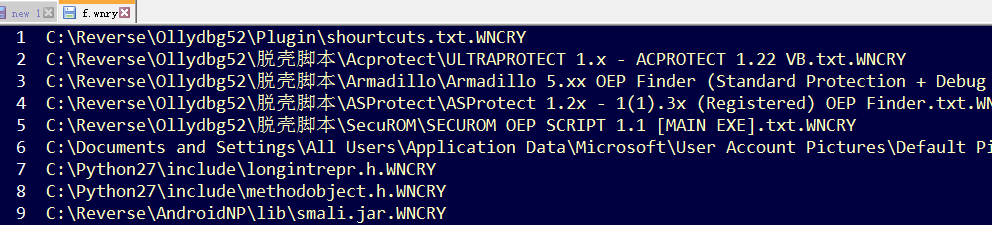
Note that during the encryption process, the ransomware will randomly select some files to encrypt using the built-in RSA public key in order to offer a couple of files that victims can decrypt for free.
The file path of the free files could be found in the file ‘f.wnry’.
5. Random number filling
After the encryption, WanaCrypt0r will fill the files that it considers as important with random numbers until totally ruin the file, and then move the files to temporary file directory to delete. By doing this, it makes it pretty difficult for file recovery tools to restore the files. In the same time, it can speed up the encryption process.
Filled files need to meet the requirements:
– In specified directory (desktop, my document, user folder)
– File is smaller than 200M
– File extension is in the extension type list 1
File filling logic:
– If the file is smaller than 0x400, it will be covered with random numbers of the same length
– If the file is bigger than 0x400, the last 0x400 will be covered with random numbers
– Re-locate the file pointer to the file header and set 0x40000 as a data buffer unit to cover the file with random numbers till the end.
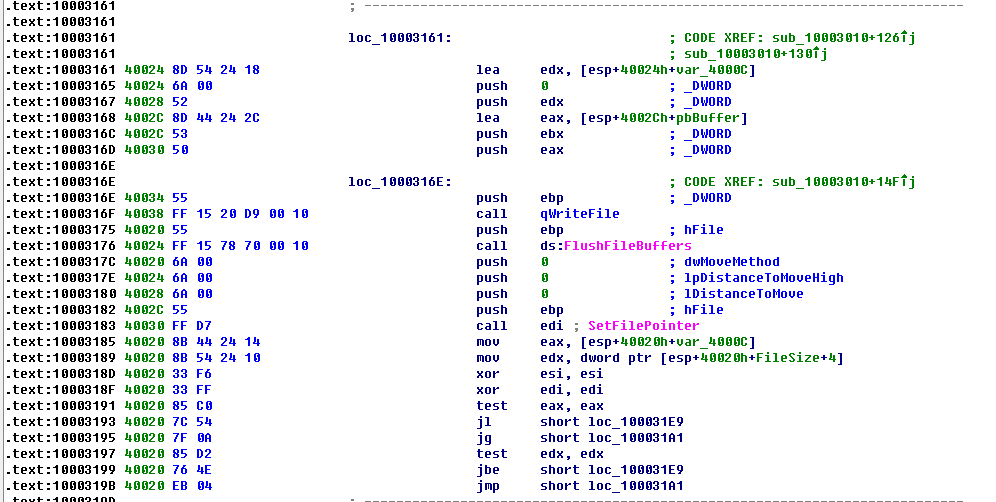
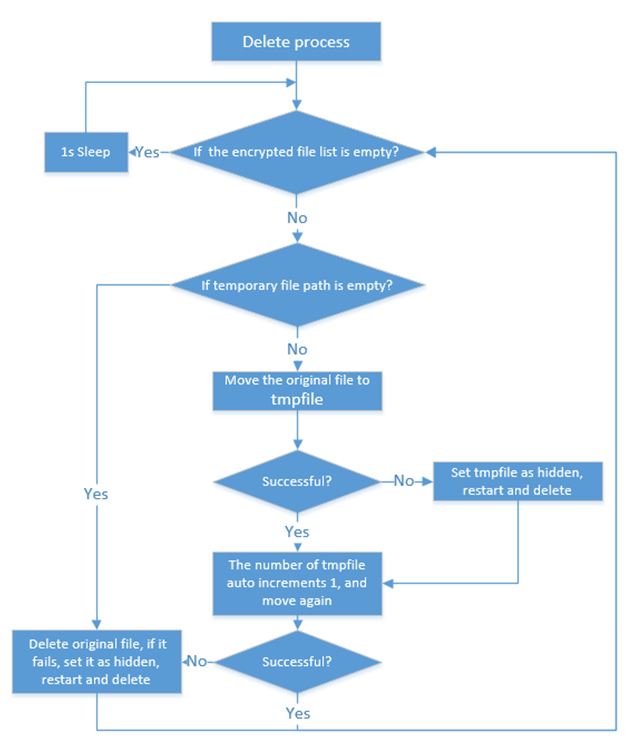
6. File deletion
WanaCrypt0r will firstly move the files to a temporary file folder to create a temporary file, and then deletes it with various methods.
When it traverses the drives for file encryption, it will create temporary file with the name format “$RECYCLE+ auto increment+.WNCYRT”(eg:”D:\$RECYCLE\1.WNCRYT”) in the current drive. Especially, if the current drive is a system drive (eg: C Drive), it will use the temporary directory of the system.
Afterwards, the process will launch taskdl.exe and delete temporary files with fixed time interval.
