Ransomware has been appearing on the Internet for a while; Cerber, TeslaCrypt, and Jigsaw are already familiar names. And now, one new ransomware is floating around. The developers of Cerber Ransomware recently released a new malware, Alfa Ransomware.
Alfa Ransomware is not decryptable at this moment
According to security researcher BloodDolly, so far, there is not much known about this new file encrypter, for example, how this ransomware is distributed still remains unclear. Yet unfortunately, one thing is for sure – this ransomware shares one concrete feature with its counterpart Cerber Ransomware – the encryption cannot be broken at this time.
When infecting a PC, Alfa Ransomware will scan all the local drives for certain file types, up to 142 different file types are targeted. After encryption, Alfa will append a file extension (.bin) to the encrypted files. For instance, ‘blog.ppt’ will become ‘blog.ppt.bin’.
File types targeted are as below:
.c, .h, .m, .ai, .cs, .db, .nd, .pl, .ps, .py, .rm, .3dm, .3ds, .3fr, .3g2, .3gp, .ach, .arw, .asf, .asx, .avi, .bak, .bay, .cdr, .cer, .cpp, .cr2, .crt, .crw, .dbf, .dcr, .dds, .der, .des, .dng, .doc, .dtd, .dwg, .dxf, .dxg, .eml, .eps, .erf, .fla, .flvv, .hpp, .iif, .jpe, .jpg, .kdc, .key, .lua, .m4v, .max, .mdb, .mdf, .mef, .mov, .mp3, .mp4, .mpg, .mrw, .msg, .nef, .nk2, .nrw, .oab, .obj, .odb, .odc, .odm, .odp, .ods, .odt, .orf, .ost, .p12, .p7b, .p7c, .pab, .pas, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .pps, .ppt, .prf, .psd, .pst, .ptx, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .r3d, .raf, .raw, .rtf, .rw2, .rwl, .sql, .sr2, .srf, .srt, .srw, .svg, .swf, .tex, .tga, .thm, .tlg, .txt, .vob, .wav, .wb2, .wmv, .wpd, .wps, .no, .xlk, .xlr, .xls, .yuv, .back, .docm, .docx, .flac, .indd, .java, .jpeg, .pptm, .pptx, .xlsb, .xlsm, .xlsx
Once encryption is finished, Alfa Ransomware will also drop two ransom notes called README HOW TO DECRYPT YOUR FILES.HTML and README HOW TO DECRYPT YOUR FILES.TXT on the victim’s Desktop and other folders. In these documents, victims will get a unique ID to be used to login to the TOR-based payment site, where they are required 1 Bitcoin ransom as the only solution to get their files back.
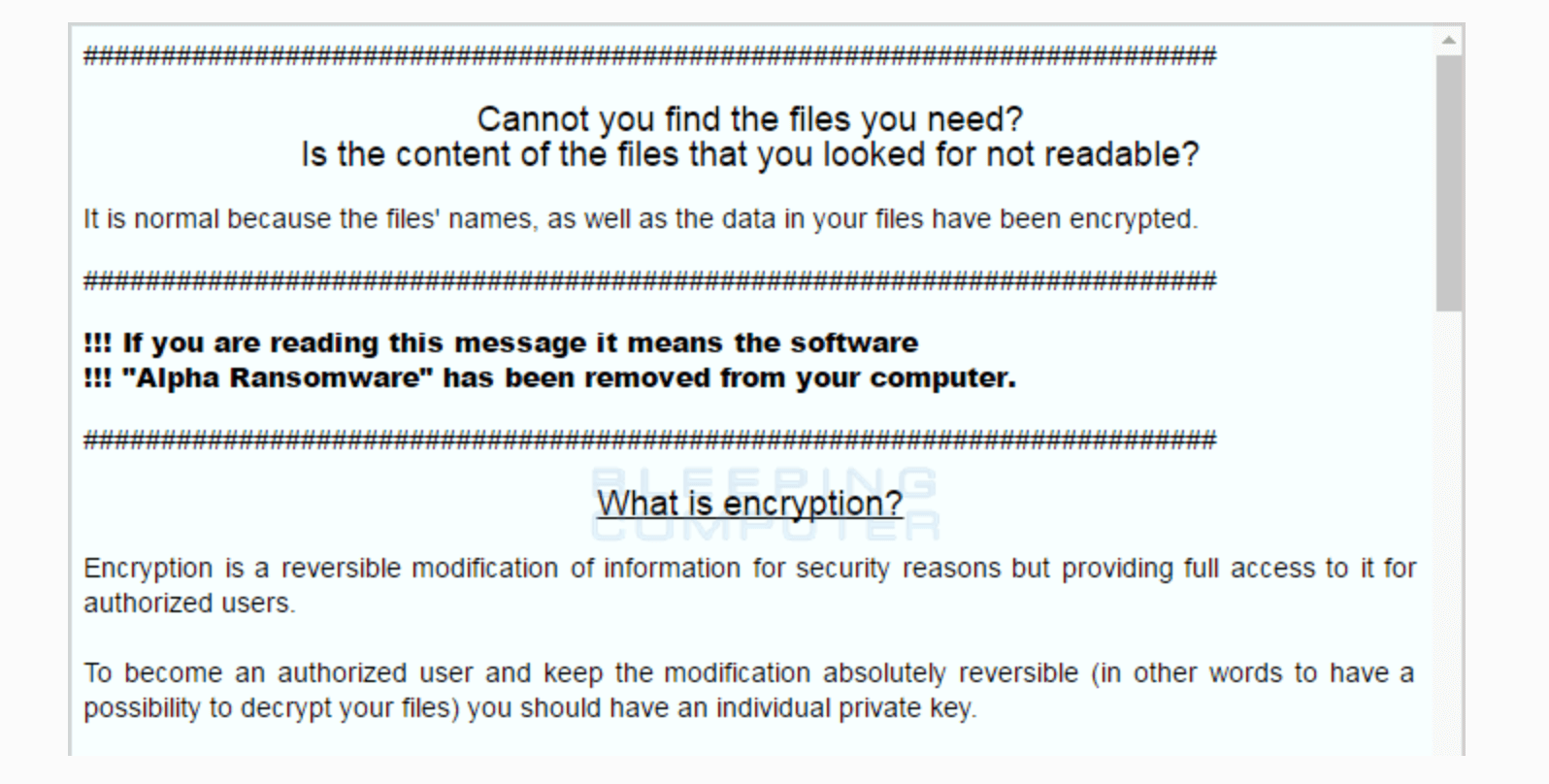
Alfa Ransomware will then delete the Volume Shadow Copies on the victim’s computer. Since Volume Shadow Copy Service allows users to manually or automatically create backup copies, this deletion will stop users from recovering the unencrypted files.
