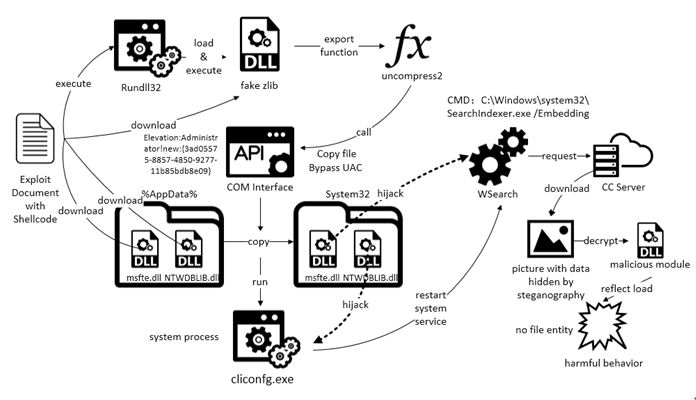
-
360 Total Security has intercepted more than 50,000 Clipboard Wallet Hijacker attacks, helping users recover over 40 million
Oct 12, 2018Elley -
Qihoo 360’s precise analysis of ransomware for September
Oct 11, 2018Elley -
Phishing attacks use Azure Blob storage to simulate Microsoft
Oct 9, 2018Elley -
Vulnerabilities discovered in electoral counting machines in 23 states
Oct 8, 2018Elley -
How to minimize corporate network security risks?
Oct 5, 2018Elley