Recently, 360 Security Center observed a state-level cyber warfare attack against Ukraine for the purpose of sabotage, including distributed denial of service (DDoS) attacks, phishing scams, exploits, supply chain attacks, malicious data wipes disguised as ransomware Except for attacks, etc.
Through the first analysis and judgment of the 360 security team, these cyber attacks may be aimed at causing chaos in Ukraine, hindering communications, and weakening Ukraine’s government, civilian and military institutions. It is a long-planned cyber war. This analysis report will analyze the key technical details of this cyber war from the global perspective of 360 Security Center.
Ukraine Cyber Attack Timeline
January 14, 2022
More than 70 Ukrainian government websites were attacked by the APT group, including those belonging to the Ukrainian Ministry of Foreign Affairs, Ministry of Defense, State Emergency Service, Cabinet and Ministry of Foreign Affairs.
January 17, 2022
The National Cyber Police Service of Ukraine issued a security notice. On the evening of January 14, 95% of the hacked Ukrainian government websites were back to work. However, more serious destructive attacks than modifying the behavior of the website pages are still going on. Since that night, some Ukrainian government agencies have been subjected to violent DDOS attacks, and at the same time, there has been data erasure and destruction disguised as “WhisperGate” ransomware. malicious sample attack.
According to the official description, the relevant APT groups are using a combination of supply chain attacks, OctoberCMS (a CMS program widely used in Ukraine) exploits and Log4j vulnerabilities to conduct a combined cyber-attack sabotage campaign.
January 18, 2022
U.S. CISA issued a security notice related to the Ukraine ransomware attack, stating that organizations in Ukraine suffered a series of malicious network incidents, including DDOS, website hacking and potentially destructive malware, of which destructive malware is the most worrying, because Historically, there have been destructive attacks suspected of counterfeit ransomware, such as NotPetya and WannaCry, causing widespread damage to critical infrastructure. CISA requires every organization in the United States to take immediate, urgent steps to mitigate the impact of a potentially damaging attack.
February 23, 2022
The security community is starting to notice that Ukraine has begun spreading new data-wiping malware, HermeticWiper.
Ukraine suffers from multiple three-dimensional cyber attacks
- The first attack: WhisperGate data wiper
Before and after the first wave of WhisperGate attacks, 360 Security Center’s network-wide view observed that the attacks began on January 10, until January 15, when Microsoft said that it found that APT groups had delivered WhisperGate samples to some important institutions in Ukraine, and the destruction of related samples The action encrypts the disk MBR and files of the specified type on the machine.
| WhisperGate Some sample information |
| stage1.exe 5d5c99a08a7d927346ca2dafa7973fc1 |
| stage2.exe 14c8482f302b5e81e3fa1b18a509289d |
| Tbopbh.jpg b3370eb3c5ef6c536195b3bea0120929 |
| Frkmlkdkdubkznbkmcf.dll e61518ae9454a563b8f842286bbdb87b |
WhisperGate implements a three-stage data breach attack:
Stage 1: Overwrite the MBR and destroy all partitions
Stage 2: Download Stage 3 via CDN hosted by the Discord service
Stage 3: Execute the file wiper
According to the global vision observation of 360 Security Center, some specific attack process chains of WhisperGate are as follows:
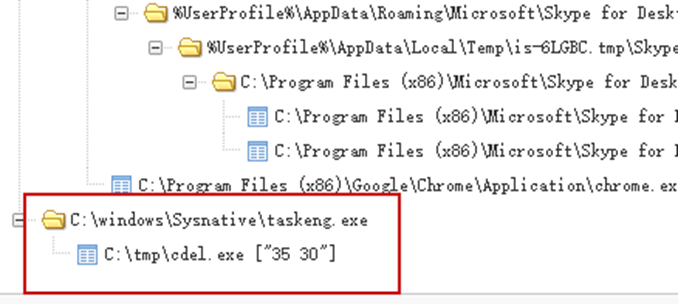
- The second round of attacks: HermeticWiper data wiper
The security community first noticed the HermeticWiper attack on February 23, saying that the APT group delivered HermeticWiper to hundreds of organizations in Ukraine for a second sabotage attack.
| HermeticWiper Some sample information |
| cdel.exe 3f4a16b29f2f0532b7ce3e7656799125 |
| Bpdr.sys 6106653b08f4f72eeaa7f099e7c408a4 |
According to the global vision observation of 360 Security Center, some of the attacks were initiated by planned tasks, which were suspected to be delivered and implanted by controlling intranet domain controllers and exploits of different network services.
