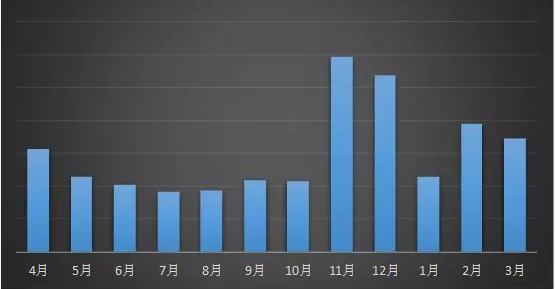
According to the monitoring of 360 Brain of Safety, the overall attack trend of Ransomware in March is relatively stable. There is no new large-scale spreading channels. The top three target infection systems are Windows. 7, Windows Server 2008 and Windows 10. The feedback volume of anti-ransomware services has also dropped slightly, but the new Paradise ransomware has a large feedback, which requires special attention.
Figure 1. Ransomware feedback statistics for the past 12 months
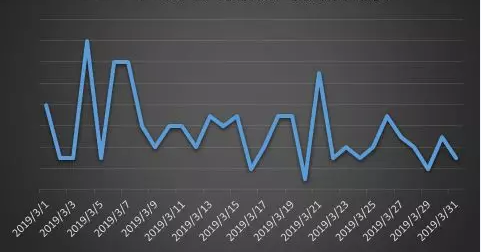
There were three feedback peaks in this month, two of them occurrences at the beginning of the month. There are two main reasons: one is that the Satan ransomware updated its version of the ransomware in early March; and the other is that the situation of the GandCrab ransomware spread in the hang-troy website is still outstanding in early March. The third peak of feedback occurred on March 21, mainly because the two new ransomware Paradise and immortallock began to spread in China.
Figure 2. Feedback trend of ransomware in March 2019
Ransomware Never Stop
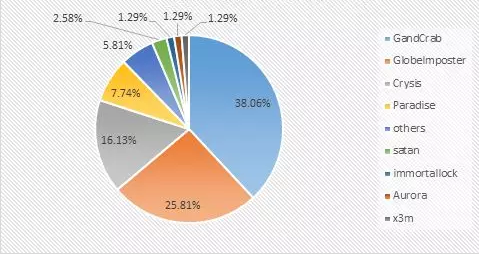
An analysis of the proportion of the ransomware family this month found that the GandCrab ransomware family still accounted for the highest proportion of all ransomware families – up to 38.06%, but decreased by 8.5% compared with February, GlobeImposter ransomware family followed by 25.10% and 16.13% of the Crysis ransom family. In addition, it is worth mentioning that the proportion of new ransomware Paradise (7.74%) in the second half of this month directly jumped to fourth place.
Figure 3. Ransomware feedback distribution map for March 2019
GandCrab Ransomware
The GandCrab ransomware, which ranked the first place this month, the three main modes of transmission as follows:
- The NO.1 is spreading by troy-hang website;
- Then by blasting the remote desktop, then manually poisoning;
- Finally, by sending a phishing email, the user is induced to download and run an email attachment with a ransomware to infect the user’s system.
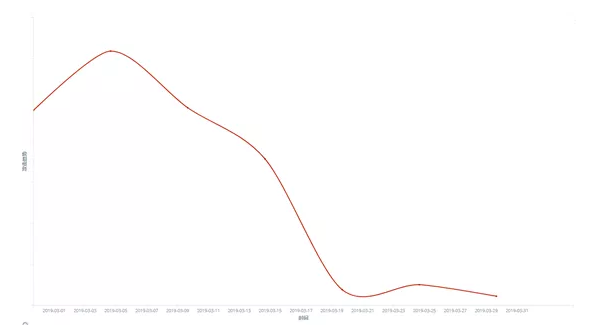
- The website with troy is mainly to attack by using the Fallout Exploit Kit exploit tool that is publicly sold on the dark network. 360 Brain of Safety monitored it and found that GandCrab’s interception volume rose sharply on 17th March, but did not substantially cause a large-scale infection.
Figure 4. The situation map of GandCrab spreading through the vulnerability
Satan Ransomware
The Satan ransomware was updated several times in March, and on 1st March, the attacker had significantly increased its attack volume to spread its latest variant. The 360 decryption master also decrypted its latest variant (suffixed with evopro). Subsequently, the ransomware author also added the appro and satan_pro suffixes, and 360 decryption master also followed up the support at the first time.
