Earlier this week, 360 Security Center discovered that a famous download website, 52pk.com, was injected with a flash exploit, CVE-2018-4878. Few days later, we also found famous IT website, 51CTO.com, and medical website, cmechina.net, were compromised as well. After analyzing the injected code, these three injection attacks came from the same criminal group and were formed with the notorious exploit kit, GreenFlash Sundown.
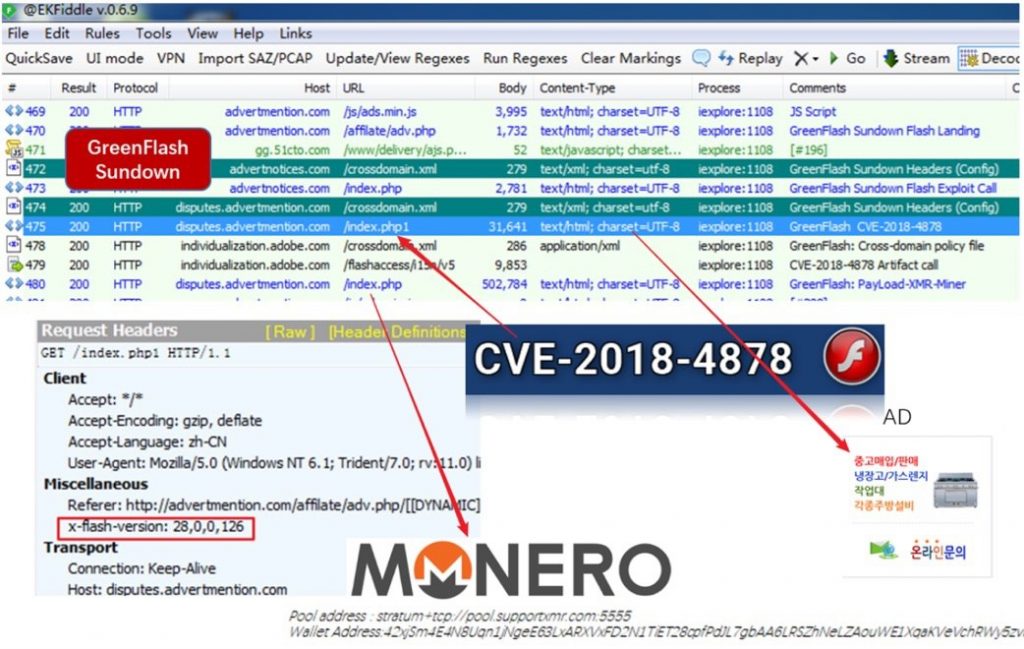
Figure 1. Network traffic of Injection Attack
GreenFlash Sundown is a comprehensive exploit kit which was found in 2016. It’s a variant of Sundown Exploit Kit. It was used to distribute Locky and Hermes ransomware. This is the first malicious activity that adopt GreenFlash Sundown.
Exploiting OpenX Advertisement Network
We have further analyzed this campaign, the recent attacks are targeting websites that are connected to OpenX’s Ads system. OpenX system was implemented with PHP for Ads management and tracking between the publishers and advertisers. But OpenX has suspended the maintenance of its system in which lots of known vulnerability have been exposed. (Note. it’s not the commercial version of OpenX) Attackers were able to abuse these vulnerabilities via GreenFlash Sundown Exploit Kit and inject the malicious code on the targets’ webpages.
The malicious code was injected to the php module of OpenX’s system under node “www\delivery.” When any request of Ads content to “hxxp://OpenX_host/www/delivery/xxx.php?zoneid=id&cb=random_number&n=nNum“ is made, the tampered php module will reply the Ads content along with malicious code. Figure 2 and Figure 3 are respectively the content of normal ads and hijacked one. The malicious code was injected before the content was returned to the Ads requester.
