Independent security researcher, Mike Olsen, found out there was pre-installed malware in the surveillance cameras bought from Amazon
Most people turn to Amazon when buying some goods, and Mike Olsen, is not an exception. Last week, this security researcher bought some surveillance camera rigs from an Amazon store with customer ratings.
While configuring this freshly bought camera, he could not find the option he needed. Considering this a bad CSS issue, he then opened up developer tools. What he found instead of the options to set up the camera rigs, was a hidden iframe sticked to the bottom of the body tag. What is more, this was linking to a suspicious host name, Brenz.pl.
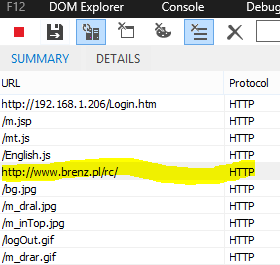
(Source: Mike Olsen’s blog)
Big names are no longer the guarantee for security
Google search results showed that this domain, Brenz.pl, had been shut down in the past due to malware distribution. However, it went back active in 2011 and kept hosting trojans like the one in Olsen’s case that may be loaded to infected users’ PC via other firmware.
Users tend to choose big brands or reputable channels when speaking of purchasing goods. However, with more channels developed for commercial activities, cybercriminals nowadays have more approaches to reach their victims.
For instance, in this comprised camera rigs case, one can barely image there might be potential risks – it’s a Sony camera bought from Amazon, how can it not be safe? Plus, this infected camera was ‘picked, packed, and shipped’ by Amazon’s Fulfillment Service and stayed ‘new’ when Olsen received it. If not found in time, hackers could have gained remote control to the security camera and stolen video feeds.
To conclude, in the time of Internet of Things, it can be expected that this type of threat will increase a lot. Vulnerabilities traditionally exploited in software are now also attempted in hardware, especially when more and more devices are connected.
Learn more about 360 Total Security