- The imminent supply chain attack crisis
According to the analysis and deduction of the 360 Advanced Threat Research Institute, large-scale sabotage attacks implemented in cyber warfare are very likely to spread to the world because they are not under the control of the attackers, and relevant organizations need to be vigilant.
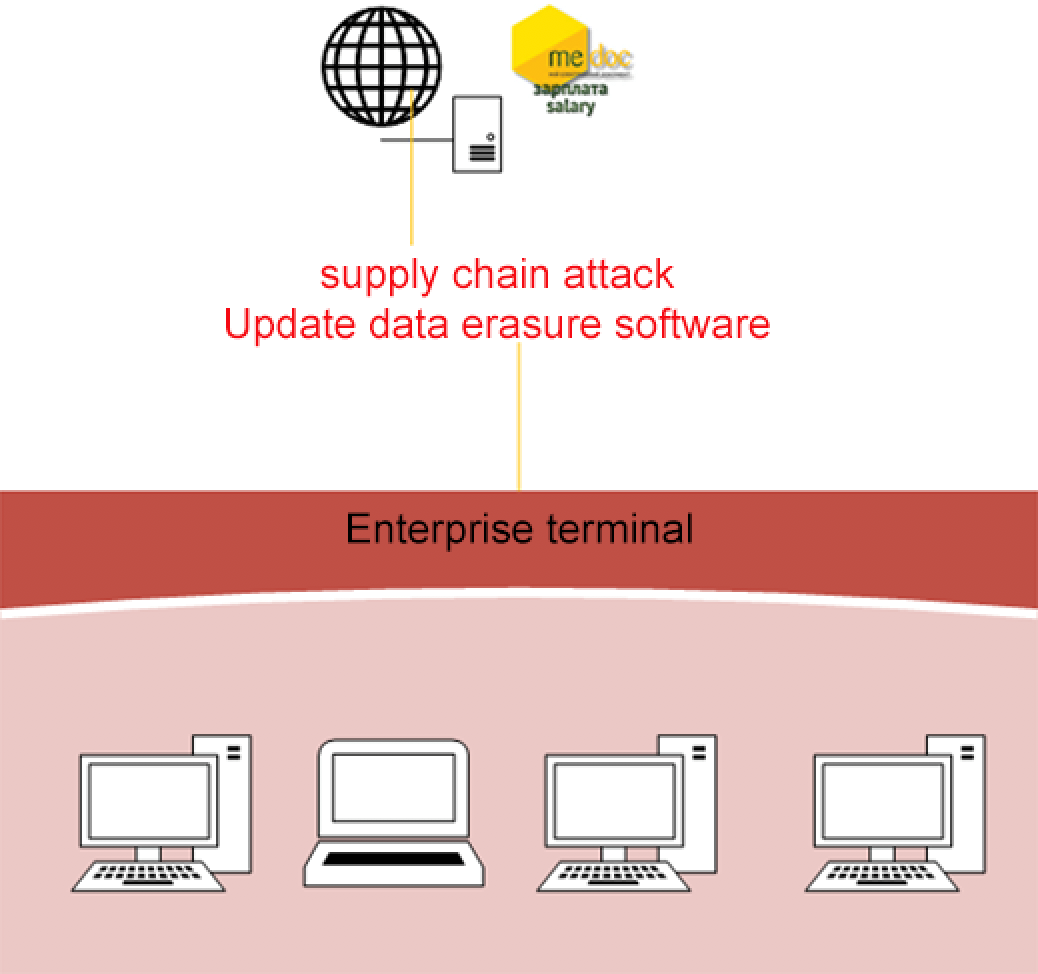
At present, there is no publicly disclosed cyber intelligence on cyber warfare supply chain attacks against Ukraine, but as early as 2017, “NotPetya” suspected of disguising as ransomware used software updates to launch supply chain attacks, and related attacks first became popular in Ukraine This complex supply chain attack method caused 80% of Ukraine’s enterprises to be attacked and damaged by “NotPetya” to varying degrees.
Unexpectedly, “NotPetya” is still spreading around the world, disrupting key IT systems of international shipping and logistics companies such as Maersk and TNT, and having unplanned and far-reaching impacts on global supply chains.
Within a day of Ukraine being attacked by cyber warfare, the US CISA issued a national security warning, warning US organizations not to be affected by ransomware and related supply chain attacks. Vigilant and advanced cybersecurity defense awareness.
- Spear phishing attacks with increased firepower
According to the global vision of 360 Security Brain, starting from the end of 2021, a large number of Ukrainian users have been attacked by malicious document spear phishing from suspected APT organizations. The attackers use decoy documents to release and execute vbs scripts, and complete malicious documents by creating scheduled tasks. Most of these vbs file names end with .log and are highly obfuscated.
