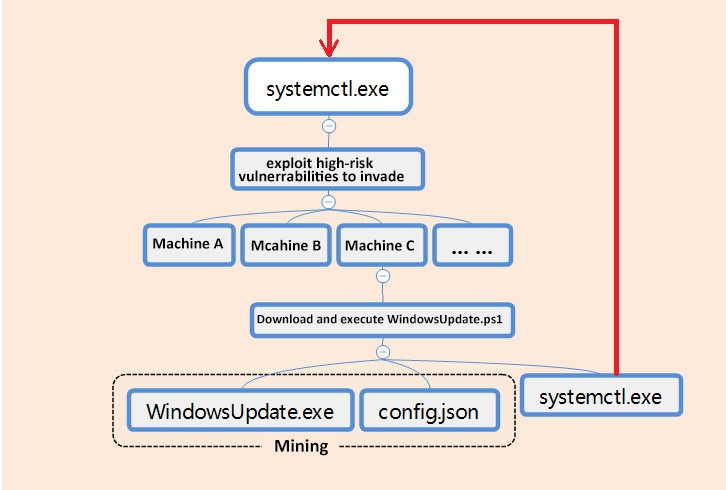
Background
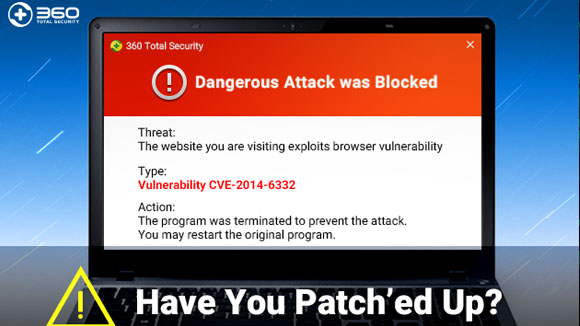
The function exported by the Task Scheduler in Windows 10 does not verify the permission of the caller. The user of any authority can call the function to obtain the write permission of the sensitive file of the system, and then privilege escalation occurs.
The vulnerability affects Windows 10 and Windows Server 2016. The currently released EXP is only available for x64 systems temporarily.
Analysis
The ALPC interface in the Windows 10 system Task Scheduler exports the SchRpcSetSecurity function, which sets a security descriptor for a task or folder.

The task scheduling service is started by svchost.exe (netsvcs), and the corresponding dll is schedsvc.dll.
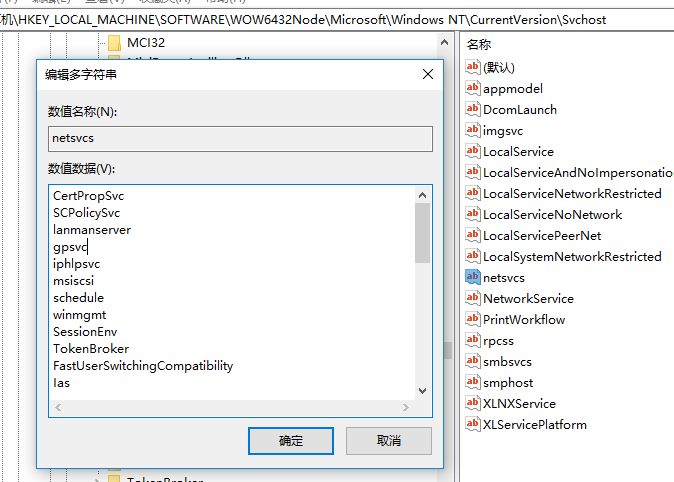
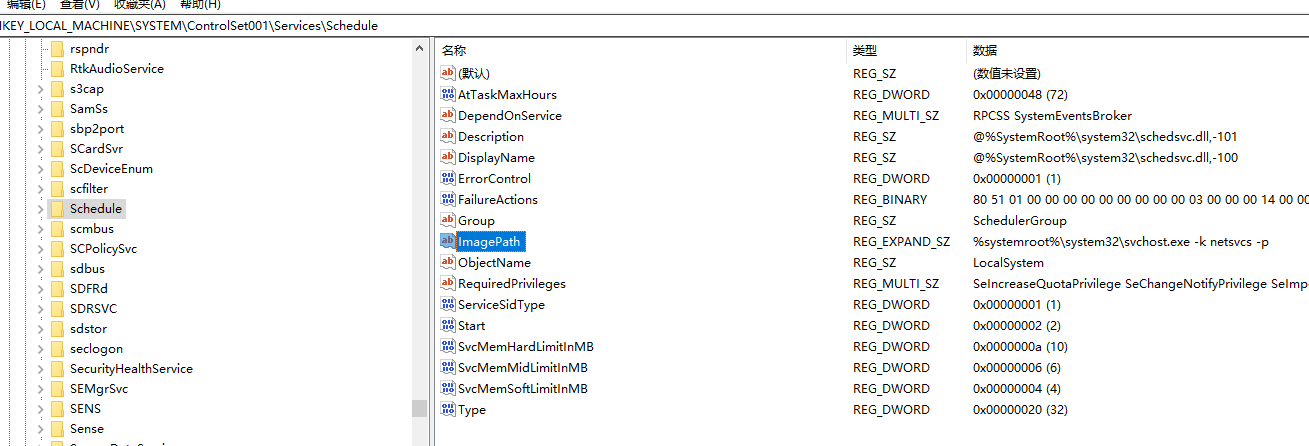
In Windows XP operating system, tasks are stored in C:\Windows\Tasks with the suffix .job. The tasks of Windows 7 and the later versions are stored in the C:\Windows\System32\Tasks in xml format.
