The latest Office 365 phishing attack uses a special method to store phishing forms hosted on Azure Blob storage for protection with Microsoft SSL certificates.
Azure Blob Storage is a Microsoft storage solution for storing unstructured data such as images, video or text. One advantage of Azure Blob storage is that it can be accessed using HTTP and HTTPS, and when signed over HTTPS, a signed SSL certificate from Microsoft will be displayed. By storing the phishing form in Azure Blob storage, the displayed form will be signed by Microsoft’s SSL certificate. This makes it an ideal way to create phishing forms for Microsoft services such as Office 365, Azure AD or other Microsoft logins.
Phishing attacks use Azure blob storage to simulate Microsoft
Using Azure Blob Storage to host phishing forms is the type of attack cloud security provider Netskope that was recently discovered. In this attack, some criminals sent spam with PDF attachments, which were disguised as documents of a law firm in Denver. The file name displayed “Scan files…, please review” and attached the Download button.
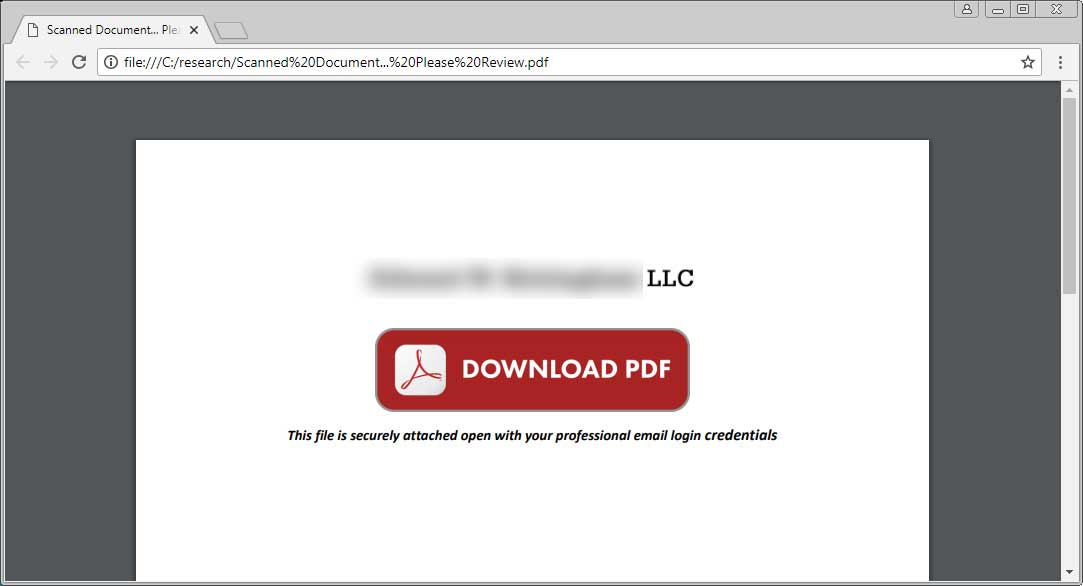
When the user clicks on this link, they will be taken to an HTML page that appears to be the Office 365 login form stored in the Microsoft Azure Blob storage solution. It should be noted that how does the URL https://onedriveunbound80343.blob.core.windows.net indicate that it is a blob. Since this page is also hosted on Microsoft services, it also has the “reputation” of secure SSL sites.