Figure 5. Satan Ransomware Spreading situation
Paradise Ransomware
The Paradise ransomware is the most infective of the new ransomware (the virus was briefly seen in 2018, mainly by blasting remote desktop passwords, followed by manual poisoning). The remind information generated by the ransomware and the encrypted file name format are all simulated Crysis ransomware; while the channel of spread imitates the GandCrab ransomware channel, which is spread by purchasing the Fallout Exploit Kit vulnerability tool on the dark network.
It is worth noting that there are four variants of this ransomware have appeared only in this month (modified suffixes are .exploit, .p3rf0rm4, .paradise, .pro). According to current variant speeds and means of spread, Paradise ransomware may become one of the fastest growing ransomware in the coming months.
Figure 6. Paradise ransomware alert message
CRYPTED Ransomware
On March 27th, 360 Brain of Safety detected that hackers had launched the new ransomware “CRYPTED!” with the “WinRAR Remote Code Execution Vulnerability CVE-2018-20250” through fake seed resources, attacking hundreds of domestic computers.
Figure 7. CRYPTED! ransomware alert message
The hacker chooses the faster TEA encryption algorithm, and the original key is stored in the form of resources in the ransomware. After the ransomware extracts the original key, the original key is XORed with the first character of the encrypted file name to form an encryption key unique to each file, encrypting the contents of the file, and extorting the victim 0.1 ransom of bitcoin.
However, users don’t need to worry about it, the 360 decryption tool has supported the decryption of the virus, users can download and install 360 Total Security to use 360 decryption tool to recover the encrypted documents.
GlobeImposter Ransomware
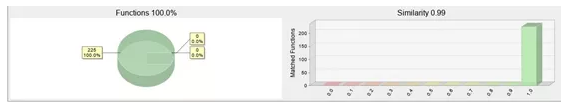
Besides, 360 Brain of Safety monitor that the GlobeImposter ransomware released a new variant “auchentoshan” this month, the variant only modified on the encrypted file suffix and extortion prompt information, the code is 99% similar with the previous version, the mode of spreading is still by blasting the remote desktop, and manually injecting the password after getting the password.
Figure 8. the similarity graph of GlobeImposter latest variant and old version code
Avoid weak password attacks with complex login passwords
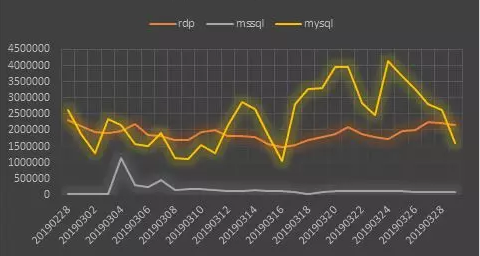
In addition, through the statistical analysis of the weak password attack data monitored by 360 Brain of Safety, it is found that the overall trend of MySQL weak password attack has a great ups and downs, and MYSQL weak password attack has become the most popular object of hackers. The RDP (Remote Desktop) weak password attack trend is relatively stable. Combined with the spread of ransomware, 360 Brain of Safety recommend that users use complex computer passwords, install 360 Total Security and turn on system protection to protect personal privacy and property security.
The ransomware attack against the server is still a major direction of the current ransomware. Enterprises need to strengthen their information security management capabilities—especially weak passwords, vulnerabilities, file sharing, and remote desktop management to deal with the threat of ransomware. Here we give the administrator some advice:
- Multiple machines, don’t use the same account and password
- The login password must be of sufficient length and complexity, and the login password should be changed periodically.
- The shared folder of important information should be set to access control and be backed up regularly.
- Regularly detect security vulnerabilities in systems and software and patch them in time.
- Check the server periodically to see if there is an exception. View range includes:
- a) If there are new account;
- b) If the guest is enabled;
- c) if there is any abnormality in the Windows system log;
- d) Whether the anti-virus software has abnormal interception
For ransomware that attacks on personal computers, it is recommended that users:
- Go to http://www.360totalsecurity.com/, download and install 360 Total Security to intercept all kinds of ransomware attacks;
- Download the installation software from official channel.
- For unfamiliar software, if it has been intercepted by anti-virus software, don’t add trust to continue running.