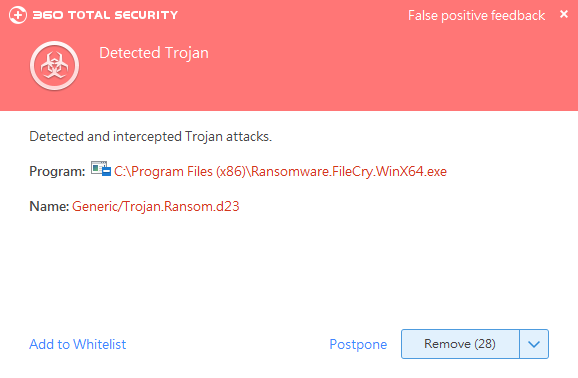
Recently, 360 Security Center detected a file ransomware named after WannaCry. In view of the virus’s ransomware pop-up window titled “FileCry”, we named it “FileCry ransomware”.
After encrypting the victim’s file, the virus will request 0.035 bitcoins to decrypt the ransom. But user don’t need to worry, 360 Total Security can intercept and kill the ransomware, and provide free decryption service.
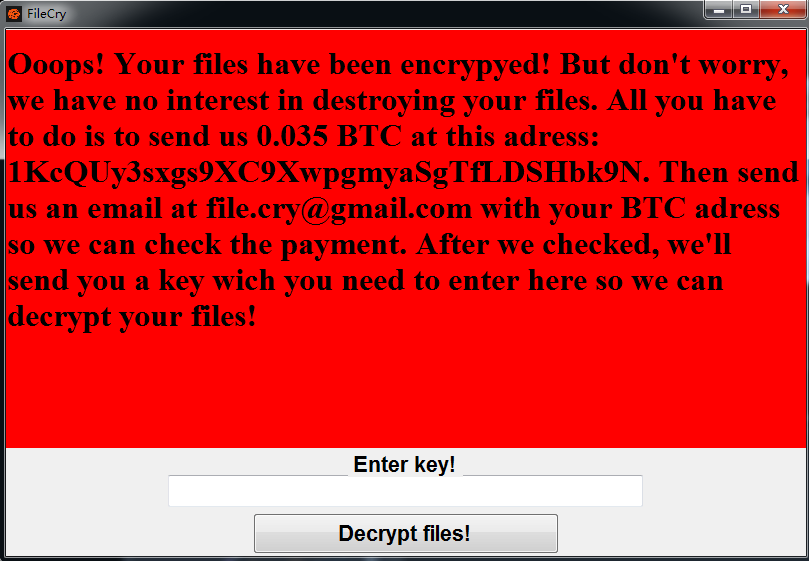
After the FileCry ransomware runs, it will encrypt all files and subfolder files in the same directory, add the encrypted file suffix named “.filecry”, and display the following bullet box, the text in the bullet box describes the ransom victim to “1KcQUy3sxgs9XC9XwpgmyaSgTfLDSHbk9N “This wallet address remits 0.035 bitcoins, and sends a ransom payment certificate to the virus author mailbox file.cry@gmail.com to obtain the decryption key and decrypt the victim’s file.
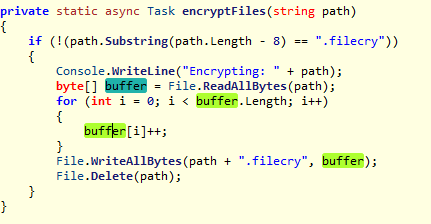
The current version of the FileCry ransomware encryption algorithm is very “plain”. Directly add 1 to each byte of the file data of the victim’s computer according to the ASCII code, and then add the encrypted file suffix as .filecry to end the file encryption operation.
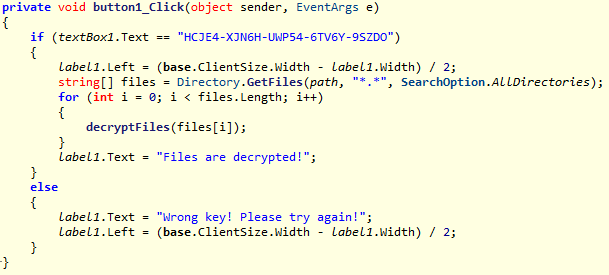
The deciphering key (HCJE4-XJN6H-UWP54-6TV6Y-9SZDO) needed to enter the ransomware box appears to be directly written by the virus author in the decryption key judgment function.
Security advice
- Go to http://www.360totalsecurity.com/ to download and install 360 Total Security for protection.
- Download and install software from the software official website, for unfamiliar software intercepted by 360 Total Security, do not continue to run and add trust.
- If you have inadvertently infected the Trojan, you can try the decryption key HCJE4-XJN6H-UWP54-6TV6Y-9SZDO of the current version of the virus in this article, or go directly to http://www.360totalsecurity.com/to download and install 360 Total Security, Use the free decryption service of 360 Total Security.
MD5:
4899accb55b148537d9b02232cb665a4
d8f7cc08aec6f3ca5d8a45a02f928b8e
Learn more about 360 Total Security