Chapter 3 Feasibility of Data Recovery
In the analysis of the its execution logics, we noticed that the Worm would overwrite files that meet the pre-set requirements with random numbers or 0x55 so as to destroy the file structures and prevent it from being restored. But this operation is only adopted on specific files or files with specific extension. This means there are still plenty of files that haven’t been rewritten which leaves room for file recovery.
In the deletion process, the Worm moved the original files to the the temporary file folder by calling function MoveFileEx. The temporary files are deleted in bulk in the end. During the above process, the original files might be changed, but current data recovery software on the market is not aware of this so that quite an amount of files cannot be recovered successfully. Victims file recovery needs are hardly meet.
For other files, the Worm simply executed “move & delete” command. Because the processes of file deletion and file movement are separate, so these two threads will compete with each other which may result in the failure of file movement due to the difference in user’s system environment. As a result, the file will be deleted directly in the current location. Under this circumstance, there is big chance that the file can be recovered.
By using our recovery techniques, a great percentage of encrypted files can be restored perfectly. Now the updated version 360 File Recovery has been developed in response to this need to help tens of thousands victims to mitigate the losses and impact: https://360totalsecurity.com/s/ransomrecovery/
On May14th, 360 is the first security vendor that released the file recovery tool which has been saving back numerous files from the ransomeware. This new version took one step further in exploiting the logic vulnerabilities of WanaCrypt0r. It can remove the virus to prevent further infection. By making use of multiple algorithms, it can find the hidden connections among restorable files and decrypt the files for customers for free. This one-stop recovery service can mitigate the damage of ransomware and protect users’ data security .
Chapter 4 Conclusion
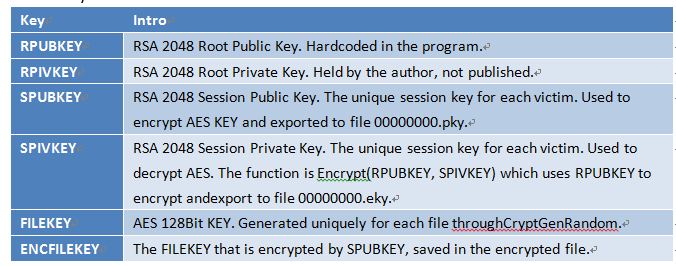
The massive outbreak and spread of Worm WannaCry benefits from the exploit of MS17-010 which makes it obtains the ability of self-replication and active spread besides the features of common ransomware. If not considering the attack payload, the technical framework of ransomware plays the most important role in the attacks. Ransomware encrypts the AES key through asymmetric cryptographic algorithm RSA-2048. Then each file is encrypted by using a random AES-128 symmetric encryption algorithm. With that said, relying on existing computing and techniques, it means to decrypt RSA-2048 and AES-128 without any public or private keys is almost impossible. However, the authors leaves some bugs in the encryption process, which provides and increases that chances to the recovery. If actions are taken promptly enough, most data can be saved back.
In addition, because the ransom money is paid in anonymous bitcoins for which anybody can get the address without real-name certification, it’s impossible to identify the attacker through the addresses, not to mention, there is even no connection among different accounts of the same address owner. Therefore, due to the adoption of unbreakable encryption algorithm and anonymous bitcoins, it is very likely that this kind of profitable ransomware outbreak will continue for a long time. Everybody should still be cautious.
360 Helios Team
360 Helios Team is the APT (Advanced Persistent Attack) research and analysis team in Qihoo 360.
The team is dedicated in APT attack investigation, threat incident response and underground economy industrial chain studies.
Since the establishment in December, 2014, the team has successfully integrated 360’s big data base and built up a quick reversing and correlation procedure. So far, more than 30 APT and underground economy groups have been discovered and revealed.
360 Helios also provides threat intelligence assessment and response solutions for enterprises.
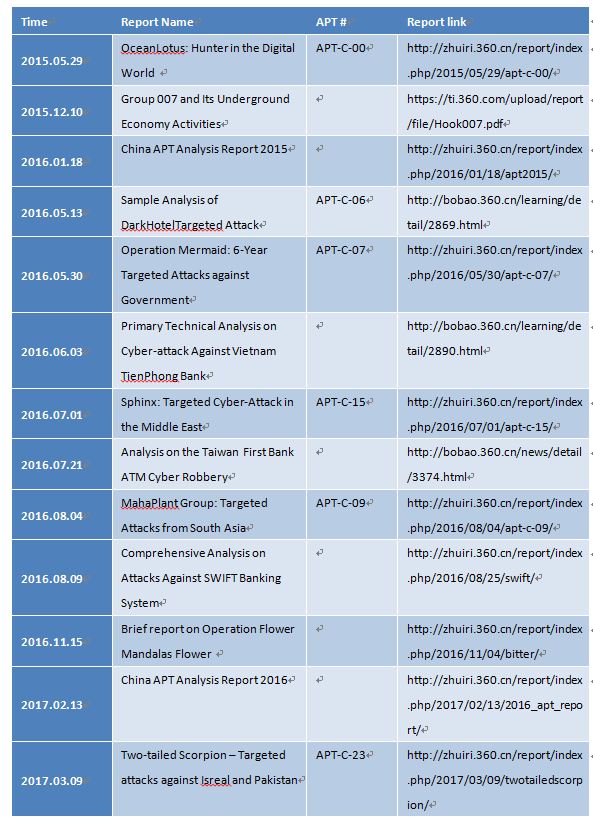
Public reports
Contact
Email: 360zhuiri@360.cn
WeChat: 360 Helios Team
Please scan the QR code below to follow us on WeChat!
Learn more about 360 Total Security