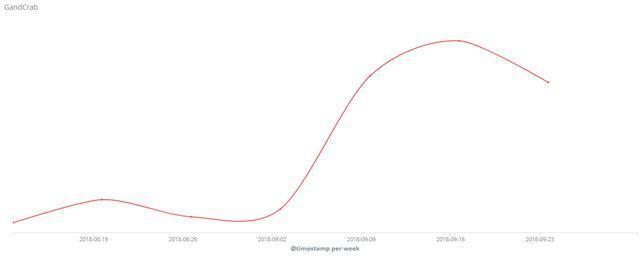
GandCrab ransomware is one of the most popular ransomware families recently. The latest version of the ransomware has been updated to 5.0.1. In September, 360 Security Center found that the spread of GandCrab ransomware began to grow rapidly that many files on Windows servers were encrypted. The ransomware is currently spreading through several known vulnerabilities, including Fallout Exploit tool which was added in September.
How is GrandCrab spread?
Currently, GrandCrab is commonly spread through the following methods:
1. Disguise itself as normal software or be bundled in cracked software to induce users to download
2. Crack weak passwords
3. Use Apache Tomcat exploit
4. Use Jboss and WebLogic server flaws
5. Exploit Struts vulnerability
The latest changes in the GrandCrab sample
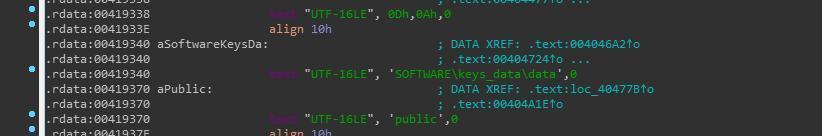
The latest version of the ransomware randomly generates a string of 5 characters in length as the file suffix and write the suffix to the SOFTWAREkeys_datadata registry, instead of using a fixed suffix:
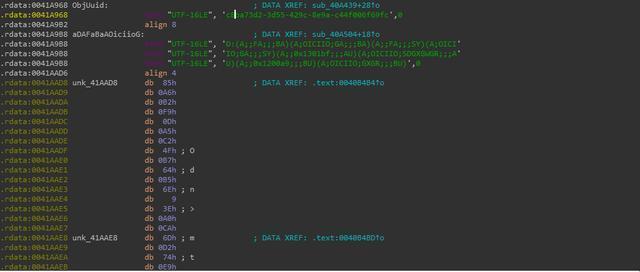
Newly increased the use of Windows 10 privilege vulnerability (CVE-2018-0896):
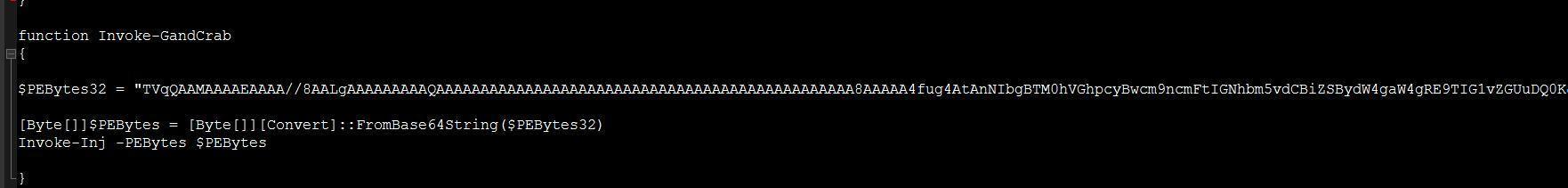
Newly added PowerShell scripts to perform encryption:
Reminder
The users who use the servers mentioned above should update the software used by the servers to fix security vulnerabilities. Fortunately, 360 Total Security can defend against these kinds of attacks. Hence, we recommend users that they should install 360 Total Security to protect their systems.