Background
On 20th September 2018, the Zero Day Initiative (ZDI) team has publicly disclosed a serious remote code execution vulnerability in the Microsoft JET database engine.
The JET database engine is bundled with Windows and used by multiple Windows products.
Vulnerability Details
The vulnerability is caused by an out-of-bounds (OOB) write in the JET database engine.
Microsoft’s OLE DB Provider for JET and Access ODBC only support 32-bit, which means that direct utilization is not available on 64-bit hosts.
But on a 64-bit host, the 32: wedit.exe can be used to start the PoC by starting c:\ windows \ SysWOW64 \wscript.exe poc.js
At the same time, this kind of attack can be triggered by Internet Explorer. Even on 64-bit Windows, the Internet Explorer rendering process is 32-bit.
However, on IE11 – Security settings “cross-domain access to data sources” are disabled in the Internet and intranet zones, which can lead to JavaScript errors and unable to trigger the vulnerability.
Launching malicious poc.html from a local drive (or USB disk) also triggers the vulnerability. However, the user needs to press “Allow Blocked Content” to trigger.
Vulnerability Verification
PoC content is as follows:
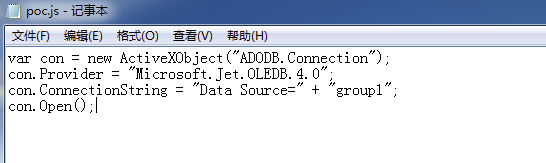
Cause wscript.exe to crash after triggering
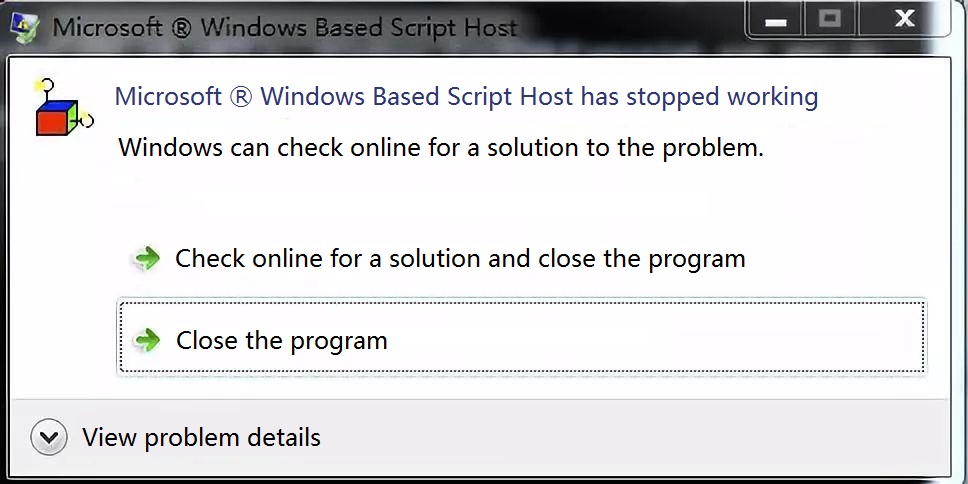
Reminder
360 CERT (360 Computer Emergency Readiness Team) would like to give the users two suggestions:
1. Be cautious. Do not open files from the untrusted sources.
2. Update IE browser version, avoid free click to allow blocking content button
Timeline
05 Aug 2018 – ZDI reported vulnerability to Microsoft
20 Sep 2018 – ZDI announced vulnerability details and PoC
25 Sep 2018 – 360 CERT issued a vulnerability warning








