U.S.-related hacking group launched cyber-attacks against China
Qihoo 360 discovered and revealed cyber-attacks by the CIA hacking group (APT-C-39) which lasts for eleven years against China. Several industry sectors have been targeted including aviation organizations, scientific research institutions, petroleum industry, Internet companies, and government agencies.
The research also shows that a former CIA employee Joshua Adam Schulte was responsible for the research, development and production of cyber weapons. During the group’s attacks against Chinese targets, he was employed at the CIA’s National Clandestine Service (NCS) as a Directorate of Science and Technology (DS&T) Intelligence Officer who directly involved in the development of the cyber weapon – Vault 7. This clue further attributes this APT group’s attack to the CIA.
About the CIA
The Central Intelligence Agency (CIA) is a one of the principal intelligence-gathering agencies of the federal government of the United States. This Langley, Virginia-based agency has four major directorates:
- The Directorate of Intelligence (DI)
- The National Clandestine Service (NCS, also known as the Directorate of Operations (DO))
- The Directorate of Support (DS)
- The Directorate of Science and Technology (DS&T)
Its main services include:
- Collect information from foreign governments, companies and individuals;
- Analyze information and intelligence collected by other U.S. sibling agencies;
- Provide national security intelligence assessments to senior U.S. decision makers;
- Perform or supervise covert activities at the request of the President of the United States.
CIA’s Cyber Arsenal Vault 7 is an Important Breakthrough to the Discovery of APT-C-39
Dating back to 2017, WikiLeaks received a “backup copy” of the hacking materials from Joshua and disclosed 8716 documents from the CIA of the United States, including 156 confidential documents that detailly record the CIA hacking group’s attack methods, targets, tools and technical specifications and requirements. The disclosure contains a hacking tool Vault 7 (code name) which is considered to be the core cyber weapon.
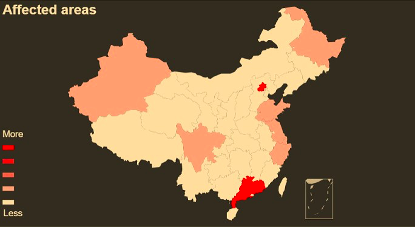
Qihoo 360 analyzed the leaked material of Vault 7 and associated with the team’s researches, it discovered a series of targeted attacks against China’s aviation industry, scientific research institutions, petroleum industry, large Internet companies and government agencies. These eleven-year attacks can be traced back to 2008 (spanning from September 2008 to June 2019), and are mainly distributed in provinces such as Beijing, Guangdong, and Zhejiang. The above-mentioned targeted attacks are all attributed to a U.S.-related APT organization – APT-C-39 (according to Qihoo 360’s code-naming system).
What is the capability of APT-C-39 and what are the security threats it may pose? Let’s take the attack on civil aviation industry as an example.
As it involves national security, we will only disclose part of the intelligence data held by Qihoo 360. In the CIA’s attack against Chinese aviation organizations and scientific research institutions, we found that attackers mainly targeted system developers in these sectors to carry out the campaigns. These developers are mainly engaged in works like information technology of civil aviation, such as flight control system, freight information services, settlement and distribution services, passenger information system, etc.
Information technology of civil aviation refers to various technology services for domestic and international commercial airlines, for instance, flight control system, passenger information system, airport passenger processing system, and extended data and information technology services.
It is worth noting that the attacked information technology sectors of civil aviation by the CIA are not only in China, but also involves hundreds of commercial airlines national states. So, what is the purpose of this movement?
In fact, long-term and targeted intelligence-gathering with careful strategic deployment and large amount of resource investment are common activities of CIA.
We speculate that in the past eleven years of infiltration attacks, CIA may have already grasped the most classified business information of China, even of many other countries in the world. It does not even rule out the possibility that now CIA is able to track down the real-time global flight status, passenger information, trade freight and other related information. If the guess is true, what unexpected things will CIA do if it has such confidential and important information? Get important figures‘ travel itinerary, and then pose political threats, or military suppression?
Qihoo 360 Tracked Down the Key Figure of CIA Cyber Arsenal R & D – Joshua Adam Schulte
When it comes to CIA’s key cyber weapon, Vault 7, it is necessary to introduce the former CIA employee Joshua Adam Schulte.
Joshua Adam Schulte was born in Lubbock, Texas in September 1988, graduated from the University of Texas at Austin. He used to work for the National Security Agency (NSA) as an intern for some time, and then joined CIA in 2010 serving at the National Clandestine Service (NCS) as a Directorate of Sience and Technology (DS&T) Intelligence Officer.
The National Clandestine Service (NCS) or the Directorate of Operations (DO) serves as the clandestine arm of the Central Intelligence Agency (CIA) and the national authority for the coordination, de-confliction, and evaluation of clandestine operations across the Intelligence Community of the United States.
Proficient in the design and development of cyber weapons and possessing knowledge of intelligence operations, Joshua became one of the core backbones of the CIA’s many important hacking tools, including a key cyber weapon – Vault 7.
In 2016, Joshua took advantage of his admin privilege of the core machine room and a preset backdoor to steal the classified documents of Vault 7 and disclosed to WikiLeaks, which was published on Wikileaks website in 2017.
In 2018, Joshua was arrested and prosecuted by the U.S. Department of Justice for the Vault 7 leaks. On February 4, 2020, at a public hearing in the federal court, the federal prosecutor alleged that Joshua, as the core developer and the person in charge of the highest administrator authority of its internal arsenal, has committed “the single biggest leak of classified national defense information in the history of CIA”by disclosing the agency’s secret hacking tools to WikiLeaks.