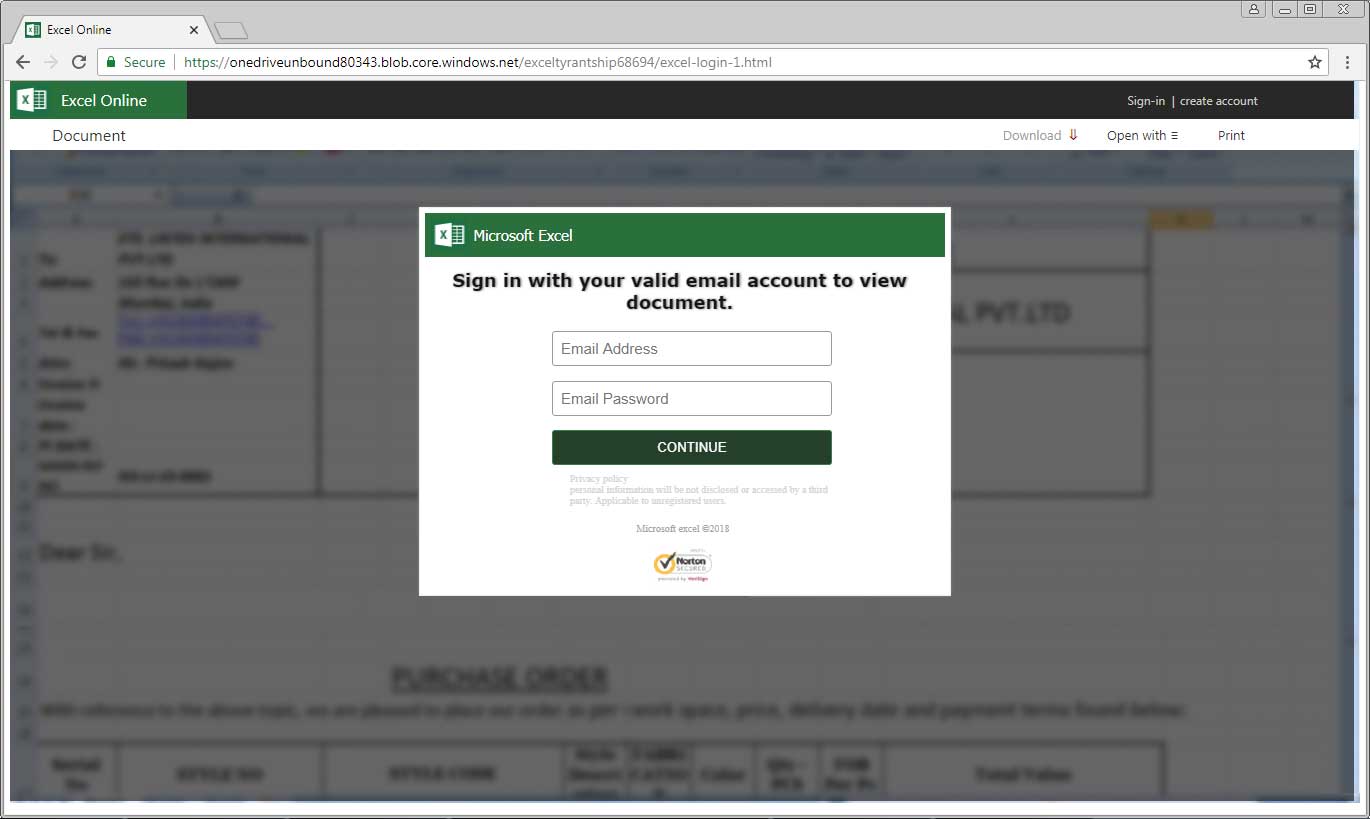
If the user is suspicious of the URL and chooses to view the certificate, he/she will see the SSL certificate signature issued by Microsoft IT TLS CA 5.
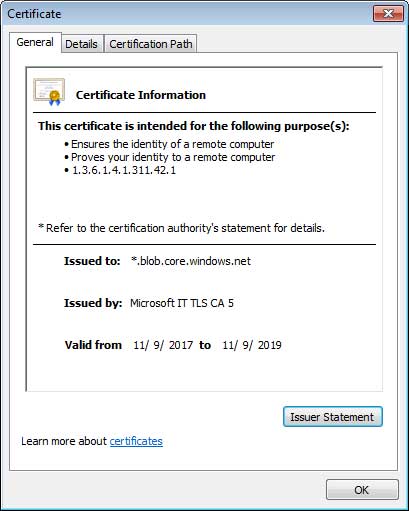
Although this is a fake login page, the site uses Microsoft SSL certificates for security, and many people may believe this is a legitimate login form. Once the user enters the information, the form submits the content to the server that the attacker is manipulating. After submitting the form, the page will pretend to prepare the document for download and eventually redirect the user to https://products.office.com/en-us/sharepoint/collaboration Microsoft site.
