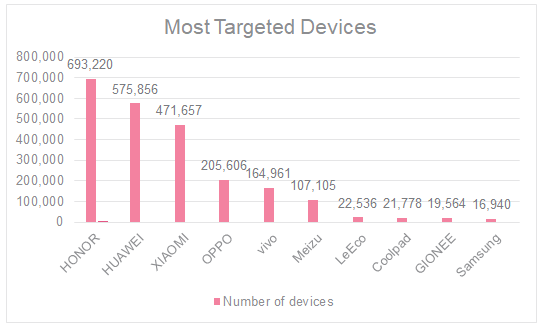
Recently, an Android malware called “RottenSys” was discovered by a security company, Check Point. It is an Adware that disguises itself as a Wi-Fi management tool, and gains money by displaying aggressive Ads. 5 million smartphones made by Samsung, Huawei, Honor, Xiaomi, OPPO, Vivo and GIONEE have been infected globally.
After further analysis, 360 Security Center confirmed that the malware was distributed by an outsourcing mobile phone supply chain company “Tian Pai” in China. Millions of Smartphones were pre-loaded with the malicious app before they got to the customers so the distributors could benefit from the aggressive ads displayed on infected phones. According to security experts, these unwelcome ads popped up over 13 million times and generated 548,822 profitable clicks within 10 days. RottenSys not only irritates smart phone users, but also significantly affects phone performance and battery life.
How RottenSys affected 5 million devices and stay unnoticed
1. The malware disguises as a system service process to deceive general users.
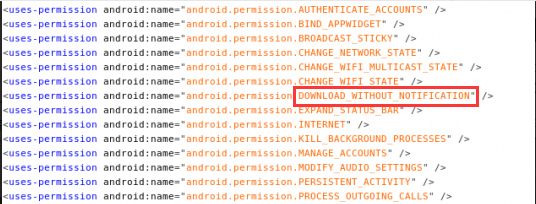
2. It lures users into confirming a long list of permissions, including sensitive ones such as “download without notification” so users will not be aware of the future updates of the malicious program.
3. This malware is able to remain persistent by equipping the ability to re-activate itself after reboot.
4. By intentionally delaying the display of the ads, users cannot easily link the ads to the malware.
5. The update server in the cloud allows attackers to dynamically add new modules to the app, changing the display policy of ads on demand.
To remove this malware, go to the App manager and uninstall the following malware packages if any exist:
- android.yellowcalendarz
- changmi.launcher
- android.services.securewifi
- system.service.zdsgt