by 360 Core Security
Background
On June 1, 2018, the Advanced Threat Response Team of 360 Core Security (@360CoreSec) discovered an attack using a new Flash 0-day vulnerability on a global scale. The hackers carefully constructed an Office document that remotely loaded Flash vulnerability. When the document was opened, all the exploit code and malicious payload were delivered through remote servers. This attack mainly targets the Middle East. This vulnerability is the second Flash 0-day vulnerability discovered in 2018 and is currently affecting Adobe Flash Player 29.0.0.171 and below versions.
Vulnerability Analysis
The sample has a very appealing file name: ***_salary.xlsx (*** salary), whose content is also consistent with the title. The file is in Arabic and shows salaries for various time periods.
The content of ***_salary.xlsx (MD5: ******517277fb0dbb4bbf724245e663) is complete, but here we only revealed a part of it:
The hacker embeds a remote Flash file link through the ActiveX control and data. The related exploit code is controlled and delivered by the remote server.
Attack Procedure
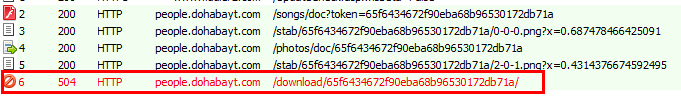
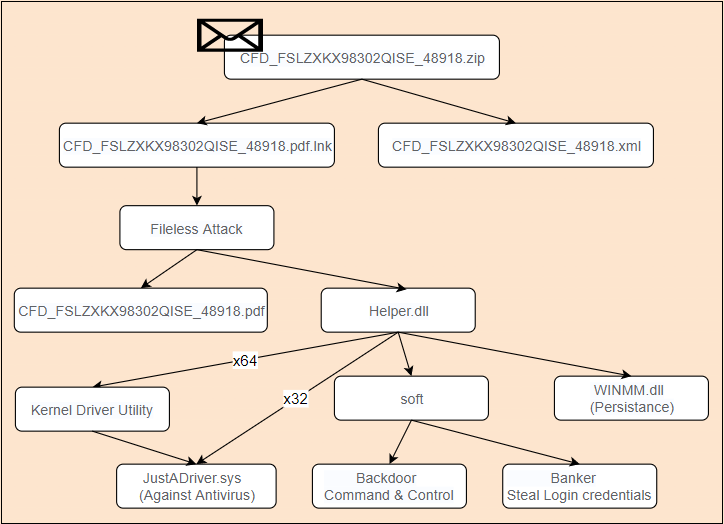
After running the xlsx, the malicious SWF (Shock Wave File) file (MD5: ******66491a5c5cd7423849f32b58f5) is downloaded from the remote C&C server (C&C:people.doha****.com) for execution. The SWF file will request the server again to download encrypted data and decryption keys. The decrypted SWF (md5: ******e78116bebfa1780736d343c9eb) is the Flash 0day exploit. After the vulnerability is triggered, it requests the remote server to download a malicious shell and execute it. During the real-time analysis, we found that the attacker had closed Trojan payload which is expected to be delivered in the final phase.
The following picture shows different phases of the attack:
Vulnerability Root Cause Analysis
The vulnerability Flash code is highly obfuscated. After debugging and analysis, we located the 0-day vulnerability code in the attack sample.
After the restoration of the main code is as follows:
Flash will use the interpreter to handle Static-init methods. The interpreter handles the try catch statement does not correctly handle the exception, and this will make li8 (123456) instruction caught by the catch block when it triggers the exception.
Because Flash assumes that it is impossible to execute to the catch block when processing the try catch statement, it does not check the bytecode in the catch block. The attacker uses the getlocal, setlocal instruction in the catch block to read and write arbitrary addresses on the stack.
In this wild used 0 day, the attacker switches the vulnerability to a type obfuscation problem by exchanging two object pointers on the stack and finally completes the attack.
To further debug the attack code, we can see that the localcount of function in the exploited bytecode is 2, while in the catch block getlocal, setlocal has manipulated the data at locations 448 and 498.
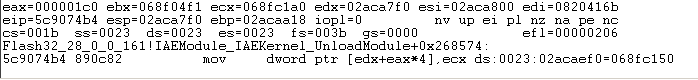
Let’s observe setlocal operation stack data. The value of ecx is the pointer of the class5 object, and 068fc1a0 is the pointer of class7.
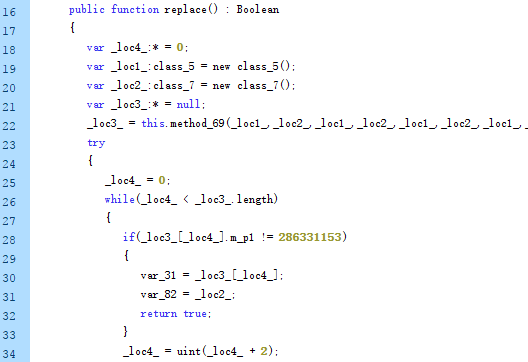
After exchanging the pointers of two objects, the attacker checks whether the exploited is successful by comparing the values of the object members.
Correlation
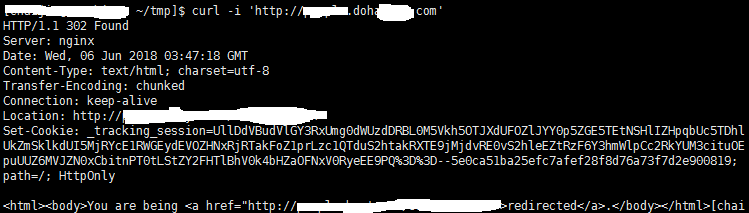
The C&C for the vulnerability attack is people.doha***.com, and the corresponding IP address is **.145.128.57 (Netherlands). The WHOIS information from this domain name shows that the domain registration time is 2018-02-18, indicating that the attacker started preparing for the attack in February this year.
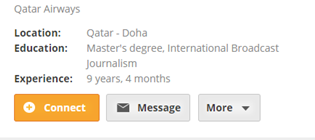
When directly access to people.doha***.com, the visits will be forced redirected to https://people.***.com/sushasolomon/, a Qatar Airways staff introduction homepage.
People.***.com is a job search site in the Middle East. The C&C used by the attackers just has one more doha (Doha). It was obvious that there was an intention of disguising the domain name for phishing. Therefore, we boldly suspected that the targeted region is Doha, Qatar.
Conclusion
Through analysis, we can see that the attack used a 0-day vulnerability regardless of the cost. The attacker developed sophisticated plans in the cloud and spent at least three months preparing for the attack. The detailed phishing attack content was also tailored to the attack target. All clues show this is a typical APT attack. We suggest all relevant organizations and users to update their Flash to the latest versions in a timely manner. We also strongly recommend using 360 SafeGuard to protect your devices against possible threats.
Learn more about 360 Total Security