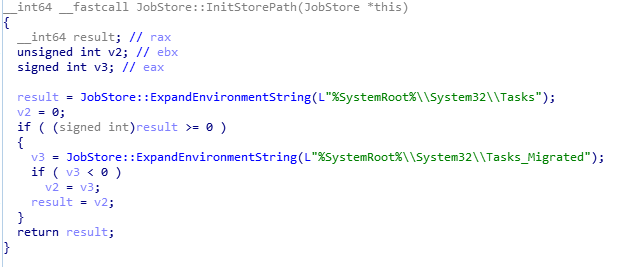
Perhaps for compatibility reasons, the SchRpcSetSecurity function will still detect whether there is a .job file in the C:\Windows\Tasks directory in Windows 10, and write DACL data if it exists. If the job file is hard-linked to a specific dll, then the specific dll will be written to the DACL data. Originally, the normal user only has read access to the specific dll, so that it has write permission, and then writes the exploit code to the dll. And start the corresponding program to get privilege escalation.
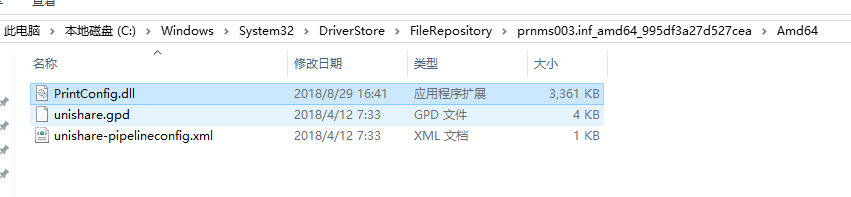
Firstly, find a normal user with read permission and the system has a dll that writes DACL permissions. The EXP uses C:\Windows\System32\DriverStore\FileRepository\prnms003.inf_amd64_4592475aca2acf83\Amd64\printconfig.dll, and then C: \Windows\Tasks\UpdateTask.job hard links to this dll.
After calling the SchRpcSetSecurity function to enable the normal user to successfully obtain the permission to write to the dll, write the exploit.dll in the resource file.
Printconfig.dll is related to system printing and is not started by the print spooler service by default. Hence, call StartXpsPrintJob to start an XPS print.
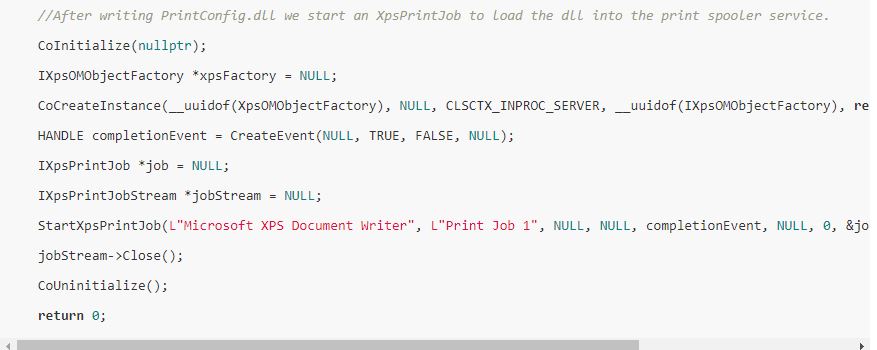
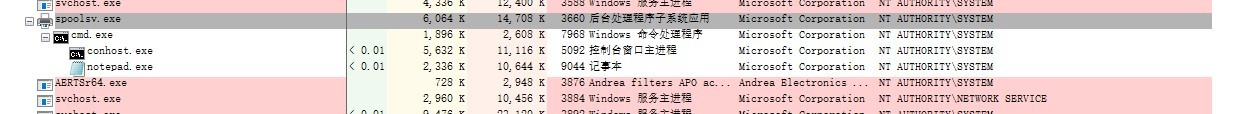
The exploit program is compiled as a dll, which is injected into the notepad. It is found that the notepad created by spoolsv.exe already has the SYSTEM permission, and the printconfig.dll in the system is also modified into the exploit.dll in the resource file.
Reminder
It is recommended that users should install 360 Total Security to defense against attacks. Do not open the programs from unknown sites.