
Speaking of PC security, what comes to your mind? An antivirus that protects you against hackers and malware, or a firewall that monitors your online traffic and blocks suspicious connections? Well, these are common answers. But have you ever heard of a VPN, or Virtual Private Network, which plays an essential role when it comes to information security?
What is a VPN?
If you have ever worked outside the office and needed to access the corporate network, you may already be familiar with this service. A VPN is a private network composed by a group of computers, or discrete networks, across a public network. By establishing a secure and encrypted connection between your device and the VPN server, it does not only protect users’ Internet privacy, but also allows users to bypass restrictive networks and reach data from remote data centres.
How does a VPN work?
An antivirus can do a perfect job keeping scammers and hackers away from your personal information stored on your PC. VPNs can work as an excellent complement to an antivirus, safeguarding your Internet browsing and online communications from eavesdroppers and snoopers.
This service uses tunnelling protocols to create a virtual channel between the VPN server and your computing device. Functioning as a temporary direct session, a VPN then uses a unique encryption key to protect the information transferred. All the traffic exchanged between the two networks within this tunnel is invisible to those who do not have access to the transmitted information. When the shared data reach the receiving the party, the encryption key decrypts the contents and reveals them. Therefore, a Virtual Private Network can protect users’ online privacy, such as credit card and banking information, during the data transmission across public unsecured networks.
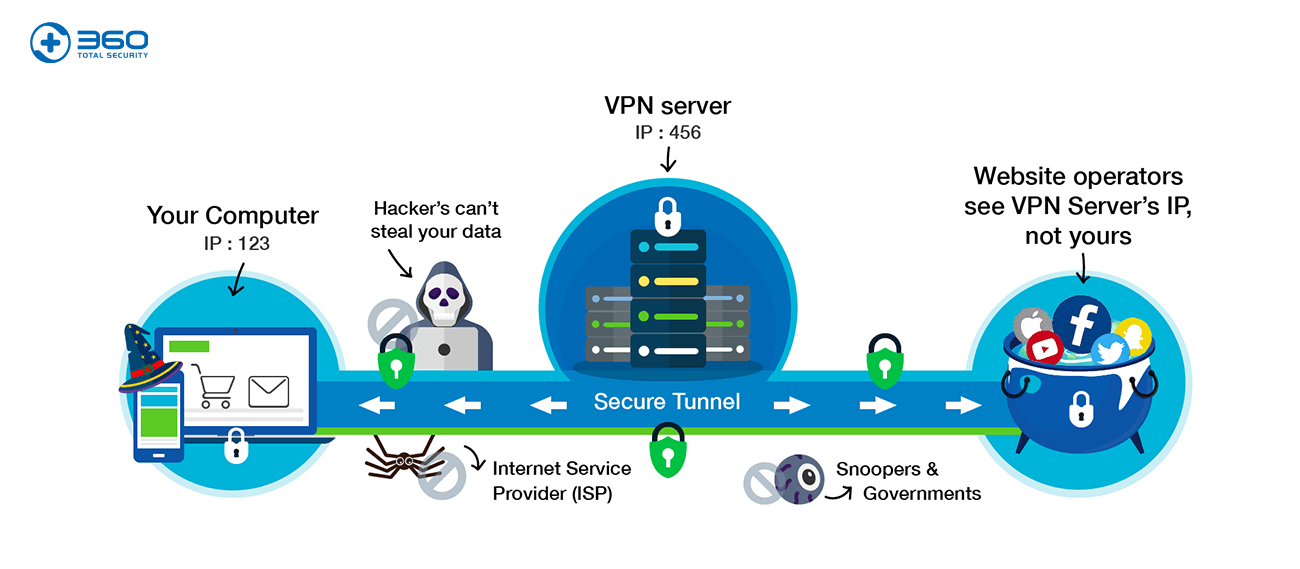
Besides protecting privacy, VPNs also enables users to hide their own IP by replacing it with the VPN server’s IP. By doing so, users can reach geo-restricted sites or blocked contents, since the websites they visit recognize the VPN server’s IP, instead of the users’.
This feature keeps users online anonymity, thus erasing their footprints, so people with malicious intentions, such as hackers or perhaps government, will not be able to track users’ online activities.
Learn more about 360 Total Security







