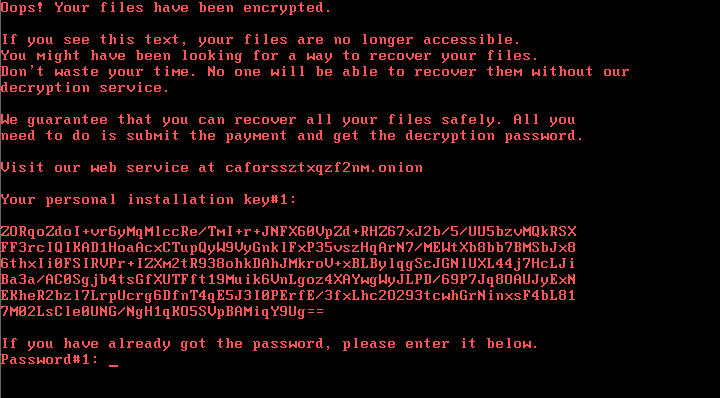
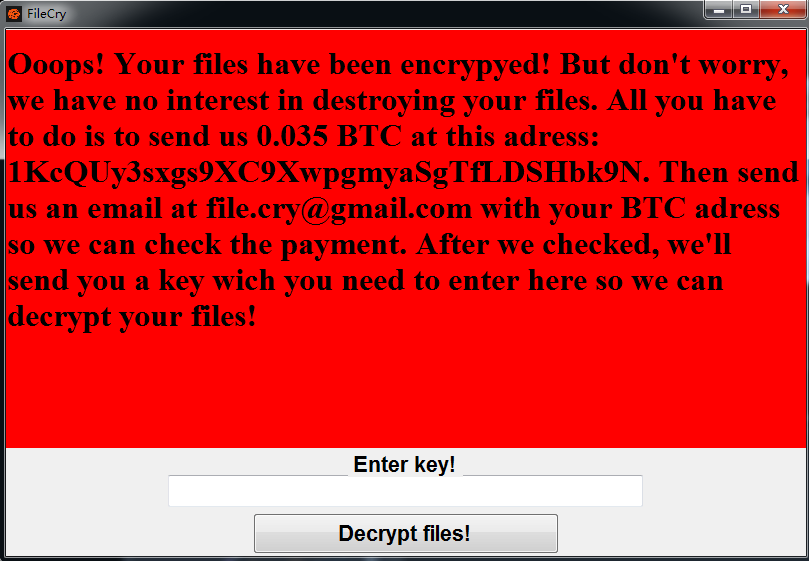
A Trojan Horse, or Trojan, is a type of malware that masquerades itself as a useful, routine or innocuous program and trick the victim to install it. Its name is derived from the well-known ancient Greek story, in which Greeks send a large wooden horse to Trojans as a symbol of peace. Yet this gift turns out to be a hiding place for Greek troops that soon attack Troy in the night.
Trojans affects your PC undetected
Since Trojans must be invited to one’s PC before being able to execute their payload, they are usually packaged as harmless or interesting programs like an e-mail attachment or a PC game. Also, attackers may insert a snippet of malicious code to a seeming legitimate program, which thus has some harmful functions hidden to the user. Hence, users tend to download and install Trojan programs unwittingly.
Once installed, Trojan creates a backdoor on victims’ PC, thus allowing hackers to gain unauthorized access to their sensitive information. Other use with sinister purposes could include, but are not limited to turn on victim’s microphone or webcam secretly, use their e-mail to send spams, or even take their PC for illegal files traffic and storage.
Despite Trojan computer programs are wrapped as unsuspicious ones and hard to be detected, there are still some indicators of their presence. Trojans may slow down victims’ PC and even force software to quit unexpectedly due to heavy network usage.
How to keep myself safe?
To keep Trojans away from affecting one’s PC, one should always be careful when opening email attachments and softwares from untrusted website. Also, there are some tools you can utilize to avoid Trojan horse programs:
1. A firewall helps detecting this issue. As a barrier set between outside Internet and your PC, a firewall monitors if there are unusual Internet activities and restricts unauthorized access from unknown users.
2. An up-to-date anti-virus software recognizes Trojans and alerts users. Internet users are suggested to deploy multi virus scanners(multi security engines), so as to detect a larger percentage of known Trojans.
In conclusion, Trojans enter victims’ computer undetected and then spy or steal private information from them. Users usually download these wrapped programs via channels like websites or email attachments. Thereby, it is suggested for users not only be careful when downloading files but also employ a security software on their PC.
Learn more about 360 Total Security