On March 1st 2018, 360 Cert, an Internet security research center, detected a massive DDoS attack happening globally. Cybercriminals use Memcached server as an amplifier for DRDoS attack, so fewer computing resources are required to launch an extensive DDoS attack.
360 Cert warned that many cloud-based servers had been attacked globally, and more DRDoS events would arise by using Memcached.
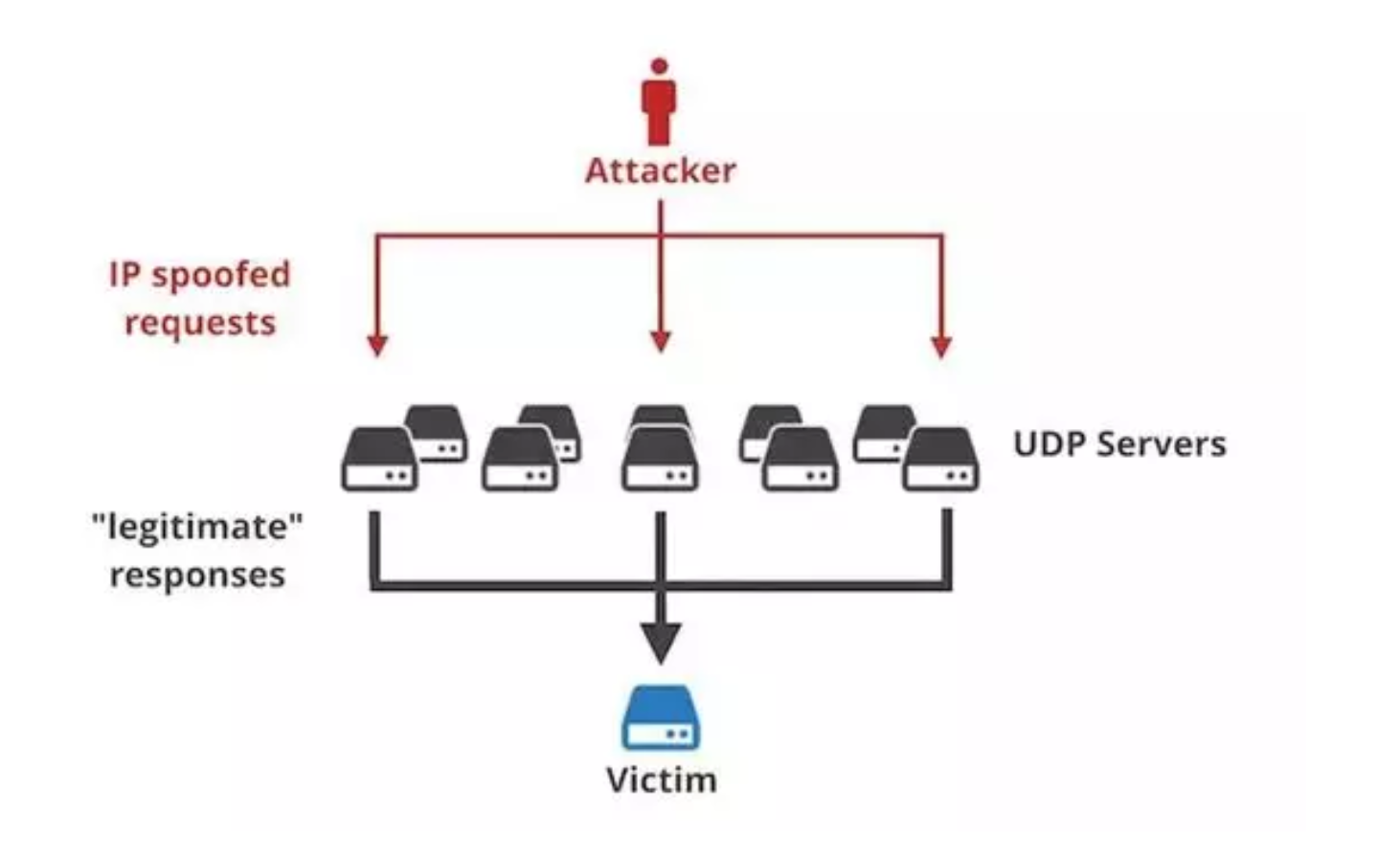
What’s DRDoS attack?
A DDoS (Distributed Denial of Service) attack is a well known method for attackers to paralyse an online service by overwhelming it with huge amount of traffic from multiple endpoints controlled by the attacker. (Learn more: Biggest DDoS attack )
The purpose of DRDoS (Distributed Reflection Denial of Service) is no difference. Yet DRDoS attackers disguise themselves as the targeted victims with IP spoofing technique, and send small packets to servers, which reflect back to victims with massive data instead of the attackers. In this way, attackers do not have to control many PC to launch an attack, but also can hide themselves from the attack.
Conduct a Memcached DDoS attack by utilizing the server
Memcached is a high-performance, distributed memory object caching system to speed up dynamic web applications. In this case, malicious actors take advantage of Memcached’s trait to intensify the attacks. Through the Memcached protocol, attackers are able to send over massive UDP packets including victims’ IP addresses, and then Memcached servers also response massive packets to these sources, and become a DRDoS attack.
In fact, one of the 360 information security teams, 0kee Team, had firstly discovered this attack technique in June 2017 and alerted security community during PoC 2017. The Memcached servers whose data storage is around 100 thousand are more likely to become targets. According to 360 Cert, these exposed hosts are mostly located in the United States and China.