The size and activity of affected users of the related attack surged and peaked on February 21 this year:
We have counted the main regions of Ukraine’s victimized users this year, and the data shows that most of the victimized users are from the Donetsk and Kyiv regions:
- Vulnerability utilization
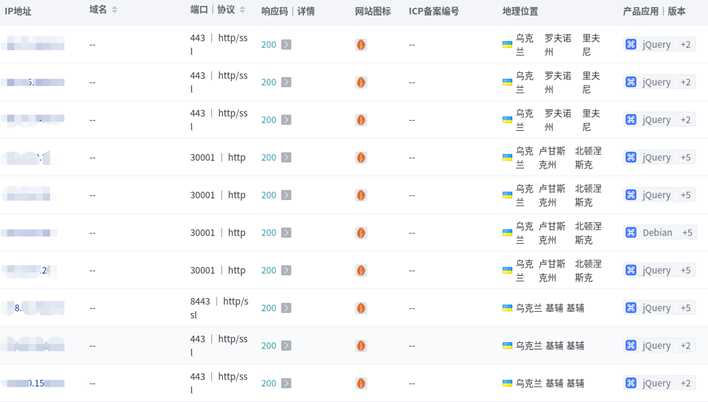
Through the analysis of the cyberspace asset mapping data of 360 Security Center, the Ukrainian government website has used a website building program called “octobercms” on a large scale.
Ukrainian authorities have noted that a vulnerability CVE-2021-32648 in the OctoberCMS content management system (CMS) platform has been widely exploited, allowing attackers to directly gain administrator privileges on a website. In addition, there are also some log4j exploits that have been officially noticed.
According to the analysis of public vulnerability information, the CVE-2021-32648 vulnerability is a password reset function verification bypass vulnerability. Verify on. According to the code logic in User.php, the process of resetting the password in octobercms is divided into the following steps:
- Trigger the reset process, and call getResetPasswordCode for the user who needs to reset the password to generate a random string with a default length of 42.
- Verify the password reset request through attemptResetPassword, only verify the random string generated in the previous step, and the verification function is checkResetPasswordCode.
- There is a PHP weak type error in the checkResetPasswordCode function, which makes it possible to bypass the verification of checkResetPasswordCode without knowing the specific content of the random characters.
- Directly overwrite the old password of the corresponding user with the new password and save the data.
Summary
Based on the analysis and deduction of key technical details, 360 Advanced Threat Research Institute believes that this attack is a major and destructive cyber warfare attack against Ukraine. Combined with the global vision of 360 Security Center, most of the attack can be deduced The process and key details of this cyber attack are still evolving, and it is very likely that organizations outside Ukraine will be affected. Relevant organizations need to be vigilant.
In the digital age, cyber warfare will become the first choice. Cyber warfare attacks are not only for the purpose of stealing intelligence, but can also cause damage to infrastructures such as transportation, energy, and finance. Any node may become a springboard for attacks, which can lead to serious consequences. For this reason, we must be aware of the network The severe situation of the war, face up to the network war!
Behind the “disconnection” caused by the cyber attack in Ukraine this time, it is undoubtedly not revealed that the new type of cyber warfare already has physical attack capabilities. That is to say, a network attack has the ability to turn the blow of the traditional virtual world into the actual damage of the physical world. The attack speed is fast and the effect is strong, but the cost, movement and controllability are much better.
The characteristics of the new type of cyber warfare can be summarized as “seven majors”, that is, the battlefield is big, the opponent is big, the means is big, the challenge is big, the goal is big and the harm is big. In the future, cyber warfare will become the biggest threat in the digital age.
In addition, judging from the Ukrainian Ministry of Defense’s call to help defend against possible cyber attacks on Ukrainian critical infrastructure, cyber warfare targeting urban infrastructure will become more frequent in the future.
The interconnection of all things in digital cities, the increase in the number of intelligent terminals and network users, the wide range of data sources, the diversification of data, and the complexity of data structures make it difficult to maintain various key information infrastructures that carry urban operation data, resulting in the construction of network security and operational risk.
At the same time, the vulnerabilities of various software and hardware systems of critical information infrastructure are also difficult to avoid being exploited and attacked. Therefore, it is necessary to strengthen the top-level design and overall plan of cyber warfare defense for digital cities, build a combat-oriented defense system and an emergency response system, and make every effort to ensure the security of digital cities.
More notably, the swift warnings issued by the U.S., large and small, ensure that senior leaders in every organization are aware of critical cyber risks and take urgent steps to deal with them. If working with Ukrainian organizations, pay extra attention to monitoring, inspecting, and quarantining traffic from these organizations; closely scrutinize access controls for these traffic.
Learn more about 360 Total Security