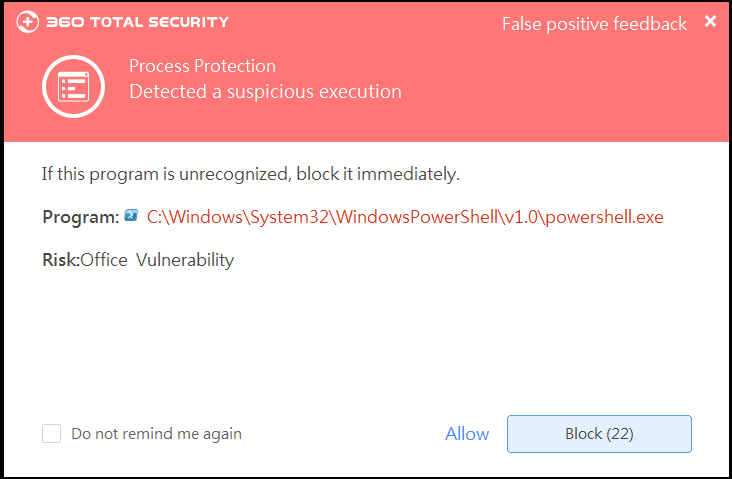
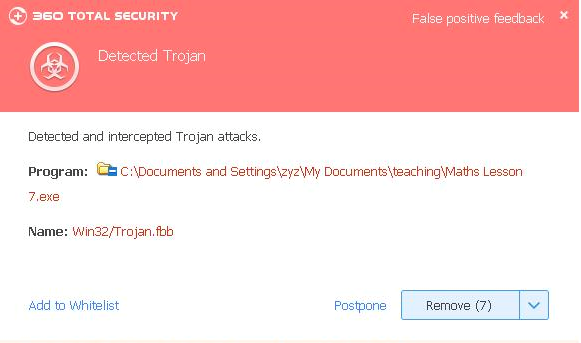
On 9th May, Microsoft has published its May security updates, including the high risk vulnerability, Double Kill. This vulnerability affects all latest Microsoft’s Internet Explorer and any applications using IE browser engine to render web pages. Security experts in 360 also found that it has been abused by a well-plotted APT attack in the wild.
Being the first software vendor that discovered the vulnerability, 360 has made a huge effort into the detection and defense of related attacks. We also help distribute the security updates. Microsoft has publicly thanked the contribution of 360 during the release of security updates. This is the 263th recognition 360 received from Microsoft.
Under the hood, hackers initiate the attack by embedding a malicious website inside an Office document. Any malicious code and payload can be deployed via remote web servers. This attack also uses a known UAC bypassing technique to acquire administrator’s privileges. Its in-memory execution methodology leaves no disk footprint and avoids traffic tracking.
In recent years, we have discovered a rising trend that Office documents have taken the center stage of APT attacks. Opening any malicious documents with “Double Kill” allows attackers to control victims’ computers without their knowledge, making ransomware infection, eavesdropping and data leakage convenient and stealthy.
360 Security Center would like to remind all users to apply the updates as soon as possible. Organizations and governments should be cautious on any attack that may abuse this exploit.
Learn more about 360 Total Security