A new bitcoin ransomware virus called “WannaRen” is spreading on a large scale. For users who are unfortunately infected with “WannaRen” ransomware, important files will be encrypted and hackers will demand a 0.05BTC ransom.
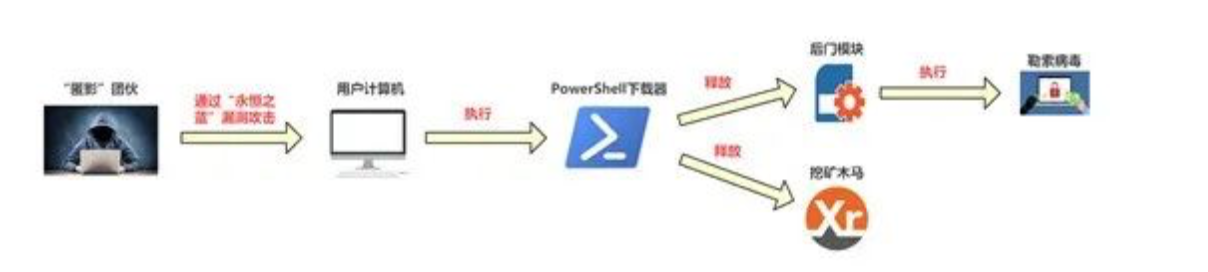
In the first time of detecting anomalies, 360 Security Center was the first to discover the source of the “WannaRen” ransomware virus and associated it with a behind-the-scenes hacker group, and the first to analyze the real ransomware attack code. 360 Security Center confirmed that the author of the “WannaRen” ransomware was the “hidden shadow” organization that previously took advantage of the “eternal blue” vulnerability.
This time, the “Hidden Shadow” organization changed the way of profiting by mining Trojan horses, and delivered the “WannaRen” ransomware through the entire network, asking for ransom to make a profit. However, users should not worry too much. 360 Total Security has discovered and supported the interception and killing of the new “WannaRen” ransomware In time.
Who is the “Hidden Shadow” organization?
“Cryptocurrency excavator” turned into “ransomware deliverer”
Based on 360 Security Center tracking data, the “Hidden Shadow” family has a long history in the illegal possession of cryptocurrencies. As early as in the previous attack activities, the “Hidden Shadow” family attacked the target computer through the “eternal blue” vulnerability, implanted a mining Trojan into it, and mined encrypted numbers such as PASC coins and Monero coins by illegally controlled computers.
In terms of attack characteristics, the “Hidden Shadow” hacker group mainly uses BT downloaders, activation tools, etc. to spread, and has also used the “Eternal Blue” vulnerability to spread laterally in the LAN. After the “Hidden Shadow” hacker group successfully invades the target computer, it usually executes a PowerShell downloader, and uses the loader to download the backdoor module and mining Trojan for the next stage.
In the proliferation of the new Bitcoin ransomware virus “WannaRen”, it looks similar to the previous “WannaCry” virus. After the virus invaded the computer, a ransomware dialog box popped up to inform the encrypted file and ask the user for Bitcoin . However, from the actual attack process, the “WannaRen” ransomware is used by the “Hidden Shadow” hacker group to use the PowerShell downloader to release the backdoor module to execute the virus.
As mentioned above, the “Hidden Shadow” organization switched to ransomware, but its attack method is a variant of its early mining Trojan. The only difference, and the key to the proliferation of “WannaRen”, is the backdoor module released by the PowerShell downloader.
From 360 Security Center tracking data, the backdoor module uses DLL side-loading technology, which will release a legitimate exe file WINWORD.EXE and a malicious dll file wwlib.dll in “C: \ ProgramData” to start WINWORD.EXE loading wwlib.dll will execute the malicious code in the dll.
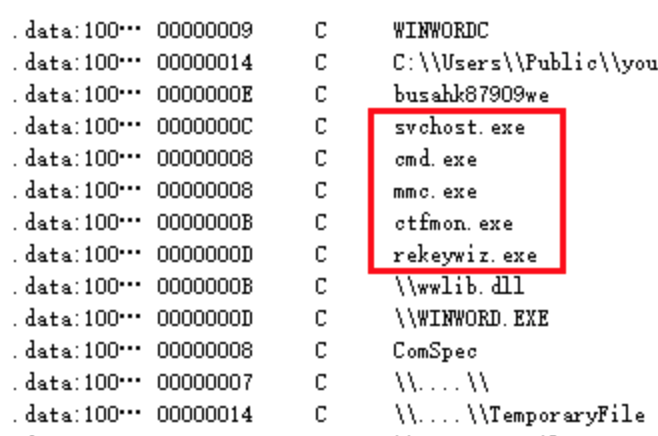
The backdoor module will register itself as a service, the program will read the content of C:\users\public\you, start one of the five processes shown in the following figure and inject the “WannaRen” ransomware virus code into the process for execution.
