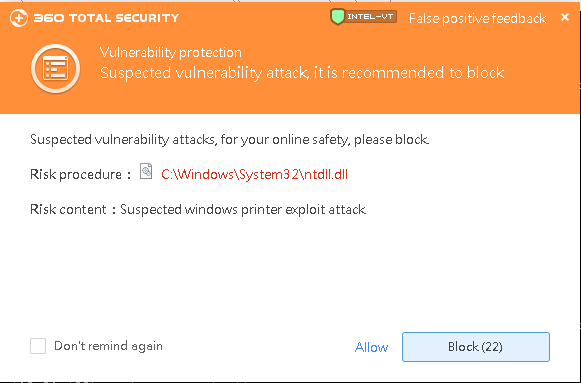
In the security update in June this year, Microsoft fixed a long-standing Windows Print Spooler remote command execution vulnerability, the vulnerability number is CVE-2021-1675. By exploiting this vulnerability, an attacker can use a low-privileged user to launch an attack on a computer in the local network and control the vulnerable computer. Especially in the enterprise, in the domain environment, ordinary domain users can use this service to attack the domain control server to control the entire network.
This problem is due to a flaw in the authentication code in SeLoadDriverPrivilege, causing general users to bypass checking and loading the driver through RpcAddPrinterDrive. The vulnerability has a wide range of impacts, and current mainstream windows operating systems will all be affected. It is recommended that users install the patch as soon as possible. If the patch cannot be updated in time, you can also close the Print Spooler service to alleviate the problem (but it will affect the normal use of the printing function). 360 Total Security also added the defense against this vulnerability attack for the first time. Install and use the latest version of 360 Total Security to defend against this vulnerability attack.
Learn more about 360 Total Security