The Alfa Decryptor Site
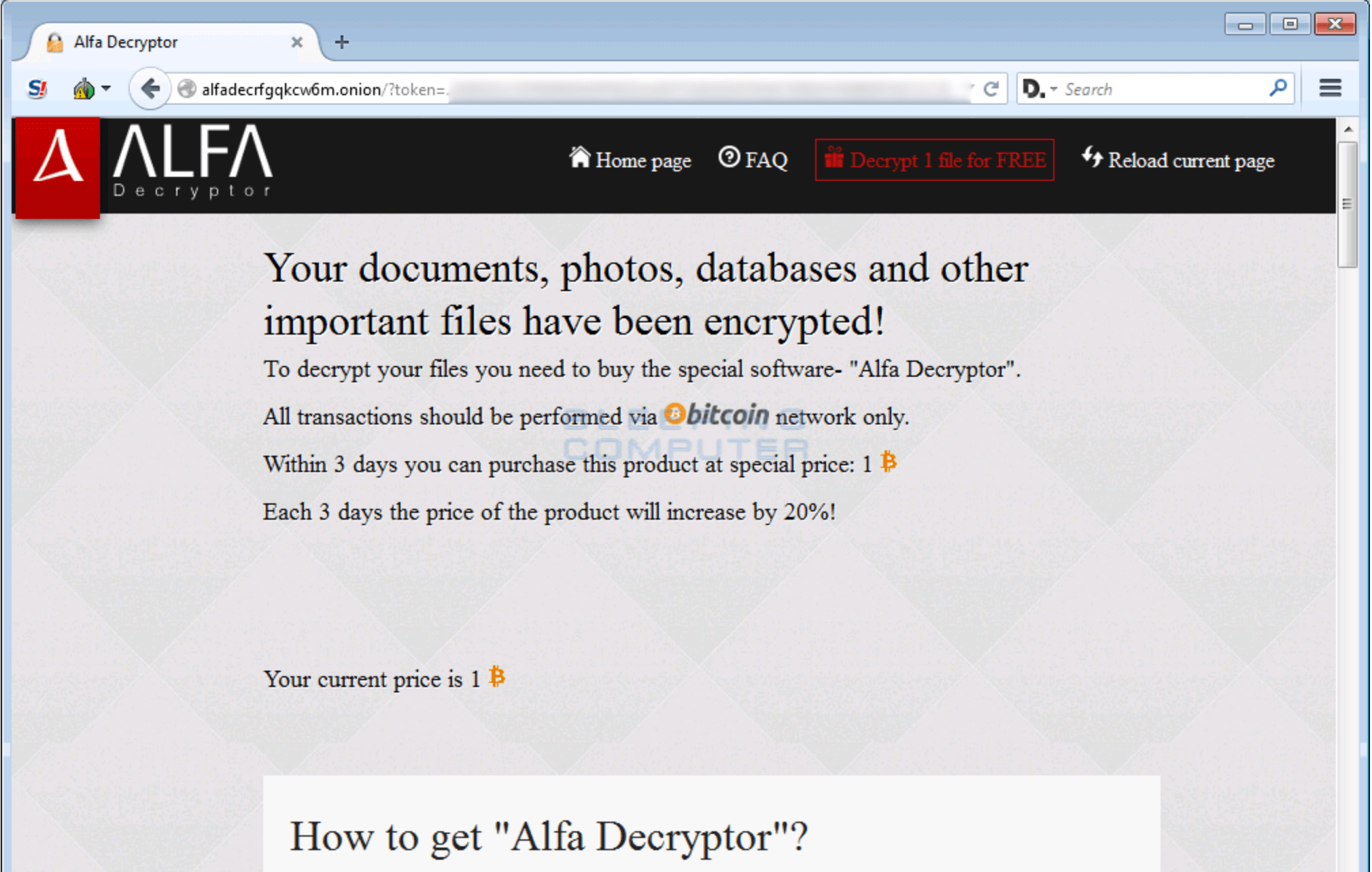
Just like many other members of the ransomware family, the payment sites to obtain the decryption key for Alfa Ransomware are TOR-based, making it almost impossible to track back the identity of the attackers.
When entering the site, victims will be shown a login form, in which they need to inset the unique ID provided in the ransom note. After logging in to the Alfa Decryptor page, victims can first choose to decrypt 1 file for free, encouraging them to pay the bitcoin ransom to save the rest of the files. Once the payment has succeeded, a decryptor will be generated and presented on this page.
Although security researchers have not yet figured out how Alfa Ransomware spreads, you can take precautions to stay away from ransomware attacks. For example, do not open emails from unknown resources, regularly update your operating system with the latest patches, and always back up your files in case your PC gets infected.








