Author: 360 Core Security
Author: 360 Core Security
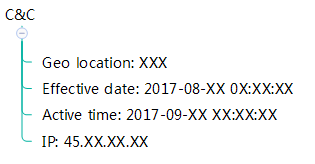
On September 28, 2017, Qihoo 360 Core Security (@360CoreSec) detected an in-the-wild attack that leveraged CVE-2017-11826, an Office 0day vulnerability. This vulnerability exists in all the supported Office versions. The attack only targeted limited customers. The attacker embedded malicious .docx in the RTF files. Through reversing analysis of the sample C&C, we found that the attack was initiated in August and the launch date of the attack can be dated back to September. It was in this time window that the vulnerability has been exploited as a 0day.
Qihoo 360 Core Security has been the first security vendor to share the details of the vulnerability and coordinated with Microsoft to disclose the news, as well as a timely patch to resolve the Office 0day vulnerability in a week.
The latest version of 360 Total Security products could detect and prevent exploitation of this vulnerability. In the meanwhile, we also highly suggest users to update Microsoft Patch in time.
The In-the-Wild Attack
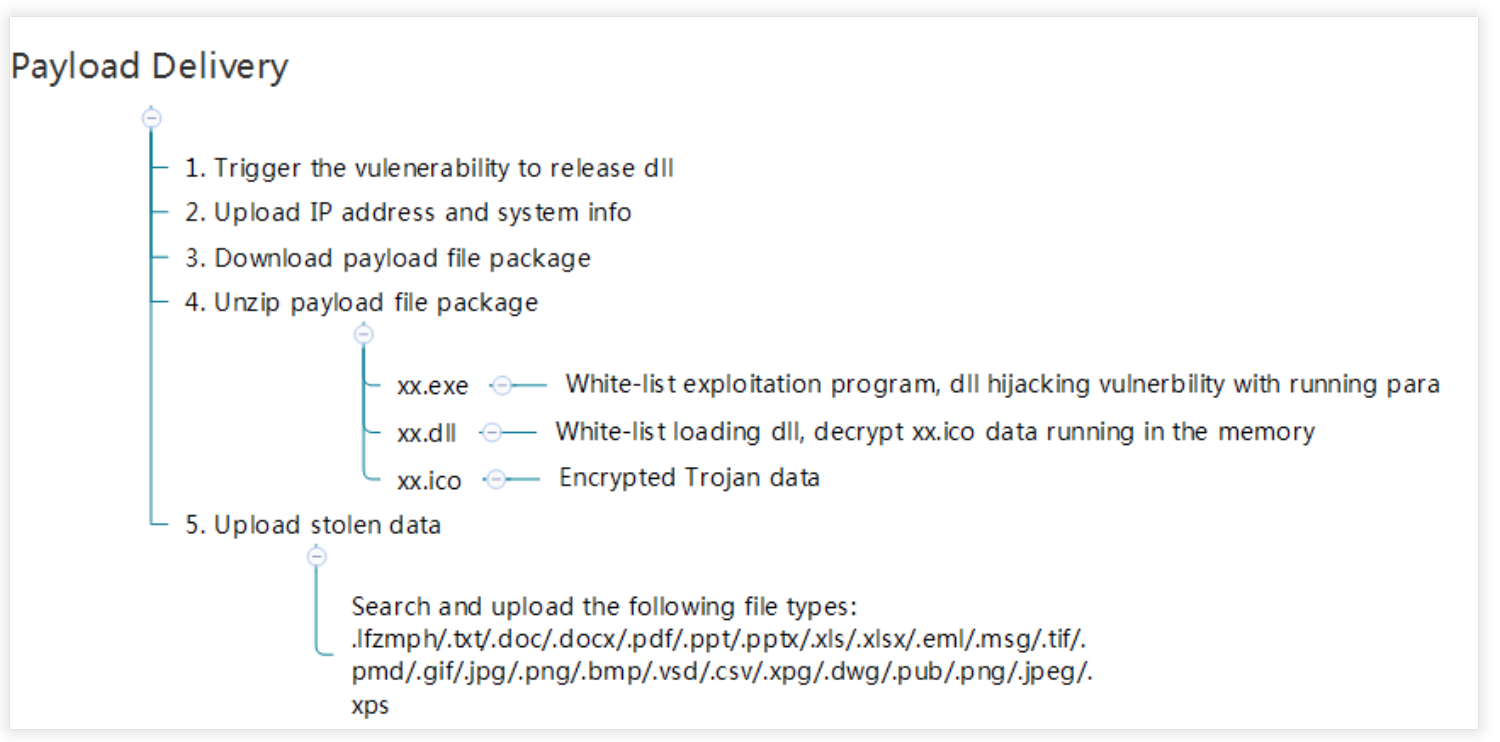
This attack that Qihoo 360 detected in the wild is initiated with RTF (Rich Text Format) files. The RTF file contains highly targeted phishing subfiles to allure user to open. The attacker triggered a remote arbitrary code execution by using Microsoft Word tags and corresponding attributions. The payload delivery is showed in the below procedure. In this process, the execution code took advantage of a dll hijack vulnerability from a well-known security software. Afterwards, a remote Trojan aiming at stealing sensitive data was installed in the victims’ devices.
Summary & Security Advice
Upon the detection of this 0day vulnerability, 360 has released a hot patch which is available in the latest updates. It enables 360 users to avoid attacks exploiting this new Office vulnerability before Patch Tuesday. Attacks using Office 0day vulnerabilities targeting common users have been increasing since the beginning of 2017.
We would like to send a kind reminder to all users that please do not to open any unknown Office files. Organizations and enterprises should also be aware of this new 0day and be more cautious of related malicious behaviors. It is also highly recommended to update your 360 Total Security software to protect your devices against any potential attacks.
Acknowledgement
Thanks to Yang Kang, Ding Maoyin, Song Shenlei, Qihoo 360 Core Security and Microsoft Active Protections Program (MAPP) for their contributions to this blog. We also thank everyone from the Microsoft Security Response Center (MSRC) who worked with us in resolving this issue.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11826
Learn more about 360 Total Security