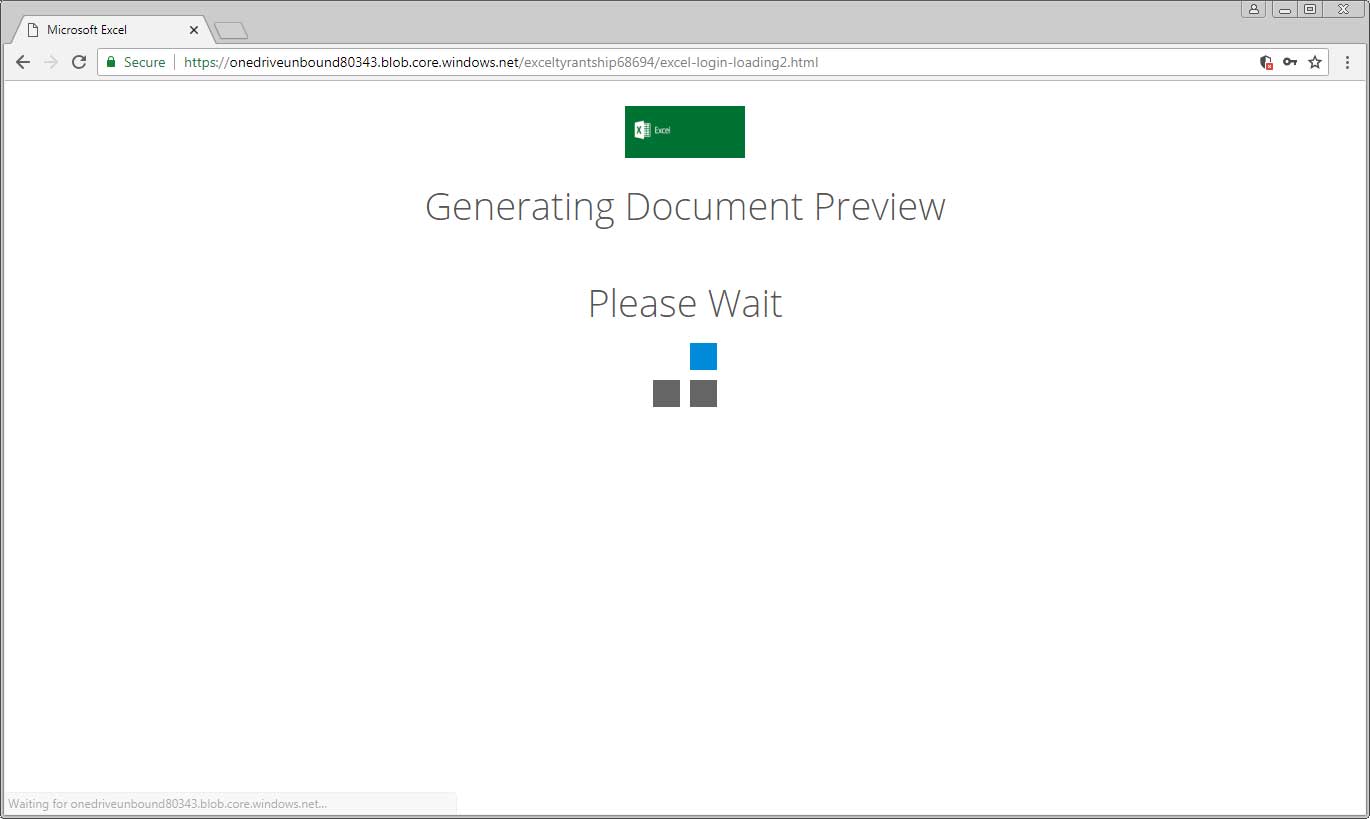
While users who have more experiences may not be convinced of attacks because of camouflaged URLs, most ordinary users are still easily hooked. In their concept, using a certificate from Microsoft means security.
To protect users from these evolving threats, Netskope recommends that companies should correctly educate users about non-standard web addresses. “Companies should popularize how to identify AWS, Azure and GCP objects to store URLs so they can identify phishing sites from the official website.”
Learn more about 360 Total Security