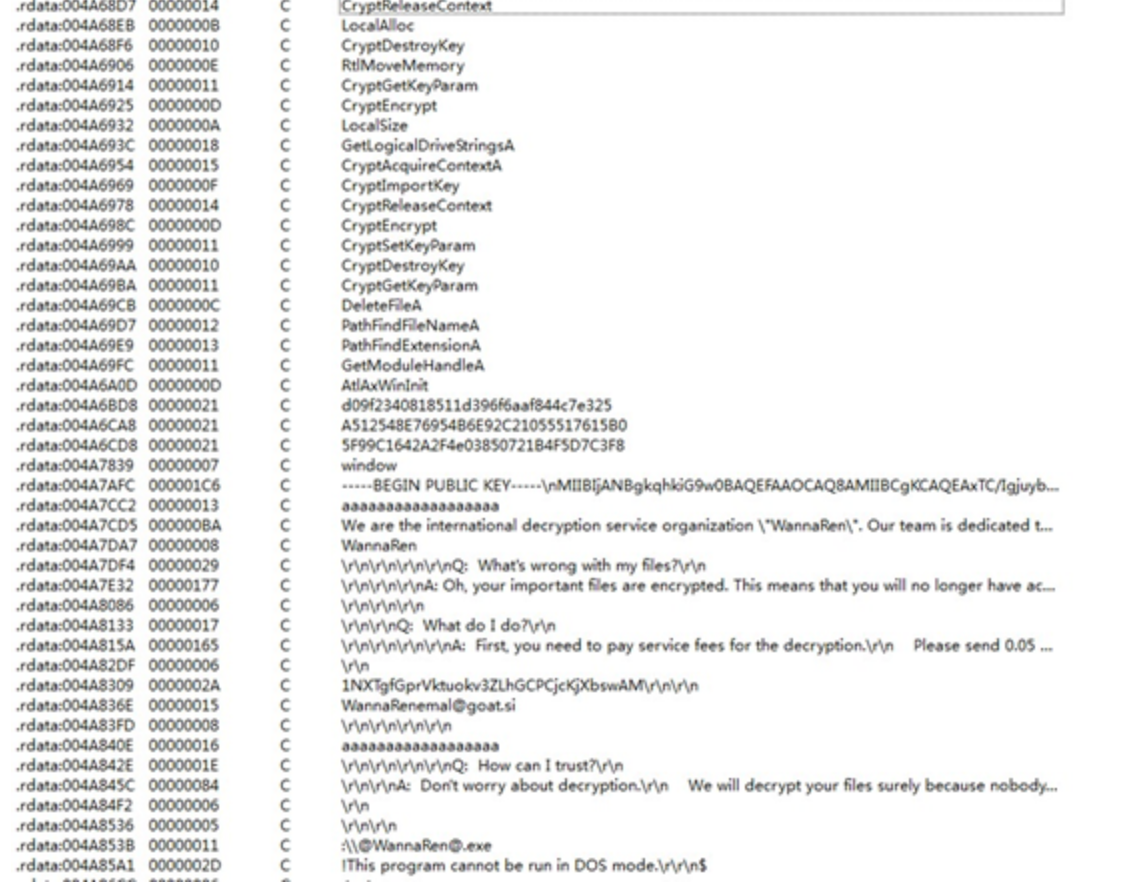
In the injected code, you can see the encrypted program part of the ransomware virus:
The complete attack process is shown in the following two figures:
(“Hidden Shadow” Powershell downloader releases and starts the backdoor module)
(“Hidden Shadow” backdoor module injects svchost.exe and encrypts the file)
WannaRen ransomware has “horizontal transmission” capability
360 Total Security Powerful Intercept
During the tracking process, 360 Security Center also found that the PowerShell downloader issued by the “Hidden Shadow” organization contained an “eternal blue” propagation module. This module will scan other machines in the intranet, and once a machine has not repaired the vulnerability, it will be brutally infected and become another “WannaRen” ransomware victim.
(The “eternal blue” communication module in the PowerShell downloader)
(Eternal Blue exploit tool released by PowerShell downloader)
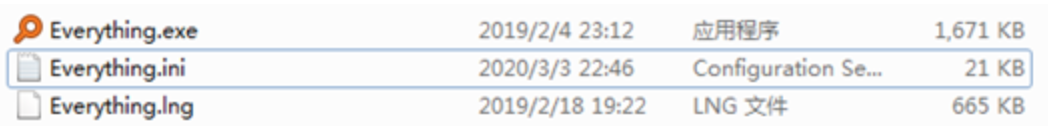
In addition, the PowerShell downloader will install a backdoor called “everything” on the infected machine, using the security vulnerability of the “HTTP server” function of everything to turn the victim machine into a file server. Trojans spread to new machines.
(Everything backdoor module)
Turn the machine into a file server by modifying “everything” configuration file
It is not difficult to see that once corporate users are unlucky, the “WannaRen” ransomware may spread on the intranet. But users need not worry too much, 360 Total Security can effectively block this ransomware virus. Facing the raid “WannaRen” ransomware, 360 Security Center once again reminds the majority of users to be vigilant, and can effectively prevent ransomware through the following measures:
- Go to www.360totalsecurity.com in time, download and install 360 Total Security, kill the “hidden shadow” back door, and prevent the machine from being delivered ransomware
- For tools that prompt security software for viruses, do not trust software prompts to add trust or exit security software;
- Regularly detect security holes in the system and software and apply patches in a timely manner.
Learn more about 360 Total Security