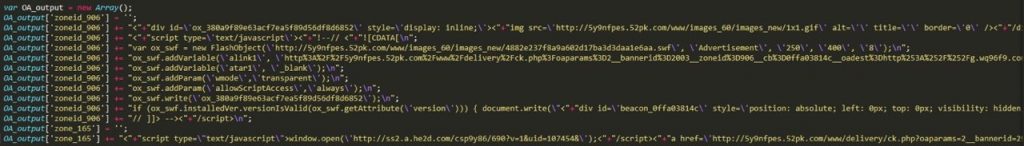
Figure 2. Clean Ads content
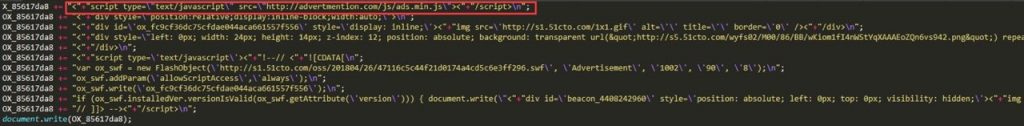
Figure 3. Tampered Ads content
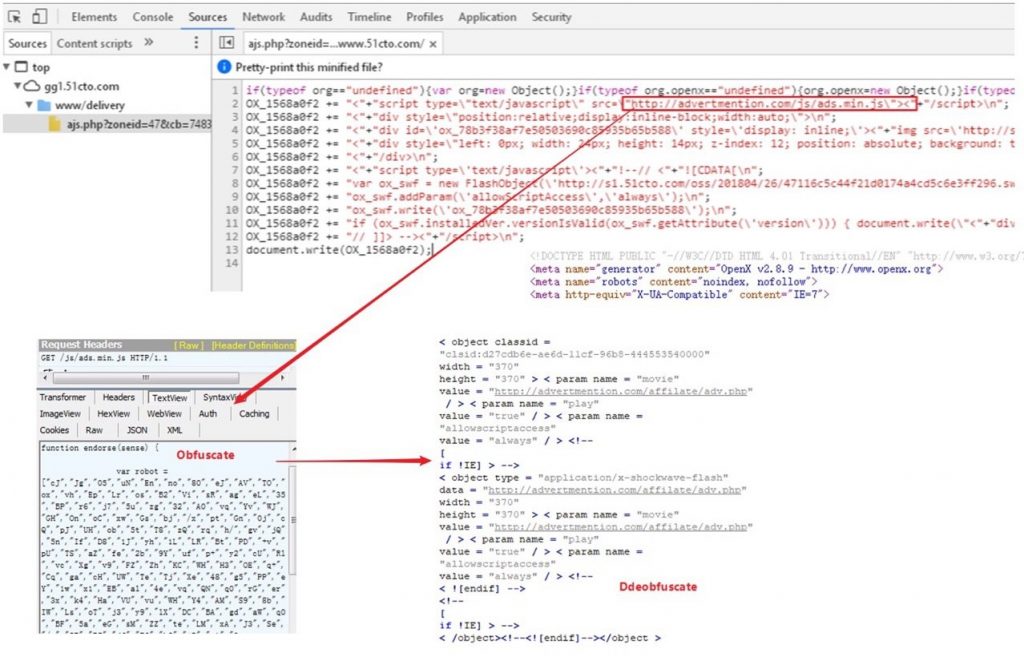
Figure 4. Obfuscated and deciphered code from injected javascript: ads.min.js.
After attacked websites are injected with malicious javascript, ads.min.js, the script downloads flash object that exploits CVE-2018-4878 and infects visitors’ computers with CryptoMiner.
Websites with OpenX were exploited
Take 51CTO.com and cmechina.net for example, their OpenX system contains lots of known vulnerabilities. OpenX system has been revealed multiple times carrying many high risk vulnerabilities, including XSS, CSRF. Among these vulnerabilities, CVE-2013-3514 and CVE-2013-3515 is related to XSS and affects version 2.8.10 and below. This allows attackers to inject arbitrary code. CVE-2013-4211 affects 2.8.10 and above and allows attackers to installs backdoor on PHP pages. Figure 4 shows the accumulated vulnerabilities of OpenX system from exploit-db.
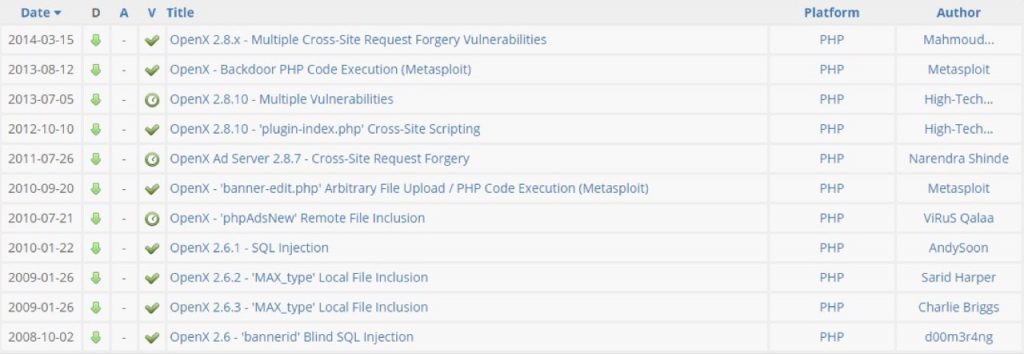
Figure 4. OpenX in exploit-db
The latest GreenFlash Sundown has come up with specialized module for OpenX system and cybercriminals can easily leverage the module to form attacks.
Website Owners are Recommended Giving Up OpenX System
OpenX has not updated its system for years and almost every version contains high risk vulnerabilities. The CVE-2013-4211 has never been fix. The last update was 5 years ago. A flawless system from OpenX is way far from reach. Owners of websites can only restrict the access to vulnerable pages of OpenX system to avoid attacks. Perhaps, abandoning OpenX and embracing a safer system are the wise choices.
Security Tips
Without officall supports, website owners of OpenX system can apply the following practices to protect themselves temporarily.
1. Apply WAF defense for your websites.
2. Limit the access to the page of the Ads system: www/admin
3. Delete the backdoor code that triggers CVE-2013-4211 in flowplayer/3.1.1/flowplayer-3.1.1.min.js. (Code highlighted below is the backdoor)
![]()
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security