Joshua’s personal experience and leaked materials provided us with important clues, and the fact that Vault 7 was developed by Joshua and the prosecution on the court all point to the conclusion that APT-C -39 is affiliated with CIA.
Five Major Related Evidences Reveal That APT-C-39 is Affiliated with the CIA
With Vault 7 as the core point of association, and through Joshua’s series of experiences and behaviors above, all the evidence leads to the attribution of APT-C-39. In addition, considering the uniqueness and time span of the use of the APT-C-39 cyber weapon, Qihoo 360 gave the conclusion that the group’s attack was initiated by the state-level hacking organization, CIA, which Joshua belongs to.
The related evidence is listed below:
Evidence 1: APT-C-39 uses massive exclusive cyber weapons in the CIA’s Vault 7 project
APT-C-39 has used CIA-exclusive cyber weapons such as Fluxwire, Grasshopper to carry out cyber-attacks against China.
By comparing relevant sample codes, behavioral fingerprints, and other information, the Qihoo 360 can be pretty sure that the cyber weapon used by the group is the cyber weapon described in the Vault 7 leaks.
Evidence 2: The technical details of most samples of the APT-C-39 are consistent with the ones described in the Vault 7 documents
Qihoo 360 analysis found that the technical details of most of the samples are consistent with the ones in the Vault 7 document, such as control commands, compile pdb paths, encryption schemes. These are the pattern usually found in standardized attack organizations, and it is also one of the methods to classify them. Therefore, the group is believed to belong to the CIA-led national hacking group.
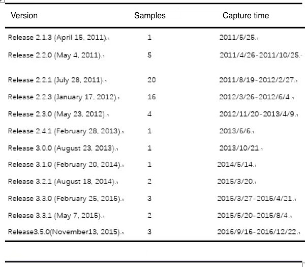
Evidence 3: Before the Vault 7 cyber weapon was disclosed by WikiLeaks, the APT-C-39 already used relevant cyber weapons against targets in China
For example, at the beginning of 2010, the APT-C-39 has used the Fluxwire backdoor in the Vault 7 cyber weapon in cyber-attack activities in China, which is much earlier than the Vault 7 leaks. This further confirms the source of these cyberweapons. After in-depth analysis and decryption of the version in the Fluxwire backdoor in the Vault 7, Qihoo 360 statistically classified the version, attack time, and samples captured by itself that APT-C-39 used to attack targets in China over the years, as shown in the following table:
Since 2010, the APT-C-39 has been continuously upgrading its cyber weapons and has frequently launched attacks on targets in China.
Evidence 4: Some attack weapons used by the APT-C-39 are associated with the NSA
WISTFULTOLL is an attack plugin in the 2014 NSA leaks. In an attack against a large Internet company in China in 2011, the APT-C-39 organization used the WISTFULTOOL plugin on the target. At the same time, in the CIA confidential documents uncovered by WikiLeaks, it was confirmed that the NSA assisted the CIA in developing cyber weapons, which is also a side-by-side evidence of the association between the APT-C-39 and U.S. intelligence agencies.
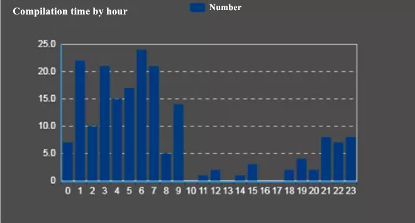
Evidence 5: APT-C-39 group’s weapons compilation time is located in the U.S. time zone
The compilation time of the captured samples is in line with the North American business working hours.
The compilation time of malware is a common method and statistics in the research of APT group attribution. Through the study of the compilation time of malware, we can find out the developer’s work schedule, so as to know the approximate time zone of his location.
The following table is the schedule of compilation activities of APT-C-39 (the time is based on the East 8 time zone). It can be seen that the organization’s activities are close to the schedule in Eastern U.S. time zone, which is in line with the CIA’s location. (Virginia, U.S. Eastern Time).
Taken together with the above technical analysis and digital evidence, we have every reason to believe that the APT-C-39 is affiliated with the United States and is involved in the attack spree by U.S. intelligence agencies.
In particular, in the course of the investigation and analysis, Qihoo 360 data have shown that the cyber-weapons used by the organization and the cyber weapons described in the CIA Vault 7 project are almost identical. The CIA Vault 7 weapons show from the side that the United States has built the world’s largest cyber weapons arsenal. It has not only brought serious threat to the global network security, but also demonstrate the APT organization’s high technical capabilities and professional standards.
The form of war goes beyond hand-to-hand battle of soldiers. Cyberspace has already become another important battleground in the war between great powers. If playing the game with the CIA, the road ahead of us is long and full of difficulties and obstacles.
Qihoo 360 – Threat Intelligence Center
Since 2014, Qihoo 360 – Advanced Threat Intelligence Center has achieved rapid reversing and correlation analysis by integrating massive security big data. It has exclusively discovered more than 40 APT hacking groups and a number of APT operations against China launched by national states threat actors using in-the-wild 0days, which greatly enriches the domestic researches in this field. Their researches show the earliest attack against China can be dated back to 2007 and tens of thousands of devices distributed in 31 provinces were affected. APT attacks discovered by Qihoo 360 and national states security vendors both prove that China is one of the main victims of APT attacks.
Learn more about 360 Total Security