The largest amplified DDoS attack in history
In the recent memcached amplification attacks, attackers use UDP port 11211 to send a tiny, byte-sized request. However, UDP doesn’t implement properly but respond with packets that are thousands of times bigger than the initial request. That said, attackers could trick memcached servers to send overwhelming packets back to victims.
It’s not common to see an attack being amplified to 1,000 times bigger, but the recent bandwidth amplification factor are estimated to be 50,000 times larger, which could be the most intense DDoS amplification attack in history.
Within this past week, the memcached DDoS attacks have been increasing rapidly from less than 50 events to more than 300 events a day. The largest recent attack was already sized over 0.5 Tbps but there could be much larger attacks that were not publicly reported, according to 360 Cert.
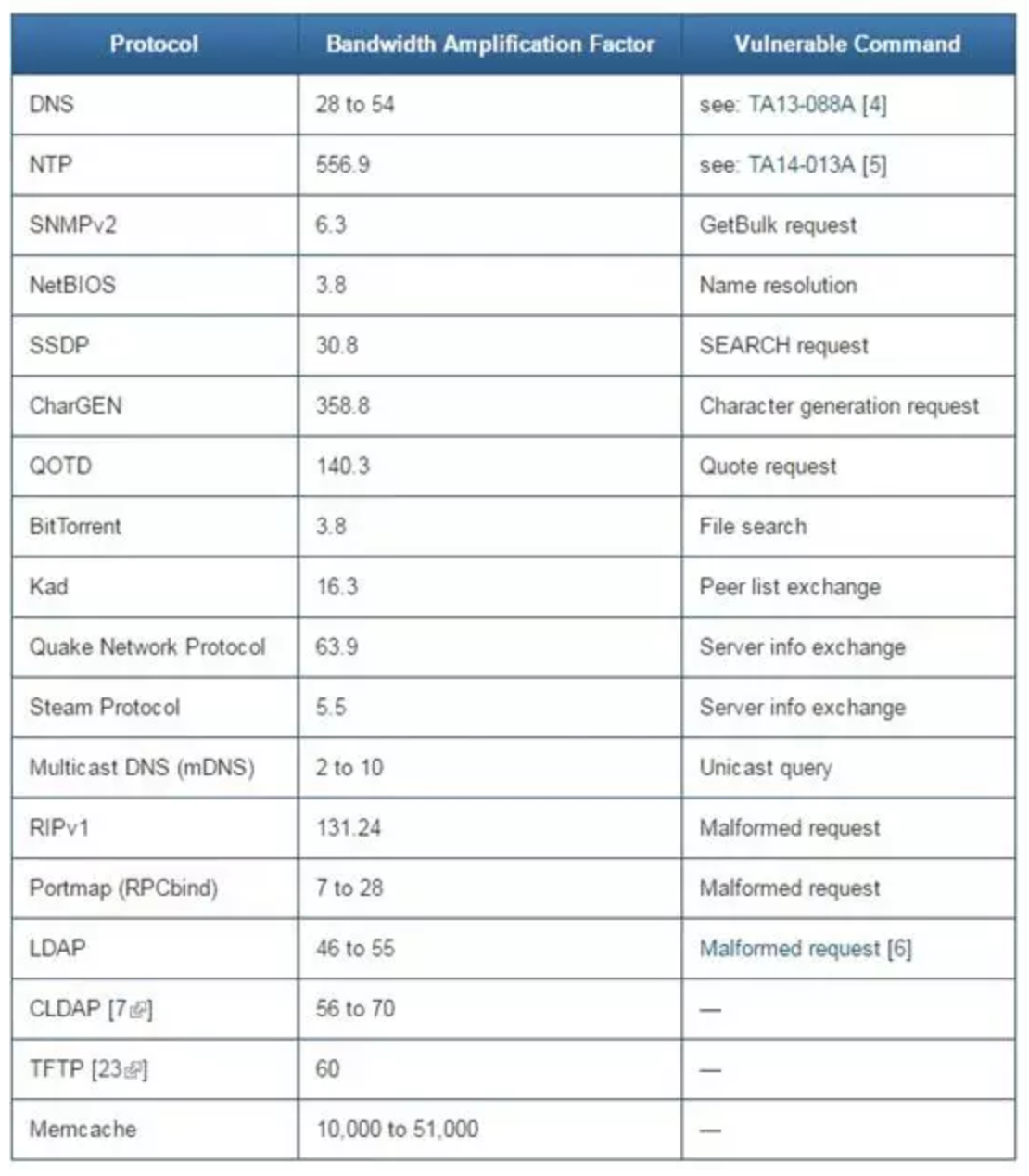
The Bandwidth Amplification Factor can be 50,000 times of the original
Reaction and Protection for Memcached users
More and severe Memcached attacks can be anticipated in the future, not to mention if the technique is acquired by other DDoS attack teams.
Memcached users are recommended to follow the steps below:
1. Put your service on a trusted domain. Set up ACL (access control list) or add security groups if necessary. Don’t listen on 0.0.0.0 when connected to extranet.
2. Change memcached default monitor ports to prevent machine scanning and SSRF (Server Side Request Forgery) attack.
3. Update to the latest version of memcached, and use SASL password for authentication.
About Internet Security, many ISP companies including NTT has set a speed limit to UDP11211. 360 security researchers further state that Internet service providers should forbid IP address spoofing in which DRDoS attacks root. They also suggest that ISP should allow users to use BGP flowspec to limit UDP11211 traffic for lessening traffic congestion while facing a DRDoS attack.
Learn more about 360 Total Security