Introduction
Windows Activator has been a popular tool for attackers to spread Trojan viruses. Recently, 360 Security Center found a new kind of ransomware, which was spread by disguising as a Windows Activator. Through our precise analysis, we found this ransomware has a hidden configuration function, which can view and modify the key and prompt information used for encryption, and also obtain key decryption through this interface.
Virus Transmission
Figure 1: The Activator bundled with ransomware
Trojans are bundled in the Windows Activator and spread through some foreign network disks. The ransomware first appeared on August 7th and has been spreading since then. Although the Trojan itself has been intercepted by security software, it is still being used by users.
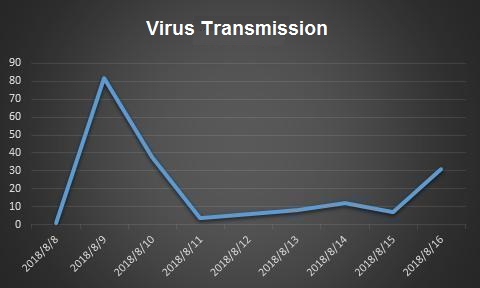
Figure 2: Virus Transmission
Analysis
We selected one of the Trojan samples for analysis:

Figure 3: Virus sample icon
After the virus was started, it would be started again with parameters to implement different functions.
Different functions are implemented with different parameters:
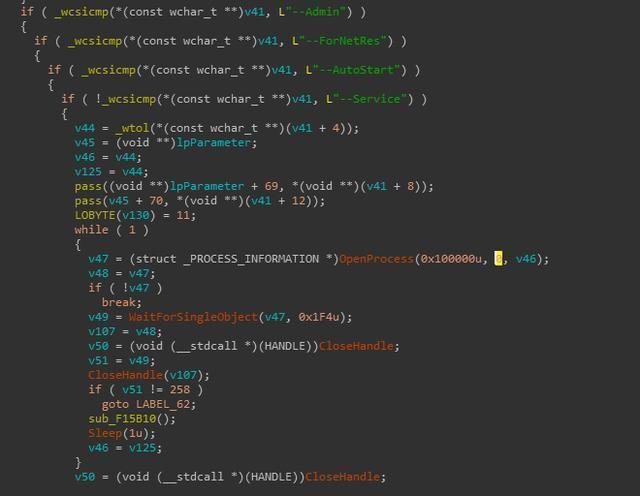
Figure 4: Start the process
Hidden debugging features
During the analysis, we found that the ransomware contains a hidden form that will be displayed after pressing F8. This configuration page allows users to configure the following information (obviously this is a debugging feature that comes with the virus):
* The key of the encrypted file
* The file name of extortion message
* Extortion message
* User’s personal id
* The suffix of the added file
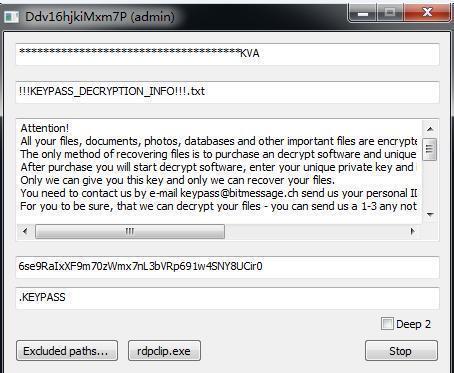
Figure 5: Set up form 1
The attack can also set the file directory which should be skipped. The contents of the dialog below are the default settings.
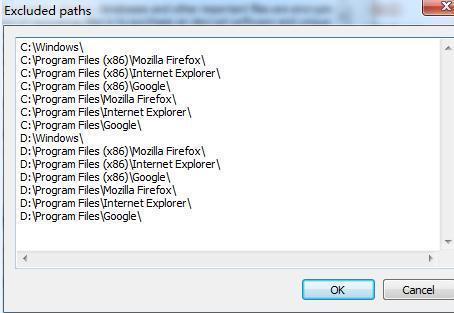
Figure 6: Set up form 2
The figure shows the situation before the file is encrypted:
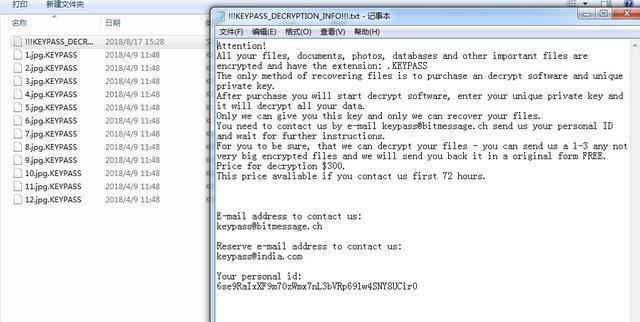
Figure 7: The encrypted file after modifying settings
Meanwhile, when failing to get parameters through cosonar.mcdir.ru/get.php, the ransomware will call the default encryption key and the default user id to the process, and set the form.
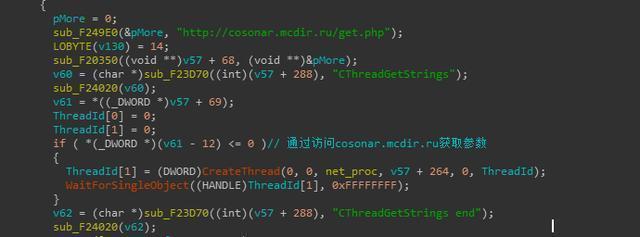
Figure 8: Get the key and id
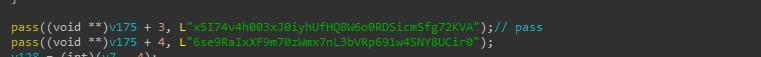
Figure 9. Default key and user id
Document Encryption
When making a ransomware virus, the creator is usually used to implement the encryption function by using the Crypto encryption library provided by Microsoft. However, the ransomware uses the open source library of CryptoPP. For file encryption, the virus only processes the first 0x500000 bytes (about 5M) of the file. The oversized files will no longer encrypt the latter part, and then the AES algorithm is called for encryption. These left an opportunity to decrypt the file.
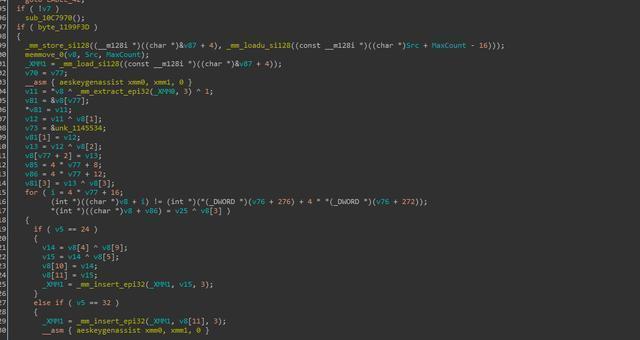
Figure 10: AES algorithm used to encrypt files
Reminder
Disguising as normal software is a common means of spreading Trojan viruses, especially various types of cracking software and plug-in software. When users encounter this type of ransomware, they can protect themselves through the followings methods:
1. Files downloaded from unknown websites must be run with anti-virus software enabled.
2. Protect important files with our “Document Protector” tool.
Figure 11: 360 Document Protector
3. Back up important files regularly.
Learn more about 360 Total Security







