Recently, 360 Security Center has found that a new CryptoMiner is spreading fast. The distributor has made tremendous profit via mining Monero on infected computers. According to our statistics, 360 Total Security has intercepted its attack over 500 thousands times in 3 days. Our analyst has named it “WinstarNssmMiner.” This malware is very hard to remove since victims’ computers crash as soon as they found and terminate the malware. Interestingly, this malware is acting snobbish when facing different antivirus software. It turns off antivirus protection of defenseless foes and backs off when facing sharp swords. As a result, users without a decent antivirus product have to live with the slowness and the blue screens of their computers.

Analysis
We’re quite surprised to see a CryptoMiner being so brutal to hijack victims’ computers by adopting techniques of stubborn malware:
1. Launch a system process, svchost.exe, and inject malicious code into it.
2. Set spawned process’ attribute to CriticalProcess.
3. Computers crash when their owners terminate the malware.
After getting into victims’ computers, this malware attempts to locate any decent antivirus software, Such as Kaspersky, Avast. If any found, this malware will quit automatically to avoid direct confrontation.
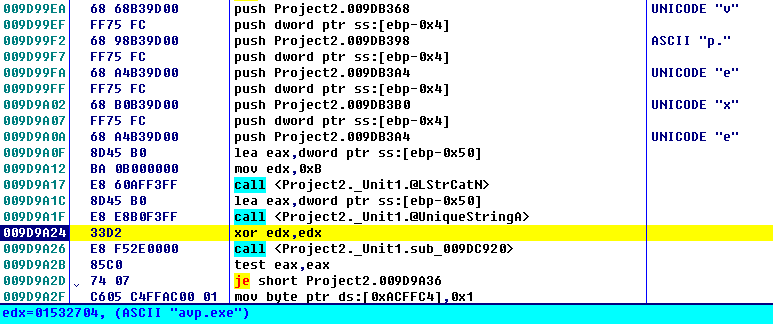
Figure 1: How this malware avoid antivirus software.
Then, this malware injecting the code to svchost.exe it created. There are actually two svchost.exe processes created. One performs the mining tasks. The other runs in the background for sensing the antivirus protection and avoiding detection.
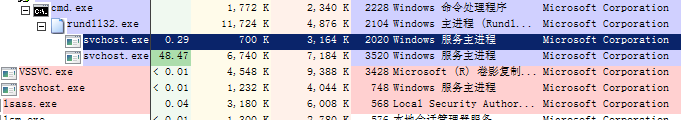
Figure 2: It creates two processes
Though WinstarNssmMiner has the ability to deceive antivirus software. It’s in its nature still a CryptorMiner and its implementation is based on the open source project, XMRIG. It comes with four ming pool and is able to determine mining pool based on the parameters passed to it.
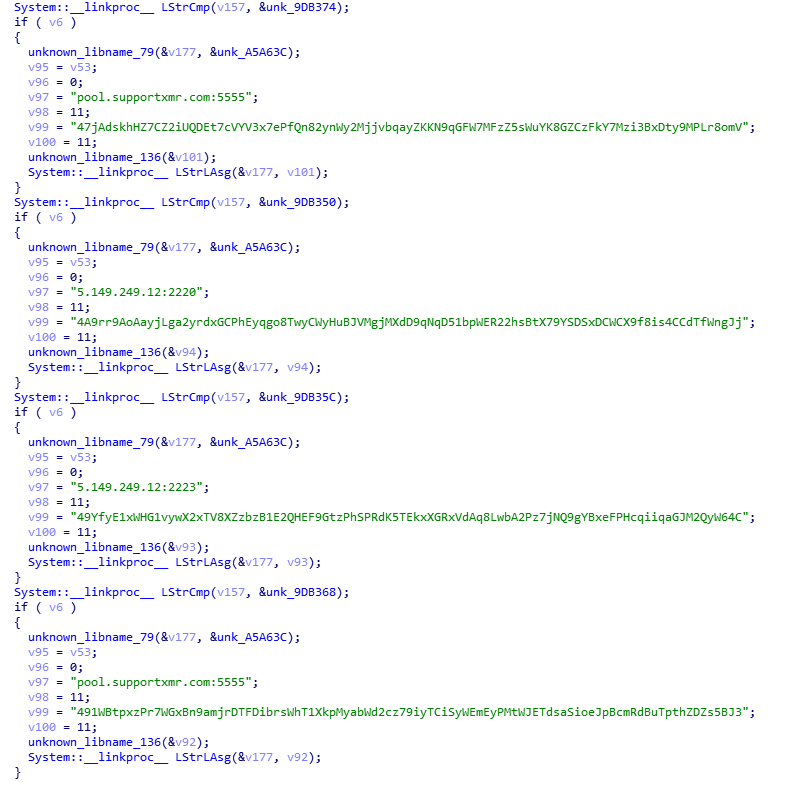
Figure 3: Addresses of mining pools
At the time we published this analysis, this CryptoMiner has already acquired 133 Monero which is approximately equivalent to 28 thousands US dollars.
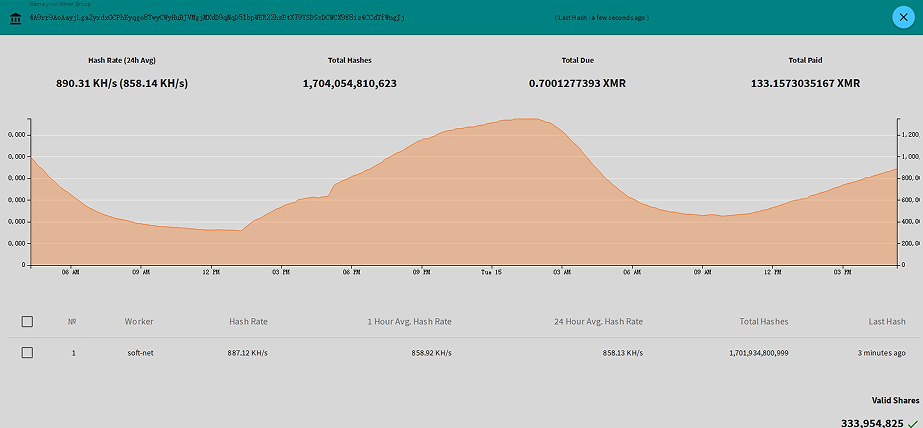
Figure 4: The profit earned
Due to the nature of digital currency mining, CryptoMiners use up victims’ processing power for the sake of their distributors. Some savvy users are able to identify and terminate the CPU consuming applications. Hence, WinstarNssmMiner protects itself by configuring its ming process’s attribute to CriticalProcess so infected computers crash when users terminate it.
Relevant file hash in MD5
184001cbd326cb3c03987c350c3ada6a
cf3e0eaf26c74db2bb5f8ba7e2607e2f
0be8a2b5f8a2fc9ad74d8ab9fcf5f583
Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Learn more about 360 Total Security







